Introduction
Overview Of AWS

In an AWS account, the responsibility for data security is shared between Amazon and the customer. Amazon is responsible for securing the infrastructure that supports its services, such as physical access control to data centers and network security. On the other hand, customers are responsible for ensuring that their own content and applications hosted on AWS comply with industry standards and applicable laws.
To make it easier for customers to manage their responsibilities, AWS has developed various security features that allow them to encrypt their data, monitor their systems for potential threats, and configure access control policies. For example, customers can use AWS Key Management Service (KMS) to create and manage encryption keys or Amazon CloudWatch to monitor system activity in real time.
While AWS takes care of securing its infrastructure, customers must ensure that they follow best practices when using the platform’s services. By leveraging tools provided by AWS such as KMS or CloudWatch along with maintaining proper compliance measures in place businesses can benefit from a highly secure cloud environment while confidently focusing on delivering value-added services.
AWS Shared Responsibility Model
The Shared Responsibility Model is an essential concept to understand when it comes to data security in an AWS account. This model clarifies which security responsibilities are shared between AWS and the customer. In this model, AWS manages the security of the cloud infrastructure itself, including hardware, software, and facilities. On the other hand, customers manage their data within that infrastructure.
Customer’s Responsibility For Data Security
Overview Of Customer’S Role
The customer’s role in data security within an AWS account is crucial. The customer has a great deal of control over the measures that are taken to ensure the security and privacy of their data.
Best Practices For Data Security In An AWS Account
To ensure best practices for data security in an AWS account, customers should implement multi-factor authentication (MFA) for all accounts and use strong passwords. Additionally, customers should encrypt sensitive data using secure protocols such as SSL/TLS or SSH when transmitting data to or from their AWS environment.
Authentication And Access Management
Authentication and access management are the mechanisms that control who has access to what resources within the account. AWS offers several authentication methods, including user name and password, multi-factor authentication (MFA), and federated identity management. MFA is highly recommended as it adds an additional layer of security for users accessing the account.
Access management involves defining policies that specify which resources each user or group of users can access within the account. These policies can be customized to grant permissions for specific actions such as reading or writing data, launching instances, or creating backups. It is important to ensure that only authorized personnel have access to sensitive data and resources.
Network Security
Customers have complete control over their data in terms of how it’s stored, accessed, and transmitted within their AWS environment. They need to ensure that they protect their sensitive information by implementing strong access controls and encryption mechanisms. In addition, customers should regularly audit their accounts to detect potential threats or vulnerabilities.
Data Encryption
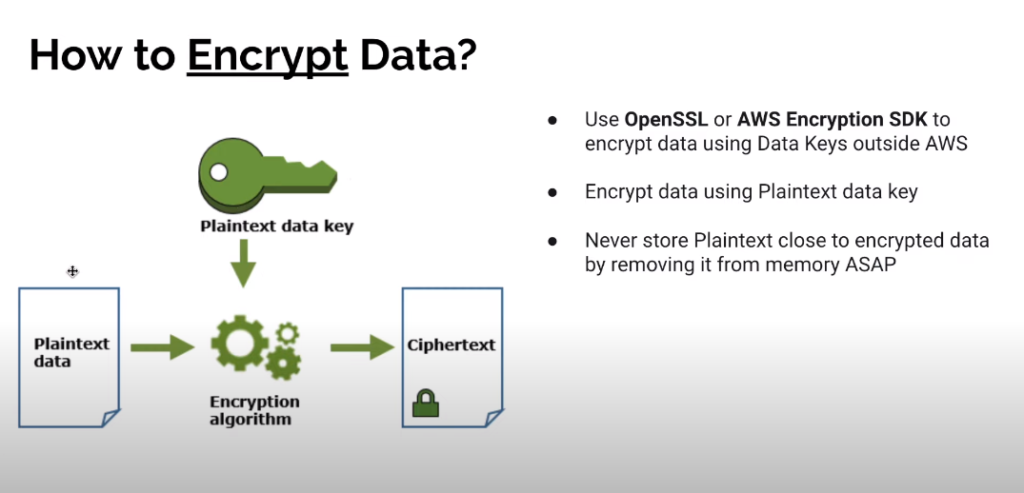
AWS has implemented various tools and services that enable customers to encrypt their data at rest or in transit. One such tool is the AWS Key Management Service (KMS), which enables customers to create and manage cryptographic keys used for encrypting their data. Customers can also use Amazon S3 server-side encryption and Amazon EBS encryption to encrypt their stored data.
