Modern digital security relies upon two distinct cryptographic paradigms: symmetric and asymmetric encryption. While both techniques are essential for data protection, they fulfill fundamentally different architectural roles dictated by their efficiency and key management characteristics. The core challenge in applied cryptography is securely transporting data at scale, a problem that neither approach can solve independently. This has necessitated the pervasive adoption of the Hybrid Encryption Model (HEM) across virtually all secure communication protocols.
Introduction to Cryptographic Dualism: The Hybrid Imperative
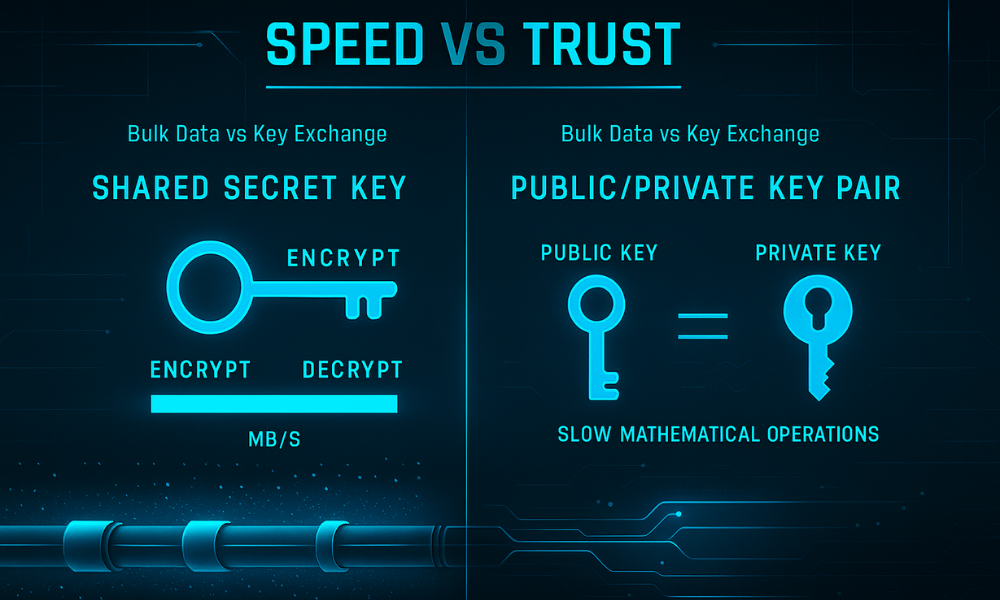
Defining the Cryptographic Architectures
Symmetric Cryptography (Confidentiality and Speed)
Symmetric encryption, often referred to as secret, key cryptography, utilizes a single, shared secret key for both the encryption and decryption of data. This architecture is built for speed and efficiency, achieving data processing throughputs typically measured in Megabytes per second (MB/s). Because the computational overhead per byte is low, symmetric ciphers, such as the Advanced Encryption Standard (AES) and ChaCha20, are the exclusive choice for handling bulk data confidentiality, disk encryption, and high, volume network traffic.
Asymmetric Cryptography (Trust and Key Exchange)
Asymmetric encryption, or public, key cryptography, employs a mathematically linked pair of keys: a public key, which is freely shared and used for encryption, and a private key, which must be kept secret and is used for decryption. This system provides the basis for secure communication channels and identity verification. However, due to the complex mathematical operations involved (relying on difficult problems like prime factorization or discrete logarithms), asymmetric encryption is computationally slow. Its performance is often measured in operations per second, making it wholly impractical for encrypting large datasets. Key asymmetric algorithms include Rivest–Shamir–Adleman (RSA), Elliptic Curve Cryptography (ECC), and the Digital Signature Algorithm (DSA).
The Inefficiency of Standalone Encryption
Using either cryptographic system in isolation reveals significant weaknesses that preclude its use in modern, distributed applications.
- The primary flaw of symmetric systems is the key distribution problem.
- For symmetric encryption to work, all communicating parties must possess the shared secret key securely before any communication takes place.
- Distributing this key securely, especially across large or untrusted networks, is nearly impossible without a secure mechanism to facilitate the exchange.
- Conversely, the main drawback of asymmetric systems is the performance problem.
- If an application attempted to encrypt a substantial amount of data, such as a large file or streaming video, directly using an algorithm like RSA, the computational cost would be prohibitive.
