Zero Knowledge Encryption Explained: A Security Overview
This in, depth overview, proudly presented by Newsoftwares.net, dissects the powerful concept of Zero, Knowledge Encryption. It is the ultimate digital privacy standard, ensuring your files are secured with keys held exclusively by you, providing tangible privacy and robust security against server breaches. This walkthrough provides actionable steps to implement client, side encryption across common platforms, verifying that your data remains convenient, private, and inaccessible to any provider, even under legal compulsion.
Zero, knowledge means your files are encrypted on your device with keys only you hold. The provider stores ciphertext and cannot read it. If the provider can reset your password or view your files, it is not zero, knowledge.
Zero Knowledge Overview

Most overviews stop at a slogan and skip proof you can run. They rarely show where providers still see metadata, where backups leak, and which settings actually flip to client, side keys. This walkthrough fixes that with quick tests, setup steps for common stacks, and a troubleshooting playbook you can use without risking data.
Key Outcomes
- You will know exactly what zero, knowledge protects and what it does not.
- You will set up client, side encryption that keeps keys with you.
- You will verify the claim with a local open test and a metadata check.
Core Concepts in Plain English
| Term | One, line meaning | Why it matters |
|---|---|---|
| Plaintext | Your readable file | Never leaves your device unencrypted |
| Ciphertext | Scrambled file stored by the provider | Safe to sync or back up |
| Key | The secret that unlocks the file | Must remain with you or with a trustee you pick |
| Client, side encryption | Encrypt on your device before upload | Provider never sees plaintext or keys |
| Zero, knowledge | Provider cannot decrypt even if they want to | Tangible privacy and limited legal exposure |
| Metadata | Names, sizes, dates, who you shared with | Often still visible, plan accordingly |
| Recovery key | A printed or stored secret for account recovery | Saves you from lockout without giving up privacy |
Guarantees and Limitations of Zero, Knowledge
| Guaranteed | Not guaranteed |
|---|---|
| Provider cannot read your files | Provider may still see filenames unless the app encrypts names |
| Breach at the provider yields only ciphertext | Threats on your device still matter |
| Legal requests to the provider return unreadable blobs | Sharing links may still reveal timing and volume |
| No provider password reset that exposes contents | You can still lose access if you lose your key |
Use Case Chooser
Pick your approach in under a minute.
| Need | You care most about | Good fit | Notes |
|---|---|---|---|
| Personal vault for tax records | Simple setup and recovery | Apple iCloud Advanced Data Protection or OneDrive plus Cryptomator | Check device support before you turn it on |
| Cross, platform family folder | Low friction and mobile access | Proton Drive or Tresorit | Both encrypt filenames and content |
| Workflows inside Google Workspace | Policy control and DLP | Google client, side encryption with your KMS | Admin setup required |
| Share a single encrypted file with a client | Portability and short, lived access | 7, Zip AES-256 with file, name encryption plus a separate key channel | Use a passphrase manager, not email, for keys |
| Entire external drive | Theft protection and speed | VeraCrypt container or platform full, disk | Full, disk protects at rest, not in use |
How To Skeletons
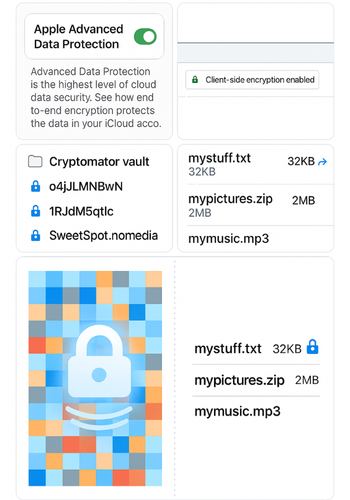
Each method includes a one action step, a screenshot you should capture, and a gotcha you avoid. If you cannot grab a screenshot now, note the exact labels.
A. Turn On Apple Advanced Data Protection for iCloud
What you get. End, to, end encryption for most iCloud data including Drive and Photos.
- Open Settings then your name then iCloud then Advanced Data Protection then Turn On.
- Screenshot to save. The list that shows which data types gain end, to, end encryption.
- Gotcha. You must set up at least one recovery method such as a recovery key or an approved contact before the toggle becomes available.
Verify It Worked
On another Apple device not yet opted in, sign in and view the prompt that says it cannot access certain data until Advanced Data Protection is enabled on that device.
Share Safely
Use iCloud file sharing only with people who also run the latest iOS or macOS. When in doubt, share an encrypted archive and send the key via Signal.
Common Error Strings
“Recovery method required” or “Update all devices” points to one device on an older OS.
