The Hybrid Handshake: How RSA and AES Combine to Secure Your Data
This comprehensive overview, brought to you by the security experts at Newsoftwares.net, details the essential mechanism behind digital trust: Hybrid Encryption. By expertly combining the speed of the symmetric Advanced Encryption Standard (AES) with the trust of asymmetric Public-Key Cryptography (RSA), this model delivers both unparalleled data security and convenience. Learn the inner workings of the two-step key-exchange process, crucial for securing everything from confidential emails to multi-gigabyte backups, ensuring your privacy and data integrity.
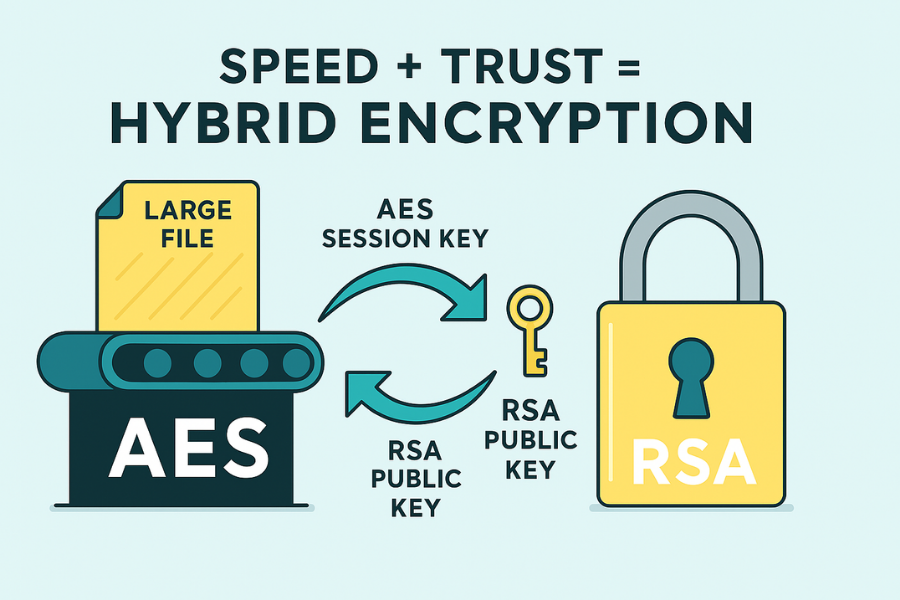
You can’t secure a website using only RSA, and you can’t encrypt a multi-gigabyte backup using only AES. Trying either method on its own fails instantly: one is too slow, and the other can’t establish trust. The core problem in digital security is how to securely and efficiently share a secret over an untrusted network.
The solution isn’t one algorithm, but a sophisticated two-step dance called Hybrid Encryption. This model, which runs every time you open a secure website, uses the speed of AES for data and the trust of RSA for keys.
This overview breaks down exactly why this handshake works, how key apps like HTTPS and PGP use it, and provides the step by step tutorials needed to implement or troubleshoot the crucial hybrid mechanism.
Why Two Keys Are Better Than One: Speed Versus Trust
The hybrid model exists because the two main types of cryptography have opposite strengths. Security architects must combine them to create a functional system.
Symmetric Encryption: Built for Speed
Symmetric ciphers, like the Advanced Encryption Standard (AES), use a single secret key to encrypt and decrypt data.
- Role: Confidentiality and data integrity.
- Speed: Extremely fast. AES-256 can process data at speeds measured in megabytes per second (MB/s). This high throughput is why AES is the only viable choice for encrypting large databases, streaming video, or entire hard drives (Full Disk Encryption).
- The Flaw (The Key Problem): Before any data can be exchanged, both parties must somehow agree upon and securely share this single secret key. If you can’t securely deliver the key, the entire symmetric system collapses.
Asymmetric Encryption: Built for Trust
Asymmetric ciphers, such as RSA and Elliptic Curve Cryptography (ECC), use a mathematically linked pair of keys: a public key (shared openly for encryption) and a private key (kept secret for decryption).
