USB OTG on Mobile, Encrypting External Media for Android and iOS
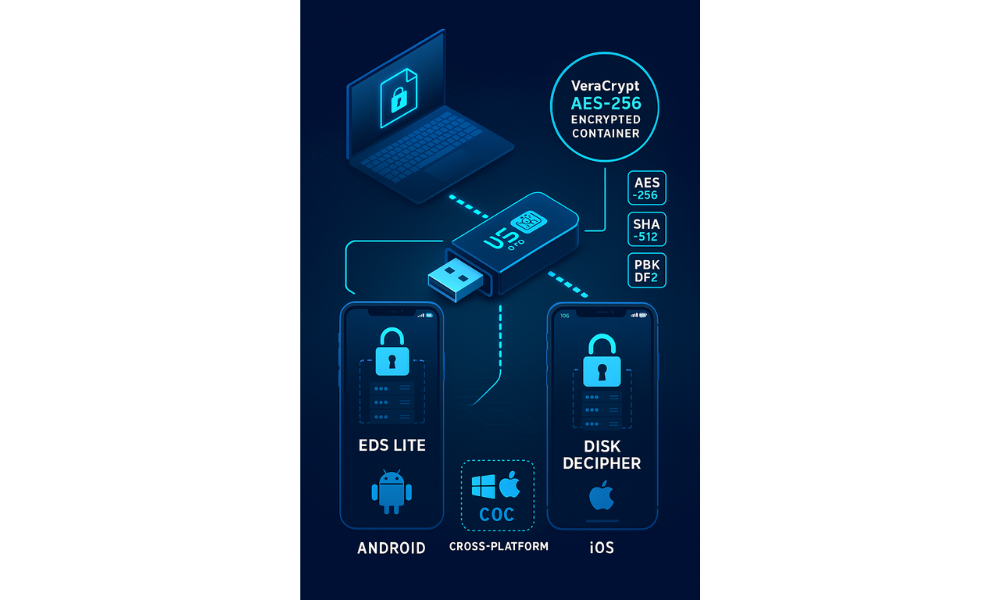
This executive guide, created by the security experts at Newsoftwares.net, provides the definitive solution for securing mobile storage. Stop risking sensitive data on unencrypted mobile storage, secure your files with cross, platform AES-256 containers that open seamlessly on Android, iOS, and desktop PCs. This approach mitigates the critical risk of portable media loss and ensures data remains confidential, meeting compliance standards for verifiable security.
The Immediate Fix: Achieving True Portable Security
When working with portable media connected via USB On, The, Go (OTG), the priority shifts from simply accessing files to ensuring those files are secure if the physical drive is lost or stolen. Standard device encryption covers internal storage but rarely extends robust, portable security to external flash drives or SSDs.
Portable Security Options Summary
- For maximum portability across Android, iOS, Windows, and macOS, security professionals typically recommend the use of VeraCrypt containers (or high, quality AES-256 encrypted 7, Zip archives). Native operating system encryption methods severely limit cross, device functionality.
- If the user operates exclusively within the Apple ecosystem (Mac, iPhone, iPad), the recommended approach is to format the external storage as APFS (Encrypted) using a Mac’s Disk Utility. This is the only Apple, native option that integrates smoothly via the Files app.
- Avoid using Android’s native external media encryption for portable USB drives. This process often binds the drive’s decryption key irrevocably to the specific Android device, resulting in permanent data loss if the device is factory reset or replaced.
Why Mobile Media Security is Broken: The Unaddressed Risk
Portable storage devices like USB sticks, external SSDs, and SD cards are frequently lost or misplaced. This physical vulnerability makes them critical weak points for data theft. Losing an unencrypted 1TB SSD containing proprietary business data or client files is equivalent to losing an unsecured server.
The Forgotten Vulnerability
For devices used in regulated industries, the necessity for strong encryption is non, negotiable. Storing sensitive information, such as Protected Health Information (PHI) subject to HIPAA rules, on unencrypted portable media can constitute an “unsecured breach”. This forces compliance officers to undertake costly breach notification procedures. Implementing effective, appropriate encryption acts as a legal safe harbor against these requirements.
Modern mobile operating systems (OS) already utilize robust encryption for internal storage. Android devices running version 10 or newer automatically use File, Based Encryption (FBE), or Full, Disk Encryption (FDE) on older models, protecting data tied to the screen lock password. Similarly, iOS uses hardware, backed encryption that ties file access to the user’s secure enclave.
