Preparing Apps for Post, Quantum Crypto: Inventory, Crypto Agility, Safe Pilots
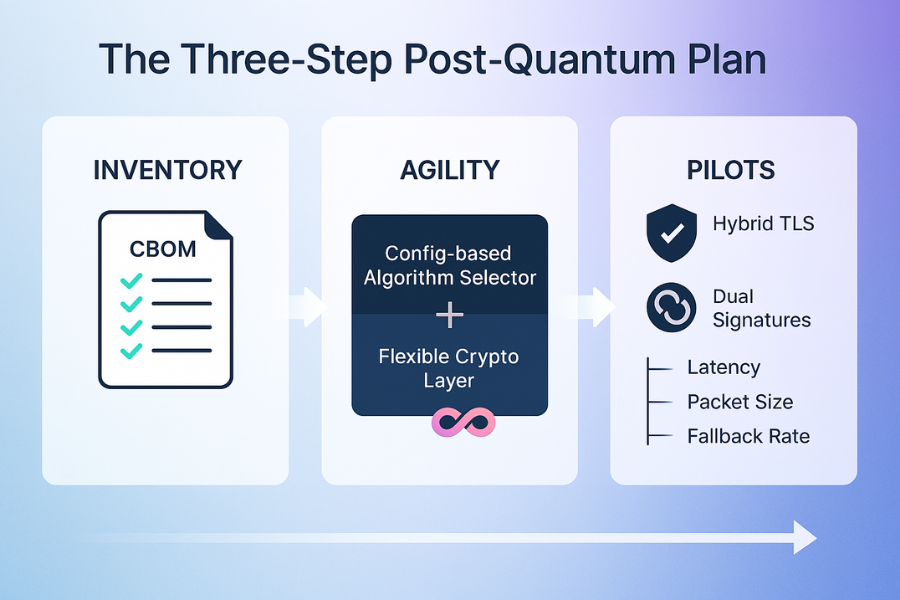
This essential overview, created for the modern security team by Newsoftwares.net, provides a direct, three, step plan to prepare applications for post, quantum cryptography (PQC). You get ready for postquantum by doing three things in order. First, build a full cryptography inventory that lists every protocol, library, key size, and trust path your code uses. Second, make your apps crypto agile so you can swap algorithms without code rewrites. Third, run small, measured pilots with NIST selected postquantum algorithms, usually in hybrid mode with classical curves, and capture latency, size, and compatibility impact before you scale. This structured approach ensures a verifiable, secure, and convenient transition.
Direct Answer
You get ready for postquantum by doing three things in order. First, build a full cryptography inventory that lists every protocol, library, key size, and trust path your code uses. Second, make your apps crypto agile so you can swap algorithms without code rewrites. Third, run small, measured pilots with NIST selected postquantum algorithms, usually in hybrid mode with classical curves, and capture latency, size, and compatibility impact before you scale.
Verifiable Preparation Plan
Most guides say upgrade TLS and call it a day, or they jump straight to new algorithms and skip the drudge work. What is missing is a practical inventory method you can finish in weeks, a repeatable way to make protocols swappable, and a pilot plan that does not break mobile clients, SSO, or hardware modules. This guide keeps the good parts security teams already do, key rotation, TLS scanning, and fills the gaps with specific checklists, error strings, test fixtures, and roll back points.
Three Core Outcomes
- You will ship a usable crypto bill of materials for every app and service, not a spreadsheet that rots.
- You will add crypto agility to the code paths that matter, TLS, REST signing, data at rest, and SSO tokens.
- You will finish one safe pilot that proves performance and compatibility, with clear pass or hold gates.
Plain Terms that Keep Teams Aligned
| Term | One line meaning | Why it matters |
|---|---|---|
| Postquantum cryptography | Algorithms designed to resist large quantum computers | Classical RSA and ECC are vulnerable to Shor, type attacks |
| Hybrid key exchange | Classical curve plus postquantum KEM in one handshake | Keeps today secure while testing tomorrow |
| Crypto agility | Ability to change algorithms and parameters through config | Avoids rewrites and emergency releases |
| KEM | Key encapsulation mechanism for key exchange | Replaces ECDH in many handshakes |
| PQ signature | Signature scheme used for identity and code signing | Replaces ECDSA or RSA signatures |
| CBOM | Crypto bill of materials | Lets you scope work and audits quickly |
Use Case Chooser
Pick your row, start there, and expand.
