Folder Lock, developed by Newsoftwares.net, provides a final layer of security by allowing you to password-protect the uninstallation process itself. This feature is crucial for preventing unauthorized removal of the software, ensuring that your protected files and folders cannot be exposed by simply uninstalling the application. Setting an uninstaller password gives you complete control over who can remove the software from your system.
Steps to Set an Uninstaller Password for Folder Lock
Follow these simple steps to set a password for uninstalling Folder Lock:
Step 1: Launch Folder Lock and Sign In
- Launch the Folder Lock application on your computer.

- Sign in to your account using your email and password.
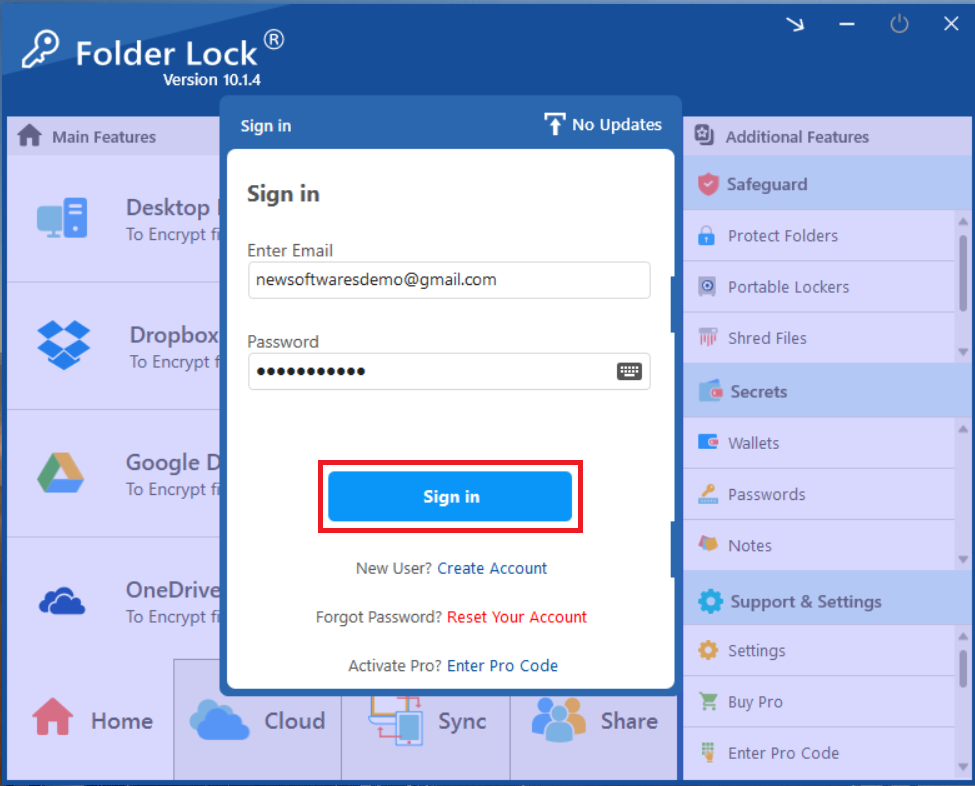
Step 2: Go to "Settings"
- Once logged in, navigate to the "Support & Settings" section in the bottom-right corner of the main window.
- Click on "Settings."