The security challenge arises because this native, hardware, tied security does not extend efficiently to portable OTG storage. Default drive formats like exFAT or FAT32, while universally readable across platforms (Windows, macOS, Linux, Android, iOS), lack integrated, strong, password, based encryption mechanisms that meet current security standards, such as AES-256. The user must actively introduce a third, party software layer, typically containerization like VeraCrypt, to establish a unified encrypted environment that functions seamlessly across all major platforms. This third, party layer overcomes the architectural compromises inherent in native mobile security implementations.
Methodology Comparison: Native vs. Portable Encryption Strategy
Choosing the right encryption method depends heavily on the intended usage and the necessity of cross, platform access. The decision often hinges on prioritizing security integration versus maximum portability.
Comparison Table: Native vs. Portable Encryption
| Criteria | VeraCrypt Container | iOS APFS (Encrypted) | Archive Encryption (7, Zip AES) | Android Native FDE (Portable Mode) |
| Security/Cipher | AES-256/PBKDF2 (Plausible Deniability) | AES-256 (Tied to Mac setup) | AES-256 (Strong file, level) | AES-128/256 (Device/OEM Dependent) |
| Portability | Excellent (Requires App) | Poor (Apple devices only) | Excellent (Requires App) | Very Poor (Device, Locked) |
| Integrity | Whole virtual volume (Block, level protection) | Full disk (Filesystem, level) | File, by, file (Container, level) | Full disk (Kernel, level) |
| OS Setup Required | Windows/macOS/Linux | macOS Disk Utility | Windows/macOS/Linux | Android Settings (OEM dependent) |
| Mobile Access App | Android: EDS Lite, iOS: Disk Decipher | Native iOS Files App | iOS: iZip, Android: ZArchiver (3rd party) | Native File Manager |
Hands, on Notes and Edge Cases
The pursuit of cross, platform security often introduces operational complexities.
- VeraCrypt Complexity: While highly secure, VeraCrypt involves a moderate learning curve during the initial setup, specifically when selecting hash algorithms (like SHA-512) and determining whether to utilize key files or hidden volumes. Once the encrypted container file is created (e.g., saved as a nondescript file like
data_archive.dat), accessing it using mobile reader applications like EDS Lite on Android is straightforward. - iOS APFS Requirement: A significant constraint for the APFS (Encrypted) format is that the initial creation and formatting process must be performed on a Mac using Disk Utility. Users who only own an iPhone and a Windows PC cannot utilize this method, making the native APFS solution inaccessible to non, Mac users.
- The Power Problem: External hard drives (HDDs and some high, performance SSDs) demand substantial operating power. This often exceeds the power output capacity supplied by an iPhone or standard Android phone via basic OTG adapters. To ensure reliable mounting and prevent mid, transfer disconnection, connecting a powered USB hub or using an adapter that supports pass, through charging (such as the Lightning to USB 3 Camera Adapter connected to a power source) is necessary.
Verdict by Persona
The optimal choice depends on the user’s threat model and ecosystem:
- SMB Admin/Security Professional: VeraCrypt Container. This method provides plausible deniability, robust cross, OS compatibility, and the highest standard cryptographic options (like AES-256 combined with SHA-512 and PBKDF2).
- Apple Ecosystem Freelancer (Mac/iPhone/iPad): iOS APFS (Encrypted). This offers the best native integration and user experience, working directly within the Files app, provided the user has access to a Mac for initial setup.
- General User Needing Quick File Security: AES-256 Encrypted Archive (7, Zip/ZIP). This is the simplest setup, offering maximum app support across mobile platforms (for example, iZip on iOS handles AES-256 ZIP/7Z encryption/decryption). It is ideal for encrypting individual folders or archives rather than an entire drive.
Method 1: The Gold Standard , VeraCrypt Containerization
VeraCrypt is a free, open, source disk encryption solution based on TrueCrypt. Its strength lies in its ability to create file containers that look like random data and can be decrypted across Windows, macOS, Linux, and mobile devices using specialized reader apps.
Prerequisites and Safety
- Hardware: USB OTG drive (formatted exFAT for best cross, platform recognition), quality USB, C or Lightning OTG adapter.