Regular Backups And Disaster Recovery
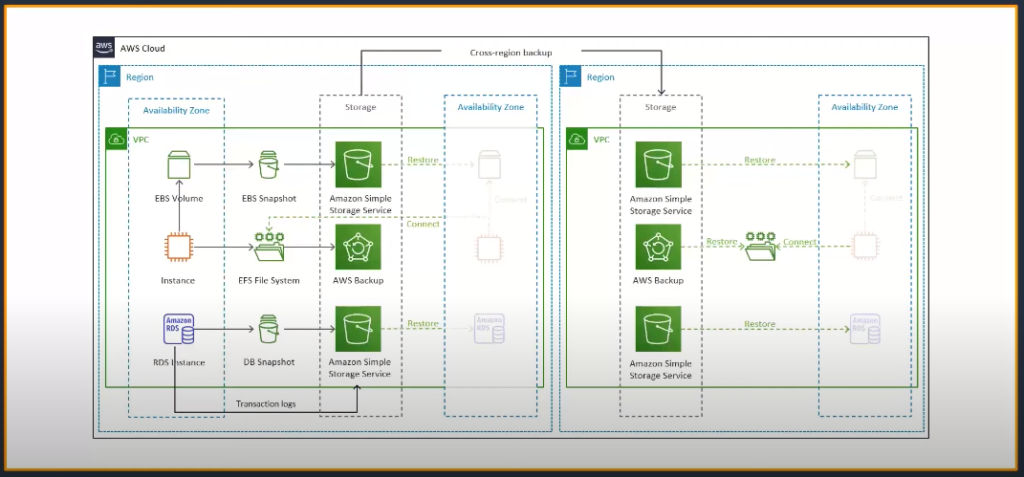
AWS provides a range of backup and recovery services that allow users to protect their data against accidental loss, corruption, or deletion. These services include Amazon S3, Amazon EBS snapshots, and Amazon RDS automated backups.
Regular backups ensure that data is stored safely and can be quickly restored in the event of a disaster. With AWS, users can schedule regular backups of their critical data to safeguard against unexpected incidents such as hardware failure or natural disasters.
Disaster recovery is another crucial element of data security in an AWS account. AWS offers various disaster recovery solutions such as Multi-AZ deployments for databases or implementing a Disaster Recovery (DR) plan with AWS Backup & Restore service to ensure business continuity during any disruption.
Security Monitoring And Logging
Security monitoring involves the continuous assessment of system activities to detect any unauthorized access or suspicious behavior. AWS provides several services for security monitoring, such as Amazon CloudWatch, which monitors the availability and performance of applications running on AWS.
Logging refers to the process of capturing events or transactions occurring within a system and storing them in a centralized location for later analysis. AWS offers various logging services like Amazon S3 Server Access Logging that captures all requests made to S3 buckets while providing detailed insights into who accessed what data at what time.
AWS Responsibility For Data Security
AWS’s Security Measures
AWS provides a secure infrastructure that includes numerous measures such as encryption, access controls, monitoring, and compliance certifications that ensure the protection of customer data.
Physical Security Of Data Centers
Physical security is a critical aspect of protecting data centers. It involves the implementation of measures that restrict access to servers, network devices, and other hardware components that store or transmit sensitive information. Data center operators must ensure that only authorized personnel can enter secure areas through strict identification protocols such as biometric authentication and ID card scanners.
