AES-128 Versus AES-256: A Pragmatic Analysis of Security and Speed Trade-offs
Executive Summary: Operational Security Trumps Key Length
The choice between the 128, bit and 256, bit variants of the Advanced Encryption Standard (AES) is often mistakenly perceived as a fundamental security race. In reality, both AES, 128 and AES, 256 provide security margins that are computationally prohibitive for all currently known classical adversaries. AES, 128’s primary weakness is purely theoretical and relates only to the distant threat posed by quantum computing or hypothetical, successful related, key cryptanalysis against the 10, round structure.
The practical distinction hinges almost entirely on performance tuning and organizational policy. While AES, 256 inherently requires more computational work due to its four extra rounds, modern systems utilizing hardware acceleration (such as Intel AES, NI) negate this difference, making speed parity common. In contrast, resource, constrained or legacy environments incur a measurable performance penalty for the unnecessary complexity of AES, 256. Security architects must prioritize the integrity of the cryptographic implementation, focusing on constant, time execution, secure key derivation, and correct cipher mode usage, as these operational factors represent the true boundary of practical security, far outweighing the marginal benefit of 128 additional key bits.
1. The Advanced Encryption Standard (AES) Foundation and Structural Differences
The Advanced Encryption Standard is a symmetric block cipher selected by the U.S. National Institute of Standards and Technology (NIST) in 2001. It is based on the Rijndael algorithm and forms the gold standard for encrypting sensitive information globally. Understanding the differences between its variants requires examining how key size structurally alters the encryption process.
1.1. Technical Distinctions: Key Length, Block Size, and Encryption Rounds
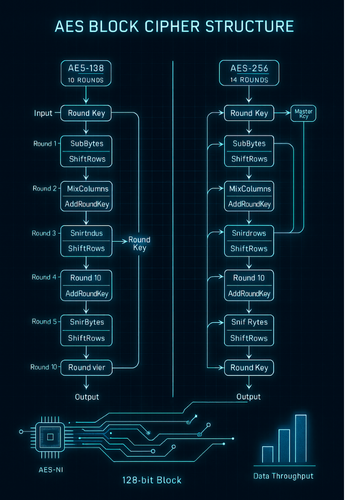
AES is defined to operate on a fixed 128, bit (16, byte) block size, regardless of the key length selected. This standardization ensures compatibility across implementations. However, the key length, 128, 192, or 256 bits, directly dictates the number of encryption rounds performed on each 128, bit block of data:
- AES, 128 is executed over 10 rounds of processing.
- AES, 256 is executed over 14 rounds of processing.
Except for the last round, every round executes an identical series of four steps: the substitution of bytes (ByteSub), a row permutation (ShiftRow), a column mixing operation (MixColumn), and the addition of a round key (AddRoundKey). The requirement for four extra rounds in the 256, bit variant is the fundamental source of its increased computational demand per block of data compared to the 128, bit variant.
1.2. Key Schedule Complexity and Cryptographic Dependencies
Beyond the raw number of encryption rounds, the Key Schedule generation process contributes to the computational complexity. The Key Schedule takes the initial secret key and generates the distinct round keys necessary for the AddRoundKey step in each of the encryption rounds. The necessity for AES, 256 to derive and manage 15 unique 128, bit round keys (one initial key plus 14 round keys) from a 256, bit master key is a structurally heavier operation than deriving 11 round keys from a 128, bit master key.
This dual overhead, the greater number of rounds and the intrinsically heavier Key Schedule derivation, is the true engine driving the performance disparity observed when these algorithms are executed in pure software. For security robustness, it is important to recognize that the core cryptographic operations of AES are consistent across all variants. If a fundamental algorithmic flaw were ever discovered that compromised the basic substitution or mixing steps, it would likely compromise both 128, bit and 256, bit keys. The only exception would be if the attack were specifically effective against 10 rounds but failed against the 14 rounds used by AES, 256.
