Introduction:
The easiest and quickest way of assembling files into one place is to put them all in a folder. This method even today is the most common way of data storage, which came into existence a long time ago. However, some folders possess data that is of average content while some folders possess data that has data, which is confidential in nature. Hence, for the latter version, password protection is important, as you do not want to risk it.
How to password protect files and folders in windows using Folder Protect?
Folder Protect is a new concept in data security softwares that is designed to provide you with maximum data protection protocols to safeguard and protect all your important and personal files, folders, and drives. It lets you password protect folders and files in a unique way that enables you to make your folders and files accessible yet completely secure from being deleted or modified. This is useful as most times, you may need to give restricted access to your data to others. In such a scenario, you can keep your data from being modified, copied, moved or deleted. Protecting folders and files in this way has solved the associated risks of data sharing by empowering you to customize the different types of security methods for your data.
Folder Protect allows you to password protect files, folders, drives, installed programs and popular extensions with four different levels of security to make your files and folders inaccessible, hidden, delete proof or write protected.
Follow these simple steps to password protect folders and files:
To start protecting folders and files with Folder Protect, follow these steps:
- Download and install it on your computer. Run the program and it will ask you to set and confirm a password.
- IMPORTANT: Make sure to set a strong password which is easy to remember but hard to guess.
- Once you have set and confirmed the password, click on ‘OK’ to log in to the application and then click the ‘Add’ button to add files, folders, drives, program or extensions.
- When you click on the ‘Add’ button, a wizard screen will appear showing you two steps:
- Step 1: Choose Protection Method
- Step 2: Add Items You Wish to Protect
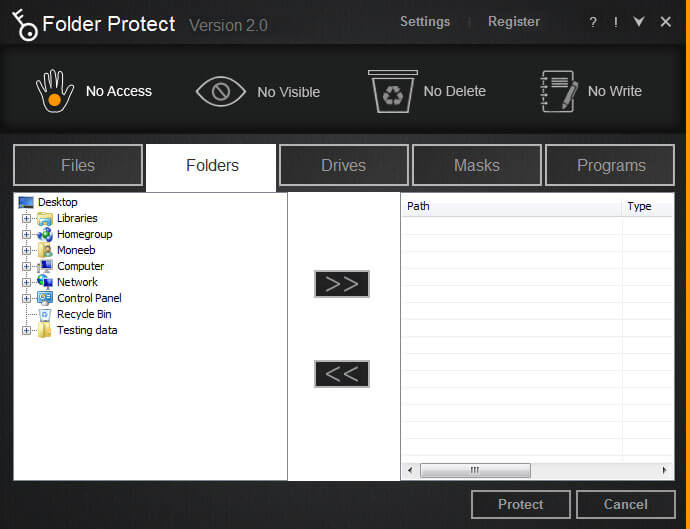
- Both of these steps are self-explanatory. The option titled ‘Choose the Protection Method’ asks you to specify the folders and files to protect. This step additionally features four distinct methods of protection that you can choose according to your needs.
- You may select from No Access, No Visible, No Delete or No Write to make your data completely inaccessible, hidden, delete proof or write proof respectively. The second option titled ‘Add Items You Wish to Protect’ allows you to protect files, folders, drives, masks or programs individually.
- Select the protection type that you want to apply on your folders and files.
- Click the ‘Files’ tab to protect files, and ‘Folders’ tab to protect complete folders. When you click the respective tabs, Folder Protect shows you a folder tree containing all the files and folders so that you can choose which file or folder you want to protect.
- Select the files and folders and add them to your locking list by using the ‘Add’ button. Drag and drop is also supported.
- When you’re done with the selection, click the ‘Protect’ button. Once you click the ‘Protect’ button, you’ll be able to see the list of your protected items, from where you can easily manage your protected items.
- With Folder Protect, you can password protect folders and files from being seen, read, or modified. With support for all variants of Windows OS including Windows 11, Windows 10, Windows 8, Windows 7, Vista, XP, Server 2008, and Server 2003, the protection for your confidential files is comprehensive.
Benefits of folder protect:
Auto protection:
When you stay in an idle state for a certain period, the protection is activated on its own to eliminate any such threat.
Dual access:
Protection can be done in two ways such as ‘deny access’ and ‘prompt password’. The former option lets you make the executable inaccessible. The latter option simply lets you access a particular executable.