In an AWS account, physical security is managed by Amazon Web Services (AWS). They provide a secure infrastructure environment for their customers’ applications and data. AWS ensures that its data centers are built with multiple layers of physical security including perimeter fencing, video surveillance, security breach alarms, and 24/7 on-site security staff.
Data Encryption
AWS offers encryption options for data at rest and in transit, which can help protect against unauthorized access or interception of sensitive information. Additionally, AWS regularly audits its systems and implements rigorous security protocols to ensure that customer data remains secure.
Compliance Certifications
There are several compliance certifications available for AWS accounts, including PCI DSS, HIPAA, and SOC 2. Each certification addresses different security concerns and requires specific controls to be implemented within an organization’s infrastructure. For example, HIPAA certification is required for healthcare organizations that handle electronically protected health information (ePHI), while SOC 2 certification focuses on security, availability, processing integrity, confidentiality, and privacy of customer data.
Ultimately, compliance certifications provide reassurance to customers and stakeholders that an organization takes data security seriously.
Incident Response And Reporting
AWS provides several mechanisms for detecting and responding to security incidents, such as Security Hub, GuardDuty, and CloudTrail. However, it is up to the user to configure these services correctly and take appropriate action when a potential incident occurs.
When an incident does occur in an AWS account, it is crucial to have a clear reporting process in place. This includes identifying what information needs to be reported, who should be notified, and how quickly they need to be informed.
Challenges In AWS Data Security
Common Challenges Faced By Customers
Lack Of Expertise
Not every organization has the in-house expertise needed to manage data security effectively. This lack of expertise can be particularly problematic when it comes to cloud environments like AWS.
Without sufficient knowledge and experience, organizations may struggle to properly configure their AWS accounts for optimal security. They may not know how to set up access controls or implement encryption measures, leaving their sensitive data vulnerable to breaches or attacks.
To address this issue, many organizations turn to third-party experts who specialize in AWS security. These professionals can identify potential vulnerabilities and recommend strategies for improving overall security posture within an AWS environment.
Misconfigured Resources
Misconfigured resources can pose a significant risk to the security of an AWS account. These misconfigurations can occur due to human error or oversight, such as leaving a resource open to public access, or through malicious intent by an attacker who gains unauthorized access to the account. Regardless of the cause, misconfigured resources create opportunities for attackers to exploit vulnerabilities and gain access to sensitive data.
In an AWS account, control over data security is ultimately the responsibility of the owner of that account. This means that any misconfigured resources are their responsibility to identify and address promptly. AWS provides tools and services designed to assist in identifying and remediating these issues quickly, but it is up to the account owner or administrator to ensure they are being used effectively.
To mitigate risks associated with misconfigured resources, it’s crucial for organizations using AWS accounts regularly conduct security assessments and implement best practices for securing their infrastructure. This includes monitoring existing configurations continuously, implementing strict access controls on all resources in use in their environment, regularly reviewing logs for suspicious activity; applying patches promptly when new vulnerabilities are identified; among many others.
Compliance Requirements
One of the major challenges in AWS data security is maintaining compliance with regulatory requirements such as HIPAA or GDPR. Security and compliance go hand-in-hand, and failing to meet these requirements can result in severe penalties or reputational damage for a business.
Threats From Malicious Actors
These attackers are often hackers or other cybercriminals who seek to exploit vulnerabilities in the system to gain access to sensitive information. They may also utilize phishing scams and other social engineering tactics to trick users into giving up their login credentials.
Once a malicious actor gains access to an AWS account, they can potentially steal valuable data, compromise sensitive information, and wreak havoc on the entire infrastructure. This can lead to major financial losses for businesses and irreparable damage to their reputation.
