Introduction
In this digital age, where data breaches and cyber threats are on the rise, safeguarding our sensitive information is of utmost importance. Encryption provides a robust solution to protect data from unauthorized access.
Understanding Encryption
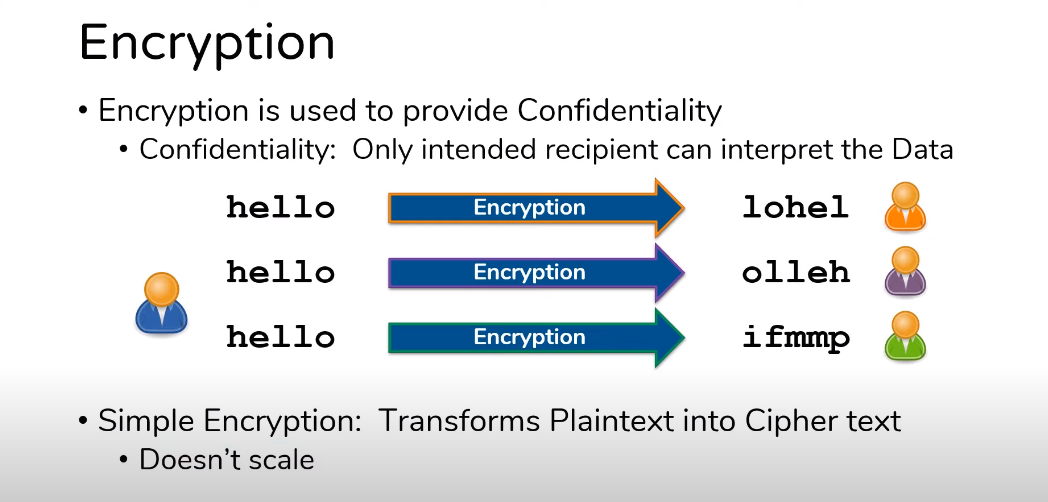
Encryption is the process of converting plaintext data into ciphertext, making it unreadable to anyone without the decryption key. It ensures that even if an unauthorized person gains access to the encrypted data, they won’t be able to decipher its contents.
Importance of Encryption
Encryption plays a crucial role in safeguarding sensitive information, such as personal details, financial data, and confidential business documents. By encrypting data, individuals and organizations can mitigate the risk of data breaches and unauthorized access.
Symmetric Encryption
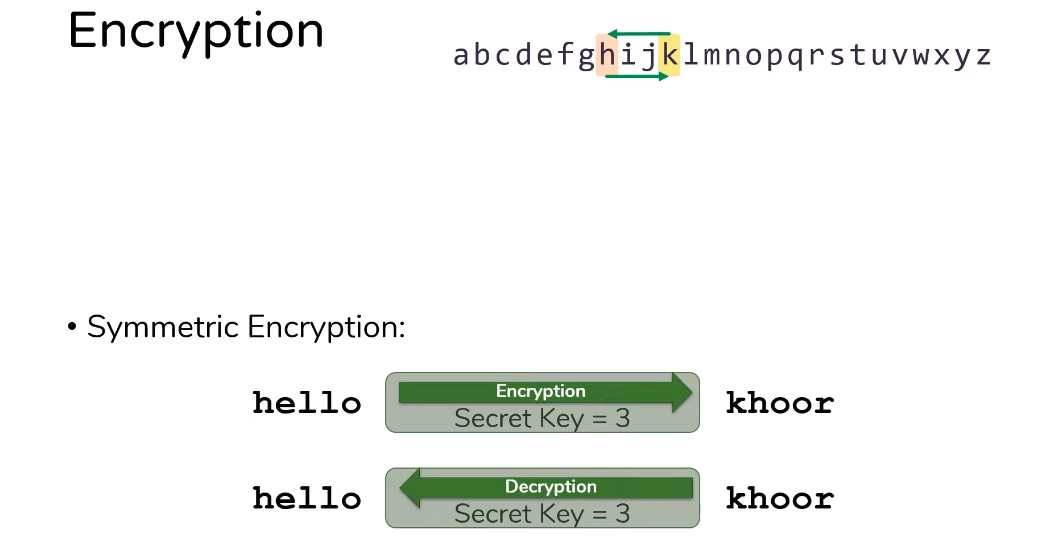
Way Symmetric Encryption Works
Symmetric encryption uses a single shared secret key to both encrypt and decrypt data. The same key is used for both processes, making it efficient for large volumes of data. The encryption and decryption processes are fast, but the challenge lies in securely exchanging the shared key between the sender and recipient.