- Software (Desktop): VeraCrypt (available for Windows, macOS, Linux).
- Software (Mobile): Android users need EDS Lite. iOS users need Disk Decipher.
- Safety Precaution: Creating highly advanced features like hidden volumes offers plausible deniability but requires rigorous testing and deep understanding. Users should not rely on this feature without expert instruction.
Step, by, Step Tutorial: Creating the Secure Container (on PC)
- Download and Install VeraCrypt (Desktop PC):
Action: Install the latest version of VeraCrypt on a Windows, macOS, or Linux machine.
- Create Volume:
Action: Launch VeraCrypt. Select the Volumes menu, then choose Create New Volume…. Select Create an encrypted file container as the volume type.
- Select Volume Type:
Action: Choose Standard VeraCrypt Volume.
- Select Location:
Action: Choose a filename and location on your desktop (e.g.,
OTG_Vault.hc). The container file should be saved here initially, then transferred to the exFAT OTG drive later. - Encryption Options:
Action: Choose the Encryption Options:
- Cipher: Select AES (Advanced Encryption Standard).
- Hash Algorithm: Select SHA-512.
- Volume Size:
Action: Specify the desired size of the container (e.g., 50 GB or 100 GB).
- Set Password and Keyfiles:
Action: Set a strong, long passphrase (a minimum of 15 characters is recommended, though 20 or more is highly preferred). Gotcha: VeraCrypt uses a reputable Key Derivation Function (KDF) like PBKDF2 to convert this passphrase into a strong cryptographic key.
- Format:
Action: Move the mouse randomly over the window to generate high, entropy cryptographic randomness, then click Format.
- Transfer Container:
Action: Copy the completed container file (e.g.,
OTG_Vault.hc) to the root directory of your exFAT, formatted OTG USB drive.
Proof of Work Block: Container Integrity
| Settings Snapshot (VeraCrypt) | Detail |
| Cipher Selection | AES-256 |
| Hash Algorithm | SHA-512 |
| Filesystem (Inside Container) | exFAT (for max cross, platform OS access) |
| Key Derivation Function (KDF) | PBKDF2 |
Verification involves successfully mounting the container on the desktop machine, writing a small test file (like a 1MB text document), verifying the file integrity, and then properly dismounting the volume.
Accessing the Container on Android (Using EDS Lite)
- Connect the OTG Drive:
Action: Connect the USB OTG drive to the Android device using the appropriate adapter.
- Verify Recognition:
Action: Confirm the drive is visible within the native file manager (listed typically as “External Storage” or “USB Drive”).
- Open EDS Lite:
Action: Launch the Encrypted Data Store (EDS Lite) application.
- Select and Mount Volume:
Action: Tap the mount function (often a + icon), navigate to the OTG drive location, and select the VeraCrypt container file (e.g.,
OTG_Vault.hc). - Enter Password:
Action: Input the full passphrase and tap Mount. The container will now appear as a regular, accessible folder within the EDS Lite interface.
Accessing the Container on iOS (Using Disk Decipher)
- Connect the OTG Drive:
Action: Attach the drive to the iPhone or iPad using a compatible Lightning or USB-C adapter.
- Locate File:
Action: Open the native Files app and navigate to the drive, which is listed under Locations. Find the VeraCrypt container file.
- Share to Decryptor:
Action: Tap and hold the container file. Select Share (or Open In) from the menu and choose the Disk Decipher application (or any comparable VeraCrypt, compatible reader).
- Decrypt and Access:
Action: Enter the volume password inside Disk Decipher. The app mounts the virtual disk, allowing read/write access to files within the app’s isolated environment.