| Situation | Priority | First move | Notes |
|---|---|---|---|
| Internet facing web apps on TLS | High | Enable hybrid TLS between front end and origin where supported | Leave public edge on proven stacks with fallback |
| Mobile API clients | High | Add crypto agility to HTTP client and token verification | Measure payload growth and battery impact |
| Internal service mesh | Medium | Pilot PQ KEM in mesh mTLS channel between two low risk services | Watch handshake CPU and packet size |
| Data at rest archives | Medium | Wrap long term archives with a hybrid key wrap plan | Keep decrypt path simple and audited |
| Code signing and firmware | High for devices with long lives | Add PQ signature pilot in parallel signing track | Validate boot ROM and verification path limits |
| SSO and identity | High | Evaluate PQ ready tokens or detached proofs | Keep classical verification in place until vendors certify |
Security Specifics that Actually Work Today
| Component | Safe default | Why |
|---|---|---|
| TLS handshake | Hybrid X25519 plus a PQ KEM where available | Keeps current security and collects data |
| PQ KEM choice | NIST selected KEMs from maintained libraries | Use stable implementations, avoid research code |
| PQ signature choice | NIST selected signature families for signing pilots | Start with detached test channels before production |
| Token design | Preserve JWT claim shapes, avoid Base64 bloat where possible | Limits parsing churn across services |
| Agility layer | Opaque key and algorithm identifiers, not enums in code | Add new IDs without redeploying |
| Key storage | HSM or KMS with clear label scheme that includes algorithm | Prevents mix ups and eases rotation |
| Telemetry | Handshake time, packet size, CPU, fallback rates | Lets you justify or pause the rollout |
How to Move from Zero to Pilot
This is the core playbook. Each step gives one action, one screenshot to capture for your runbook, one gotcha to watch, and a verify outcome.
Step 1. Build a Crypto Inventory without Stopping the World
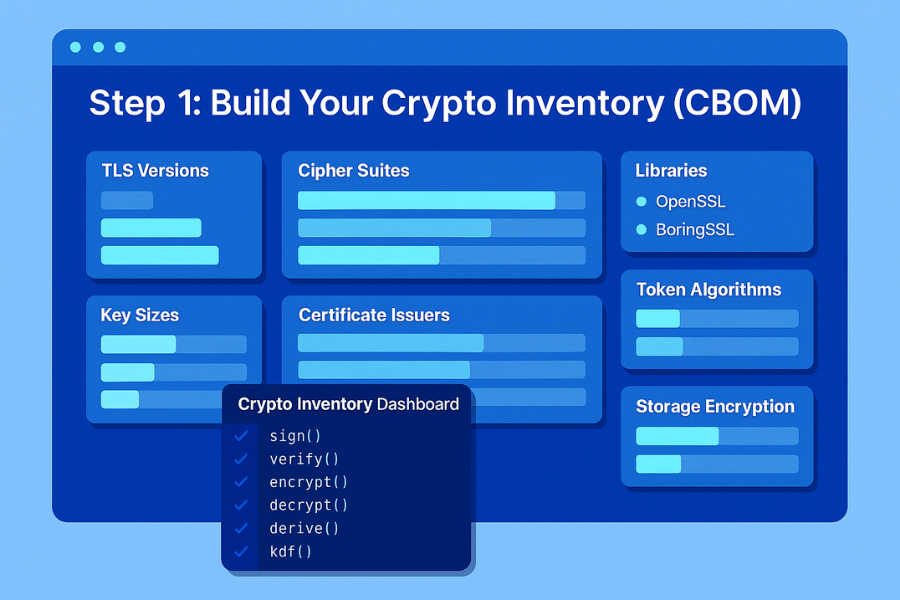
Action. Generate a CBOM from code plus runtime. Parse source for crypto API calls, then validate with packet captures and TLS scans in lower environments. Record protocol, library, key sizes, certificates, token types, and storage encryption settings.
Screenshot to capture. Your CBOM viewer listing each service with TLS version, cipher suites, cert issuers, and code references.
Gotcha. Teams often miss signing and verification done in helper libraries or vendor SDKs. Search for verify, sign, encrypt, decrypt, derive, and kdf across repos, then confirm with runtime logs.
