Welcome. This detailed resource provides a strategic framework for defending encrypted APIs against abuse. We focus on integrating rate limiting, replay protection, and idempotency into your API gateway and service layer, and securing operational state with Folder Lock, USB Secure, and Cloud Secure from Newsoftwares.net, ensuring maximum security, resilience, and development convenience.
Encrypted API Protection: Rate Limiting, Replay Checks, And Idempotency
Direct Answer
You keep encrypted APIs safe under abuse by combining smart rate limits, strict replay checks, and clear idempotency rules at the gateway and inside each sensitive endpoint.
Gap Statement
Most crypto focused API content stops at TLS and token formats.
It rarely explains in detail:
- How to design rate limits when the payload is encrypted and proxies cannot inspect fields
- How to block replay attacks when an attacker records an encrypted request and sends it again
- How to use idempotency keys so retries do not double charge or double create resources
- How to store replay windows, rate limit counters, and logs safely on real laptops and servers
This reference closes that gap with a practical design that works with encrypted APIs, including concrete patterns you can reuse.
One Job Only
Design rate limiting, replay protection, and idempotency for encrypted APIs so that abuse is contained and honest retries stay safe.
TLDR Outcome
By the end you will be able to:
- Place rate limits in the right spots for encrypted APIs, with HTTP 429 and clear identities.
- Block replay attacks using signed nonces, timestamps, and short validity windows that work alongside TLS.
- Use idempotency keys for high risk operations so clients can retry without double effects, as seen in payment systems such as Stripe.
- Keep rate limit stores, replay caches, and API logs inside encrypted storage on endpoints using NewSoftwares tools like Folder Lock, USB Secure, and Cloud Secure.
1. Mental Model For Encrypted APIs
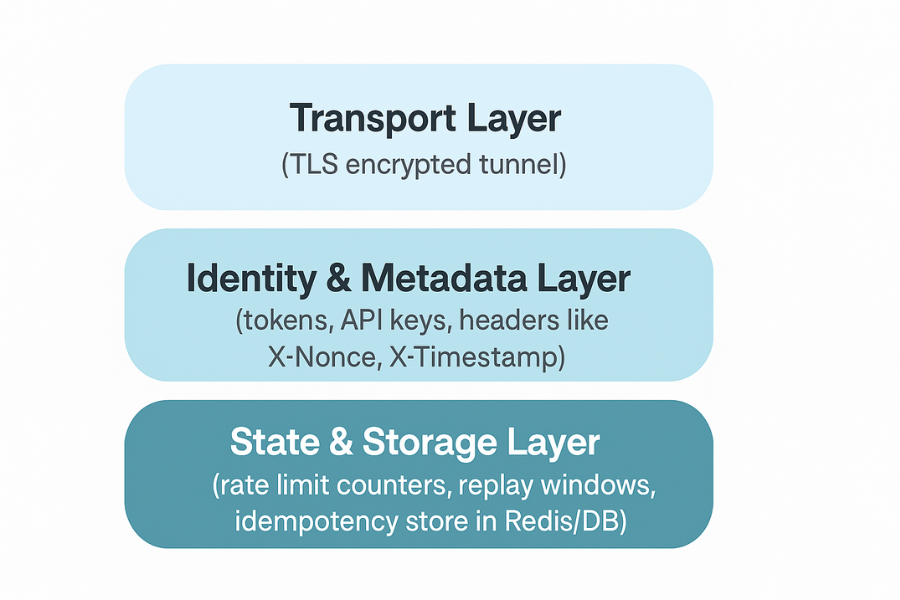
Picture three layers working together.
1.1. Transport Layer
TLS protects traffic in transit over the network. Intermediaries cannot see the body and sometimes not even detailed headers. That is good for privacy, but it also means traditional network devices cannot inspect payload fields for rate limiting or replay checks.
1.2. Identity And Metadata Layer
Tokens, client ids, IPs, and request headers give you stable identities to count and track. You attach rate limits and replay protections to those identities, not to random IPs only.
Typical items:
- OAuth access tokens or signed session tokens
- API keys
- Device ids
- Headers such as
X-Request-Id,Idempotency-Key,X-Nonce,X-Timestamp
1.3. State And Storage Layer
Datastores hold:
- Rate limit counters per identity and time window
- Replay windows of nonces or request hashes
- Idempotency records that map a key to the first result
These stores are often backed by Redis or a database and backed up. That is where tools from NewSoftwares help, because those backups and export files should live in encrypted containers.