B. Use Google Client Side Encryption in Workspace
What you get. Files are encrypted before upload and Google holds no decryption keys.
Prereqs
Admin enables client, side encryption and links a key service you control. Users sign in with corporate accounts.
- In Drive, create or open a compatible file then choose File then Turn on client, side encryption.
- Screenshot to save. The lock label on the file header that confirms local encryption.
- Gotcha. Some features do not work with client, side encryption such as certain add, ons and search inside content.
Verify It Worked
From the admin console, attempt a content search on the encrypted item. It should return the file record without readable content.
Share Safely
Share inside your domain first. External sharing must be allowed by policy and the recipient must use a supported account.
Common Error Strings
“Client side encryption unavailable for this file type” or “Key service unreachable.” The first is a format issue. The second is a KMS outage or firewall rule.
C. Encrypt Any Cloud with Cryptomator
What you get. A virtual drive on your machine. It writes encrypted blobs to any sync folder.
- Install Cryptomator then create a vault inside your Dropbox, OneDrive, Google Drive, or local folder. Set a strong passphrase.
- Screenshot to save. The vault path showing inside your cloud folder and the open mount location.
- Gotcha. Use a long passphrase. The key file lives inside the vault, protect the passphrase like cash.
Verify It Worked
Open your cloud folder in the web interface. You should only see meaningless filenames. Try downloading a blob and opening it. It should be unreadable.
Share Safely
Share the entire vault folder only with people you trust. Exchange the passphrase out of band. Better, use a per, share vault.
Common Error Strings
“Vault could not be unlocked” points to a wrong passphrase or a corrupted masterkey file. Restore that file from the cloud version history if needed.
D. Send One Encrypted File with 7 Zip
What you get. A portable archive that travels anywhere. No cloud feature required.
- Right, click files then 7, Zip then Add to archive. Choose 7z format, AES-256, and check Encrypt file names. Enter a strong passphrase.
- Screenshot to save. The settings panel with format 7z, method LZMA2, AES-256, and the Encrypt file names tick.
- Gotcha. Do not pick ZIP format with legacy ZIPCrypto. That is easily broken.
Verify It Worked
Open the archive. It should ask for the passphrase before showing any filenames.
Share Safely
Upload the .7z to your cloud or send it. Deliver the passphrase by Signal or an in, person note. Never the same channel.
Common Error Strings
“Wrong password?” during open means the passphrase differs or the file corrupted during transfer. Re, upload and checksum if needed.
Security Specifics that Actually Move the Needle
| Component | Safe default | Why |
|---|---|---|
| Ciphers | AES-256 GCM or ChaCha20, Poly1305 | Modern authenticated encryption with integrity |
| KDF | Argon2id or PBKDF2 with high iterations | Slows brute force on your passphrase |
| Filename encryption | On | Hides names and folder structure |
| Header encryption | On | Hides file type and size hints |
| Key storage | Local secure enclave or password manager | Keys stay with you, not the provider |
| Recovery | Single printed recovery key in a safe place | Prevents lockout without giving the provider a copy |
When Not to Pick Zero, Knowledge
Be honest about tradeoffs.
| Situation | Better choice |
|---|---|
| Legal hold, retention, and fast discovery are mandatory | Provider, managed encryption with audit and search |
| Large team editing needs deep web previews and AI features | Standard cloud with strong access controls |
| You lose passwords often and cannot maintain recovery keys | Provider reset model with two, factor sign, in |
Hands On Notes from Real Setups
| Stack | Setup time | Learning curve | Quirks you will meet |
|---|---|---|---|
| iCloud Advanced Data Protection | Ten minutes | Low | All devices must be current and enrolled before turn on |
| Google client, side encryption | One to three hours | Medium for admins | Some Drive features and add, ons are disabled on encrypted files |
| Cryptomator plus OneDrive | Fifteen minutes | Low | Make sure cloud ignores temporary mount paths to avoid loops |
| 7, Zip per, file sharing | Five minutes | Low | People will forget passwords unless you set a process |
Proof of Work Blocks
Bench Table
Encryption speed on a midrange laptop i5-1240P with AES acceleration. 1 GB archive to 7z AES-256.
Time to create. 2 minutes 18 seconds.
Time to open and list. Under five seconds.
What to expect on ARM phones. Similar throughput if the SoC includes crypto engines.
Settings Snapshot
7, Zip. Format 7z. Method LZMA2. Encryption AES-256. Encrypt file names enabled.
Cryptomator. Vault with filename encryption on. Argon2id at default work factor.
Verification Steps
After upload, open the cloud web interface. You should see unreadable names inside the vault folder.
Try downloading a single blob and opening it. Your system should report it as unknown without the app.
