The Cryptographer’s Toolkit: Salt, IV, Nonce, and KDFs, Why They Make Passwords Safer
Stop treating a password like a simple string input. Modern cryptography views the human passphrase as a seed that must be processed through multiple defensive layers to become a cryptographically robust master key.
The complexity required to defeat a modern encrypted system is not measured only in the time it takes to test keys, but in the exponential cost of specialized hardware and energy required by an attacker. By correctly implementing Key Derivation Functions (KDFs) with Salt and unique Nonces, security engineers ensure this cracking cost remains astronomically high.
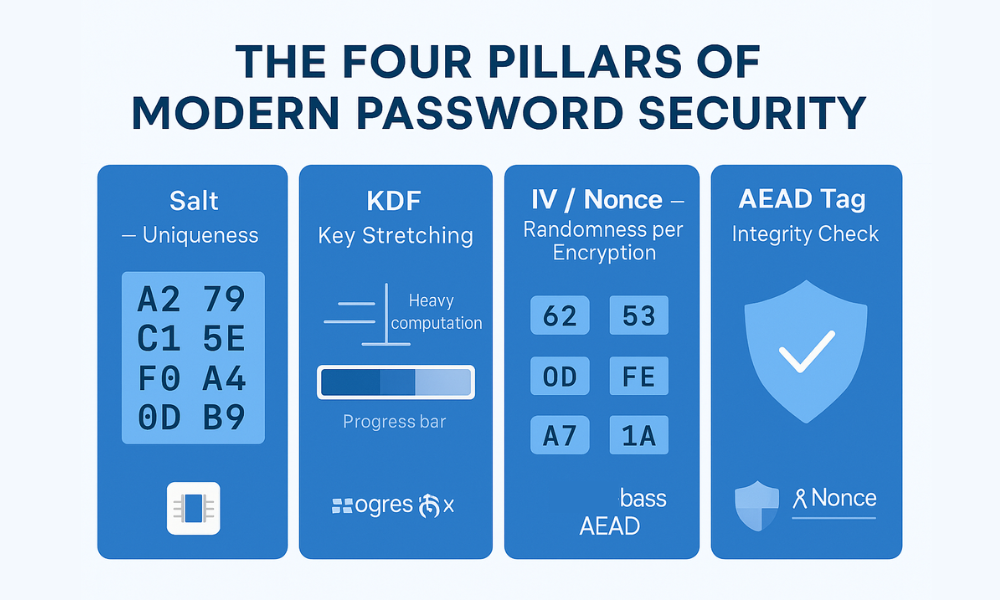
I. Lead with the Answer: The Four Pillars of Modern Password Security
The modern security model operates on a principle of layered defense primitives. These components mitigate specific, well, known cryptographic attacks that simple password hashing alone cannot stop:
- Salt: Guarantees that the same password generates a unique derived key or hash. This neutralizes pre, computed attacks like rainbow tables by forcing a unique calculation for every user, even if they share a common password.
- KDF (Key Derivation Function): Deliberately maximizes the computational time and/or memory resources required per password guess. This technique, called key stretching, makes large, scale brute force financially and temporally infeasible.
- Initialization Vector (IV) / Nonce (Number Used Once): Ensures that encrypting identical plaintexts with the same secret key yields completely different ciphertexts. This randomness safeguards the data stream against pattern recognition and key stream leakage.
The Justification for Complexity: Historical Failures
Reliance on legacy or simplified standards presents an immediate threat. The foundational shift from Data Encryption Standard (DES) to modern ciphers was necessary because the original 56, bit DES key space was easily defeated by brute force. For instance, the Electronic Frontier Foundation’s (EFF) Deep Crack machine broke a DES key in just 56 hours in 1998.
Even the subsequent enhancement, Triple DES (3DES), which effectively uses a 168, bit key, is now officially retired by NIST and deprecated by standards bodies like PCI DSS. This decision was driven by its susceptibility to the meet, in, the, middle attack, which reduces the effective security margin, proving it inadequate against current computing power.