Pros and Cons of Symmetric Encryption
Pros:
- Fast and efficient for bulk data encryption
- Simple implementation
Cons:
- Key management and distribution can be challenging
- Lack of scalability for large-scale deployments
Asymmetric Encryption

Way Asymmetric Encryption Works
Asymmetric encryption, also known as public-key encryption, uses a pair of mathematically related keys: a public key and a private key. The public key is used for encryption, while the private key is kept secret and used for decryption. Messages encrypted with the public key can only be decrypted with the corresponding private key.
Pros and Cons of Asymmetric Encryption
Pros:
- Secure key exchange without the need for a shared secret
- Enables digital signatures and non-repudiation
Cons:
- Slower compared to symmetric encryption
- Requires more computational resources
Generating Your Encryption Keys
Random Number Generators
To create encryption keys, it is crucial to use a reliable random number generator (RNG). A strong RNG ensures the generation of unpredictable and unique keys, enhancing the security of your encrypted data.
Key Length and Strength
The length of your encryption key directly impacts its strength. Longer keys provide higher levels of security, as they increase the complexity of breaking the encryption. It is recommended to use encryption algorithms with key lengths that align with current security standards.
Implementing Encryption Algorithms
Popular Encryption Algorithms
There are various encryption algorithms available, each with its strengths and weaknesses. Some popular encryption algorithms include:
- Advanced Encryption Standard (AES)
- RSA
- Elliptic Curve Cryptography (ECC)
Choosing the Right Algorithm
Selecting the appropriate encryption algorithm depends on several factors, including the level of security required, the performance impact, and compatibility with existing systems. It is essential to conduct thorough research and consult experts before finalizing your encryption algorithm.
Encryption Best Practices
Secure Key Storage
Storing encryption keys securely is crucial to maintaining the integrity of your encrypted data. Implement measures such as key vaults, hardware security modules (HSMs), or secure key management systems to protect your keys from unauthorized access.
Regular Key Rotation
Regularly rotating your encryption keys adds an extra layer of security. By changing your keys periodically, even if one key is compromised, the impact will be limited, as the data encrypted with the previous keys will remain secure.
Multi-factor Authentication
Adding an extra layer of authentication, such as biometrics or smart cards, strengthens the security of your encryption keys. Multi-factor authentication ensures that even if one factor is compromised, the data remains protected.
Conclusion
Data encryption is an essential aspect of securing sensitive information in today’s digital landscape. By understanding encryption concepts, generating your encryption keys, and implementing best practices, you can significantly enhance the security of your data. Remember to stay up to date with the latest encryption standards and technologies to ensure optimal protection against evolving threats.
FAQs
Is it necessary to encrypt all data?
While encrypting all data is not always necessary, it is highly recommended for sensitive information and data that needs to be protected from unauthorized access.
Can encrypted data be decrypted without the encryption key?
Decrypting encrypted data without the encryption key is extremely difficult, if not impossible. The encryption key is required to decipher the encrypted information.
Are encryption algorithms infallible?
While encryption algorithms provide robust security, they are not infallible. It is crucial to stay updated with the latest encryption standards and employ best practices to mitigate potential vulnerabilities.
Can I use the same encryption key for multiple purposes?
It is generally not recommended to use the same encryption key for multiple purposes. Each encryption key should be specific to its intended use to maintain data security.
How often should I rotate my encryption keys?
The frequency of key rotation depends on your security requirements. It is advisable to establish a key rotation policy based on industry best practices and regulatory guidelines.