- Role: Identity verification, digital signatures, and secure key transport.
- Speed: Very slow. RSA-2048 operations are measured in operations per second (ops/sec). Trying to encrypt a 1 GB file with RSA would take hours, making it impractical for bulk data.
- The Strength (Key Exchange): You can encrypt a message (like a small secret key) using someone’s public key, and only they can open it with their private key. This ability to share a secret without ever exchanging the private key solves the symmetric key distribution problem.
Table 1: Performance Comparison, AES Versus RSA
The performance gap is massive, reinforcing why bulk data handling must be delegated to the symmetric AES component.
| Feature | Symmetric (AES-256) | Asymmetric (RSA-2048) | Primary Use |
| Speed/Throughput | High (MB/s) | Low (Ops/sec) | Data Encryption |
| Computational Cost | Low | High (Orders of magnitude slower) | Key Exchange/Signing |
| Key Type | Single, Shared Secret Key | Public/Private Key Pair | Trust and Identity |
| Core Principle | Efficiency and Confidentiality | Non-Repudiation and Key Transport |
The Core Hybrid Encryption Model: Step by Step
Hybrid encryption leverages the asymmetric key pair to securely wrap the symmetric key, which in turn secures the actual message. This process is the architectural heart of applications from web browsers to encrypted file utilities.
The Mechanism of Hybrid Key Exchange
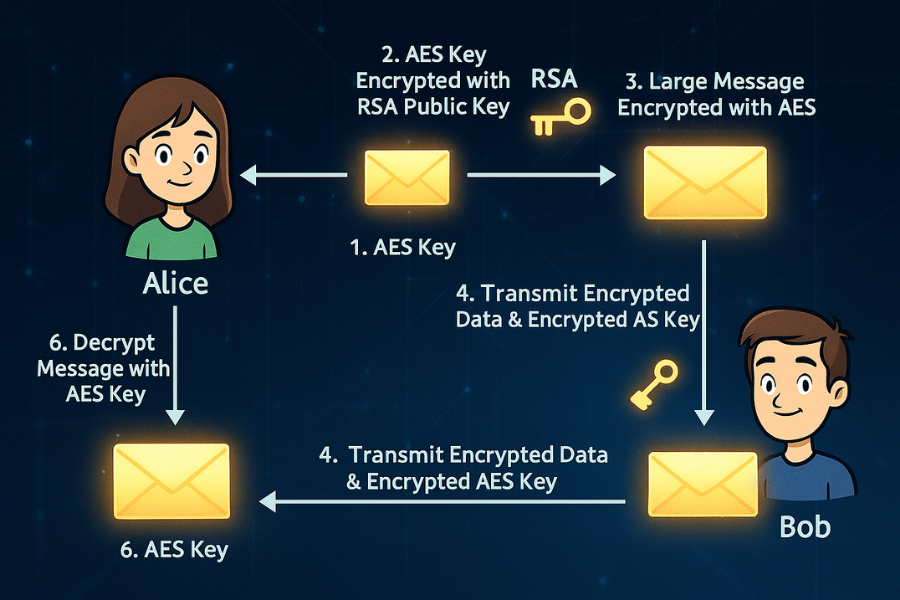
Here is the five step process that allows two parties, Alice (Sender) and Bob (Recipient), to share a large, secure file:
- AES Session Key Generation (The Secret Letter): Alice’s software generates a random, single use symmetric session key (e.g., a 256 bit AES key). This key is only used for this one file or communication session and is highly volatile. This makes the bulk encryption fast and efficient.
- Asymmetric Wrapping (The Mailbox Lock): Alice takes the AES session key and encrypts it using Bob’s public key (RSA or ECC). Only Bob’s corresponding private key can unlock this session key.
- Data Encryption (The Package): Alice uses the fast, unencrypted AES session key to encrypt the large message or file data.
- Transmission (The Secure Package): Alice sends Bob the encrypted message/file and the small, encrypted AES session key wrapped by Bob’s public key.
- Decryption (Unlocking):
- Bob uses his secret private key to decrypt the small, wrapped AES session key.