If a system relies on outdated mechanisms like legacy ZIPCrypto, which is inherently vulnerable to known, plaintext attacks, or anything older than the current AES standard, its stored data is already functionally compromised against a determined attacker. The continuous enhancement of password security mechanisms is a required response to the continuous advancement of attack hardware.
II. The Core Problem: Why Simple Hashes Are Too Fast
Standard cryptographic hash functions, such as SHA, 256, are excellent tools for verifying data integrity, but they are catastrophically inefficient for securing passwords. They are intentionally designed to execute in nanoseconds across all processor types. An attacker leveraging modern GPU parallelization can check billions of simple hashes per second, making a dictionary or brute, force attack trivial against fixed, unstretched hashes.
2.1 Pillar 1: Salt, Randomness for Uniqueness
The primary defense against mass pre, computation attacks is the Salt.
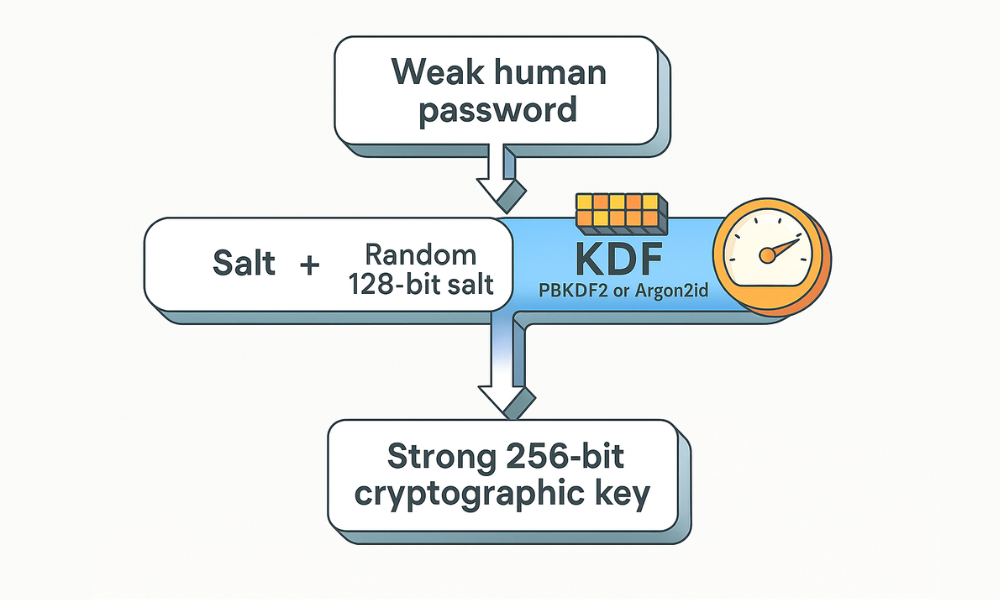
The Salt mechanism works by generating a unique, randomly generated cryptographic string for every user’s password. This unique Salt is appended to the user’s passphrase before the hashing or key derivation process begins.
The importance of the Salt lies in its ability to enforce uniqueness. If two users select the exact same weak password, for example, “123456”, their unique salts ensure that the final derived key or stored hash is completely different. This forces an attacker to compute every possible password combination against every stored salt individually. The computational and storage requirement for pre, calculating a table (a rainbow table) covering common passwords combined with every possible salt value is prohibitively immense.
Implementation Standard: Salt Length
The cryptographic efficacy of the Salt depends entirely on its length and randomness. If a salt is too short, an attacker can revert to pre, computation by pre, calculating every likely password combined with every possible short salt value. To ensure a sufficiently large and random space that counters cryptographic phenomena like the Birthday Paradox when applied to hash generation, security standards mandate a minimum Salt length of 16 bytes (128 bits). This length dramatically minimizes the risk of two unique passwords accidentally generating the same output hash.