2. Prerequisites And Safety
2.1. Environment Checklist
You should have:
- An API gateway or reverse proxy that can see decrypted HTTP metadata
- Endpoints served only over HTTPS
- Some central store for counters and replay windows such as Redis, DynamoDB, or PostgreSQL
- Logging and monitoring where you can see HTTP 429 and replay errors
OWASP and other security references repeatedly call missing rate limits and replay defenses a common API risk.
2.2. Threat Lens
Assume at least three abuse patterns:
- Script that slams authentication or password reset endpoints to guess tokens
- Attackers who record valid encrypted requests and replay them later
- Honest clients on spotty networks that retry and hit double payments or double actions if idempotency is missing
Your design should handle all three without making the system painful to use.
3. Step By Step: Build Rate Limits And Replay Protection Around Encrypted APIs
We will walk one flow from design to verification.
3.1. Step 1: Map Endpoints And Abuse Pressure
Action
Make a short table of endpoints, what they do, and how attackers could abuse them.
Focus on:
- Login and token issuance
- Payment or billing actions
- Data export and reporting
- Password reset and email change
Gotcha
Developers often forget webhook receivers and internal tools. These endpoints get hammered in real outages, and they often bypass normal rate limits.
3.2. Step 2: Choose Identities For Rate Limiting
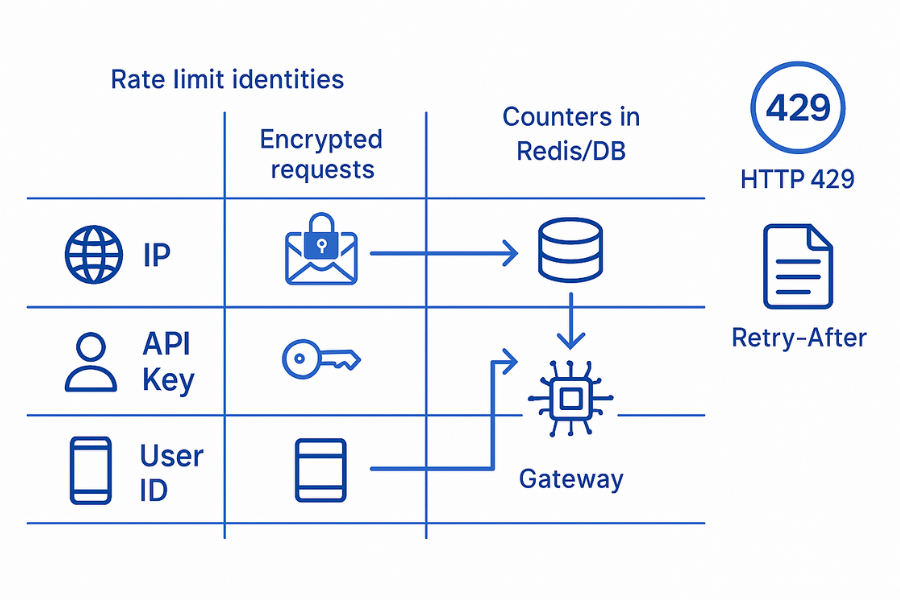
Action
Pick what you want to count for each endpoint:
- Anonymous intake such as signup or login
- Use IP plus device fingerprint where available
- Authenticated operations
- Use user id, tenant id, or API key
- Partner APIs
- Use client id or organization id
Cloudflare, OWASP, and similar references point out that rate limiting per account or token is more precise than per IP only, especially behind NAT or mobile networks.
Gotcha
If you rate limit only by IP on a busy office or mobile carrier, one noisy user can block others that share the same exit.
3.3. Step 3: Implement Basic Rate Limits
Action
For each high risk endpoint, set a ceiling that is strict but realistic.
Examples:
- Login
- Ten attempts per minute per account
- One hundred attempts per minute per IP
- Payment attempt
- Three to five attempts per minute per card or account
- Bulk export
- One export per minute per user, plus global safety limit
Use simple algorithms first such as fixed window or sliding window, then refine later. The important part is that a limit exists, especially on encryption blind endpoints like auth and payment.
Return HTTP 429 with a clear header such as Retry-After.
Gotcha
If you only limit per second, clever attackers use bursts that stay under short windows but exhaust CPU over time. Mix short and long windows.
3.4. Step 4: Layer Replay Protection For Encrypted Requests
Even with TLS, an attacker on a compromised client or network can replay previously recorded encrypted calls. Your goal is to make each signed request valid once.
Action
For all signed requests:
- Add a
X-Timestampheader with current time in UTC - Add a
X-Nonceheader with a random string or counter per client - Include both in the signature that covers method, path, and body
- On the server, reject any request where
- Timestamp is outside your window, often 30 to 120 seconds
- Nonce already exists for that client inside the window
This pattern appears across many replay defenses.