2. Security Margin Assessment: Dispelling the Brute Force Myth
The most common argument for using AES, 256 rests on its brute, force security margin. While mathematically accurate, this argument rarely holds practical relevance against modern computational threats.
2.1. The Exponential Security Gap Versus Practical Irrelevance
AES, 128 requires approximately $2^{128}$ operations for an exhaustive brute, force attack. To put this into perspective, even if an attacker commanded the computational power of the peak Bitcoin network, arguably the largest modern network devoted to cryptographic hashing, performing approximately $10^{20}$ operations per second, cracking a single AES, 128 key would still require over $10^{23}$ years. Considering the universe is only about $13.8 \times 10^{9}$ years old, this required time frame makes AES, 128 keys functionally unbreakable by classical computation within any realistic timeframe, or even the estimated lifespan of the universe.
Given that the operational lifetime of almost all sensitive information (e.g., financial data, intellectual property, session keys) is measured in years, not sextillions of years, the added margin provided by AES, 256 ($2^{256}$ operations) represents a security level that is mathematically enormous yet practically meaningless for contemporary risk mitigation. Choosing AES, 256 for typical data confidentiality needs is often an example of over, engineering, resulting in unnecessary complexity and potential performance penalties.
2.2. Known Theoretical Attacks and Practical Feasibility
Cryptographers have devised theoretical attacks that are computationally faster than a full exhaustive search, though none of these are currently feasible against the full 10, round or 14, round versions of AES.
- Biclique Attacks: These attacks reduce the theoretical complexity of AES, 128 slightly to $2^{126}$ and AES, 256 to $2^{254.4}$. These complexities remain practically insurmountable.
- Related, Key Attacks (RKA): RKA requires the attacker to observe encrypted data based on keys that share a mathematical relationship. While a related, key attack against a reduced 9, round version of AES, 256 has been demonstrated with a complexity of $2^{99.5}$ (a feasible timeframe), the full 14, round AES, 256 requires a complexity of $2^{256}$ in both time and data, which is computationally infeasible.
The main cryptographic benefit of AES, 256’s 14 rounds is that they provide a wider structural safety cushion against any hypothetical future cryptanalytic breakthroughs that might successfully attack the 10, round structure of AES, 128 but be defeated by the additional processing in AES, 256. This theoretical defense against future structural weaknesses is a valid, non, brute, force argument for the stronger key size.
2.3. Future, Proofing: The Impact of Quantum Computing
The only scenario where AES, 128’s security margin becomes potentially questionable is in the highly speculative future dominated by practical quantum computers. Quantum computing, leveraging Grover’s algorithm, could theoretically accelerate brute, force searches against symmetric ciphers by a square root factor, effectively halving the key’s security strength.
- Under a quantum threat, AES, 128 would drop to approximately 64 bits of effective security.
- AES, 256 would drop to approximately 128 bits of effective security.
While 64 bits of security is generally considered vulnerable, the hardware required to mount such an attack remains purely theoretical. Breaking AES, 128 would require an estimated 2,953 logical qubits, and AES, 256 would require 6,681 logical qubits. Given that the largest operational quantum computers in 2020 only possessed 65 qubits, this threat is constrained by the physical limitations of quantum technology for the foreseeable future.
For organizations or governments that must maintain 128 bits of effective security in a post, quantum world, for example, when archiving highly classified data that must remain secure for centuries, AES, 256 is the only viable AES option. For all other use cases, the 128, bit key length is sufficient even against foreseeable quantum challenges. The determination of when to use AES, 256 thus shifts from current threat mitigation to a long, term policy mandate driven by the extreme time horizon of the protected data.
