Cloud security involves protecting data stored in the cloud through various strategies and technologies to prevent unauthorized access and data breaches. It follows a shared responsibility model, with both cloud service providers and customers playing roles in securing data. Data is stored in massive data centers using virtualization technologies, and various storage devices, including HDDs, SSDs, and object storage, are employed. Encryption, access control, security patching, and disaster recovery are critical components of cloud security.
Understanding Cloud Security

Cloud security refers to the measures and protocols put in place to protect data stored in the cloud. It encompasses various strategies, technologies, and best practices designed to safeguard data from unauthorized access, data breaches, and other threats.
One of the essential concepts in cloud security is the shared responsibility model. This model outlines that the responsibility for securing data in the cloud is a shared effort between the cloud service provider (CSP) and the customer. While the CSP is responsible for securing the underlying infrastructure, customers are accountable for securing their data and access.
How Data is Stored in the Cloud?
- Data Centers
At the core of cloud storage are massive data centers operated by cloud service providers (CSPs). These data centers consist of vast arrays of servers, storage devices, and networking equipment. Data centers are strategically located across the globe to ensure high availability and redundancy.
- Virtualization
Cloud storage relies heavily on virtualization technologies. Data is not stored on specific physical servers but is instead distributed across a pool of servers and storage resources. Virtualization allows for efficient resource allocation, scalability, and load balancing.
- Storage Devices
Within data centers, various types of storage devices are used to store data. These include hard disk drives (HDDs), solid-state drives (SSDs), and, increasingly, technologies like non-volatile memory express (NVMe) SSDs for high-performance storage. Redundancy is a key aspect, with data often stored on multiple devices to ensure data durability.
- Storage Tiers
Cloud providers often offer multiple storage tiers to cater to different use cases. These tiers may include:
- Standard Storage: Suitable for general-purpose storage needs.
- Cold Storage: Optimized for infrequently accessed data with lower cost but longer retrieval times.
- Hot Storage: Designed for frequently accessed data with low-latency requirements.
Users can choose the appropriate storage tier based on their data access patterns and budget.
- Object Storage
Many cloud providers use object storage as the primary method for storing data. Object storage stores data as objects, each associated with a unique identifier and metadata. This method is highly scalable and well-suited for unstructured data like images, videos, and documents.
- File Storage
Cloud services also offer file storage solutions that mimic traditional file systems. Users can store and organize files in a hierarchical structure, making it suitable for shared data and application files.
- Block Storage
Block storage is another storage type provided by cloud services. It divides data into fixed-size blocks and is often used for virtual machines and databases that require low-level disk access.
Is Cloud Storage Really Secure?

-
Encryption
Encryption is the cornerstone of cloud security. It involves encoding data in such a way that only authorized parties can access it. Most reputable cloud providers employ robust encryption techniques to protect data both in transit and at rest.
- Data in Transit: When data is transferred to and from the cloud, it is typically encrypted using protocols like SSL/TLS. This ensures that even if intercepted, the data remains unreadable.
- Data at Rest: Cloud providers employ advanced encryption algorithms to safeguard data stored on their servers. This means that even if a breach occurs, the data remains encrypted and inaccessible.
-
Access Control
Controlling who can access your data is paramount. Cloud services offer robust access control mechanisms that allow you to define who can view, edit, or delete your data.
- User Authentication: Multi-factor authentication (MFA) and strong password policies are often employed to ensure that only authorized users can access data.
- Role-Based Access: Cloud platforms offer role-based access control, enabling organizations to define specific permissions for different users or groups. This minimizes the risk of unauthorized access.
-
Security Patching
Cloud providers are responsible for keeping their infrastructure secure. This includes regularly updating and patching their systems to defend against emerging threats.
- Timely Updates: Providers often release security patches promptly to address vulnerabilities. This reduces the window of opportunity for attackers.
-
Disaster Recovery and Redundancy
Cloud providers invest heavily in disaster recovery and redundancy. They ensure that even in the face of hardware failures or natural disasters, your data remains accessible and intact.
- Data Replication: Cloud providers often replicate data across multiple data centers, ensuring redundancy and data availability.
Factors Making Your Data Vulnerable in the Cloud:
Weak Passwords
One of the most common and avoidable vulnerabilities is the use of weak or easily guessable passwords. When users choose passwords that are simple or reused across multiple accounts, they become easy targets for cybercriminals. Brute-force attacks and password-cracking techniques can compromise cloud accounts with weak authentication credentials.
Inadequate Access Controls
Misconfigured access controls within cloud environments can lead to data exposure. When users have excessive privileges or permissions that are not properly defined, unauthorized individuals may gain access to sensitive information. This risk is particularly significant in shared cloud environments.
Unpatched or Outdated Software
- Failure to apply regular updates and patches to your cloud infrastructure and applications can create vulnerabilities that hackers can exploit. Security vulnerabilities are frequently discovered in software, and timely updates are essential for addressing these weaknesses.
Lack of Encryption
Data encryption is a fundamental component of cloud security. Failing to encrypt data both in transit and at rest can leave it vulnerable to interception or theft. Encryption should be implemented consistently to protect sensitive information.
Insider Threats
Insider threats can be just as detrimental as external threats. Employees or individuals with access to your cloud resources may misuse their privileges intentionally or inadvertently. Proper employee training and monitoring are essential to mitigate this risk.