- Benchmarking confirms that the difference in speed between symmetric ciphers like AES, 256 and asymmetric ciphers like RSA, 2048 is often a factor of orders of magnitude.
The Hybrid Encryption Model (HEM)
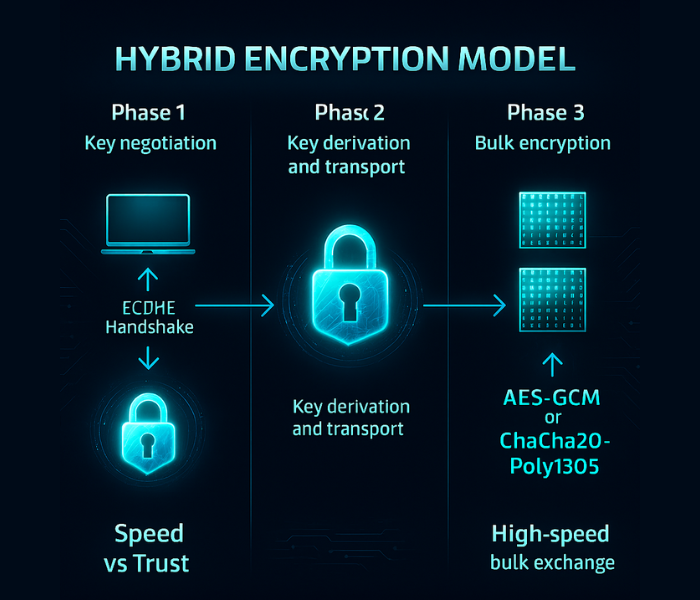
The Hybrid Encryption Model (HEM) is the mandatory architectural choice for modern system design, specifically engineered to reconcile the key distribution and performance paradoxes. HEM leverages asymmetric cryptography to establish trust and exchange a key, and then transitions to symmetric cryptography for efficient data handling. The process works in three essential steps:
- Key Negotiation: Asymmetric algorithms, typically Elliptic Curve Diffie, Hellman Ephemeral (ECDHE), are utilized during a secure handshake to securely negotiate an ephemeral symmetric key.
- Key Transport/Derivation: The asymmetric method ensures that this newly generated symmetric key is only known to the authorized parties. The high initial computational cost of the asymmetric step is viewed as the necessary architectural overhead for secure key derivation and key distribution, establishing the foundational trust required for the session.
- Bulk Encryption: Once the session key is established, all subsequent high, volume application data is encrypted rapidly using the symmetric cipher (e.g., AES, GCM), utilizing its high, throughput capabilities.
This integrated model forms the backbone of essential protocols such as Transport Layer Security (TLS/HTTPS), Secure Shell (SSH), and modern end, to, end encrypted messaging systems. Furthermore, symmetric algorithms like AES are highly standardized (NIST, FIPS) and integrated deeply into system hardware (AES, NI) for rapid confidentiality, placing them clearly within the “data transport layer.” Asymmetric algorithms, conversely, are utilized within the broader Public Key Infrastructure (PKI) ecosystem (certificates, revocation lists), defining them as the critical components of the “trust establishment layer.”
Table 1 provides a comparison of the fundamental characteristics of these two cryptographic architectures.
| Feature | Symmetric Encryption (e.g., AES, ChaCha20) | Asymmetric Encryption (e.g., RSA, ECC, DH) |
| Key Usage | Single secret key for encryption and decryption. | Key pair: Public key (encrypt/verify) and Private key (decrypt/sign). |
| Speed/Efficiency | Extremely fast (MB/s throughput); ideal for bulk data. | Very slow (operations/sec); impractical for large data. |
| Primary Roles | Confidentiality, Integrity, Data Authentication (AEAD). | Key Exchange, Digital Signatures, Identity Authentication. |
| Key Distribution | Requires secure channel or use of asymmetric method. | Public key is openly shared; only the private key needs protection. |
| Foundational Concept | Substitution, Permutation Networks (SPN) or Stream Ciphers. | Mathematical problems (factoring large numbers or discrete logarithms). |
Symmetric Cryptography: The Architecture of Performance and Implementation Risk
Symmetric cryptography is defined by its speed, primarily enabled by two leading algorithms: AES and ChaCha20. Analysis of these algorithms reveals that while key length provides theoretical security, practical security hinges entirely on implementation quality and robust key hygiene.