2.2 Pillar 2: Key Derivation Functions (KDFs), Making Work Harder
A KDF applies key stretching, using controlled time and resource consumption as a primary defense. A KDF transforms the relatively weak entropy of a human, chosen password into a strong, fixed, length cryptographic key (the master key) suitable for a cipher like AES, 256.
Instead of one instantaneous hash calculation, a KDF performs hundreds of thousands or even millions of sequential operations (time cost) or forces the process to consume huge amounts of memory (memory cost). This translates a nanosecond operation into a hundreds, of, milliseconds operation, exponentially increasing the barrier to entry for an adversary attempting a brute, force attack.
III. Deep Dive: Configuring Modern KDFs (PBKDF2 Versus Argon2)
The choice and configuration of the KDF represent the most fundamental architectural decision in modern password security infrastructure.
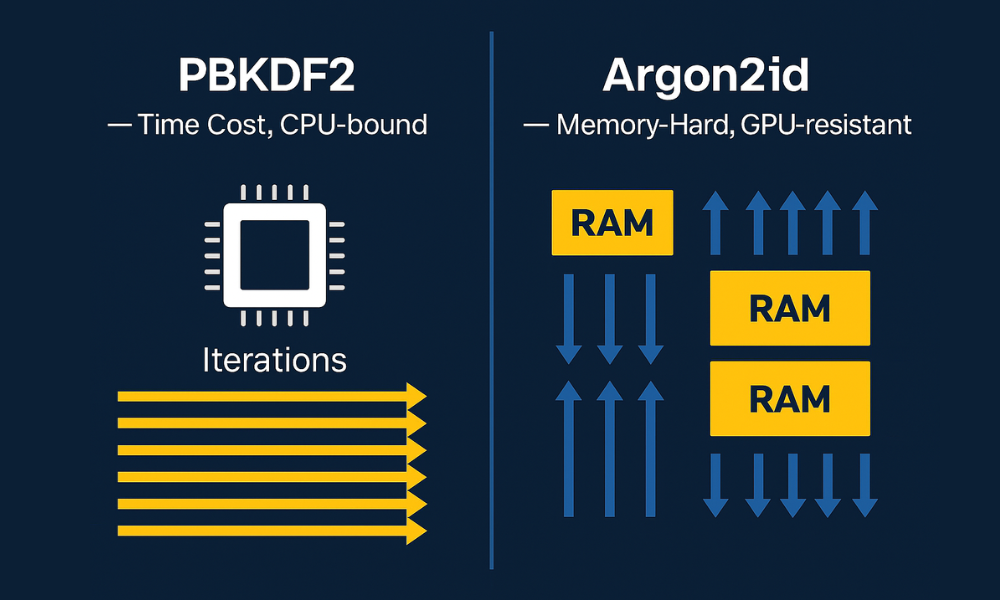
3.1 PBKDF2: The Reliable, Standard Workhorse
PBKDF2 (Password, Based Key Derivation Function 2) is a mature and widely adopted standard. It is frequently utilized in large frameworks and operating systems, including Windows Encrypting File System (EFS), where the implementation typically uses HMAC based on SHA, 256.
Mechanism and Configuration
PBKDF2’s defense relies purely on maximizing sequential CPU cycles. It repeatedly applies the standard hashing algorithm (e.g., HMAC, SHA256) for a specified number of iterations ($i$) to stretch the key.
The key to securing PBKDF2 lies in setting the iteration count ($i$) appropriately. This parameter must be tuned to consume approximately 500 milliseconds (0.5 seconds) of CPU time on the target hardware where the key verification occurs. OWASP, recognizing the need to counter accelerating hardware, advises a minimum of 600,000 iterations for PBKDF2, HMAC, SHA256, a significantly higher threshold than older, legacy defaults which might only specify 1,000 iterations.
KDF Obsolescence: The Time Cost Trap
PBKDF2’s dependence on sequential CPU cycles creates an inherent vulnerability to technological progress. As central processing unit (CPU) performance continues to increase, the security level provided by a fixed iteration count degrades over time. An iteration count that required 500 milliseconds in 2020 might only require 250 milliseconds in 2024, functionally halving the security margin without any change to the code base.