Data Loss Prevention (DLP) Gaps
Not having a robust DLP strategy in place can expose your data to unauthorized sharing or leakage. DLP solutions help monitor and control the movement of sensitive data within your cloud environment, preventing unintended data exposure.
Third-Party Vulnerabilities
When you rely on third-party applications or services within your cloud environment, you inherit their security risks. If these third-party services have vulnerabilities, your data may be at risk. Regularly assess and vet third-party providers for security concerns.
Inadequate Backup and Disaster Recovery
Failure to implement proper backup and disaster recovery plans can result in data loss. In the event of a data breach, natural disaster, or hardware failure, having reliable backup and recovery procedures is crucial for data preservation.
The Importance of Cloud Security:
1. Protection of Sensitive Data
Cloud security matters because it protects sensitive data. Whether it’s personal information, financial records, intellectual property, or confidential business data, organizations and individuals entrust cloud providers with their most valuable assets. Ensuring the security of this data is imperative to prevent data breaches and unauthorized access.
2. Prevention of Data Breaches
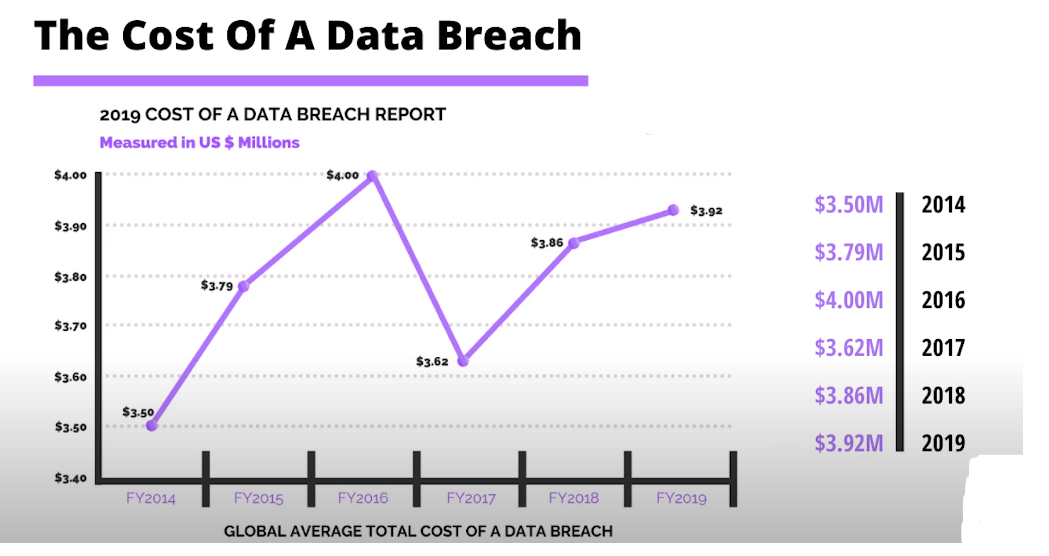
Data breaches can have devastating consequences, both financially and reputationally. Cloud security measures, such as encryption, access controls, and intrusion detection systems, are essential in preventing data breaches and minimizing the impact if a breach does occur.
3. Preserving Customer Trust
Customers and users expect their data to be handled with care and security. A data breach can erode trust and damage a company’s reputation. Demonstrating a commitment to cloud security not only protects your business but also fosters trust among your customer base.
4. Preventing Downtime and Loss of Revenue
Downtime caused by security incidents can result in significant financial losses. Cloud security measures, including redundancy and failover mechanisms, help minimize downtime and ensure uninterrupted access to services and data.
Insider threats, whether intentional or unintentional, are a real concern. Cloud security helps organizations monitor user activities, detect anomalies, and prevent unauthorized actions by employees or other trusted individuals.
6. Adapting to Evolving Threats
The threat landscape is constantly evolving. Cybercriminals continually develop new techniques and exploit vulnerabilities. Cloud security is a dynamic field that adapts to emerging threats, ensuring that defenses remain effective over time.
Conclusion:
Cloud security is not merely an option but a fundamental necessity in today’s digital landscape. It serves as the shield that protects sensitive data from unauthorized access, data breaches, and evolving cyber threats. By adhering to robust security practices such as encryption, access controls, and timely software patching, cloud providers and users alike can fortify their defenses against vulnerabilities and insider risks. Furthermore, cloud security is pivotal in preserving customer trust, preventing costly downtime, and adapting to the ever-changing threat landscape.
FAQs:
How has cloud security evolved over time?
In the early days of cloud computing, security concerns were prevalent. However, modern advancements have significantly improved cloud security. Providers now offer enhanced encryption, continuous monitoring, and proactive threat detection.
What are the key security measures in cloud computing?
Key security measures in cloud computing include encryption (both in transit and at rest), multi-factor authentication, regular updates and patch management, and intrusion detection and prevention systems (IDPS).
What is the shared responsibility model in cloud security?
The shared responsibility model stipulates that cloud providers are responsible for securing the infrastructure, while customers must secure their data and access to it. It’s vital to understand and adhere to this model for effective cloud security.
How can I enhance the security of my cloud storage?
To enhance cloud security, use strong and unique passwords, educate your employees about security best practices, conduct regular security audits, and stay informed about the latest security advancements and threats.
Are there any tools or services available to help with cloud security?
Yes, many tools and services are available to enhance cloud security. These include cloud access security brokers (CASBs), security information and event management (SIEM) systems, and cloud-native security solutions offered by cloud providers.