Advanced Encryption Standard (AES) Structure and Security Margins
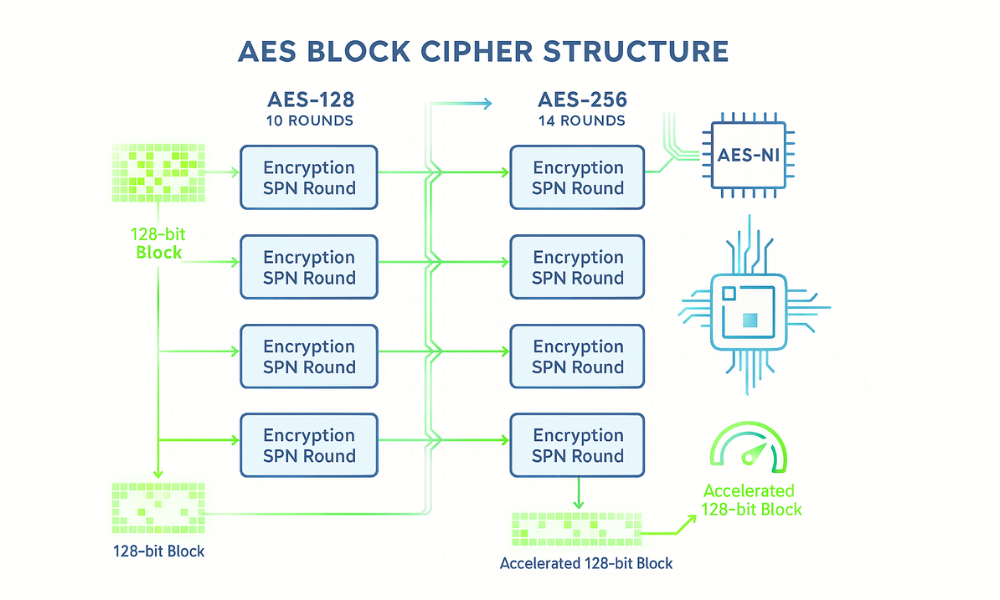
AES, originally named Rijndael, was selected by NIST for its strength, efficiency, and flexibility, becoming the established gold standard for encrypting sensitive information globally. AES is a Substitution–Permutation Network (SPN) block cipher operating on fixed 128, bit blocks. AES supports three specific key sizes: 128 bits, 192 bits, and 256 bits. The key size directly dictates the number of processing rounds performed during encryption:
- AES, 128 employs 10 rounds of processing.
- AES, 192 employs 12 rounds of processing.
- AES, 256 employs 14 rounds of processing.
The theoretical security margin provided by AES, 128 is overwhelmingly robust. A brute, force attack against a $2^{128}$ key space is considered infeasible by modern technology. Even leveraging the estimated aggregate computational power of massive systems, such as the Bitcoin network at its peak, cracking a single AES, 128 key would require an estimated $10^{23}$ years. While academic attacks exist that are theoretically faster than brute force (e.g., the biclique attack on AES, 128 with a complexity of $2^{126}$), none of these known cryptanalytic attacks are currently computationally feasible.
Performance Dynamics: The Hardware Acceleration Dictate
The practical performance difference between AES, 128 and AES, 256 is negligible on modern hardware. Although AES, 256 requires 40% more operational rounds than AES, 128 (14 vs. 10), dedicated hardware instructions, such as Intel’s AES, NI and ARM crypto extensions, minimize the processing time. These CPU features drastically accelerate the cipher execution, leading to speeds for both AES, 128 and AES, 256 becoming “virtually identical” on modern processors.
However, the speed difference becomes pronounced when hardware acceleration is unavailable. In pure software implementations, the added overhead of AES, 256’s extra rounds can result in a measurable performance degradation (benchmarks suggest around 20% difference in some software contexts). On embedded devices, low, power systems, or architectures without AES, NI, this performance gap can manifest as a significant operational bottleneck, particularly when handling high volumes of transactions.
Consequently, AES, 128 provides formidable protection sufficient for most web applications and everyday use cases, offering a superior balance of security and speed. AES, 256 is typically reserved for environments with stringent compliance demands, such as government or military operations, or for long, term data archiving where resilience against future theoretical quantum threats is a primary concern.