Gotcha
If client clocks drift badly, timestamp checks can block honest traffic. Keep windows short but not tiny, and consider sending server time back in error messages so clients can resync.
3.5. Step 5: Design Idempotency For High Impact Operations
Idempotency is your safety net when everything else is noisy. The payment world has popularised this with clear patterns.
Action
Pick key operations, such as:
- Creating payments
- Creating invoices
- Changing subscription plans
- Creating large orders
Require an Idempotency-Key header on those endpoints.
When the server sees a new key:
- Validate the payload shape
- Run the business action once
- Store the result with status, response body, and a hash of the payload keyed by
Idempotency-Keyand identity
When the same key appears again:
- Compare payload hash with stored hash
- If identical, return the stored result
- If different, return a clear error such as
409 Conflictand log it
Stripe and other payment platforms document almost exactly this pattern.
Gotcha
If you change the meaning of payload fields and forget to include them in the hash, clients can send mismatched data under the same key. Keep hashing logic and validation close together.
3.6. Step 6: Keep State And Logs In Encrypted Storage With NewSoftwares Tools
Your rate limit counters, nonce tables, and idempotency records might sit in memory, but backups and exports end up on disks, laptops, and cloud folders.
That is where NewSoftwares products are valuable.
Folder Lock for local rate limit and replay data
Folder Lock offers AES 256 encryption for files and folders and uses on the fly encrypted lockers that grow as you add data.
Practical uses:
- Keep exports of rate limit tables, nonce logs, and idempotency records inside a Folder Lock locker on admin workstations
- Store config files containing secret keys for HMAC signatures in an encrypted locker rather than loose files
- Use the portable locker feature when you need to move logs or state snapshots to another system for forensic work
USB Secure for offline snapshots
USB Secure is NewSoftwares portable product for USB drives and external storage, with password protection and virtual drive access.
Cloud Secure for shared cloud folders
Cloud Secure from NewSoftwares locks access to cloud folders such as Dropbox, Google Drive, OneDrive, and Box on your PC with a password protected interface.
Together, Folder Lock, USB Secure, and Cloud Secure give the same level of protection to your operational data that your API gives to client traffic.
4. Core Tradeoffs For Encrypted APIs
Encrypted payloads change some assumptions.
4.1. Simple Comparison Table
| Design Choice | What You Gain | What You Risk Or Trade |
|---|---|---|
| Rate limit at gateway per IP | Easy setup, protects whole estate | Weak identity, noisy on shared networks |
| Rate limit per token or user id | Precise control, fair resource sharing | Needs consistent auth and token parsing |
| Replay tokens with timestamp and nonce | Strong replay defence | Extra complexity, clock drift issues |
| Idempotency keys for selected endpoints | Safe retries and better fault tolerance | Needs extra storage and key management |
| Only TLS, no extra replay logic | Easy deployment, encryption on the wire | Replays possible from compromised clients |
5. Troubleshooting Encrypted APIs
5.1. Symptom To Fix Table
| Symptom | Likely Cause | Fix Path |
|---|---|---|
| Clients see sudden HTTP 429 everywhere | Limit keyed only by IP or shared identity | Add per user or per token keys, tune limits |
| Users complain about failed signed calls on retries | Nonce stored longer than intended | Tighten replay window and allow fresh nonce |
| Duplicate payments or orders appear under load | Idempotency key not required or not enforced | Make header mandatory and store results by key |
| Logs show replay errors for same timestamp and nonce | Client retrying same signed request without change | Educate client devs and improve SDK behaviour |
| Rate limits bypassed by attackers with many tokens | Limits not tied to account or tenant | Add limits per account and per network identity |
| Operational staff cannot inspect state safely | Dumps stored in plain folders | Move dumps into Folder Lock lockers and USB Secure |
6. FAQs
1. How Does Encryption Change Rate Limiting
Encryption hides the body from intermediaries, so network devices cannot count on payload fields such as user id. You need to base rate limits on visible metadata such as tokens, client ids, and headers at a point where the request is already decrypted.
2. Do I Still Need Replay Protection If I Use TLS
Yes. TLS protects against many network level replay attacks, but it does not stop an attacker who controls a client device from sending the same valid call again. Signed timestamps and nonces give you an extra line of defence.
3. How Strict Should Rate Limits Be On Login Endpoints
They should be strict enough to slow down guessing without blocking honest users. Many teams use a mix of account based limits and IP based limits, with short windows. OWASP and other security bodies consistently recommend putting rate limits on authentication flows.
