Encryption converts readable data (plaintext) into an encoded form (ciphertext) using mathematical algorithms and cryptographic keys. Some of the best-paid tools for 256-bit AES encryption include AxCrypt, Folder Lock, and Privacy Drive, offering password management and cloud sharing features. Free options include AES Crypt, 7-Zip, and Gpg4win, which provide strong encryption without compromising security.
What is encryption?
Encryption is a complex process that serves as a digital security measure to protect sensitive and confidential information from unauthorized access or interception. It involves transforming readable data, plaintext, into an encoded format called ciphertext. This conversion is achieved through the use of mathematical algorithms and cryptographic keys.
The primary purpose of encryption is to ensure that even if someone gains access to the encrypted data, they cannot understand or decipher it without the corresponding decryption key. This makes the data essentially unreadable and secure, providing privacy and confidentiality for various types of information, such as personal messages, financial transactions, and sensitive corporate data.
Types of encryption:
- Symmetric Encryption (Private-Key Encryption):
- How it works: Symmetric encryption uses the same key for encryption and decryption. This key is typically kept secret between the sender and receiver.
- Advantages: Fast and efficient; well-suited for large volumes of data.
- Disadvantages: The challenge lies in securely sharing the secret key between parties.
- Examples: AES (Advanced Encryption Standard), DES (Data Encryption Standard), 3DES (Triple DES).
- Asymmetric Encryption (Public-Key Encryption):
- How it works: Asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption. The public key can be freely shared, while the private key must be kept secret.
- Advantages: Solves the key distribution problem in symmetric encryption; enables secure communication without prior key exchange.
- Disadvantages: Slower and less efficient than symmetric encryption due to complex mathematical operations.
- Examples: RSA, ECC (Elliptic Curve Cryptography), DSA (Digital Signature Algorithm).
- Hash Functions:
- How they work: Hash functions take an input (message or data) and produce a fixed-size output, known as a hash value or digest. They are one-way functions, meaning it’s difficult to reverse the process and obtain the original input from the hash.
- Use cases: Hash functions are used for data integrity verification, password storage (salting and hashing), and digital signatures.
- Examples: SHA-256 (part of the SHA-2 family), MD5 (less secure due to vulnerabilities).
Why 256-bit AES Encryption?
AES encryption is a symmetric encryption algorithm widely used to secure data. The “256-bit” refers to the length of the encryption key, and this level of encryption is renowned for its exceptional security. It provides trillions of possible key combinations, making it incredibly challenging for unauthorized parties to decipher encrypted data.
Best Free Tools for 256-bit AES Encryption:
1. AxCrypt
AxCrypt offers both 128-bit and 256-bit encryption options, ensuring robust security. AxCrypt simplifies the process with features like password management, cloud sharing, and a convenient drag-and-drop interface. It’s a portable application, eliminating the need for installation on your PC.
Key Features of AxCrypt:
- 128-bit and 256-bit encryption options
- Password management
- Cloud sharing
- Drag-and-drop interface
- Portable application
Before committing to the paid version, you can test the waters with the free version to understand its capabilities. However, note that the free version lacks 256-bit encryption, which may impact its suitability for your needs. Visit AxCrypt Homepage
2. Folder Lock
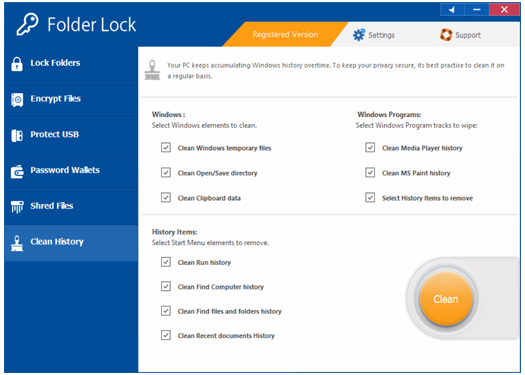
Folder Lock is a versatile file-locking software that not only password-protects but also encrypts your folders with AES 256-bit encryption. It extends its protection to optical media, email attachments, portable storage, and more. The software even includes password wallets for securely storing sensitive information like credit card and bank account details. It offers both free and paid versions, with the paid version providing additional features.