Alternative Symmetric Ciphers: ChaCha20, Poly1305
ChaCha20, usually paired with the Poly1305 authenticator, offers a high, performance alternative to AES, particularly favored in scenarios where hardware diversity or software efficiency is critical. ChaCha20 functions as a stream cipher, processing data sequentially (byte, by, byte), which simplifies integration into communication protocols and negates the need for complex block cipher padding.
ChaCha20, Poly1305 is heavily optimized for software execution across varied CPU architectures (especially 32, bit platforms). For systems lacking dedicated AES instructions, such as certain embedded microcontrollers or mobile devices, ChaCha20 often provides faster, more consistent, and more power, efficient encryption than software, only AES implementations. The popular modern VPN protocol, WireGuard, explicitly mandates the use of ChaCha20, Poly1305, highlighting the cipher’s preference among developers seeking consistent performance without reliance on proprietary hardware acceleration. This strategy positions ChaCha20 as the preferred cross, platform standard due to its inherent resistance to certain side, channel attacks and consistent speed profile.
Implementation Risks: The Threat to Confidentiality and Integrity
The security of modern symmetric cryptography is not challenged by brute force, instead, it is compromised by implementation failures and environmental side effects. The focus has pivoted from key size concerns to implementation integrity and strict cryptographic hygiene.
Authenticated Encryption and Nonce Reuse
Contemporary cryptographic design requires Authenticated Encryption with Associated Data (AEAD) modes, such as AES, GCM or ChaCha20, Poly1305. AEAD modes provide both data confidentiality and guaranteed integrity, eliminating common attack vectors associated with earlier, non, authenticated modes like CBC.
- The most severe implementation failure is the reuse of an Initialization Vector (IV) or Nonce (N) with the same key.
- For AES, GCM, a single nonce reuse is catastrophic.
- This error reduces the scheme to a two, time pad, immediately compromising the confidentiality of the plaintexts (allowing an adversary to decrypt one if the other is known).
- Furthermore, nonce reuse can leak the authentication key material, allowing the adversary to forge subsequent messages with high probability.
- Therefore, adherence to the principle of using a unique and unpredictable IV for every encryption operation under a single key is mandatory.
Side, Channel Vulnerabilities
System attacks rarely target the mathematical strength of ciphers but instead exploit information leakage from the hardware or software execution environment.
- Cache and Timing Attacks exploit variations in execution time or memory access patterns (e.g., data, dependent table lookups used in some software implementations of AES S, boxes).
- An unprivileged process running concurrently on the same processor can monitor the CPU’s memory cache state.
- By observing these inter, process leakage patterns, attackers can deduce memory access sequences and fully recover the secret encryption key from operations performed by other processes, such as OpenSSL or Linux encrypted partitions (dm, crypt).
- In one experimental demonstration, the full key of a Linux dm, crypt volume was recovered in just 65 milliseconds after only 800 writes.
- Mitigation against these practical threats includes the use of constant, time implementations of ciphers, code engineered to execute in the same time regardless of the input data, and the reliance on dedicated Hardware Security Modules (HSMs) to isolate keys from exploitable software environments.
Table 2 summarizes the characteristics and implementation context of the leading symmetric algorithms.
| Algorithm | Type | Key Size (Bits) | Standard Mode | Hardware Accelerated | Primary Advantage |
| AES, 128 | Block Cipher (128, bit block) | 128 | GCM (AEAD) | Yes (AES, NI/ARM Crypto) | Maximum throughput on server/desktop hardware. |
| AES, 256 | Block Cipher (128, bit block) | 256 | GCM (AEAD) | Yes (AES, NI/ARM Crypto) | Compliance, long, term security margin. |
| ChaCha20 | Stream Cipher (512, bit block) | 256 | Poly1305 (AEAD) | No (Software, optimized) | Performance portability, efficiency on embedded systems, constant, time design. |
Asymmetric Cryptography: Key Management, Trust, and Authentication
The fundamental purpose of asymmetric cryptography within the hybrid model is not data encryption but rather the establishment of trust and the secure exchange of the symmetric session key. These functions are critical for session integrity and future resilience.
Fundamental Asymmetric Algorithms and Roles
Asymmetric schemes rely on complex mathematical foundations to manage key pairs. ECC is increasingly preferred over traditional RSA due to its efficiency, it provides equivalent security levels with much smaller key sizes, leading to faster computations and shorter transaction times.