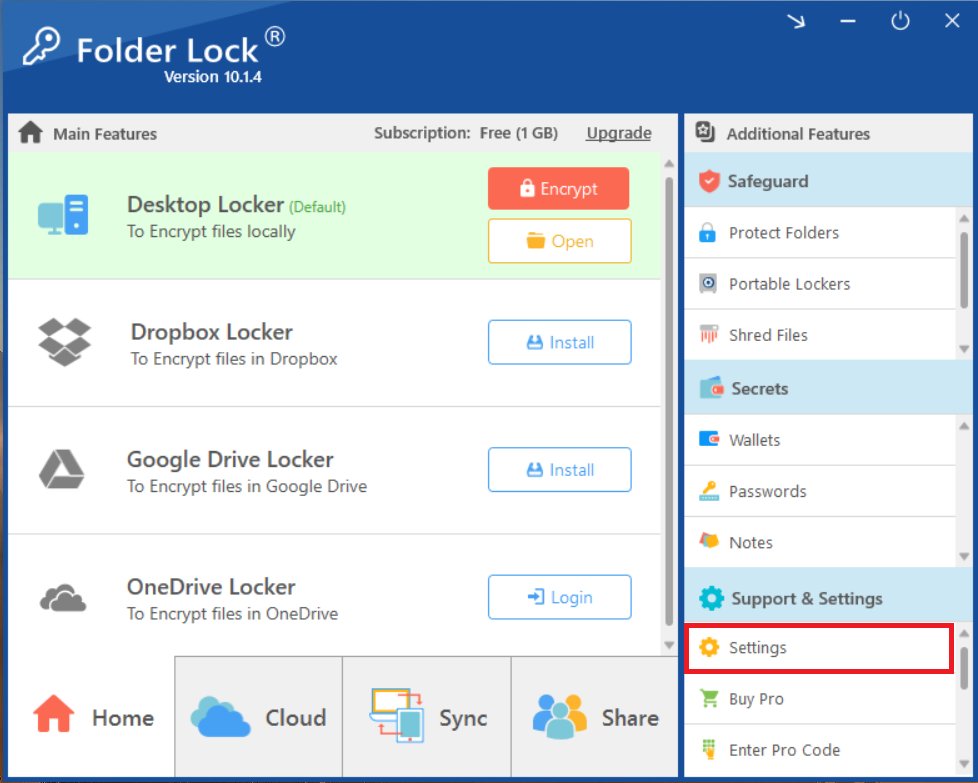
Step 3: Go to "Security & Privacy"
- In the Settings menu, click on "Security & Privacy" in the left-hand menu. This section contains the uninstaller password option.
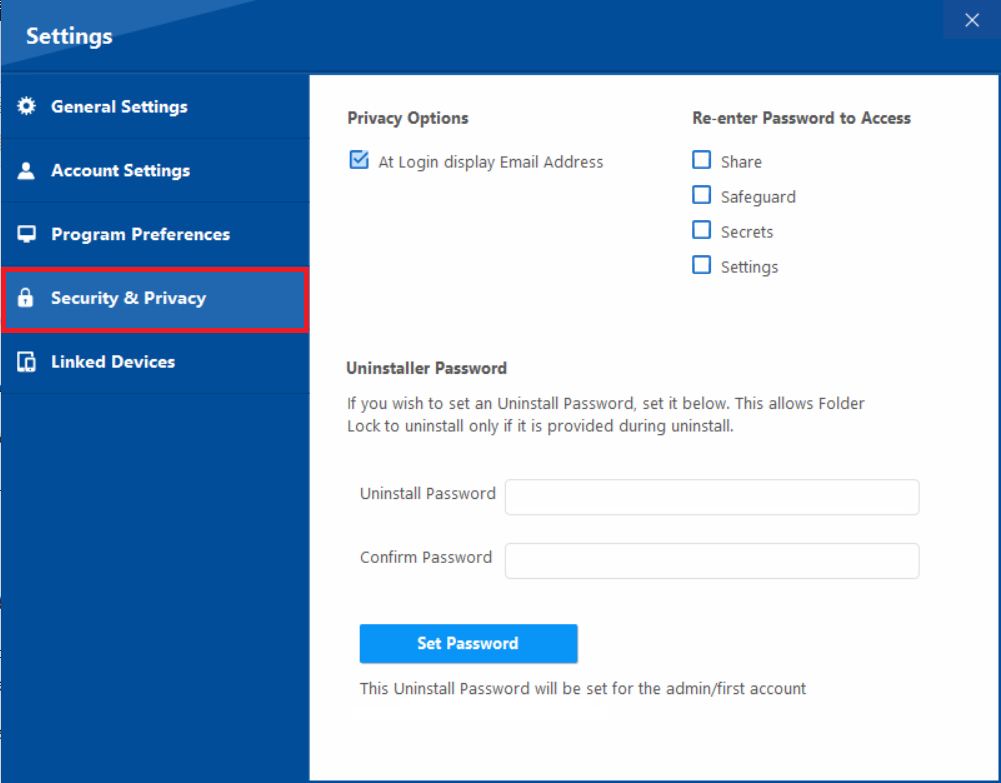
Step 4: Enter and Confirm the Password
- On the right side of the screen, look for the "Uninstaller Password" section.