Developers must treat the iteration count not as a static setting, but as a variable that requires periodic, systematic increase, perhaps yearly, to maintain a consistent security threshold against hardware acceleration. Failure to dynamically adjust this parameter results in a functional security regression.
3.2 Argon2: The Memory, Hard Champion
Argon2, the winner of the Password Hashing Competition (2015), is the current industry champion because it directly addresses the architectural flaw inherent in PBKDF2: the weakness against massive parallelization attacks.
Defeating Parallelization
The core problem with PBKDF2 is that its defense, sequential CPU cycles, can be bypassed by attackers using inexpensive, highly parallel GPUs or FPGAs. These specialized hardware platforms can test millions of passwords simultaneously, easily overwhelming a time, based defense.
Argon2 shifts the attack bottleneck from calculation time ($t$, time cost) to memory consumption ($m$, memory cost). Argon2’s memory, hard design requires the constant, high, volume consumption of slow, to, access RAM during the key derivation process. This architectural defense forces the attacker to invest in expensive, large, capacity, and slow RAM arrays rather than cheap, fast computing cores, making large, scale, parallel attacks cost, prohibitive.
Argon2 Modes and Configuration
Argon2 offers several modes, but Argon2id is universally recommended by OWASP. This hybrid mode provides a crucial balance, offering resistance to side, channel timing attacks (a strength of Argon2i) while maintaining resistance to parallel brute, force attacks (the strength of Argon2d).
Tuning Argon2id requires careful consideration of the three primary resource parameters:
- Memory Cost ($m$): This is the primary defense, measured in kibibytes (KiB). It must be set as high as the target environment allows without triggering a denial, of, service for legitimate users. OWASP provides specific trade, offs, recommending settings such as 12 MiB memory cost combined with 3 iterations, or 46 MiB memory cost combined with 1 iteration.
- Time Cost ($t$): The number of passes over the memory block. If the memory cost is set very high (e.g., 46 MiB), a low time cost (e.g., $t=1$) is often adequate. If memory is constrained (e.g., mobile devices), increasing the time cost (e.g., to $t=4$) compensates for the lower memory cost.
- Parallelism ($p$): This defines the number of concurrent threads or lanes utilized. This value should typically be set equal to the number of available CPU cores to maximize the legitimate user’s performance efficiency during login.
IV. The Cipher’s Defense: Initialization Vector (IV) and Nonce
Once a robust key is derived using a KDF, it must be used securely with a symmetric cipher, such as AES, 256. The use of an Initialization Vector (IV) or a Nonce ensures that the encryption operation itself is non, deterministic, meaning that identical blocks of input data will never produce identical blocks of output ciphertext.
4.1 IV Versus Nonce: The Non, Repetition Mandate
The terms IV and Nonce are often conflated but have distinct requirements dictated by the cipher mode employed.
- Initialization Vector (IV): Typically used in older block cipher modes like AES, CBC, which requires a 16, byte (128, bit) input. The IV must be both unique and unpredictable (random) to prevent chosen, plaintext attacks. If the IV is predictable, the first ciphertext block can leak information about the plaintext.
- Nonce (Number Used Once): Used in modern stream ciphers and Authenticated Encryption with Associated Data (AEAD) modes, such as AES, GCM or ChaCha20, Poly1305. The Nonce only needs to be unique (never repeated) for any given key. Nonces can, therefore, be generated deterministically, often as a simple sequential counter.
4.2 The Catastrophic Failure: Nonce Reuse in AEAD
The core security requirement for modern AEAD modes is Nonce uniqueness. While the Nonce is not a secret, it is usually transmitted openly alongside the ciphertext, reusing it under the same encryption key is extremely dangerous.