The critical role of asymmetric algorithms is in key establishment. Algorithms based on Diffie, Hellman (DH) and its elliptic curve variant (ECDH) are essential because they allow two parties to collaboratively derive a shared secret key over an otherwise insecure communication channel, removing the need for pre, shared secrets beyond the known public keys.
Perfect Forward Secrecy (PFS) in Key Exchange
Modern protocols, particularly TLS 1.3, mandate Perfect Forward Secrecy (PFS) to protect against future compromises of long, term identity keys. PFS is realized through the use of Ephemeral Diffie, Hellman key exchange (ECDHE).
- In an ECDHE session, the key pair used for the session key exchange is generated uniquely and randomly for that specific session and is immediately discarded upon completion.
- This means that even if an attacker were to compromise the server’s long, term private signing key (stored in its certificate) at a later date, they would gain no information allowing them to decrypt past communication traffic, as the ephemeral session key used for derivation no longer exists.
- This ephemeral approach is a direct rejection of older methods, such as static RSA key exchange, where the compromise of the long, term private key would retroactively expose all recorded past sessions encrypted with keys wrapped by that static key.
The architectural evolution of these systems demonstrates a critical strategic shift: the asymmetric key pair is now viewed less as a key, wrapping tool and more as a secure entropy source utilized for ephemeral session key generation (ECDHE), thereby minimizing the lifetime and exposure of the most security, critical assets.
Identity and Digital Signatures
Asymmetric cryptography is also the basis for identity verification via Public Key Infrastructure (PKI). During a TLS handshake, the server must authenticate itself to the client. This is achieved when the server presents its digital certificate, which contains its public key, and then uses its corresponding private key to generate a digital signature over the key materials established during the handshake. This signature proves ownership of the private key and assures the client that the symmetric session key was negotiated with the legitimate entity, successfully thwarting man, in, the, middle attacks.
It is important to note that while the mathematical strength of asymmetric algorithms (e.g., RSA 2048 or ECC 256) is highly robust, the practical failure points in asymmetric security often lie outside the cryptography itself. The complexity of the PKI ecosystem, specifically the administrative processes of distributing, verifying, and reliably revoking digital certificates (e.g., via Certificate Revocation Lists or OCSP), poses a greater operational threat than the mathematical feasibility of breaking the underlying keys.
Hybrid Encryption in Practice: Application Case Studies
The deployment of symmetric and asymmetric cryptography is best understood by analyzing their specific roles within established applications.
Case Study 1: Secure Network Communication (TLS 1.3/HTTPS)
Transport Layer Security (TLS) 1.3 provides the definitive blueprint for the Hybrid Encryption Model in network communications.
Handshake Phase (Asymmetric Dominance)
- The TLS handshake begins with the client sending a list of supported parameters, including preferred AEAD cipher suites (e.g., AEAD, AES128, GCM, SHA256, AEAD, CHACHA20, POLY1305, SHA256).
- The server and client then engage in an ECDHE key exchange using ephemeral key pairs to derive a high, entropy master secret. This step is designed to enforce PFS.
- Concurrently, the server authenticates its identity by transmitting its certificate and using its long, term private key to digitally sign key establishment messages, proving ownership of the certified public key.
Data Transfer Phase (Symmetric Dominance)
- The established master secret is then fed into a Key Derivation Function (HKDF) to generate the ephemeral symmetric session keys and Initialization Vectors (IVs) required for the bulk transfer, designated as [sender]_write_key and [sender]_write_iv.
- All application data is subsequently encrypted and authenticated at high speed using the chosen symmetric cipher suite (AES, GCM or ChaCha20, Poly1305).
Case Study 2: End, to, End Messaging (Signal Protocol)
Secure end, to, end encryption (E2EE) systems, exemplified by the Signal Protocol, require continuous key renewal to ensure both forward secrecy (protecting past messages if the current key is compromised) and backward secrecy (protecting future messages if the current key is compromised).
The Signal Protocol utilizes the Double Ratchet Algorithm to achieve this high standard of security. The system combines two key renewal mechanisms:
- Diffie, Hellman Ratchet (Asymmetric): This mechanism uses Elliptic Curve Diffie, Hellman (ECDH), specifically Curve25519, to periodically mix a new asymmetric shared secret into the communication path. This step ensures key renewal based on ephemeral asymmetric key exchange, guaranteeing forward secrecy.