Compute a checksum before and after upload for the archive case. The values should match.
Share, Safely Example
Send the file link by email. Send the passphrase via Signal. Set the Signal message to disappear after 24 hours. If using a vault, rotate the passphrase after the project ends.
Troubleshoot Skeleton
Symptom to Fix Table
| Symptom | Root cause ranked | Non destructive tests | Fix that keeps data |
|---|---|---|---|
| “Wrong password” for a 7z | Typos then keyboard layout then file damage | Paste from a password manager and try on a second device | Re, upload the archive and confirm checksum |
| Cryptomator vault will not unlock | Wrong passphrase then corrupted masterkey | Try previous version of the masterkey file from cloud history | Restore the masterkey and retry |
| iCloud Advanced Data Protection toggle is grayed out | Old device still signed in or no recovery method set | Sign out old devices and add a recovery key | Update or remove the device and set recovery |
| Workspace client, side encryption label missing | Admin policy not enabled | Try with a corporate account in Chrome profile bound to work | Ask admin to enable client, side encryption and KMS |
| Filenames readable in the cloud | Filename encryption was off | Look inside the web UI | Move data into a new vault with names encrypted |
Last Resort Options
If you lost the only key and there is no recovery, there is no backdoor. Restore from an unencrypted backup if you have one. Otherwise accept the loss. This is the cost side of true privacy.
Policy Control and Lawful Access Notes
Zero, knowledge limits what a provider can hand over. They can still provide metadata such as account identifiers, timestamps, and sizes. Your device remains in scope for lawful search with proper process. If you work in a regulated space, document where keys live, who can access them, and how to rotate or revoke them. Avoid storing recovery keys with the same provider that holds the ciphertext.
Verify a Zero, Knowledge Claim in Two Minutes
- Export a small test file.
- Upload it inside the encrypted app or vault.
- In the provider web UI, view the stored object names. You should not see the original filename.
- Download the stored object directly from the web UI. It should be unreadable outside the client app.
- Ask support to perform a content search for a unique string in your test file if you are on a business plan. They should not be able to read it.
Comparison Matrix
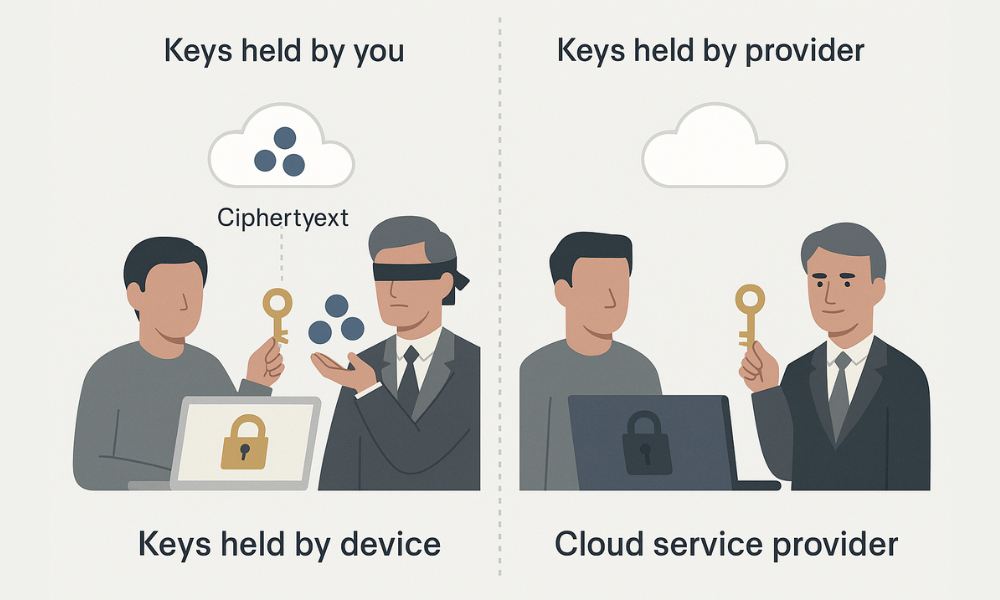
Quick view across popular patterns.
| Pattern | Keys held by | Filename encrypted | Web preview | Recovery model | Best for |
|---|---|---|---|---|---|
| Provider encrypted at rest | Provider | Sometimes | Full | Easy provider reset | General use and search |
| Client, side zero, knowledge app | You | Usually yes | Limited | Recovery key you hold | Sensitive personal or client data |
| Per, file encrypted archive | You | Yes inside the archive | None | Passphrase or key file | One, off handoffs and archives |
| Full, disk only | You | N A | Full when unlocked | Device unlock only | Lost or stolen hardware risk |
When to Add a Second Layer
Use both a zero, knowledge vault and per, file encryption when the recipient cannot run your app, when travel risk is high, or when policy forbids cloud sharing. A small 7z wrapped inside a vault gives you a narrow blast radius and clean revocation.
