Introduction:
The software is not bound to give protection against USB drives only as it covers a wide range of options against which, you could protect yourself. Along with flash drives, it lets you block disc/floppy drives, block network access and block non-system devices. The main objective of USB block is to make sure there are no loose ends left behind from which, data theft may occur. In fact, it lets you have a complete peace of mind knowing you have nothing to be afraid of while you have turned your back on your system.
The process of how you can block devices with USB Block
Many IT professionals and administrators use firewall to secure their network and to block unauthorized access while permitting authorized communications. Many people install spam filters on their SMTP servers or install anti-virus software on all client workstations just to secure their network and database. But all these security measures would not ensure complete end point security. What happens if a user brings his 2GB thumb drive, connects it to your PC and downloads all your sensitive information?
A small sized USB drive or even a memory stick can store complete or a significant portion of your company’s data including financial records, customers’ details, business plans and sales history. What will happen if someone gets access to all such sensitive data? Your reputation can go straight down the hill or the worst scenario would the lost of all your customers in seconds. Therefore, it is always recommended to prevent data leakage to ensure complete security of your data.
USB Block is security software that prevents data leakage by blocking all unauthorized removable storage devices and drives. For example; it can block USB drives, external drives, SD cards, memory sticks, digital cameras, memory cell phones, iPods, blackberry, android, FireWire, blu ray media and floppy discs, network mapped drives and computers, Ethernet, Wi-Fi and Bluetooth networks as well as Non-System drives.
USB Block is easy to use and install software that does not complicate its users with complicated procedures. It provides an easy way to assign access rights to certain devices while blocking all others.
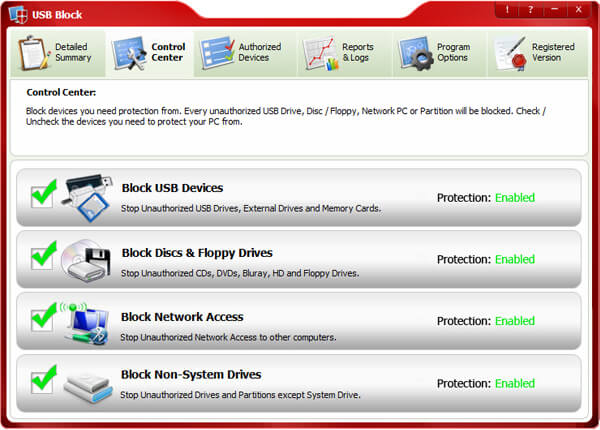
- Follow these simple steps to block unauthorized access of devices that do not belong to you:
- Download and install USB Block. Note: Administrative rights will be required to install USB Block.
- When you run the program for the first time, it will ask you to set and confirm a password. Make sure to set a strong password which is easy for you to remember but hard for others to guess.
- Enter Password and click ‘OK’.
- Switch to ‘Control Center’ tab from where you can block devices you need to protect your PC from. By default, USB devices / ports are blocked. However, you can also block other types of devices from ‘Control Center’ tab.
- For your convenience, we have categorized all types of removable devices into four categories which are listed below:
1. USB Devices
-
- This category includes any storage device that is attached to USB port or any connector and shows a drive in the system. For example; USB Drives, External Drives, SD Cards, MMCs, Memory Sticks, Digital Cameras, Memory Cell Phones, iPods, Blackberry, Android and Other Mobile Phones, FireWire, Enhanced mini-USB, HCI i.e. Host Controller Interface, HP-IL, Com, LPT, IrDA, USB on-the-go, U3, EHCI, RAID Controller, Host adapter, Serial Cable (use with data transfer), Serial ATA, ACCESS.bus etc.
2. Media Discs / Floppy Drives
-
- This category includes CD-R, CD-RW, CD-RAM, DVD-R, DVD-RW, DVD-RAM, HD-R, HD-RW, HD-RAM, Blu Ray-R, Blu Ray-RW, Blu Ray-RAM, Floppy Disk A, Floppy Disk B and Zip Drives.
3. Network Drives / PCs
-
- This category includes Network Computers, Specific PC’s Drives, Map Network Drives, Ethernet, Wi-Fi and Bluetooth Networks or any other drive that user access via Run command, IP, DOS or Windows Explorer.
4. Non-System Drives
- This category includes IDE, SATA, ATA, FATA, Parallel ATA, SCSI, SASI, RAID and all other relevant types of Hard Drives.
- To block a particular type of device simply check the relevant box. Once blocked, unauthorized devices cannot access your computer without your permission (password).
- All those devices and drives which you have authorized to access your data by adding them to the Authorize List will get full access to your data as soon as they are plug-in.
- To add a device to Authorize List, simply check the box ‘Remember (add to Authorize List)’ that appears every time an unauthorized device is plugged-in or a network mapped drive is accessed from the computer where USB Block is installed.
Benefits of USB block:
USB block lets you restrict all the unauthorized devices from connecting into your system
Let’s you access your trusted devices by whitelisting them
USB block’s security even works while you are away
Unauthorized USB drives, floppy disks, non-system drives can be restricted easily