- Key Derivation Function (KDF) Ratchet (Symmetric): Between the asymmetric key updates, a symmetric key ratchet, typically based on HMAC, SHA256, continually derives a new, unique message key for every single message sent. This rapidly cycling symmetric process ensures backward secrecy (or future secrecy).
The actual encryption of message content is handled by a fast symmetric cipher, historically AES, CBC/CTR, but increasingly AES, GCM or ChaCha20, Poly1305 are favored.
Case Study 3: Data Storage and VPNs (Symmetric, Focused)
For applications requiring high, throughput encryption of massive, local data volumes, the symmetric element dominates.
Full, Disk Encryption (FDE)
FDE solutions prioritize speed, using symmetric algorithms exclusively for bulk data protection.
- BitLocker (Windows): The default encryption algorithm is AES, with a default key length of 128 bits. While 256 bits is configurable, the AES, 128 default reflects the high industry confidence in its security margin combined with its performance advantage.
- VeraCrypt (Cross, Platform): This volume encryption tool defaults to the AES algorithm. Although the specific default key size is not explicitly documented in the initial setup guides, the underlying key file generation can produce keys up to 512 bits. The common selection of AES, 128 in FDE solutions, such as BitLocker, over AES, 256 for standard operations serves as a clear indicator of prioritizing engineering performance and minimal resource drain unless external compliance mandates the higher key size.
Modern VPNs (WireGuard)
WireGuard uses a hybrid approach, but its selection of symmetric cipher emphasizes cross, platform efficiency. It uses Curve25519 (asymmetric ECDH) for the key exchange and establishment phase. However, all subsequent high, speed tunnel traffic is encrypted using ChaCha20, Poly1305 (symmetric AEAD). This strategic choice ensures consistent, high performance even on mobile or embedded devices that may lack dedicated AES hardware.
Architectural Recommendations and Future Proofing
For any modern system architecting security, adherence to best practices in implementation and key management is paramount, as this now represents the weakest link in cryptographic security.
Key Management and Derivation Strategies
The robustness of symmetric encryption is intrinsically tied to the quality of its key management. A strong symmetric key size (e.g., $2^{256}$) is functionally irrelevant if the input entropy (e.g., a human password) is weak. The security of the system is ultimately determined by the strength of the weakest component.
- Therefore, keys must never be derived directly from user input.
- Robust Key Derivation Functions (KDFs), such as Argon2id, scrypt, or PBKDF2, must be employed.
- These functions are designed to be computationally expensive by incorporating significant work factors (iterations, memory consumption) that force an adversary to expend excessive time and resources on offline dictionary or brute, force attacks, thereby effectively extending the “strength” of the underlying human secret.
- For highly sensitive long, term secrets and private asymmetric keys, physical security is essential.
- Utilizing dedicated Hardware Security Modules (HSMs) or Trusted Platform Modules (TPMs) is crucial.
- These devices isolate the keys from the operating system, providing a physical layer of defense against software, based extraction and side, channel attacks.
Mitigation of Implementation Risks
Given that practical attacks target implementation flaws over mathematical weaknesses, strict hygiene measures must be enforced:
- Constant, Time Implementation: Cryptographic libraries must guarantee constant, time execution to prevent timing and cache side, channel attacks, particularly where AES is utilized on shared cloud infrastructure or virtualized environments.
- AEAD Nonce Discipline: Unique Nonce or IV generation for every encryption operation under a single key is mandatory when using AEAD modes (GCM, Poly1305). System designers must implement robust noncing mechanisms to ensure uniqueness, as single reuse events can lead to catastrophic security failure and message forgery.
Strategic Selection: AES versus ChaCha20
The choice between the two leading symmetric ciphers should be guided by the target platform architecture:
- Server and Desktop Environments: AES, GCM should be the default, provided the underlying CPU architecture supports and utilizes hardware acceleration (AES, NI). Prioritize AES, 128 for general throughput unless compliance or extreme longevity requirements mandate AES, 256.
- Mobile, Embedded, and IoT Devices: ChaCha20, Poly1305 offers superior performance consistency and is the recommended default. Its software optimization ensures minimal power drain and reliable speed across diverse, often resource, constrained, hardware architectures.
