
How to Provide Technical Security to Health Care Data?
To ensure the technical security of healthcare data, organizations should follow the principles of confidentiality, integrity, and availability. This involves ...
Read More
To ensure the technical security of healthcare data, organizations should follow the principles of confidentiality, integrity, and availability. This involves ...
Read More
To secure user data across all platforms, it’s vital to: Understand the role and importance of user data in today’s ...
Read More
Abode Security’s data usage varies based on numerous factors, including the number of cameras and sensors, video quality, frequency of ...
Read More
The safest way to securely store data involves a combination of encryption, regular data backups, physical data storage security, cloud ...
Read More
Security cameras play a pivotal role in mitigating physical security risks in data centers by offering real-time surveillance, deterring unauthorized ...
Read More
To use data collection while maintaining privacy, organizations should minimize unnecessary data collection, obtain explicit consent from individuals, anonymize the ...
Read More
To retrieve data from an encrypted SD card, insert the card into an SD card reader connected to a computer. ...
Read More
AWS services that natively encrypt data at rest within an AWS region include Amazon S3, Amazon RDS, and Amazon EBS. ...
Read More
To recover data from a corporate McAfee encrypted drive, follow a systematic approach: determine the cause of data loss, evaluate ...
Read More
Both individuals and organizations are responsible for the security of data and information stored on computers. This includes the device’s ...
Read More
Understanding Data Encryption Data encryption is the process of transforming information into an unreadable form using cryptographic algorithms. To encrypt ...
Read More
To secure a data analytics firm, implement strong encryption, conduct regular security audits, train employees on security best practices, use ...
Read More
Data Warrior” offers robust security features, including strong encryption, multiple protection measures, user authentication, and granular access controls. However, like ...
Read More
In today’s digital age, the protection of personal information and secure communication has become a top priority. With rising concerns ...
Read More
If you are at fault for a data security breach, you should promptly acknowledge the mistake, inform affected parties, rectify ...
Read More
As our digital footprint continues to grow, so does the importance of data security. This is especially true when it ...
Read More
To bypass Android phone security using methods like Google account recovery, third-party software, and safe mode without losing data. In ...
Read More
To set up versioning for high-security data, you must use a secure data management system with built-in version control, enforce ...
Read More
The ultimate responsibility for the security of data and information often lies with an organization’s leadership, everyone involved, from it ...
Read More
The biggest data security threats are human error, sophisticated cyber attackers, and insider threats. In today’s digital stage, protecting sensitive ...
Read More
To copy secured data onto new devices, you should: End-to-End Encryption (E2EE) Tools Secure Data Transfer Platforms Physical Transfers with ...
Read More
AT&T Secure Family should typically function even when data is throttled, though with potentially reduced performance. In today’s digital age, ...
Read More
Storing data securely with multi-device access is crucial in the digital age. It’s imperative to choose the right platform, be ...
Read More
When a security breach occurs, capturing logs, user activity, affected accounts or systems, IP addresses involved, and timestamps of suspicious ...
Read More
Salaries vary based on region, experience, and specific roles. However, as of recent data up to 2023, computer security & ...
Read More
Yes, it is secure. iPhones integrate advanced hardware and software security mechanisms to protect stored local data. In today’s digital ...
Read More
A logging device typically receives various security data, including but not limited to login attempts (successful and failed), system alerts, ...
Read More
Data fragmentation and encryption significantly enhance data security by making it difficult for unauthorized persons to access or interpret the ...
Read More
Data transmission plans dictate how data is sent and received over networks, and their security components ensure that this transmission ...
Read More
Smart cards provide two-factor authentication for cloud data centers, enhancing security by requiring both the card and a PIN or ...
Read More
The most secure data transfer methods utilize end-to-end encryption and protocols like HTTPS or SFTP. In today’s digital age, data ...
Read More
Whether you need Dell Data Protection Security Tools depends on your security needs, device model, and data type you handle. ...
Read More
A mobile security data plan refers to services or features offered by mobile carriers to provide additional layers of security ...