To mitigate these threats, it’s essential for AWS account holders to implement strong security measures such as multi-factor authentication (MFA), regular password updates, and continuous monitoring of user activity within the account. Additionally, staying informed about current cybersecurity risks and following best practices can help prevent these types of attacks from occurring in the first place.
FAQs
Can AWS Be Held Responsible For A Data Breach In My Account?
In the event of a data breach in an AWS account, both parties may be held responsible depending on the cause of the breach. AWS will investigate any reported incidents but ultimately it is up to the user to take action to prevent future breaches by following best practices for cloud security.
Do I Need To Hire A Dedicated Security Team To Manage My AWS Account?
It depends on the size of your business and the complexity of your infrastructure. For small businesses with a limited number of resources, outsourcing security services from an external provider might be enough. However, if you have multiple applications running in different environments and handle sensitive data, then having an in-house security team can provide better control over the security posture.
What Compliance Certifications Does AWS Have?
AWS has numerous compliance certifications that ensure the security of their customer’s data. These certifications cover a broad range of industries and regulatory requirements. Some examples of AWS compliance certifications include SOC 1, SOC 2, and SOC3 for financial institutions, FERPA for educational institutions, HIPAA for healthcare organizations, and PCI DSS for payment card industry companies.
Can I Use Third-Party Security Services With My AWS Account?
Using a third-party security service with your AWS account can help you address specific security concerns that are not covered by AWS’s native security features. For example, if you are concerned about threats from distributed denial-of-service (DDoS) attacks, you may want to consider using a specialized DDoS mitigation service as an additional layer of protection.
Can I Transfer Ownership Of Data In My AWS Account To Another Party?
The ownership of data in an AWS account can be transferred to another party through several means. The first option is to use AWS’s built-in tools for transferring ownership, such as the Amazon S3 bucket policy or IAM policies. These tools allow users to grant permissions to other parties for accessing and managing their data. However, it is crucial to ensure that the new owners have the necessary security credentials before transferring ownership.
Another option for transferring ownership of data in an AWS account is by using third-party migration services like CloudEndure or Racemi. These services help move data from one AWS account to another while maintaining the security and integrity of the information being moved. Additionally, some companies opt for a legal approach where they transfer control through contracts or agreements with their clients.
Which Web Service To Use For Data Security?
To help ensure data security in an AWS account, users should take advantage of native AWS services such as Identity and Access Management (IAM), Key Management Service (KMS), and CloudTrail. IAM allows users to create and manage user accounts with specific permissions to access resources within their AWS account. KMS enables encryption key management for sensitive data stored in Amazon S3 buckets or other compatible storage solutions. CloudTrail provides audit trails to track API calls within an AWS environment.
What Are The Features Of AWS That Can Ensure Data Security For Your Confidential Documents?
There are several features that can help ensure the confidentiality of your documents. Amazon Virtual Private Cloud (VPC) offers a secure and isolated environment where you can launch resources and store data. VPC allows you to define network topology, and configure IP addresses, subnets, routing tables, security groups, and network ACLs. All these features provide granular control over access to your confidential documents.
Another essential feature of AWS is Identity and Access Management (IAM), which enables you to manage user access at scale. IAM provides fine-grained permission controls for accessing AWS services and resources. You can use IAM policies to grant or deny permissions based on specific conditions such as time of day or source IP address.
Amazon S3 provides encryption options for both data in transit and at rest using server-side encryption with Amazon S3-managed keys (SSE-S3), AWS Key Management Service-managed keys (SSE-KMS), or customer-provided keys managed outside of AWS (SSE-C). These encryption options enable customers to meet regulatory compliance requirements while maintaining the high availability of their data.
Conclusion
It is crucial for businesses to understand their responsibility in terms of data security when using AWS. While AWS does provide a secure infrastructure and various tools to enhance security measures, it is ultimately up to the user to properly configure and manage their account settings. This includes implementing strong access controls, monitoring for suspicious activity, and regularly backing up data.