Quantum Resilience and Cryptographic Agility
Current standards rely on mathematics vulnerable to theoretical quantum algorithms. While the massive scale of quantum computing required to break AES is not yet realized, strategic planning is essential. Grover’s algorithm theoretically halves the effective security margin of symmetric keys, meaning AES, 128 becomes $2^{64}$, bit secure. Therefore, AES, 256, offering an effective $2^{128}$, bit security post, quantum, is a prudent choice for protecting data required to remain confidential for decades.
For asymmetric cryptography (RSA, ECC), which is entirely broken by Shor’s algorithm, the strategy is shifting toward cryptographic agility, designing systems capable of rapidly transitioning to new, quantum, resistant algorithms (PQC candidates) without extensive architectural redesign. The integration of ECDHE for ephemeral key derivation in modern protocols makes such transitions more manageable by isolating the key establishment phase from the bulk data encryption phase.
Frequently Asked Questions
What is the primary difference in speed between symmetric and asymmetric encryption?
Symmetric encryption (e.g., AES) is extremely fast, with throughput measured in Megabytes per second (MB/s), making it ideal for bulk data. Asymmetric encryption (e.g., RSA) is very slow, with performance measured in operations per second, making it wholly impractical for encrypting large datasets.
Why is the Hybrid Encryption Model (HEM) necessary for secure communications?
HEM is necessary because neither system is sufficient on its own. Symmetric encryption is fast but has the “key distribution problem,” meaning a secure way to share the secret key is needed. Asymmetric encryption solves the key distribution problem securely but is too slow for bulk data. HEM uses the slow, secure asymmetric method for key exchange and then switches to the fast symmetric method for data transfer.
What is Perfect Forward Secrecy (PFS) and how is it achieved?
Perfect Forward Secrecy (PFS) is a property that ensures a compromise of a server’s long, term private key will not allow an attacker to retroactively decrypt past communication sessions. It is achieved through the use of Ephemeral Diffie, Hellman key exchange (ECDHE), where the key pair used for the session key is generated uniquely and randomly for each session and immediately discarded.
What is the greatest risk to the security of modern symmetric ciphers like AES?
The greatest risk is not the mathematical strength of the key size (AES, 128 is overwhelmingly robust), but rather implementation failures and side, channel attacks. The most severe implementation failure is the reuse of an Initialization Vector (IV) or Nonce (N) with the same key in AEAD modes (e.g., AES, GCM), which can lead to catastrophic security compromise.
When should an architect choose ChaCha20-Poly1305 over AES-GCM?
ChaCha20, Poly1305 should be chosen for mobile, embedded, and IoT devices, or any system lacking dedicated AES hardware acceleration (AES, NI). ChaCha20 is heavily optimized for consistent, efficient software execution across diverse CPU architectures, ensuring reliable speed and minimal power drain where hardware resources are constrained.
What is the role of Hardware Security Modules (HSMs) in a cryptographic architecture?
Hardware Security Modules (HSMs) or Trusted Platform Modules (TPMs) are crucial for key management. They provide a physical layer of security by isolating sensitive long, term private keys from the operating system and software environment, protecting them against software, based extraction and side, channel attacks.
Conclusions
The comparison between symmetric and asymmetric encryption demonstrates a complementary relationship formalized by the Hybrid Encryption Model. Symmetric encryption (AES, ChaCha20) is essential for rapid bulk data confidentiality, while asymmetric encryption (ECC, RSA, DH) is irreplaceable for establishing authenticated key exchange, guaranteeing identity, and enforcing Perfect Forward Secrecy.
The current frontier of cryptographic engineering centers not on increasing key length, where AES, 128 is already considered overwhelmingly sufficient against classical brute force, but on ensuring implementation integrity. Real, world security is predominantly compromised by architectural failures, such as poor Nonce management in AEAD modes (e.g., AES, GCM), and side, channel vulnerabilities (e.g., cache timing attacks) that exploit software flaws in constant, time execution.
For application deployment, strategic choices include:
- For High, Power Servers: Prioritize AES, GCM with hardware acceleration (AES, NI), defaulting to AES, 128 for maximum performance unless compliance dictates AES, 256.
- For Embedded/Mobile Devices: Default to ChaCha20, Poly1305 for its superior, consistent, and power, efficient software performance.
- Key Management: Investment in robust Key Derivation Functions (KDFs) like Argon2id and the use of Hardware Security Modules (HSMs) are mandatory requirements to protect keys from both dictionary attacks and physical extraction attempts.