In AES, GCM, the use of a repeated Nonce is globally classified as a “catastrophic failure,” leading to a total loss of confidentiality and integrity guarantees. Nonce reuse in GCM allows an attacker to recover key stream information and, more critically, to derive the GHASH subkey used for authentication. This derivation enables an attacker to forge messages successfully and potentially achieve full decryption.
Mitigation through Nonce Size
Standard AES, GCM uses a 96, bit (12, byte) Nonce. To manage the statistical risk of accidental collision (Nonce reuse) when generating random Nonces, NIST limits the number of messages that can be encrypted with a single key to $2^{32}$.
A more robust architectural approach is seen in XChaCha20, Poly1305, which employs a large 192, bit (24, byte) Nonce. This significantly larger Nonce space provides a statistically massive pool that virtually mitigates the risk of accidental collision, even when generated randomly, allowing the system to operate more safely where stateful counters cannot be guaranteed.
V. Case Study: Authenticated Encryption (AEAD) Standards
Modern applications must combine encryption (confidentiality) with message authentication (integrity) into a single primitive, known as Authenticated Encryption with Associated Data (AEAD).
5.1 Why Data Integrity Matters
AEAD ciphers calculate an Authentication Tag (MAC) over both the ciphertext and any associated data (AAD) that needs integrity protection but not secrecy.
This integrity protection is crucial. It ensures that an attacker cannot maliciously modify the ciphertext during transmission without the modification being detected. If the tag verification fails during decryption, often indicated by an error like GCMInvalidTagException, the system must reject the entire message. This prevents the output of potentially corrupted or manipulated plaintext, thereby defending against integrity breaches and padding oracle attacks.
5.2 AEAD Comparison: Performance, Portability, and Trust
The selection of an AEAD cipher depends heavily on the deployment environment and the availability of hardware acceleration. The two industry, leading standards are AES, GCM and ChaCha20, Poly1305.
Table: Advanced Encryption Comparison: AES, GCM Versus ChaCha20, Poly1305
| Feature | AES, GCM (NIST Standard) | ChaCha20, Poly1305 (IETF Standard) |
|---|---|---|
| Primary Cipher | AES (Block Cipher) | ChaCha20 (Stream Cipher) |
| MAC Algorithm | GHASH | Poly1305 |
| Nonce Size | 96 bits (12 bytes) | 192 bits (24 bytes – XChaCha20 recommended) |
| Hardware Acceleration | Widespread (AES, NI instructions) | Limited/Generic SIMD |
| Software Performance (No AES, NI) | Suboptimal; susceptible to timing side, channel attacks | Excellent and Constant, Time |
| Performance Benchmark (M3 Pro CPU, 1MB Block) | ~1.8 GB/s (Software Only) | ~4.2 GB/s (Software Only) |
| Optimal Use Case | Server environments with Intel/AMD AES, NI support. | Mobile (ARM), cloud functions, or environments without guaranteed hardware acceleration. |
Decision Matrix for Implementation
The data illustrates a clear trade, off:
- AES, GCM is the optimal choice for high, throughput, guaranteed enterprise environments, such as large data centers leveraging Intel or AMD CPUs with AES, NI instructions. Under hardware acceleration, AES, GCM can achieve phenomenal speeds, often below 1 cycle per byte (cpb).
- ChaCha20, Poly1305 is superior for cross, platform applications, mobile devices (which primarily use ARM, based CPUs), or general software implementations. Without dedicated hardware instructions, ChaCha20, Poly1305 typically delivers better, more consistent software performance (demonstrated as 2.3 times faster than software AES, GCM on Apple M3 Pro CPUs for 1MB blocks) and provides inherent resistance to timing side, channel attacks often missed in software implementations of AES.
VI. Secure File Encryption Tutorial: Deploying AES, 256 via 7, Zip
This practical overview uses the common, open, source 7, Zip utility to demonstrate the successful deployment of KDF key stretching and AES standards for securing files and metadata.
Outcome: Archive and encrypt sensitive files using AES, 256 with a KDF, derived key, ensuring confidentiality of both content and file names.
Prereqs & Safety:
- Tool: 7, Zip (desktop utility).