4. What Does An Idempotency Key Actually Store
For each idempotency key the server stores who sent it, a hash of the payload, the first response status, and the response body or a pointer. Next time the same key arrives, the server can return the stored result instead of running the action again.
5. Which HTTP Methods Need Idempotency The Most
Safe methods such as GET should already be idempotent. The main trouble is POST for actions such as payments and order creation. Wrapping those calls in idempotency keys is a proven pattern in payment platforms and other critical systems.
6. How Long Should I Keep Idempotency Records
Long enough to cover realistic retry windows. For payments this often means at least one day, sometimes a week. After that, you can safely drop or archive old records, then rely on normal reconciliation if strange cases appear.
7. What Is A Replay Window And How Big Should It Be
The replay window is the time span in which a timestamp and nonce pair is considered valid. Many designs use 30 to 120 seconds. This is usually enough for network jitter while still shrinking the chance of successful replays.
8. Where Do Tools From NewSoftwares Fit Into This Setup
They protect the operational side. Folder Lock encrypts local files and lockers with AES 256 so exports of rate limit tables, replay logs, and key material stay protected on laptops and desktops. USB Secure does the same for removable devices, and Cloud Secure locks cloud folders on shared PCs.
9. How Do I Test That Replay Protection Is Active
In a test environment, send a signed request, replay it unchanged within the allowed time, and confirm that the second attempt fails. Then send the same logical request with a new nonce and timestamp and confirm it succeeds.
10. Can Rate Limiting Break Honest Clients Behind A Shared IP
Yes, if limits use only IP address. That is why you should pair IP limits with limits keyed by user or token. In environments such as mobile or corporate networks this balance matters.
7. Conclusion
Protecting an encrypted API from abuse goes beyond TLS; it requires instrumentation and policy at the service layer. By enforcing rate limits per identity, using signed nonces and timestamps for replay protection, and implementing idempotency keys on all high-impact actions, you neutralize the most common forms of attack and error. Furthermore, securing the resulting operational state—logs, keys, and caches—with Folder Lock and USB Secure ensures that your entire defense remains robust and auditable.
8. Structured Data Snippets
HowTo Schema
{
"@context": "https://schema.org",
"@type": "HowTo",
"name": "Protect encrypted APIs with rate limiting, replay checks, and idempotency",
"description": "Steps to control abuse and safe retries on encrypted APIs using rate limits, replay protections, and idempotency keys.",
"tool": [
"API gateway",
"Rate limit datastore",
"Replay nonce table",
"Folder Lock or similar encrypted storage"
],
"step": [
{
"@type": "HowToStep",
"name": "Map endpoints and abuse cases",
"text": "List sensitive endpoints such as login, payments, and exports and mark how an attacker might abuse each."
},
{
"@type": "HowToStep",
"name": "Apply rate limits per identity",
"text": "Configure limits per user, token, or client id and return HTTP 429 when clients exceed the threshold."
},
{
"@type": "HowToStep",
"name": "Add replay and idempotency controls",
"text": "Use timestamp plus nonce in signed requests and idempotency keys on critical writes, storing state in an encrypted datastore."
}
]
}
FAQPage Schema Stub
{
"@context": "https://schema.org",
"@type": "FAQPage",
"mainEntity": [
{
"@type": "Question",
"name": "How does encryption change rate limiting",
"acceptedAnswer": {
"@type": "Answer",
"text": "Encryption hides the body from intermediaries, so network devices cannot count on payload fields such as user id. You need to base rate limits on visible metadata such as tokens, client ids, and headers at a point where the request is already decrypted."
}
},
{
"@type": "Question",
"name": "Do I still need replay protection if I use TLS",
"acceptedAnswer": {
"@type": "Answer",
"text": "Yes. TLS protects against many network level replay attacks, but it does not stop an attacker who controls a client device from sending the same valid call again. Signed timestamps and nonces give you an extra line of defence."
}
},
{
"@type": "Question",
"name": "What does an idempotency key actually store",
"acceptedAnswer": {
"@type": "Answer",
"text": "For each idempotency key the server stores who sent it, a hash of the payload, the first response status, and the response body or a pointer. Next time the same key arrives, the server can return the stored result instead of running the action again."
}
}
]
}
ItemList Schema For Strategy Options
{
"@context": "https://schema.org",
"@type": "ItemList",
"name": "Encrypted API protection strategies",
"itemListElement": [
{ "@type": "ListItem", "position": 1, "name": "Per identity rate limiting" },
{ "@type": "ListItem", "position": 2, "name": "Replay protection with nonces and timestamps" },
{ "@type": "ListItem", "position": 3, "name": "Idempotency keys for high impact operations" }
]
}