Table 1: Comparative Security Margins of AES Variants
| AES Variant | Rounds | Classical Complexity (Operations) | Post, Quantum Security (Grover) | Estimated Logical Qubits to Break | Rationale for AES, 256 Policy |
| AES, 128 | 10 | $2^{126}$ (Biclique) | $2^{64}$ bits | 2,953 | Adequate for current threats; sufficient for most corporate data lifecycle. |
| AES, 256 | 14 | $2^{254.4}$ (Biclique) | $2^{128}$ bits | 6,681 | Necessary only for extreme long, term assurance or highly classified data requiring 128, bit quantum resilience. |
3. Performance Dynamics: Measuring the Cost of 256 Bits
The computational cost of cryptography is a key architectural consideration, but the performance difference between AES, 128 and AES, 256 is entirely contingent upon the execution environment.
3.1. Hardware Acceleration and AES, NI: Achieving Throughput Parity
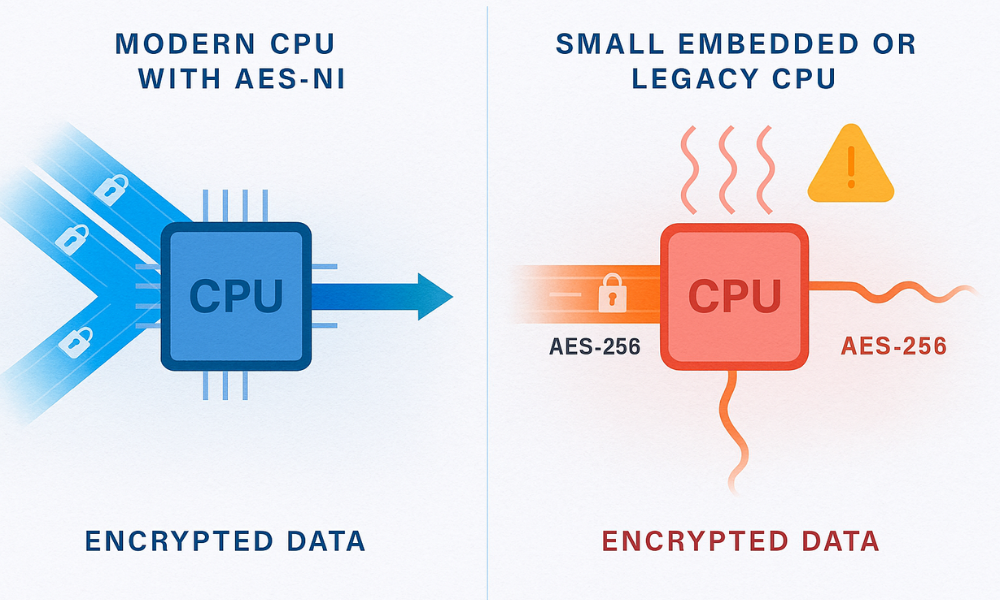
The widespread integration of dedicated cryptographic instructions, such as Intel AES, NI (New Instructions) or ARM crypto extensions, has fundamentally altered the performance landscape. These hardware features execute the complex mathematical operations of AES directly on the CPU silicon, drastically minimizing the computational overhead for cryptographic tasks.
In modern hardware, accelerated environments, the difference in speed between AES, 128 and AES, 256 becomes negligible, often rendering their speeds “virtually identical” in throughput benchmarks. This occurs because the hardware unit is highly optimized for pipelining and rapid execution of the base AES round functions (ByteSub, ShiftRow, etc.). Security architects must ensure their cryptographic libraries (e.g., OpenSSL) are configured to automatically leverage these hardware instructions to maximize throughput, regardless of the key size selected.
3.2. Bottlenecks in Resource, Constrained Environments
The performance disparity becomes pronounced when hardware acceleration is unavailable, which can occur on older processors, low, power embedded devices, or IoT systems. When AES is implemented entirely in software, relying on standard CPU instructions, the inherent structural differences become significant. The reliance on software, only implementation imposes a “significant performance penalty,” particularly on AES, 256, owing to the four additional rounds and the heavier Key Schedule operation required per block.