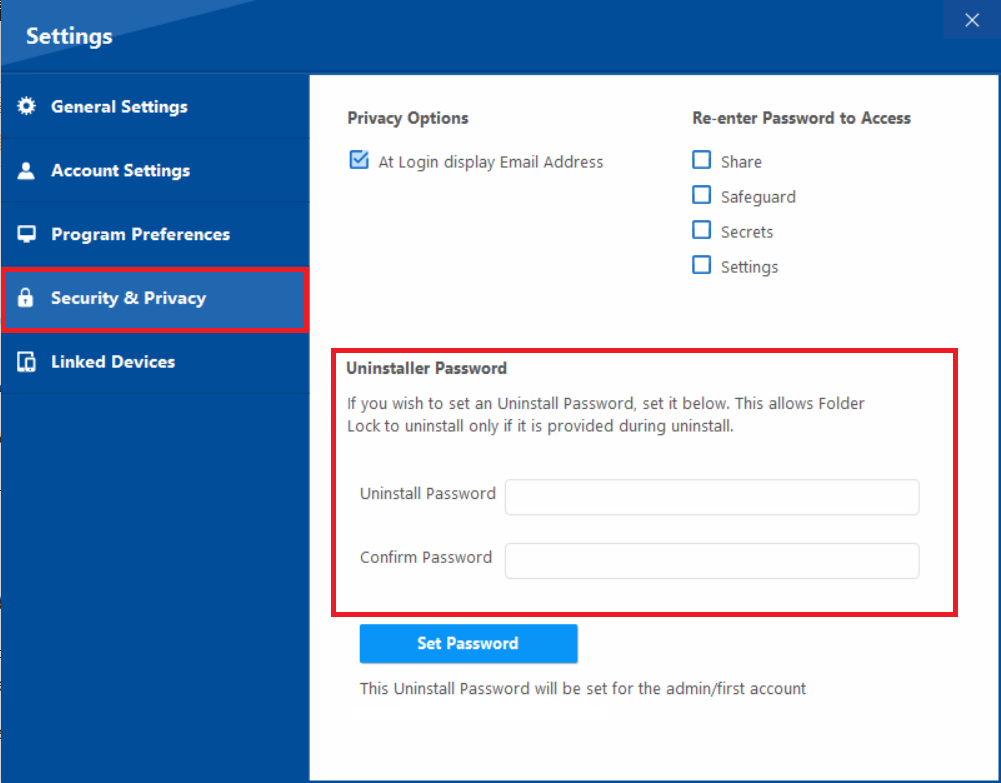
- Enter your desired strong password in the "Uninstaller Password" and confirm password field.