- Safety Warning: The encryption system is designed to provide high assurance. If the master password is lost or forgotten, the data is cryptographically unrecoverable.
Step, by, Step Overview: Creating a Secure.7z Locker
- Select File and Initiate Archiving: Locate the sensitive file or directory containing the data. Right, click the item and select 7, Zip > Add to Archive…
- Set Encryption Standard: In the ‘Add to Archive’ configuration dialog, locate the Encryption section. The Archive format should be set to
.7z.- Set Encryption Method to AES, 256.
- Configure Key Derivation and Password: Enter a unique, complex password (a long passphrase of 15 or more characters is highly recommended).
- KDF Implementation: The 7, Zip tool automatically uses an internal PBKDF2 function based on the SHA, 256 hash algorithm. This function applies a substantial number of iterations to derive the 256, bit AES cipher key from the text password, satisfying the requirement for key stretching.
- The Metadata Gotcha (Crucial Step): This step protects the file names, which are a critical piece of metadata. You must check the box labeled “Encrypt file names”.
- Failure Implication: If this box is not checked, an attacker can open the archive, see the list of contents (e.g., “Q4_Financials.xlsx” or “Employee_PII.txt”), and understand the scope of the confidential data, even if the content itself remains unreadable. Encrypting metadata is mandatory for comprehensive security.
- Finalize and Verify: Click OK to generate the encrypted
.7zarchive file.
- Verify It Worked: Right, click the new
.7zfile and select Test Archive. It should confirm integrity. When attempting to open the archive, the utility must immediately prompt for the password before displaying the list of file names, confirming that metadata encryption is active.
Proof of Work Block: Settings Snapshot (7, Zip)
| Parameter | Setting |
|---|---|
| Archive Format | 7z |
| Encryption Algorithm | AES, 256 |
| Key Derivation Function | PBKDF2, SHA256 (Internal Iterations Applied) |
| Metadata Protection | “Encrypt file names” ON |
Sharing the Encrypted File Safely
Once a file is encrypted using a strong algorithm and KDF, the archive can be transferred safely via relatively insecure channels, such as email or standard cloud upload. The critical final layer is key management: The decryption password must always be shared with the recipient via a separate, secure communication channel. This means transmitting the file via email, then sending the password via text message, phone call, or an end, to, end encrypted messenger like Signal. Never send the file and the key in the same conversation thread.
VII. Troubleshooting: When Key Derivation and Decryption Fails
Cryptographic protocols are inherently fragile, and failures often stem from implementation or key management errors, not algorithmic flaws. Misaligned KDF parameters, IV/Nonce misuse, or lost keys are the most frequent causes of catastrophic failure.
Table: Key Derivation and Decryption Troubleshooting: Symptoms and Fixes
| Symptom / Error String | Root Cause (Ranked) | Non, Destructive Fix / Test | Last, Resort Option / Warning |
|---|---|---|---|
The specified file could not be decrypted (EFS Error 0x80071771 or 6001) |
1. EFS private key/certificate is missing or corrupted (common after OS reinstallation). 2. File was moved from an NTFS partition to a non, NTFS format (EFS is NTFS, dependent). | Import the private key/PFX file via Windows Certificate Manager (certmgr.msc) to the ‘Personal > Certificates’ store. Check the certificate details for confirmation of the private key presence. |
If the EFS private key backup (.pfx) is irretrievably lost, the files are permanently inaccessible. |
GCMInvalidTagException or AEADBadTagException |
1. Ciphertext or Associated Data (AAD) was tampered with during transmission (integrity breach). 2. Nonce was reused with the same key. | Immediately halt all processing and reject the message. The error confirms the data integrity defense mechanism has successfully detected tampering. System logs should be checked for Nonce generation issues. | This outcome indicates a successful forgery attempt or catastrophic implementation flaw (Nonce reuse). The encryption key must be rotated, and all messages encrypted with the potentially compromised Nonce should be considered vulnerable. |
Wrong IV length: must be 16 bytes long |