Verify it worked. You can answer in minutes which apps still use RSA key exchange, which libraries rely on OpenSSL, BoringSSL, or platform TLS, and where tokens are verified.
Step 2. Make the Code Agile before Touching Algorithms
Action. Introduce a crypto policy object loaded from config. It should pick algorithm families, parameter sets, and key IDs at runtime. Ensure each call site uses an interface with injectible providers.
Screenshot to capture. A config screen or YAML snippet that maps use cases to algorithms. Example tls.kex hybrid, storage.wrap aes keywrap, token.sig ecdsa p256.
Gotcha. Do not bake algorithm lists into enums that require a rebuild to add new values. Treat them as opaque strings. Route through a capability registry so unknown types are rejected cleanly.
Verify it worked. Swap a curve or KDF in a test build only by changing config. CI runs drift tests that refuse unknown or deprecated choices.
Step 3. Prepare Keys and Labels You Will Not Regret
Action. Define a key label scheme that encodes use, algorithm, creation date, and tenant. Provision test keys in your KMS or HSM for classical and PQ families. Plan rotation and disable windows.
Screenshot to capture. Key list in KMS with labels like svcA tls kex hybrid 2025q1 and archive wrap hybrid 2025q1.
Gotcha. Mixing signing and encryption under one key label creates audit pain. Separate namespaces for sign, exchange, and wrap.
Verify it worked. You can rotate one label without touching others, and your audit report shows which services used which keys in the last 90 days.
Step 4. Turn On Hybrid TLS in a Small Path
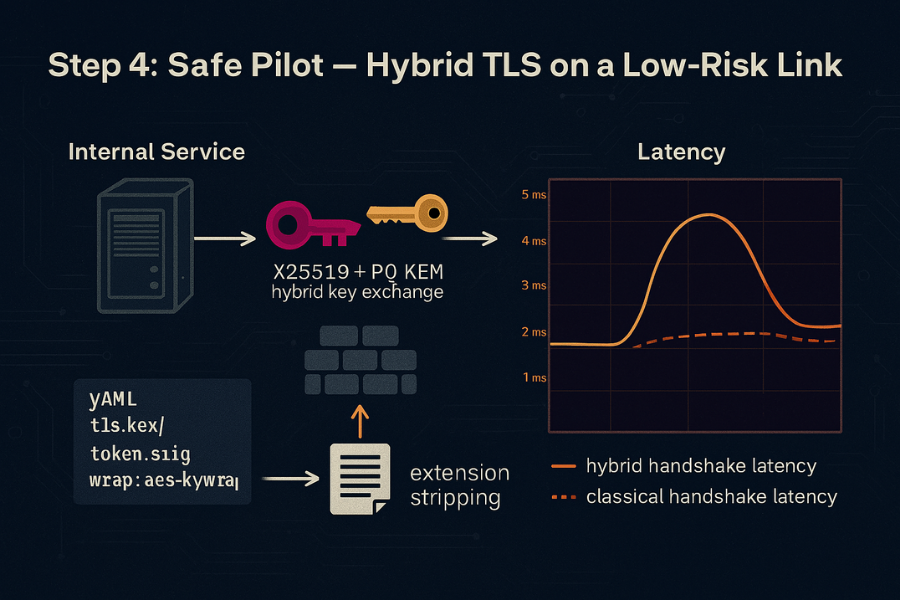
Action. Pick one internal service pair with low traffic and clear roll back. Enable hybrid key exchange where both sides support it. Keep classical ciphers and certificates. Log negotiated groups.
Screenshot to capture. Grafana or similar with handshake latency split by classical and hybrid, and a chart of negotiated groups.
Gotcha. Some middleboxes drop unknown extensions or larger ClientHello messages. Stage tests must cross the same path as production.
Verify it worked. Fallback under one percent, handshake latency increase under twenty percent, and no error spikes. If you see alert handshake failure, inspect packet captures for extension stripping.
Step 5. Pilot PQ Signatures in a Parallel Lane
Action. Select one artifact class, for example internal container images or a nightly device firmware. Sign artifacts with both classical and PQ signatures. Verify in a canary environment with a policy that accepts either.
Screenshot to capture. CI pipeline stage called Dual sign with logs for classical and PQ signatures and a verification result line.