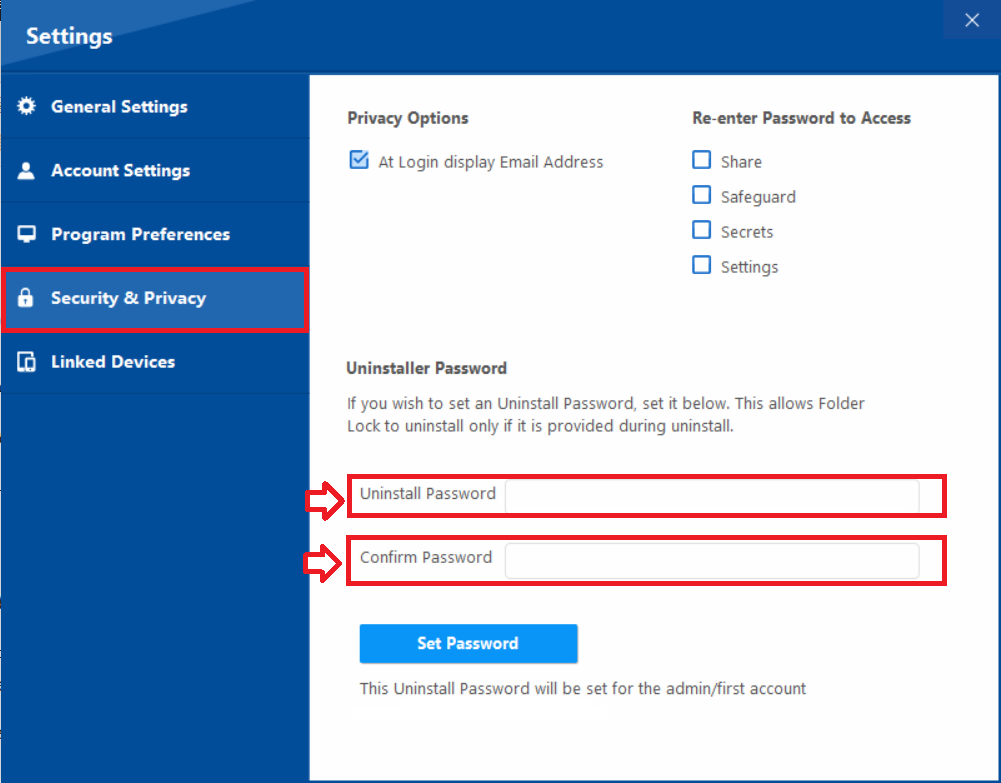
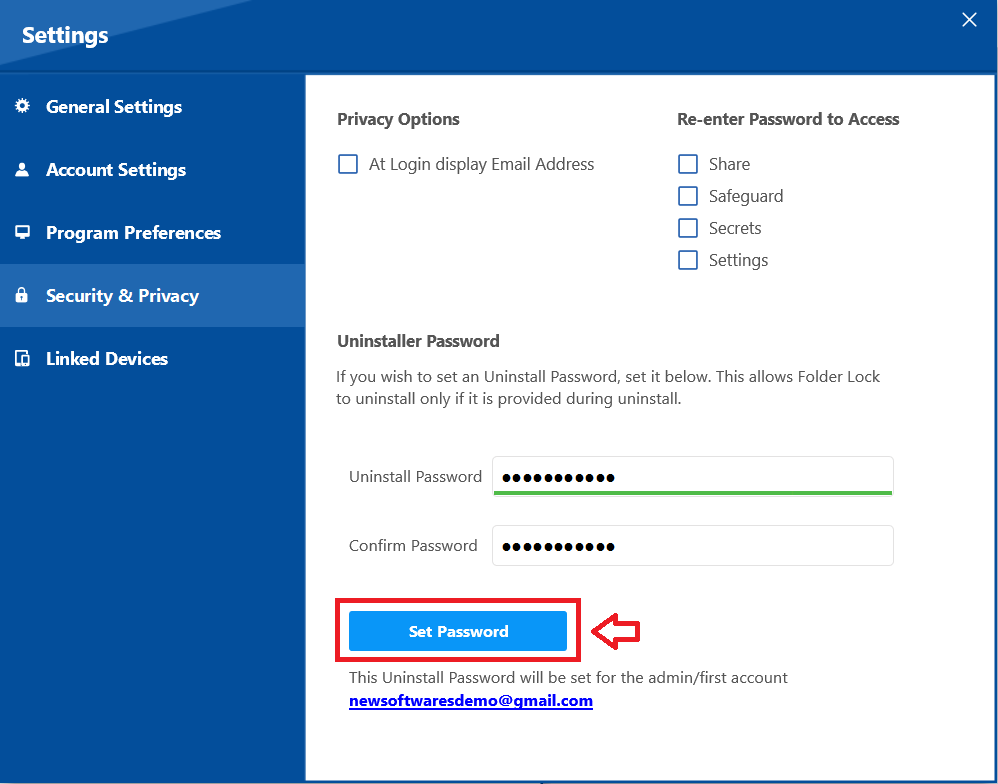
Step 5: Set the Password
- Click the blue "Set Password" button to save the uninstaller password to your account.