IV length mismatch for the requested cipher mode (e.g., attempting to use a 12, byte Nonce in AES, CBC mode, which requires 16 bytes). | Confirm the specific cipher mode being initialized. Adjust the IV generation function to produce the precise required length (e.g., 16 bytes for CBC, 12 bytes for GCM). | This is an implementation configuration error only. It carries no inherent data loss risk unless the library defaults to an insecure or dangerous mode. |
| File opens, but contents are garbage; no error given. | Incorrect key derived from the password because the wrong KDF parameters (salt, iteration count $i$, or memory cost $m$) were used during attempted decryption. | Decryption must precisely match the parameters used during encryption. Verify that the KDF parameters stored alongside the ciphertext or metadata are exactly matched during the key derivation function call. | If the KDF parameters were not stored securely or logged correctly, the decryption key cannot be replicated, likely leading to irrecoverable data loss. |
The Key Management Threat (EFS Example)
Analysis of decryption failures consistently points toward key management rather than the mathematical breakdown of the algorithm. The specific Windows EFS error 0x80071771 illustrates that file, level encryption is rendered useless if the system responsible for holding the decryption authority (the user’s private certificate key) is lost or corrupted, such as after an operating system reinstallation.
This situation enforces the absolute necessity of security layering. BitLocker, which encrypts the entire drive, is essential because it secures the underlying system drive where EFS stores its root secrets and private keys. EFS is functionally dependent on the security provided by full, disk encryption to protect its keys from physical attackers who might bypass the operating system.
VIII. Essential Context and Final Recommendations
8.1 The Difference Between Encryption and Encoding
A prevalent security mistake is confusing encoding with encryption. Encoding, such as Base64 or Hex, is a reversible process used to transmit binary data over systems designed for text, like email or certain web APIs.
Encoding a 256, bit AES key into a Base64 string adds zero security. If an attacker gains access to the Base64 representation of a key, they instantly possess the key itself. True security requires strong cryptographic primitives like AES, 256, secured by KDF, derived keys, protected by unique Nonces/IVs, and not merely obscured by reversible encoding.
8.2 Security Through Layering
Data protection requires applying multiple levels of defense, leveraging the distinct capabilities of each tool:
- Full Disk Encryption (BitLocker): This protects the entire device and the core operating system files, using AES, XTS/CBC 128, bit or 256, bit modes, specifically defending against offline tampering and physical device theft.
- File Level Encryption (EFS/7, Zip): This provides fine, grained, per, user, or per, file protection (AES, 256) necessary for controlling access between multiple users on a single machine or for selectively sharing data.
- Transport Encryption (AEAD): This protects data in motion using modern, authenticated protocols like ChaCha20, Poly1305 or AES, GCM, ensuring both confidentiality and integrity when moving data across insecure networks.
IX. Frequently Asked Questions (FAQs)
1. Is a KDF the same as a hash function like SHA-256?
No. Standard hash functions are optimized for speed, which is counterproductive for password security. A KDF intentionally uses key stretching or memory, hardness to create a process designed to be computationally slow, protecting weak human passwords from high, speed cracking attempts.
2. What happens if a Nonce is reused in AES-GCM mode?
Nonce reuse in GCM mode is considered a catastrophic failure. It allows attackers to recover the internal authentication key (GHASH key) and subsequently forge messages, severely compromising data integrity and potentially enabling full data decryption.
3. Why should Argon2id be chosen over PBKDF2?
Argon2id is a memory, hard KDF, forcing attackers to commit high amounts of expensive, slow, access RAM for effective computation. This specifically counters modern parallelized attacks using GPUs, which PBKDF2 is vulnerable to, thereby maximizing the financial cost barrier for adversaries.
4. How long should a cryptographic Salt be?
The standard minimum recommended length for a cryptographic salt is 16 bytes (128 bits). This length provides a sufficiently large salt space to prevent efficient pre, computation or collision attacks using rainbow tables.