- Bob then uses the now revealed AES session key to rapidly decrypt the large message or file.
The high cost of RSA encryption is applied only to the small session key, while the efficient AES cipher handles the heavy lifting of the data itself.
Case Study 1: Securing the Web (TLS/HTTPS)
When you see the padlock icon in your browser, the website is running a hybrid handshake via the Transport Layer Security (TLS) protocol, which underpins HTTPS.
While earlier TLS versions used static RSA to wrap the key, modern TLS 1.3 is far more advanced, focusing on Perfect Forward Secrecy (PFS). The server’s RSA key is now primarily used for identity, while a different asymmetric method (ECDHE) handles key exchange.
The Modern TLS 1.3 Handshake (ECDHE + AES-GCM)

Modern browsers and servers (like Cloudflare) rely on Elliptic Curve Diffie, Hellman Ephemeral (ECDHE) for speed and PFS, but the server’s RSA or ECC certificate key still authenticates the connection.
| Step | Protocol | Mechanism | Purpose |
| 1. Negotiation | TLS (Start) | Client Hello | Client and server agree on an AEAD cipher suite (e.g., AEAD-AES128-GCM-SHA256). |
| 2. Key Exchange | Asymmetric (ECDHE) | Ephemeral Key Generation | Client and server generate temporary, one time (ephemeral) ECDHE key pairs. They use these public keys to jointly calculate a unique, shared Master Secret. |
| 3. Authentication | Asymmetric (RSA/ECC) | Digital Signature | The server uses its permanent private key (from its RSA certificate) to sign the key exchange parameters. This proves its identity and ensures the Master Secret negotiation wasn’t intercepted. |
| 4. Session Key Derivation | Symmetric (HKDF) | Key Derivation Function | The shared Master Secret is fed into a Key Derivation Function (HKDF) to generate the actual AES Session Keys and Nonces. |
| 5. Data Transfer | Symmetric (AES-GCM) | Bulk Encryption | All subsequent data (website content, credit card numbers) is rapidly encrypted and authenticated using the derived AES session key. |
Actionable Insight: Check Your Cipher Suites
Cloudflare recommends prioritizing the fastest, most secure cipher suites for TLS 1.3, which includes AEAD-AES128-GCM-SHA256 and AEAD-CHACHA20-POLY1305-SHA256. This reinforces that AES-128 is the preferred workhorse for maximum web performance.
Case Study 2: Secure File Sharing (PGP/GPG)
Pretty Good Privacy (PGP) and its open source equivalent, GnuPG (GPG), are the hybrid standard for encrypting files, emails, and code commits. PGP strictly follows the five step hybrid model outlined earlier.
Tutorial: Encrypting a File with GPG (Hybrid PGP)
To send a file to a recipient, say Bob, using their public key:
Supply and Tool: GnuPG (GPG) utility. Recipient’s public key (imported).
- Identify Recipient’s Key: Ensure you have Bob’s public key imported.
gpg --list-keys
(Look for Bob’s user ID and a key fingerprint). - Execute Hybrid Encryption: Use GPG’s command line to encrypt the file (document.txt). GPG automatically handles the hybrid process.
gpg --encrypt --recipient "Bob's User ID" document.txt - GPG’s Hybrid Process (Internal):
- GPG generates a random, one time AES session key (symmetric).
- GPG uses the AES session key to encrypt
document.txt(bulk data). - GPG uses Bob’s public key to encrypt the AES session key (key wrapping).
- GPG bundles the encrypted file and the encrypted session key into a single output file (e.g.,
document.txt.gpg).
- Verification: The output file is only decryptable by Bob’s private key. The security is now tied to the safety of Bob’s private key and the AES algorithm’s integrity.