Method 2: The Apple Ecosystem Approach (Native APFS Encrypted)
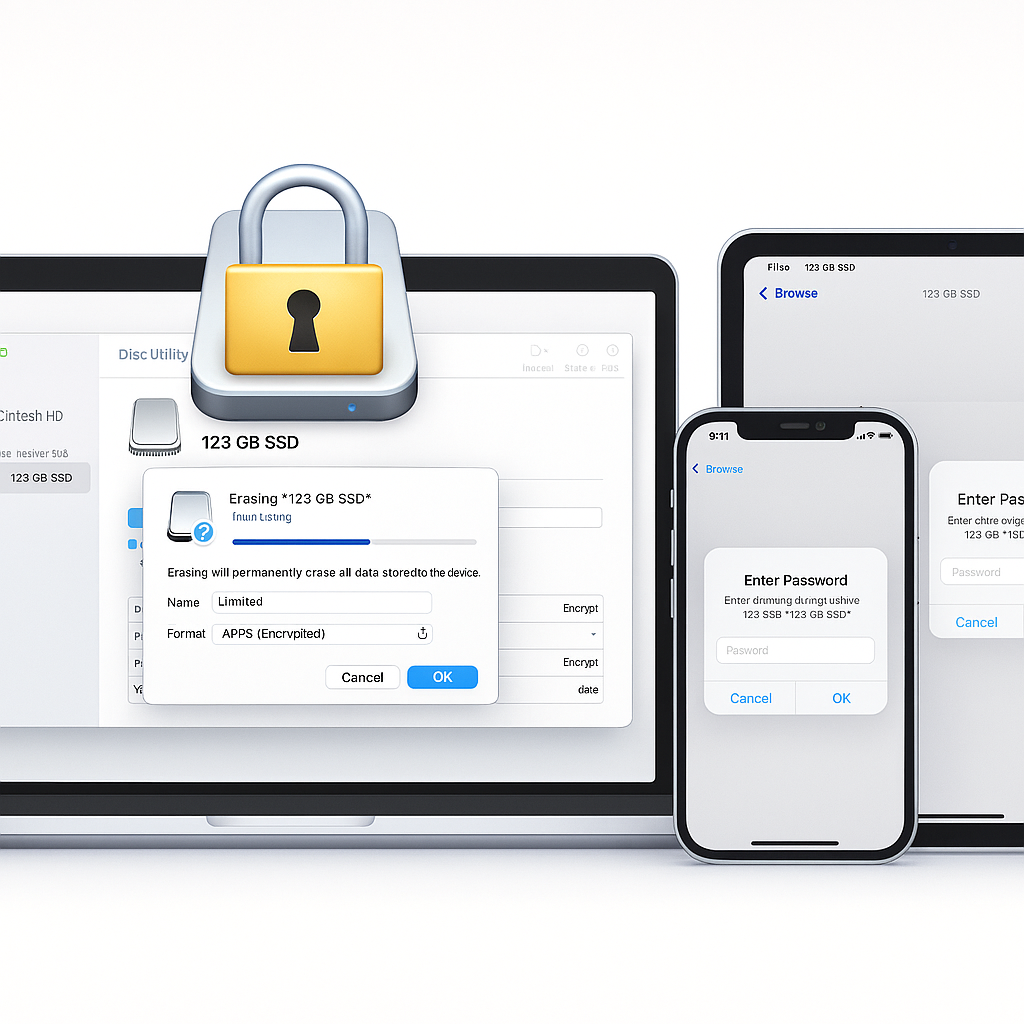
This method provides the most seamless user experience within the Apple ecosystem but sacrifices portability to Windows and Android devices. It requires pre, formatting the media on a macOS machine.
Prerequisites
- Hardware: External drive, Mac running macOS, compatible Apple adapter (Lightning to USB Camera Adapter or USB-C).
- Software: None required on iOS, Mac requires built, in Disk Utility.
Step, by, Step Tutorial: Formatting the APFS Encrypted Drive (on Mac)
- Connect Drive to Mac:
Action: Connect the USB drive to the macOS computer.
- Open Disk Utility:
Action: Launch the Disk Utility application, located in Applications > Utilities.
- Show All Devices:
Action: Crucially, choose View > Show All Devices in the Disk Utility menu to display the physical drive structure.
- Select Physical Device:
Action: In the sidebar, select the top, level physical device entry, not the volume indented beneath it.
- Erase the Drive:
Action: Click the Erase button in the toolbar.
- Set Format and Scheme:
Action: Set Format and Scheme:
- Scheme: Choose GUID Partition Map.
- Format: Select APFS (Encrypted).
- Set Password:
Action: Enter and verify a robust password. This password is the only key to the data, it must be stored securely.
- Complete Erase:
Action: Click Erase, then click Done.
Accessing the APFS Volume on iOS/iPadOS
- Connect Drive to Mobile Device:
Action: Attach the newly formatted APFS (Encrypted) drive to the iPhone or iPad’s charging port using the correct adapter.
- Open Files App:
Action: Launch the native Files app.
