Introduction:
In this rapidly changing world, it is hard for anyone to survive without facing stiff competition. Before USB drives, there were floppy disks, which eventually were replaced with the famous USB drives. The future however predicts the emergence of cloud services (Dropbox, Google Drive, OneDrive etc.) which are meant to replace these USB drives. However, most of the users are still reluctant in moving to cloud from USB drives, as the data stored in the cloud has no guaranty of being safe from all directions.
USB Secure for reliable security
According to The Privacy Rights Clearinghouse, the year 2010 saw more than 10.2 million records being breached and were publicly reported in the United States from a total of 388 breach incidents using one form of portable flash drives or another.. The year , as of July , has fared even worse with close to 19 million records breached from 215 breach incidents that were publicly reported.
Consider the following example as to how USB flash drives can be used to attack a network system and retrieve valuable data.
“Keystone Mercy Health Plan and AmeriHealth Mercy Health Plan said Tuesday that a portable computer drive containing the names, addresses, and health information of 280,000 Medicaid members in Pennsylvania has been lost. The affiliated companies together insure 400,000 people on medical assistance in Pennsylvania. The computer drive included members’ health plan identification numbers and some of their health information, the insurers said. Also stored on the drive were the last four digits of 801 members’ Social Security numbers, plus complete Social Security numbers for seven others.” As reported by OSVDB.
The above scenario paints a gloomy picture of how USB flash drives have been, and continue to be used for malicious purposes. The above data breach incidents affecting private corporations, government institutions, public networks, and individual data indicates the importance of USB security and having a secure USB drive. Since USB flash drives are being used extensively because of the convenience and ease of use, they also pose a great risk of data loss or data leakage. USB Secure is a USB security software that lets you password protect USB flash drives, thumb drives, jump drives, pen drives, memory cards, memory sticks and lock external hard drives. The program supports plug and play i.e., whenever you plug in your USB drive, USB Secure runs automatically asking you for the correct password to protect and / or unprotect your USB drive. Furthermore, it protects your data by using multiple layers of patent pending protection methods that makes its protection PC independent. It means you need not to install USB Secure at other end to unprotect your protected data.
With USB Secure installed on your USB flash drive, you attain complete USB security and put your mind at peace from security breaches and data seepage. Simply follow these easy steps and never again worry about your lost or stolen flash drive:
Download USB Secure to your hard drive. Plug in
USB flash drive and run the Setup to install the program on your flash drive. Please note that when you run the Setup
file, USB Secure will install itself on your flash drive or any other storage device currently plugged in to your
computer. Even if you have downloaded USB Secure to your hard drive, it will always get installed on your flash drive.
Next, run the program directly from your flash drive. If the program is already installed on your USB drive then
plugging it in your computer will prompt an Autoplay window asking you two options:
- Open USB-Drive
- Protect This USB Drive
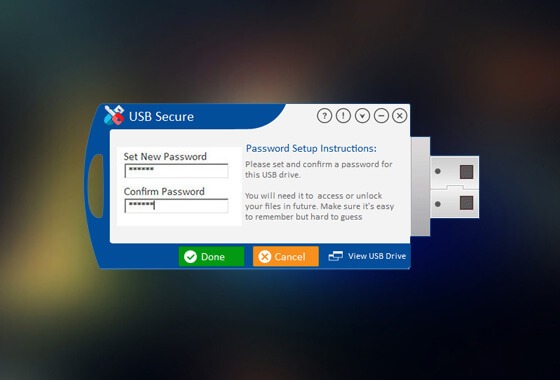
- Click ‘Protect This USB Drive’. Next, set and confirm a new password for the USB flash drive and click
on ‘OK’ to password protect and use USB Secure to protect your flash drive.
How to access protected data?
USB Secure is an easy way to password protect and, when you deem necessary, to unprotect your USB flash drives.
Operating the program does not require technical know-how about USB flash drives or computers.
Simply follow these simple and easy-to-follow steps to unprotect your USB flash drive:
- Plug in your USB flash drive and enter the correct password. Once you have entered the required
details, USB Secure will ask you to choose between two options: - Open USB-Drive
- Unprotect This USB Drive
- To unprotect your USB flash drive, click on the ‘Unprotect This USB Drive’ option. And that is
all there is to it. You are done, and you may start editing the contents of the flash drive. You
can password protect the contents after you are done. - Please note that USB Secure may ask you to replace existing files if it finds files and folders
of similar names that need to be unprotected. If you do get a prompt for replacing existing
files and folders, then simply click on the ‘Replace’ or the ‘Cancel’ button. Based on your
selection, your files and folders will be unprotected. - Furthermore, USB Secure comes with a ‘Master Key’ feature that lets you unprotect your data and
reset your password in case if you have forgotten your password. Click on the ‘Options’ button
placed at the bottom left of the application screen to enable / disable the ‘Master Key’
feature. *
*Please note that this feature currently works in registered versions of USB Secure only.
When you click ‘Options’, you will also see three other options that are listed below:
- Enable Autoplay for This Device
- Show Autoplay list containing USB Secure
- Execute USB Secure on Autoplay
All of the above options are activated by default. However, you can enable/disable these options by checking /
un-checking the boxes and clicking on the ‘Done’ button to set the new preferences.
Conclusion:
USB drives are always in our possession; cloud storage may give access to multiple users
USB drives have various ranges of storage ranging from 2-64 GB while cloud have a limited amount storage available,
which varies with each cloud service
USB drives do not come with self-security. Cloud services have the basic idea of login credentials
Only you have access to your drive. People who you do not know may access cloud accounts
Threats like malware, spyware etc. persist alongside USB drives but does not exist in cloud services