Troubleshooting PGP/GPG Decryption Failures
PGP decryption failures almost always stem from a key mismatch, not algorithmic failure.
| Symptom | Exact Error String (Common) | Root Cause | Fix/Actionable Insight |
| Cannot decrypt file. | no secret key |
The system lacks the required private key that corresponds to the public key used for encryption. | Use gpg --list-secret-keys to verify the private key is present in the keyring. Import the correct private key and passphrase. |
| Cannot decrypt file (though key is present). | Incompatible private key for this file’s decryption |
The encrypting party may have used the wrong public key, or the private key is corrupted. | Ensure the sender used the exact key ID you intended. Use key management software (like Kleopatra) to confirm the key pair is functional. |
| Decryption succeeds, but data looks corrupted/wrong. | (No explicit error, but output is junk) | Sender/receiver used incompatible GPG versions or algorithms (less common, but possible). | Check gpg --version on both systems to ensure compatibility. Confirm the symmetric key algorithm (e.g., AES-256) was agreed upon and correctly derived. |
The Real Weak Links: Implementation Flaws
Regardless of whether RSA-4096 is used to wrap an AES-256 key, the entire hybrid system’s practical security is compromised by mistakes in implementation, not by brute force attacks against the mathematics.
Symmetric Attack Vector: Nonce Reuse
AES-GCM (the standard mode in TLS) provides confidentiality and integrity, but it is dangerously fragile if implemented incorrectly.
- The Pitfall: Reusing the Initialization Vector (IV) or Nonce (N) with the same symmetric key is catastrophic.
- The Consequence: A single nonce reuse allows an adversary to immediately leak the XOR sum of plaintexts (a two time pad) and gives them a very high chance of forging subsequent messages.
- The Fix: Mandate unique, unpredictable Nonces for every encryption operation under a single key. Protocols like TLS 1.3 enforce strict rules for generating new keys and IVs for every session, using cryptographic hash functions (HKDF) to ensure uniqueness.
Asymmetric Attack Vector: Weak Key Management
The private key is the ultimate secret in the hybrid system. If an attacker gains the private key, they can decrypt all past and future traffic secured by that key.
| Failure Point | Impact | Mitigation Strategy |
| Weak Passphrases | Allows dictionary attacks against the private key file (e.g., PGP key file). | Always use a strong, long passphrase to encrypt the private key. Use Key Derivation Functions (KDFs) like Argon2id or scrypt when deriving keys from passwords. |
| Key Mismanagement | Private key stored on an unsecured disk or exposed in memory. | Store long term RSA/ECC private keys within a Hardware Security Module (HSM) or a Trusted Platform Module (TPM). |
| Incorrect Key Size | Using key lengths that aren’t supported by the standard (e.g., 190 bits). | AES is limited to 128, 192, or 256 bits. Using keys of other sizes triggers immediate errors (Key length not 128/192/256 bits) or leads to incorrect algorithm selection. |
Real World Hybrid Implementation Tutorials
Successfully deploying hybrid encryption requires mastering the configuration of your applications, whether for disk encryption or secure file transfer.
Setting up Key Derivation (Essential for Passwords)
When encrypting a disk (like with VeraCrypt or BitLocker) or a file (PGP), the symmetric AES key is often derived from a passphrase. The KDF adds computational cost to the key generation, making dictionary attacks infeasible.
KDF Proof of Work Block (Example Argon2id)
To secure a password derived key for an encrypted file container:
- Action: Derive a 256 bit AES key from the user’s password.
- Setting Snapshot: Use a modern KDF like Argon2id, configured with a high work factor:
argon2id(password, salt, iterations=100000, memory=65536). - Verification: Ensure the system automatically stores the Salt alongside the encrypted data or file container header. Without the unique salt, the key derivation fails.
Full Disk Encryption (FDE): The Symmetric Workhorse
FDE focuses on bulk data, using AES almost exclusively, but key management relies on the hybrid trust model (using the TPM/TPM keys or password/KDF).
Example: Microsoft BitLocker
- Default Algorithm: AES-128.
- AES-128 Versus AES-256: BitLocker defaults to 128 bit because it is overwhelmingly sufficient against classical threats and delivers optimal performance with hardware acceleration. Use 256 bit only if mandated by extreme policy or compliance.
Example: VeraCrypt
- Default Algorithm: AES.