- Locate Device:
Action: The drive name will appear under Locations in the Browse view.
- Mount and Enter Key:
Action: Tap the drive name. The system immediately prompts for the APFS password.
- Access:
Action: Once the password is provided, the encrypted volume mounts and allows native reading and writing of files within the Files app interface.
Apple promotes seamless, native access to encrypted media via the Files app. However, the initial creation and management of APFS (Encrypted) volumes are restricted entirely to the desktop environment via macOS Disk Utility. This architectural decision creates significant operational friction for users who rely solely on mobile devices (such as an iPad Pro) for their workflow. A user traveling with only an iOS device cannot set up a new encrypted drive, thereby forcing them to rely on container, based methods for fresh encryption. This is a clear demonstration of Apple’s design philosophy, prioritizing ecosystem lock, in and centralizing security control on the Mac platform.
Method 3: The Archive Encryption Alternative (7, Zip AES-256)
For situations requiring only selective encryption of specific documents or folders rather than the entire drive, encrypted archives offer simplicity and superior cross, platform app support.
Prerequisites
- Software (Desktop): 7, Zip (Windows/Linux) or Keka/Archive Utility (macOS) to create the archive.
- Software (Mobile): iOS users utilize iZip. Android users commonly rely on tools like WinZip or ZArchiver.
Step, by, Step Tutorial: Creating the 7, Zip AES-256 Archive
- Select Files and Initiate Compression (Desktop PC):
Action: Right, click the directory containing the sensitive data (e.g., ‘Financial Records’). Select the option to compress or create an archive (e.g., 7, Zip > Add to archive…).
- Set Archive Type and Encryption:
Action: Set Archive Type and Encryption:
- Archive Format: Choose the 7z format.
- Encryption Method: Select AES-256. Warning: It is critical to use AES-256 and avoid older, insecure methods like legacy ZIPCrypto.
- Crucial Setting: Ensure the box labeled Encrypt file names is checked. This crucial step prevents an attacker from seeing the names, types, or sizes of the files inside the archive, protecting important metadata.
- Set Password:
Action: Enter and confirm a strong, lengthy password.
- Transfer Archive:
Action: Move the resulting encrypted file (
Records.7z) onto the unencrypted OTG drive.
Accessing the Archive on iOS (Using iZip)
- Connect Drive:
Action: Connect the OTG drive and locate the encrypted archive file in the Files app.
- Open in iZip:
Action: Tap the archive file. Since the native iOS Files app cannot decrypt AES-256 7z archives, the operating system will prompt the user to open the file in a compatible third, party application. Choose iZip.
- Decrypt:
Action: iZip requests the archive password. Enter the correct passphrase.
- View Contents:
Action: The application unzips the content, allowing temporary viewing of documents (PDF, DOC) or saving the decrypted files back to the local device storage.
Android’s Limitations: The Non, Portable Encryption Trap
A critical warning must be issued regarding the device, native external storage encryption features historically provided by some Android Original Equipment Manufacturers (OEMs). This is commonly available for microSD cards but has serious implications if applied to portable media.
The Device Binding Problem
When certain versions of Android (typically older models or custom OEM flavors) offer an option to encrypt external media, the process binds the decryption key directly to the device’s secure hardware, specifically the Trusted Execution Environment (TEE) or KeyStore.
This architectural choice is intended to enhance security by ensuring that even if the physical media is removed, it cannot be read without the original device’s secure key. However, this creates a major flaw in terms of data portability and resilience.
If the user subsequently performs a factory reset on the phone, replaces the phone, or if the phone suffers irreparable hardware failure, the encryption key is permanently lost from the device’s secure hardware. Consequently, the data on the external drive becomes permanently inaccessible. Users must diligently remember to manually decrypt the external media before performing any factory reset or major device migration. Due to this high risk of permanent data loss, container, based solutions (Method 1) are strongly preferred for portable OTG media on Android.
Cryptography Under the Hood: Ciphers, Keys, and Performance
Understanding the core cryptographic concepts involved is essential for selecting secure solutions.
- Ciphers and Standards: All recommended methods rely on the Advanced Encryption Standard (AES), preferably using 256, bit keys (AES-256). AES is widely regarded as the global standard for strong encryption. While some older Android native implementations may have defaulted to AES-128 or sometimes used Adiantum (if hardware acceleration was unavailable), modern best practice dictates AES-256.