On devices with limited processing capacity or systems handling millions of transactions per second, the added overhead of AES, 256’s computational burden can manifest as a “tangible bottleneck”. In embedded systems, the increased computational cycle time of the 14, round cipher translates directly into higher CPU utilization, which in turn leads to increased power consumption and reduced battery life. The decision to deploy AES, 256 in such an environment must therefore weigh the non, trivial cost to operational efficiency against the purely theoretical security gain.
In systems where AES acceleration is lacking and performance is paramount, a strategic alternative may be superior. Stream ciphers like ChaCha20, Poly1305 are specifically optimized for excellent performance in pure software execution and often prove more efficient than either AES, 128 or AES, 256 on resource, constrained devices.
Table 2: Conceptual Performance Impact by Environment
| Execution Environment | AES Implementation | AES, 128 Performance | AES, 256 Performance | Performance Delta | Key Implication |
| Data Center/Desktop (x86/ARM) | Hardware Accelerated (AES, NI) | High Throughput | High Throughput | Negligible (<5%) | Choice is purely policy, driven; speed parity exists. |
| Embedded/Legacy CPU | Pure Software | Moderate Throughput | Lower Throughput | Pronounced (Up to 40%) | AES, 256 imposes a cost penalty; consider AES, 128 or ChaCha20. |
4. Operational Security: Where Real, World Attacks Occur

Focusing exclusively on the mathematical difference between $2^{128}$ and $2^{256}$ operations obscures the real, world attack landscape. In practice, attackers overwhelmingly target implementation flaws and human error, rather than attempting to brute, force a mathematically sound cipher.
4.1. Implementation Vulnerabilities: The Threat of Side, Channel Attacks (SCA)
Real, world attackers operate by targeting the “easiest/weakest/least expensive link in the chain”. This path bypasses the mathematical strength of the key length entirely and leads to side, channel attacks (SCA). SCA exploits information leaked from the physical execution of the encryption process, such as variations in timing, power consumption, or cache access patterns.
A classic example is a timing attack, which measures the micro, differences in computation time needed to process data based on the secret key. These differences leak information about the key material. Crucially, SCA targets the mechanism of implementation, for example, data, dependent table lookups, not the key’s length. Consequently, a vulnerable, non, constant, time implementation of AES, 256 is practically less secure than a robust, constant, time implementation of AES, 128. The primary defense against SCA involves utilizing Hardware Security Modules (HSMs) or ensuring that cryptographic operations are executed in a time, invariant manner, independent of the input data or key.
4.2. Key Management Failure: The True Weakest Link
Even if a cipher is mathematically secure, its practical security collapses if the key material is weak or poorly handled. Many security breaches result from attacks against the mechanism used to derive or manage the key, rather than the cipher itself.
Robust key derivation is paramount. If a user password is used as the base secret, a strong Key Derivation Function (KDF) such as Argon2id or scrypt must be employed. These functions intentionally impose computational work (memory and time) to slow down offline dictionary or brute, force attacks against the password itself. An insufficient work factor in the KDF can compromise the security of the base secret, thereby exposing the encrypted data regardless of whether AES, 128 or AES, 256 was used. Furthermore, all cryptographic keys and nonces must be generated using a Cryptographically Secure Pseudo, Random Number Generator (CSPRNG) to guarantee unpredictability.
4.3. Misuse of Cipher Modes and Nonce/IV Handling
The overall security of an AES implementation is highly dependent on the Mode of Operation selected. Modern protocols typically favor Authenticated Encryption with Associated Data (AEAD) modes like Galois/Counter Mode (GCM), which provides both confidentiality and data integrity.
However, the misuse of these modes can be catastrophic. In GCM mode, reusing the Initialization Vector (IV) or nonce with the same key completely destroys the security guarantees of the cipher, leading to a total compromise of confidentiality and integrity. This vulnerability is entirely unrelated to the length of the AES key. Configuration errors, such as using keys of incorrect sizes (AES supports only 128, 192, or 256 bits) or accidentally introducing multi, byte characters into the key definition, are common pitfalls that introduce operational vulnerabilities, overriding the theoretical strength of the algorithm itself.