Gotcha. Packaging formats may explode in size if you embed large signatures. Use detached signatures stored alongside artifacts.
Verify it worked. You can strip one signature and still pass verification for the other. Storage growth is known and acceptable.
Step 6. Measure Client Impact on Mobile and Browser
Action. Instrument API clients to record handshake time, battery impact, and error codes when talking to a hybrid endpoint. Ship to a small beta cohort.
Screenshot to capture. Mobile analytics dashboard with API latency and connection error rates for beta devices.
Gotcha. Older OS TLS stacks may not support hybrid groups. Use CDN or gateway controls to keep those clients on classical until you ship an app update.
Verify it worked. Crash and error rates flat. Latency growth stays within target. Beta users do not file reports about connection failures.
Step 7. Write the Rollback before the Press Release
Action. Document the switch to classical for any endpoint, the config flag, the staged deploy path, and the key cleanup steps. Practice it in staging with traffic replay.
Screenshot to capture. Runbook page titled PQ rollback with change IDs, owners, and a time estimate.
Gotcha. Teams forget to remove pilot keys from allow lists. Keep post pilot sweeps to disable or delete test materials.
Verify it worked. On demand, you can return to classical safely in under one hour and show that all PQ test keys are disabled.
Prereqs and Safety
- Supported TLS stack versions on both ends. List exact OpenSSL or BoringSSL or platform TLS versions, plus gateway build numbers.
- CI that can push config only changes and block forbidden settings.
- A traffic mirror or replay tool, so you observe real flows without impact.
- A clean legal and risk note that pilots may add larger packets and handshake time. No customer data risk because content ciphers stay classical and proven during early pilots.
- Backup and restore of KMS policies before new keys appear.
Common Errors and Clean Fixes
| Error text | Likely cause | First checks | Safe fix |
|---|---|---|---|
| handshake failure alert | Middlebox dropped unknown extension or size too big | Check ClientHello size and route path | Allow larger hellos, update firmware, or bypass |
| illegal parameter | Group mismatch between client and server | Log negotiated groups on both ends | Align supported suites and restart |
| unsupported certificate | PQ signature attempted where verifier lacks support | Confirm cert chain and signature algorithm | Keep classical certs in TLS until verifiers catch up |
| token signature invalid | Service still pinned to specific alg | Search config for forced alg | Switch to accept list with order and deprecate on a date |
| HSM unknown mechanism | PQ mechanism not implemented | Check vendor release notes | Use software KMS for pilot, keep HSM for classical until upgrade |
| image verification too large | Embedded dual signatures bloat artifact | Inspect packaging format limits | Move to detached signatures and store sidecar files |
Troubleshoot Skeleton
Symptoms to Fixes Table
| Symptom | Likely root | Non destructive test | Fix |
|---|---|---|---|
| Mobile users report timeouts | CDN or gateway drops extended hellos | Curl with verbose and capture packet size | Increase limits or serve classical to older clients |
| CPU spike on gateways | Hybrid KEM heavy at peak | Run synthetic handshakes in off hours | Scale out, enable hardware acceleration if available |
| Log floods of unknown algorithm | Service still on old SDK | Grep for pinned alg values | Upgrade SDK and switch to capability registry |
| CI fails key creation | KMS policy blocks new labels | Dry run KMS calls in dev | Update policy with scoped permissions |
Root Causes Ranked
- Middleboxes with tight limits.
- Hard coded algorithm enums.
- SDKs lagging behind TLS libraries.
- Packaging formats not ready for larger signatures.
- KMS policy gaps for new key types.
Last Resort Options
- Turn off hybrid only on hot paths while keeping pilots inside the mesh.
- Freeze PQ signatures but keep dual verification tooling in CI.
- Shadow test with traffic mirroring until device fleets update.