- AES 256-bit encryption
- Password wallets
- Protection for internal and external drives
- Easy-to-use interface
Folder Lock’s simplicity makes it an excellent choice for users who prefer a hassle-free experience. Select the desired drive to secure your confidential data and click on the ‘Encrypt’ option. Download Folder Lock for Desktop
3. Privacy Drive
Privacy Drive employs virtual disk and on-the-fly technology, allowing you to encrypt your data effortlessly. With a user-friendly drag-and-drop feature, Privacy Drive makes encryption accessible to all. It supports both AES 128-bit and AES 256-bit encryption, catering to various security needs.
Key Features of Privacy Drive:
- Virtual disk and on-the-fly technology
- Drag-and-drop interface
- AES 128-bit and AES 256-bit encryption support
4. BitLocker
BitLocker is a paid encryption tool integrated into the Windows operating system. It offers robust 256-bit AES encryption for entire drives or specific folders. While it comes with a cost for the Windows Pro edition, it’s a highly trusted solution that ensures your data’s safety.
5. Symantec Endpoint Encryption
Symantec Endpoint Encryption is tailored for businesses and offers top-notch data protection. With 256-bit AES encryption, it’s capable of safeguarding sensitive corporate information, and its centralized management makes it an ideal choice for large organizations.
6. VeraCrypt
VeraCrypt is an open-source encryption tool that not only supports 256-bit AES encryption but also offers plausible deniability. It’s a versatile option suitable for individual users and organizations alike. Plus, it’s free!
7. AES Crypt
AES Crypt is a straightforward file encryption software that employs 256-bit AES encryption. It’s user-friendly, allowing you to encrypt individual files easily. It also offers cross-platform compatibility, making it an excellent choice for users on different operating systems.
8. 7-Zip
7-Zip is primarily known for its file compression capabilities but also supports strong encryption, including 256-bit AES. It’s a versatile tool that can both compress and encrypt files efficiently.
9. Gpg4win
Gpg4win is an encryption suite that includes GnuPG, a powerful encryption tool using the OpenPGP standard. It supports 256-bit AES encryption and is commonly used for securing email communications. It’s a comprehensive solution for those looking to encrypt emails and files.
Additional Considerations for 256-bit AES Encryption:
1. Usability
Ensure that the tool you choose aligns with your technical proficiency. Some tools are user-friendly, while others may require more advanced knowledge.
2. Compatibility
Verify that the tool is compatible with your operating system and the types of files you need to encrypt.
3. Plausible Deniability
If you require an extra layer of security, look for tools like VeraCrypt that offer plausible deniability, making it nearly impossible for unauthorized parties to detect the existence of encrypted data.
4. Support and Updates
Opt for tools that receive regular updates and have a supportive community or customer service, ensuring that potential issues are promptly addressed.
Conclusion:
Encryption, particularly 256-bit AES encryption, safeguards our digitally interconnected world. It provides a formidable barrier against unauthorized access, ensuring the confidentiality and security of sensitive information. While we’ve explored paid and free encryption tools, the choice ultimately hinges on your specific needs, technical proficiency, and preferences. Paid options like AxCrypt and Folder Lock offer robust features and ease of use, while free tools such as AES Crypt and 7-Zip provide formidable security without breaking the bank.
FAQs:
What are the advantages of symmetric encryption (AES) over asymmetric encryption?
Symmetric encryption, such as AES, is generally faster and more efficient than asymmetric encryption. It’s well-suited for encrypting large volumes of data. However, the challenge lies in securely sharing the secret key between parties, which is not required in asymmetric encryption.
What should I consider when choosing an encryption tool?
When selecting an encryption tool, consider usability, compatibility with your operating system and file types, plausible deniability features, and ongoing support and updates. Choose a tool that aligns with your technical proficiency and meets your security needs.
How can encryption be used to secure email communications?
Encryption tools like Gpg4win can be used to secure email communications. By encrypting email messages with strong encryption algorithms like 256-bit AES, you can ensure that only the intended recipient can decrypt and read the content, protecting the confidentiality of your emails.
Why is regular updating and support important for encryption tools?
Regular updates and support are crucial for encryption tools because they help address potential vulnerabilities and security issues. Having an actively maintained tool ensures that any security flaws are patched promptly, enhancing the overall security of your encrypted data.
Are there any additional considerations when choosing a 256-bit AES encryption tool?
Yes, when selecting an encryption tool, consider the following:
- Usability: Choose a tool that matches your technical proficiency.
- Compatibility: Ensure the tool works with your operating system and file types.
- Plausible Deniability: Some tools offer this feature, making it hard for unauthorized parties to detect the presence of encrypted data.
- Support and Updates: Opt for tools with regular updates and good customer support to address any issues that may arise.