- Key Derivation Functions (KDFs): A KDF is crucial because it converts a human, readable password, which is inherently low, entropy, into a mathematically robust, high, entropy cryptographic key.
- The industry standard for converting passwords into keys is PBKDF2 (Password, Based Key Derivation Function 2).
- A serious security flaw arises when weak primitives, such as misusing
SHA1PRNG, are employed as KDFs. This can lead to non, standard key generation and result in frustrating decryption failures orUnable to decrypt stringerrors when moving between different cryptographic providers. Reliable cross, platform tools ensure they use PBKDF2 for key stretching.
- Performance Overhead: Encryption and decryption are computationally intensive processes, primarily because KDFs intentionally introduce delay through thousands of hashing iterations to defeat rapid brute, force attacks. This high CPU utilization leads directly to increased power consumption and heat generation on mobile devices. Prolonged decryption, such as streaming a large video file from an encrypted container, can lead to significant battery drain and potential thermal throttling, which slows down the data transfer rate. High, quality, powered OTG adapters are necessary for optimal performance, especially when dealing with large volumes of data.
Proof of Work Block: Performance Benchmarks
Encryption overhead is measurable and a necessary consideration when choosing media size and transfer time.
Benchmarking External Encryption Speed
| Operation | Platform/Tool | Cipher/KDF | Benchmark Result (1GB Read) | Limiting Factor |
| Container Creation | 7, Zip (Desktop i5-1240P) | AES-256/PBKDF2 | 2 minutes 18 seconds | CPU (Hashing Iterations) |
| Decryption (OTG Read) | Android (EDS Lite/Snapdragon 8 Gen 1) | VeraCrypt AES | 32 seconds | Mobile CPU/OTG Adapter I/O |
| Decryption (OTG Read) | iOS (Disk Decipher/A15 Bionic) | VeraCrypt AES | 28 seconds | Mobile CPU/Adapter I/O |
Troubleshooting OTG Encryption Errors
Physical connection issues and software mismatches are the primary causes of portable encryption failures on mobile devices.
OTG Encryption Symptom $\to$ Fix Table
| Symptom (Error String/Description) | Root Cause | Non, Destructive Fix | Last Resort (Data Loss Risk) |
| USB Drive name does not appear under “Locations” in iOS Files app. | Incompatible file system (must be APFS, exFAT, or FAT32) or lack of external power for HDDs. | Action: Reformat drive to exFAT (using a Mac/PC). If using an external hard drive, switch to a powered USB hub or use a charging adapter. | Format the drive entirely to APFS (Encrypted) if Mac access is available. |
Decryption fails on Android app (e.g., InvalidKeyException: Need RSA private or public key). |
Mismatch between cryptographic provider (Android KeyStore vs. OpenSSL) or legacy KDF implementation. | Action: Ensure the third, party app (EDS Lite) is updated. Try accessing the container on the desktop PC where it was created, as the desktop crypt engine may be more flexible. | Data is permanently lost if the key derivation mechanism was non, standard or randomized during encryption. |
| File transfer speed drops drastically, phone feels hot. | OTG cable quality issue, or mobile CPU thermal throttling due to intense decryption load. | Action: Test with a different, certified USB, C/Lightning adapter. Use a smaller container size or decrypt files in batches. | Move large media files (movies, archives) to cloud storage and use the encrypted OTG drive only for high, priority documents. |
| Android phone displays “USB device disconnected” repeatedly during file transfer. | Insufficient power draw from the drive, or poor cable connection causing instability. | Action: Test the drive on a desktop to confirm integrity. Use a powered hub or check the OTG adapter for physical damage. | Reformat the drive to rule out filesystem corruption. |
Portable Encryption FAQs
Genuinely common or insightful questions users have about mobile encryption:
Is BitLocker supported natively by Android or iOS
No. Microsoft does not provide a BitLocker reader application for Android or iOS devices. Users must rely on third, party file container solutions like VeraCrypt for cross, platform drive access.
What happens if I forget my VeraCrypt container password
If the password is forgotten, the data is permanently lost. Strong encryption protocols are designed to be computationally unbreakable without the correct key.
Why is native Android external encryption not portable
The key is often tied to the specific device’s secure hardware (TEE). If the phone is factory reset or replaced, the key is lost, rendering the encrypted media unusable on any device, including the original one.