- Key Derivation Function: VeraCrypt uses strong KDFs (like SHA-512) to generate the master key and key material.
- Tutorial Snippet (Volume Creation): In the volume creation wizard (Step V), the Encryption Algorithm defaults to AES. This selection confirms the system is using the fast symmetric cipher for all subsequent data encryption within the container.
Frequently Asked Questions (FAQs)
Q1. Why don’t applications just use RSA to encrypt all the data?
RSA is computationally intense because of the complex mathematics involved (factoring large prime numbers). Encrypting a large file with RSA would take orders of magnitude longer than with AES, making it impractical for everyday use. AES is thousands of times faster for bulk data.
Q2. Does my secure VPN (WireGuard/OpenVPN) use RSA and AES?
Yes, but often a variant. WireGuard uses the faster ECC (Curve25519) instead of RSA for the asymmetric key exchange. It then uses the high performance symmetric cipher ChaCha20-Poly1305 (a modern alternative to AES) for all data traffic. OpenVPN supports both AES and ChaCha20, depending on the configuration.
Q3. Can AES-GCM really be cracked if I reuse the Nonce?
Yes, reusing the Nonce with the same key in AES-GCM is catastrophic. This error leaks critical information and allows an attacker to decrypt plaintexts and forge new, authenticated messages with high probability. Never reuse an IV or Nonce under the same key.
Q4. Is a 4096-bit RSA key more secure than a 256-bit AES key?
The sizes are not directly comparable. They serve different purposes. The 4096 bit RSA key secures the initial key exchange (trust layer), while the 256 bit AES key secures the bulk data (speed layer). Both must be strong for the hybrid system to work.
Q5. What is a “Session Key,” and why is it used only once?
A session key is a temporary, randomly generated symmetric key (usually AES-128 or AES-256) used only for a single communication session or file encryption. Using it only once minimizes the window of exposure, ensuring that if that single key is ever compromised, only one file or session is affected.
Q6. Are timing and side-channel attacks more dangerous than brute force?
Yes. Brute force attacks against AES-128 are computationally impossible today. In practice, attackers target much easier flaws, such as side channel attacks (SCA) that observe variations in the CPU’s power or timing, which can expose the secret key in milliseconds.
Q7. If RSA is so slow, why is it still used?
RSA is still widely used in certificates and PKI because it provides the robust framework for identity and digital signatures. This allows a server to prove who it is, even if a faster, ephemeral asymmetric algorithm (like ECDHE) is used for the key exchange itself.
Q8. Does Hybrid Encryption make the encrypted message bigger?
Yes, slightly. The message size increases because you must attach the small, RSA encrypted symmetric session key and the Initialization Vector (IV)/Nonce to the encrypted bulk data. This overhead is minimal compared to the size of the bulk data being protected.
Q9. What is the difference between encryption and digital signing?
Encryption (using public key) ensures confidentiality (only the private key holder can read the message). Digital signing (using private key) ensures authenticity and non-repudiation (proves the message came from the private key holder).
Q10. What happens if I use an unsupported key size like 190 bits for AES?
AES only supports 128, 192, and 256 bit keys. If you attempt to use an unsupported length (e.g., 190 bits, or 20 characters in a string), your application will throw an IllegalArgumentException or similar error, requiring the key length to be corrected.
Q11. Which KDF should I use to secure my password for disk encryption?
Use a modern, memory hard Key Derivation Function like Argon2id or scrypt. These functions are intentionally resource intensive, which drastically slows down an attacker’s ability to perform offline brute force attacks against your password.
Conclusion
The Hybrid Encryption model, leveraging the unique strengths of asymmetric (RSA/ECC) and symmetric (AES/ChaCha20) cryptography, remains the cornerstone of modern digital security. By delegating key transport to the slower, trust based asymmetric algorithms and bulk data processing to the efficient symmetric algorithms, secure communication is made both scalable and practical. True security, however, lies not just in the algorithms, but in diligent implementation, particularly rigorous key management and the mandated use of unique Nonces for every operation.