The conclusion drawn from analyzing these practical attack vectors is that organizations prioritizing AES, 256 based solely on its larger bit size often engage in “security theater.” They absorb the cost of increased computational load without addressing the much more realistic and dangerous vulnerabilities residing in poor key management, improper mode usage, and lack of side, channel countermeasures.
5. Contextual Deployment and Policy Recommendations
Determining the appropriate key length should be a risk, based decision rooted in the data’s longevity, the operational environment, and specific regulatory mandates.
5.1. Standard Recommendations for High, Volume, Short, Lived Data
For most high, volume applications, secure communication, and user session management, AES, 128 is the default standard and provides an optimal balance of robust security and speed.
- Web Communications: Modern protocols, including TLS 1.3, widely support both AES, 128, GCM and AES, 256, GCM cipher suites. The industry consensus, reflected by major providers like Cloudflare, treats AES, 128 as fully adequate for robust security.
- System Defaults: Major operating system components and encryption utilities validate the sufficiency of AES, 128. For example, Microsoft BitLocker defaults to AES, 128, recognizing it as the required commercial baseline for enterprise data protection.
For applications where hardware acceleration is available, AES, 128 offers maximum practical security with the least possible (if negligible) overhead, making it the mathematically pragmatic choice for data with a typical lifespan.
5.2. Recommendations for Long, Term Archival and Classified Data
AES, 256 is warranted primarily when the data requires extreme long, term protection, often measured in decades or centuries, or is subject to stringent regulatory mandates (such as government or military classified data).
This mandate is a strategic choice, acting as an expensive form of insurance driven by the need for future, proofing. It ensures that the system maintains a recognized 128 bits of security even if a powerful quantum computer capable of exploiting Grover’s algorithm becomes reality. AES, 256’s greater number of rounds also offers an extended structural defense against hypothetical, future cryptanalytic attacks that might slightly compromise the security of the 10, round AES, 128 structure.
5.3. Strategic Alternatives: When ChaCha20, Poly1305 is Superior
For environments where performance is the dominating factor and dedicated AES hardware acceleration is absent, alternative algorithms may be necessary. ChaCha20, Poly1305, a 256, bit stream cipher, is recognized for its high efficiency and robustness in pure software implementations.
This preference is institutionalized in high, performance, security, focused protocols. For instance, the WireGuard VPN protocol mandates the use of ChaCha20, Poly1305 over AES due to its superior performance characteristics on a wide variety of hardware architectures that may not offer AES, NI acceleration. When constrained systems must prioritize low latency, battery life, or reduced computational burden, ChaCha20 often provides better efficiency than either AES variant.
Table 3: Strategic Key Size Recommendation Matrix
| Security Context | Risk Profile/Data Life | Hardware Environment | Recommended Algorithm | Primary Rationale |
| Web Session / VPN Tunneling | High Confidentiality, Short, Term | Hardware Accelerated (AES, NI) | AES, 128 GCM | Optimal speed/security balance with minimal overhead. |
| Regulatory / Classified Archive | Extreme Security, Multi, Decade | Any (Performance Secondary) | AES, 256 GCM | Policy mandate; hedge against quantum computing and theoretical attacks. |
| Embedded/Mobile Data Storage | Resource Constrained, Low Power | Software Only (No AES, NI) | ChaCha20, Poly1305 or AES, 128 | Minimizes performance and power overhead while maintaining excellent security. |
| Generic Corporate Storage (HDD/SSD) | Medium Confidentiality, Medium, Term | Hardware Accelerated (BitLocker) | AES, 128 (Default) | Sufficient security margin; industry standard and default configuration. |
6. Conclusion and Final Policy Guidance
The notion that AES, 256 is always practically superior to AES, 128 is a fundamental misconception rooted in an incomplete understanding of modern cryptanalysis and implementation security. The analysis overwhelmingly demonstrates that AES, 128 provides security far beyond the reach of classical computational power and resists foreseeable quantum threats, proving sufficient for the vast majority of commercial and personal data confidentiality requirements.