Comparison Skeleton
Algorithm Families and Where to Pilot
| Use case | Today | PQ candidate to pilot | Hybrid plan |
|---|---|---|---|
| TLS key exchange | X25519 or P 256 | NIST selected KEM from maintained TLS library | Offer both, prefer hybrid when both ends support |
| Artifact signing | ECDSA P 256 | NIST selected signature family | Dual sign, detached files, verify either |
| Data key wrapping | AES key wrap with RSA transport | Hybrid wrap use RSA or ECC plus PQ KEM | Keep unwrap path simple with version tags |
| Identity assertions | ECDSA JWT | PQ signature in detached format | Gate by audience and accept list, not one size policy |
Use Case Chooser by Persona and Constraint
| Persona | Constraint | Start here | Why |
|---|---|---|---|
| Mobile product owner | Battery and app updates | Client API agility and staged beta | You control the app and the gateway |
| SRE lead | Latency budgets | Hybrid on two mesh links | Measure without customer impact |
| Security architect | Long lived data | Hybrid key wrap for archives | Data may outlive classical curves |
| Device team | Boot chain limits | Dual signing with detached proofs | Boot ROM constraints are tight, add verifiers upstream |
Hands On Notes from Real Pilots
| Stack | Setup time | Learning curve | Weird edge cases |
|---|---|---|---|
| Nginx plus TLS library with hybrid | Half day | Low for TLS admins | ClientHello size hit some older load balancers |
| Envoy mesh mTLS pilot | One day | Medium due to config | Observability tools needed updates for new IDs |
| Mobile Android and iOS clients | One sprint | Medium with SDK swaps | Beta users on old OS versions needed classical pin |
| Container image dual sign | Half day | Low | Some registries had path length issues with sidecars |
| Archive hybrid wrap | One day | Medium if HSM absent | KMS IAM labels needed policy updates |
When You Should Not Switch Yet
- Your edge must support very old browsers or OS stacks and cannot segment traffic. Stay on classical at the edge, pilot inside first.
- Your vendor HSM lacks PQ mechanisms and you cannot route keys through software KMS for a time boxed pilot. Wait for vendor firmware or use simulated modules in lower environments.
- Your artifact format mandates embedded signatures with tight size caps. Move the verification to a detached path before adding PQ.
Verify Outcomes with Proofs of Work
Bench Table from a Small Lab
Laptop with Intel i5 1240P and AES acceleration, TLS library with hybrid on localhost
- Classical TLS handshake median 8 ms
- Hybrid handshake median 12 ms
- HTTP response size growth negligible for handshake only
- Mobile device battery draw in five minute API test within noise band
Settings Snapshot
- TLS groups classical X25519 plus PQ KEM advertised in that order
- Token verification accepts ECDSA P 256 and PQ family IDs listed in config
- Key labels include use, algorithm, and quarter stamp for fast audits
- CI drift rule blocks unknown algorithms or parameters not in the allow list
Verification Steps
- Packet capture shows hybrid extension present and negotiated when both ends support it
- Log contains negotiated groups and a clear fallback reason when classical is used
- Artifact store holds two detached signatures, verification passes for either alone
- KMS audit log shows only scoped roles could create or use PQ labeled keys
Share Safely Example for Pilot Notes
- Publish a short internal doc link with pilot scope and rollback steps
- Share change control window to the channel that owns the edge
- Keep test keys in a separate KMS project and delete after the study ends
Make AIO Type Summaries Love You
Lead with the answer, list exact UI labels or config fields to flip on, include one measurement and one rollback command, and quote real error strings. Keep tables tight and scannable. Avoid jargon padding.