Read More
The category of computing security that focuses on protecting and accessing data is “Data Security” or “Information Security. In today’s ...
Read More
AT&T Secure Family is a service provided by AT&T that offers parental controls and location services, allowing parents to monitor ...
Read More
To secure and protect data on a smartphone, use strong passwords, enable biometric features, regularly update software, avoid suspicious downloads, ...
Read More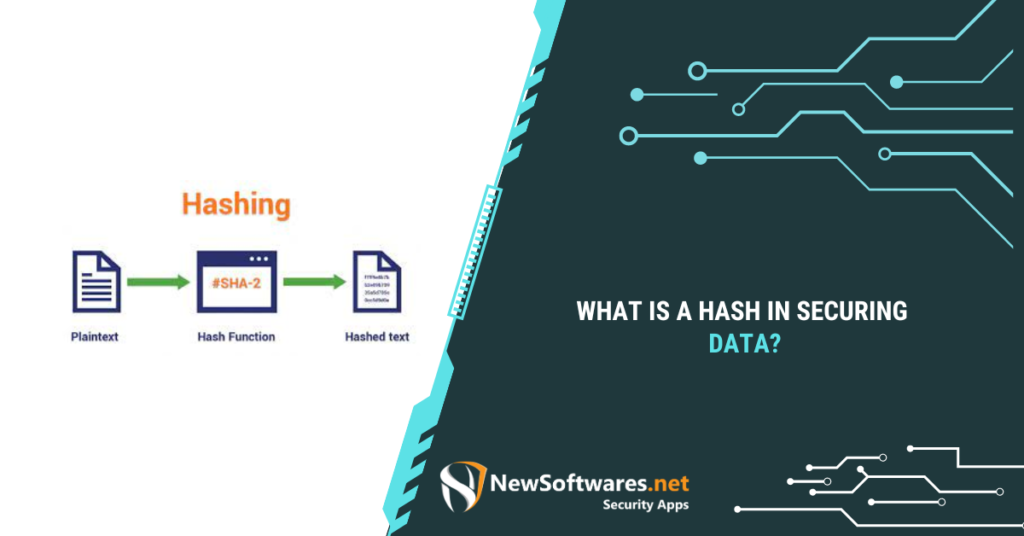
A hash is a function that converts an input (or ‘message’) into a fixed-size string of bytes, primarily used to ...
Read More
Yes, RAID (Redundant Array of Independent Disks) improves the security of your data by providing redundancy, which protects against data ...
Read More
To securely transfer data from the DMZ: Use encrypted protocols like SFTP or SCP. Employ a secure VPN tunnel. Implement ...
Read More
Homeland Security, like other government agencies, can access browsing data under specific circumstances, often requiring legal processes such as warrants ...
Read More
Data impact levels categorize data breaches’ sensitivity and potential impact. While specifics can vary, generally, higher levels indicate greater sensitivity ...
Read More
To make a secure data site, one should implement strong encryption, user authentication, access controls, and regular backups and ensure ...
Read More
To use hashing securely for data matching, choose a strong cryptographic hash function, salt your hashes, avoid outdated hashing algorithms, ...
Read More
To protect your internet privacy from data mining, use encryption tools, utilize virtual private networks (VPNs), regularly clear cookies and ...
Read More
To secure your data on Facebook, Ensure you adjust your privacy settings, be cautious of third-party applications, and regularly review ...
Read More
To keep database management systems (DBMS) and data-warehousing techniques secure, one must implement robust security protocols, apply regular software updates, ...
Read More
Yes, data stored in iCloud is encrypted both in transit and at rest, and Apple has executed multiple layers of ...
Read More
Disabling Android data destruction features often involves going to the security settings and turning off options like “Factory Reset Protection” ...
Read More
Securing nonrelevant data involves implementing measures to protect data that may not be directly related to core operations but could ...
Read More
To track secure data drives: Use hardware solutions like secure enclosures, biometric authentication, and tamper-evident seals. Implement software tools offering ...
Read More

Data Security and Encryption Softwares.