The true superiority of AES, 256 is confined to two narrow domains: fulfilling strict long, term policy requirements for 128, bit quantum security, and providing an additional, theoretical structural buffer against future cryptanalytic breakthroughs aimed at lower, round AES versions. In almost all other cases, particularly when hardware acceleration is unavailable, AES, 256 incurs a performance cost without yielding a significant or necessary increase in real, world security.
The industry consensus, evidenced by the default settings of widely deployed security tools like BitLocker and the broad acceptance of AES, 128 in modern TLS cipher suites, confirms that 128 bits is the pragmatic balance between security efficacy and operational efficiency.
Checklist for Implementing AES Securely
To achieve robust practical security, organizations must shift their focus from maximizing key length to perfecting operational integrity. The following actions are critical for any secure AES deployment, regardless of the chosen key size:
- Prioritize Side, Channel Resistance: Mandate the use of cryptographically secure libraries that provide constant, time AES implementations to neutralize timing and cache attacks. For the highest level of assurance, utilize Hardware Security Modules (HSMs).
- Ensure Unique Nonces: Utilize the cipher in an Authenticated Encryption mode (AES, GCM) and establish strict controls to guarantee that the Initialization Vector (IV) or nonce is generated securely and never reused under the same key.
- Mandate Hardware Acceleration: Ensure that all processing environments where high throughput is required have access to and are configured to utilize dedicated cryptographic instructions (AES, NI, ARM Crypto) to minimize performance overhead.
- Implement Strong Key Derivation: Use contemporary Key Derivation Functions (KDFs) with appropriately tuned work factors (memory and time) when generating keys from passwords, ensuring that the base secret remains resilient against offline brute, force attacks.
Frequently Asked Questions
Is AES-256 Truly More Secure Than AES-128?
Mathematically, yes, AES, 256 has a much larger key space ($2^{256}$ vs $2^{128}$) and four more encryption rounds (14 vs 10). Practically, no. Both are unbreakable by classical computers within the lifespan of the universe. AES, 128 is overwhelmingly sufficient for almost all current commercial and personal data, making the extra security margin of AES, 256 largely irrelevant in real, world risk scenarios.
Does AES-256 Impact Performance Significantly?
If your processor has dedicated hardware acceleration (like Intel AES, NI or ARM crypto extensions), the performance difference is negligible, often less than 5%. However, in software, only implementations (on older CPUs, embedded systems, or IoT devices), AES, 256 can be noticeably slower (up to 40% slower in some benchmarks) due to its four additional rounds and heavier key schedule.
When Is AES-256 Actually Required?
AES, 256 is primarily required for two specific cases: 1) Meeting extreme long, term data archival requirements (often military or government) where 128 bits of effective security must be maintained against a hypothetical, future quantum computer (Grover’s algorithm), and 2) Fulfilling strict regulatory or compliance mandates that specifically require a 256, bit key.
What is a Side-Channel Attack and How Does it Relate to Key Length?
A side, channel attack (SCA) exploits information leaked from the physical execution of the cipher (e.g., timing, power usage, or cache access patterns) to deduce the secret key. SCA targets implementation flaws (like non, constant, time code), not the length of the key. Therefore, a poor implementation of AES, 256 is less secure than a robust, constant, time implementation of AES, 128.
Why is Correct Nonce/IV Usage More Important Than Key Size?
Misusing a cipher mode, particularly by reusing the Initialization Vector (IV) or nonce with the same key in GCM mode, completely destroys the cipher’s security, exposing both confidentiality and integrity. This is a fundamental operational failure that renders any key length, including AES, 256, useless. The integrity of the implementation is the true weakest link.