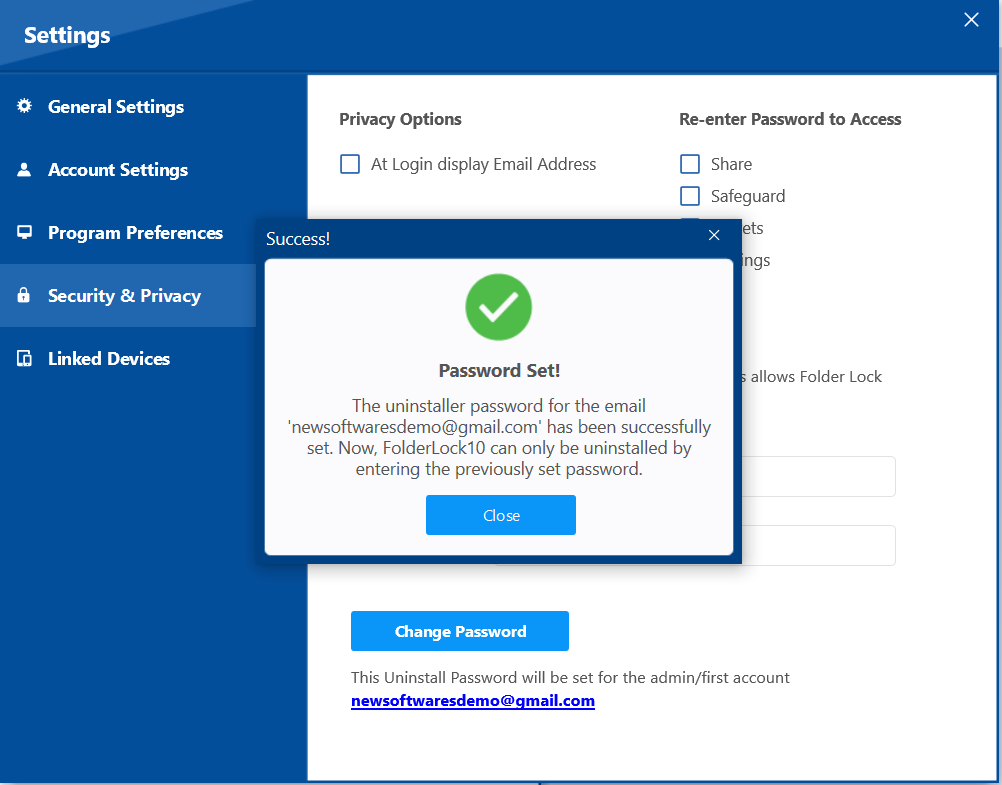
- "A pop-up will confirm that the password has been successfully set, and the uninstaller is now protected
By setting an uninstaller password, you have added a crucial final layer of defense for your data. This simple yet powerful step prevents anyone from bypassing the application's security by simply removing it. You can now rest assured that your confidential files and folders are protected by a robust security measure that controls not only access to your data but also the integrity of the application itself.