5. Is Base64 encoding secure for protecting secrets?
No. Base64 is only a reversible structural encoding method. It provides zero confidentiality and should never be mistaken for encryption.
6. Why is AES-256 preferred over AES-128 in high-security roles?
AES, 256 (using 14 rounds versus 10) offers a higher security margin against unforeseen attacks. It is specifically required by the US government for protecting TOP SECRET classified information and offers better resistance against future quantum computing attacks.
7. What is the practical difference between an IV and a Nonce?
An IV (used in CBC mode) must be both non, repeating and random. A Nonce (used in AEAD modes like GCM) must only be non, repeating or unique. A Nonce can therefore often be generated deterministically (e.g., as a sequential counter).
8. Why choose ChaCha20-Poly1305 for a mobile app?
ChaCha20, Poly1305 delivers excellent, consistent, and constant, time software performance on mobile devices (typically ARM CPUs) where hardware acceleration like AES, NI is unavailable. It is significantly faster and more power, efficient than software implementations of AES, GCM.
9. Why is protecting file names necessary during encryption?
Failure to encrypt file names (metadata) compromises privacy. It exposes sensitive information about the data’s contents or nature (e.g., names like “Q4_Budget.xlsx”), even if the content remains encrypted and unreadable.
10. Can files be recovered if the EFS certificate is lost?
If the original EFS private key or the certificate backup (.pfx file) is lost or corrupted, the files encrypted with that key are designed to be permanently unrecoverable. This ensures the foundational confidentiality promise of the encryption system.
11. Why do cloud services block password-protected ZIP files?
Cloud services often enforce Data Loss Prevention (DLP) policies that block password, protected containers because encryption prevents the cloud provider from scanning the contents for malware, viruses, or sensitive data that is subject to regulatory compliance (like PCI or HIPAA data).
12. Does BitLocker eliminate the need for EFS?
No. BitLocker is full, disk encryption against offline attacks. EFS provides fine, grained, per, user file encryption. BitLocker is crucial because it protects the system drive where EFS stores its own key secrets, forming a necessary layer of defense against sophisticated physical attackers.
13. What is the standard KDF used by Windows EFS?
Windows EFS commonly uses PBKDF2 based on SHA, 256 for key derivation, reflecting its widespread adoption in native operating system security features.
14. What are the key parameters for tuning Argon2?
Argon2 is primarily tuned using three parameters: Memory Cost ($m$), Time Cost ($t$, iterations), and Parallelism ($p$, lanes). Memory Cost is considered the most effective defense parameter against dedicated hardware parallel attacks.
15. What are the minimum required iterations for PBKDF2-SHA256?
Due to advances in hardware, security organizations like OWASP now recommend a minimum of 600,000 iterations for PBKDF2, HMAC, SHA256 to ensure that the key stretching process consumes approximately 500 milliseconds, thereby maintaining adequate security margins.
X. Conclusion
The security of any system relying on human, generated passwords does not rest on the complexity of the final cipher (e.g., AES, 256) but on the integrity of the preprocessing steps. Modern security mandates the layered application of primitives: Salt prevents rainbow table attacks by ensuring unique per, user hashes; Key Derivation Functions (KDFs) like Argon2 or PBKDF2 apply key stretching to maximize the financial and temporal cost barrier for brute, force attempts; and Nonces (or IVs) guarantee stream randomness and safeguard against pattern, based attacks.
The architectural choice of KDF, particularly selecting a memory, hard function like Argon2id over a CPU, sequential function like PBKDF2, is critical for defending against modern GPU parallelization. Similarly, choosing an Authenticated Encryption with Associated Data (AEAD) cipher (AES, GCM or ChaCha20, Poly1305) and strictly enforcing Nonce uniqueness is non, negotiable, as reuse is a catastrophic failure that instantly compromises the system. Ultimate security is achieved by adopting this layered defense, ensuring constant, time implementation, and correctly managing metadata, thereby transforming a weak human secret into a cryptographically robust master key.