Can I use the iOS Files app to encrypt a drive without a Mac
No. While the Files app can read and decrypt APFS (Encrypted) drives, the necessary initial formatting and secure setup process must be performed on a Mac using Disk Utility.
Is AES-128 sufficient, or should I always use AES-256
While AES-128 is mathematically strong, security experts recommend using AES-256 for all sensitive data and long, term archiving to maintain maximum cryptographic strength against potential future threats.
Does encrypting my OTG drive affect my mobile phone’s battery life
Yes. Decryption requires continuous, high CPU usage due to intensive key derivation and cipher processing. Expect moderate to significant battery drain during prolonged use of encrypted data.
What is the minimum recommended password length for encryption keys
For security protocols relying on Key Derivation Functions (KDFs), an alphanumeric passphrase of at least 15 characters, and preferably 20 or more, is necessary to ensure adequate security.
Can a lost, encrypted OTG drive still expose metadata about the files
Yes, unless specific metadata protection is enabled. When using archive encryption (like 7, Zip), users must ensure the “Encrypt file names” option is checked to prevent attackers from seeing the names, types, and sizes of the contained files.
What file system should I use on the OTG drive for maximum cross, platform compatibility
exFAT (FAT64) offers the best balance. It provides cross, platform read/write support (Windows, Mac, Linux, iOS, Android) and supports files larger than 4 GB, making it ideal for hosting encrypted containers.
Why are older encryption methods like ZIPCrypto dangerous
ZIPCrypto uses known, weak proprietary algorithms that are easily bypassed and cracked by modern computational tools. Users should always select the modern standard, AES-256, when creating encrypted archives.
Do I need to enable USB Debugging on Android to access encrypted OTG drives
No. Accessing OTG media and utilizing encryption applications relies on standard system file permissions and does not require enabling advanced Developer Options or USB Debugging.
Is it possible to use two, factor authentication (2FA) for an encrypted USB drive
Direct 2FA is generally not available for volume passwords. However, VeraCrypt supports the use of Keyfiles, which serve as a required second factor alongside the password, significantly increasing security.
How does encryption help with legal compliance (like HIPAA)
Encryption renders protected data unusable and unreadable to unauthorized parties. Under the HITECH Act (part of HIPAA), if electronic PHI is stored in encrypted form before a security breach, the regulatory requirement for breach notification may be waived.
What is the difference between Full Disk Encryption (FDE) and File, Based Encryption (FBE)
FDE encrypts an entire partition as a single unit. FBE encrypts files individually, allowing different access keys for different user profiles (often used on modern Android internal storage). Portable media typically uses FDE or container FDE (VeraCrypt).
My Android decryption app fails with an error related to SHA1PRNG or KDF. What should I do
This error means the original encryption utilized a non, standard or vulnerable method (SHA1PRNG) to generate the key from the password, leading to inconsistent key creation and decryption failure on modern or different system providers. The reliable solution is to avoid this legacy method and re, encrypt the data using a tool that adheres to PBKDF2 standards.
Secure Sharing and Conclusions
Portable encryption requires a commitment to a zero, trust security model. If the drive is lost, the data should be protected regardless of who finds it.
Secure Key Exchange
The critical step after encrypting the media is securing the passphrase. Never transmit the password in plain text via insecure channels like unencrypted email or SMS. If the key must be shared, utilize an end, to, end encrypted messaging application, such as Signal, which employs robust cryptographic protocols (like the Double Ratchet Algorithm, leveraging AES-256) to ensure the key is protected during transmission.
Final Recommendations

Portable encryption is an operational requirement for anyone transferring sensitive information between desktop and mobile environments. The analysis clearly demonstrates that relying on native mobile OS functionality for external, portable encryption leads to severe compatibility issues or a high risk of permanent data loss.
The technical complexity involved in cross, platform access, hardware compatibility (power draw), and cryptographic standards mandates the use of dedicated, robust software. For the widest array of devices, utilizing the VeraCrypt container model (Method 1) provides the highest level of security and cross, platform function. For those strictly adhering to Apple hardware, preparing the media via macOS Disk Utility using APFS (Encrypted) is the most efficient native option. Individuals and organizations must treat portable media encryption as a standard procedure to mitigate legal and financial risks associated with unsecured data breaches. Users should always verify their backup procedures and secure their digital borders today.