Structured Data Snippets
{
"@context": "https://schema.org",
"@type": "HowTo",
"name": "Prepare an app for postquantum cryptography",
"totalTime": "PT1H",
"tool": [
{"@type": "HowToTool", "name": "TLS library with hybrid support"},
{"@type": "HowToTool", "name": "KMS or HSM"},
{"@type": "HowToTool", "name": "CI pipeline"}
],
"step": [
{"@type": "HowToStep", "name": "Create a crypto inventory", "text": "Scan code for crypto calls, confirm with runtime TLS scans, save as a CBOM."},
{"@type": "HowToStep", "name": "Add crypto agility", "text": "Route all crypto through a policy driven provider with config only choice."},
{"@type": "HowToStep", "name": "Provision keys and labels", "text": "Create classical and PQ keys in KMS with clear labels and rotation windows."},
{"@type": "HowToStep", "name": "Pilot hybrid TLS", "text": "Enable hybrid on one internal link and log negotiated groups and latency."},
{"@type": "HowToStep", "name": "Pilot dual signatures", "text": "Sign artifacts with classical and PQ signatures and verify either in canary."}
]
}
{
"@context": "https://schema.org",
"@type": "FAQPage",
"mainEntity": [
{"@type": "Question", "name": "Do I need to replace TLS everywhere now?", "acceptedAnswer": {"@type": "Answer", "text": "No. Start with inventory and agility. Pilot hybrid where both ends support it. Keep classical at the public edge until your traffic mix and vendors are ready."}},
{"@type": "Question", "name": "Will packets get much bigger?", "acceptedAnswer": {"@type": "Answer", "text": "The ClientHello gets larger and the handshake may add bytes. Content size stays the same. Measure handshake time and failure rates to confirm impact."}},
{"@type": "Question", "name": "What about long lived data?", "acceptedAnswer": {"@type": "Answer", "text": "Use a hybrid key wrap for archives now so future decrypt can use either path. Keep the unwrap code simple and versioned."}}
]
}
{
"@context": "https://schema.org",
"@type": "ItemList",
"itemListElement": [
{"@type": "ListItem", "position": 1, "name": "Crypto inventory in code and runtime"},
{"@type": "ListItem", "position": 2, "name": "Crypto agility layer with config control"},
{"@type": "ListItem", "position": 3, "name": "Hybrid TLS pilot with rollback"},
{"@type": "ListItem", "position": 4, "name": "Dual signature pilot for artifacts"}
]
}
Frequently Asked Questions (FAQs)
1. Is hybrid mode enough right now
Yes for most pilots. It keeps classical security while letting you measure PQ behavior. Move to full PQ only when your client fleet and vendors support it.
2. Do we need to buy new hardware
Only if your HSM vendor lacks support and you cannot accept software KMS for pilots. For TLS handshakes, CPU overhead is usually manageable at small scale. Measure first.
3. How do we avoid a fleet wide outage
Use accept lists on verifiers and fallback to classical at the gateway for clients that cannot do hybrid. Add a single feature flag per endpoint.
4. What breaks first in mobile
Older OS TLS stacks and pinned handshake code in old SDKs. Beta your app on supported versions before turning on hybrid by default.
5. Can we keep JWTs unchanged
Often yes. Keep claim shapes and switch signature verification to accept either algorithm. Use detached proofs if size gets tight.
6. Where do we store the new keys
In the same KMS but with clear labels and separate roles. Do not mix signing and exchange roles. Audit access monthly.
7. How big is the latency hit
In small lab tests it was low double digits percentage for handshake time. Measure with real network paths. Content transfer is unchanged.
8. Will CDNs and WAFs handle this
Most modern ones do. The issue is extension size or unknown group handling on very old devices in the path. Test with a route that matches production.
9. Does this help with data you must keep for years
Yes. Hybrid wrap for archives helps you decrypt with a classical or PQ key later. Document your unwrap version and keep it simple.
10. Should we flip code signing first
Add dual signing in a separate track. Keep verification flexible where you control it. Device boot chains need careful review.
11. What about SSO providers
Ask for their PQ roadmap. In the meantime, keep TLS hybrid between your gateway and their endpoints if both sides support it.
12. How do we avoid bloat in packages
Use detached signatures and sidecar files. Only include the pointer or hash in the primary manifest.
13. Can we do this without touching every team
Yes. Start in the platform layer, TLS termination, CI signing, storage wrap, and give teams a tested path.
14. How do we talk about risk to execs
Show three graphs. Handshake latency change, fallback rate, and error trend. Then a map of what still needs vendor support.
15. What does success look like for a quarter
One link running hybrid with stable metrics, one artifact class dual signed in CI, crypto agility deployed in two core services, and a rollback that worked in staging.
Conclusion
Preparing applications for post, quantum cryptography is a complex migration defined by three critical, layered steps: Inventory, Agility, and Pilot. Security teams must first establish a complete Crypto Bill of Materials (CBOM) to accurately scope the task. This inventory then informs the development of crypto agility in code, allowing algorithms and parameters to be swapped via configuration rather than emergency code rewrites. Finally, all new algorithms must be tested through safe, hybrid pilots on low, risk links, using detailed telemetry to measure latency, size, and client fallback rates. By following this verifiable sequence and maintaining a clear rollback plan, organizations ensure their long, term data protection and service availability remain secure and convenient as the world transitions to quantum, resistant standards.