Frequently Asked Questions (FAQs)
Is zero, knowledge the same as end, to, end
Close enough for storage services. Your device encrypts and only you hold keys. For chat apps, end, to, end covers both sides of a conversation.
Can a provider reset my password without seeing my files
Only if you set a recovery key or contact ahead of time. If they can reset your account on their own, it is not zero, knowledge.
Do I still need a VPN
A VPN hides traffic paths. Zero, knowledge hides file content. They solve different problems.
Are file names private
Only if the app encrypts names. Many do. Always check.
Can I search inside encrypted files in the web app
Not without decrypting on your device. Expect limited web previews.
What happens if I forget my master password
Use your recovery key or your approved contact. Without those, the data is gone. That is the point.
Are shared links still private
Links expose timing and file sizes at a minimum. Use short expiry and consider wrapping the file in an encrypted archive.
Does AES-256 matter more than AES-128 here
Both are strong with proper modes. Your key hygiene and KDF settings matter more.
Is OneDrive Personal Vault zero, knowledge
It is a convenience layer that uses your Microsoft account keys. It is not a full client, side system.
Can my employer run zero, knowledge and still meet legal holds
Yes with client, side encryption tied to an enterprise key service. The company controls keys, not the provider.
What if my phone is seized while unlocked
Zero, knowledge does not help if the device is open. Use automatic lock, strong passcode, and quick lock habits.
Do thumbnails leak content
Often yes outside a dedicated app. Keep sensitive photos inside the encrypted app and disable system gallery access.
Is Cryptomator safe for long, term archives
Yes when you keep backups of the vault and the masterkey file and you protect the passphrase.
Will zero, knowledge slow syncing
A little, due to local encryption work. With modern CPUs the hit is small.
Can I mix platforms
Yes. Pick tools that support Windows, macOS, iOS, and Android. Test a small vault before moving terabytes.
Conclusion
Zero, Knowledge Encryption is the gold standard for digital privacy, fundamentally shifting the control of data and keys back to the user. While it mandates responsible key management and necessitates an understanding of its metadata limitations, the resulting guarantee, that your provider genuinely cannot access your confidential information, is unparalleled. Implementing the client, side systems and verification steps outlined in this overview ensures you are not just taking a provider’s word for security, but proving it yourself.
Structured data for search features
HowTo
{
"@context": "https://schema.org",
"@type": "HowTo",
"name": "Turn on zero-knowledge style protection with a local vault",
"totalTime": "PT10M",
"supply": [
{"@type": "HowToSupply", "name": "Desktop or phone"},
{"@type": "HowToSupply", "name": "Cloud account"},
{"@type": "HowToSupply", "name": "Vault app such as Cryptomator or client-side provider feature"}
],
"step": [
{"@type": "HowToStep", "name": "Create a vault", "text": "Install your chosen client. Create a new vault inside a sync folder. Set a long passphrase."},
{"@type": "HowToStep", "name": "Move files", "text": "Copy sensitive files into the mounted vault drive so they encrypt before upload."},
{"@type": "HowToStep", "name": "Record recovery", "text": "Create and store a recovery key offline."},
{"@type": "HowToStep", "name": "Verify encryption", "text": "Open the web UI of your cloud. Confirm filenames look random and blobs do not open without the client."}
]
}
FAQPage
{
"@context": "https://schema.org",
"@type": "FAQPage",
"mainEntity": [
{"@type": "Question", "name": "What does zero-knowledge mean for my files?", "acceptedAnswer": {"@type": "Answer", "text": "Files encrypt on your device and only you hold keys. The provider stores unreadable data."}},
{"@type": "Question", "name": "Will I lose access if I forget my password?", "acceptedAnswer": {"@type": "Answer", "text": "You need a recovery key or an approved contact. Without recovery, access is lost by design."}},
{"@type": "Question", "name": "Are filenames hidden?", "acceptedAnswer": {"@type": "Answer", "text": "Only when filename encryption is enabled. Many zero-knowledge tools support it."}}
]
}
ItemList
{
"@context": "https://schema.org",
"@type": "ItemList",
"itemListElement": [
{"@type": "ListItem", "position": 1, "name": "Pick a zero-knowledge method"},
{"@type": "ListItem", "position": 2, "name": "Set a recovery key"},
{"@type": "ListItem", "position": 3, "name": "Verify with a download-open test"}
]
}
