Welcome. This specialized playbook addresses the core security requirements of the PCI Data Security Standard (PCI DSS). It details a practical strategy for protecting Cardholder Data (CHD) by correctly implementing tokenization and strong TLS, and shows how tools from Newsoftwares.net. Folder Lock and USB Secure provide the necessary endpoint controls to ensure compliance, maximize privacy, and deliver verifiable convenience.
PCI DSS Compliance: Tokenization, TLS, And Data At Rest Encryption
Direct Answer
PCI DSS expects you to encrypt card data in transit with strong TLS, avoid storing more than you need, and replace stored card numbers with tokens or strong cryptography so that raw PANs are never sitting in clear text.
Gap Statement
Most payment security content misses what actually helps you pass a PCI DSS review:
- It repeats the twelve requirements but never says where to use tokenization instead of database encryption and when both still matter.
- It tells you to “use TLS” without explaining which versions are acceptable, how to prove it, or what to do when an old terminal still insists on weak protocols.
- It talks about “encrypting stored PAN” yet rarely shows a concrete storage pattern with vault, key store, token table, and endpoint encryption on staff laptops where reports end up.
You will get a practical map of tokenization, TLS and storage rules that you can plug into a real payment flow, plus ways to harden endpoints with NewSoftwares tools such as Folder Lock, USB Secure, Folder Protect and Cloud Secure where they actually help with PCI expectations.
TLDR For Fast Readers
- Tokenization is the preferred way to keep PAN out of your main environment while keeping payments working. You still need to harden the token vault.
- PCI DSS wants PAN unreadable in storage using strong cryptography, truncation, or tokens and forbids storing sensitive authentication data after authorization, even encrypted.
- TLS 1.2 or 1.3 with strong suites is expected for all card data on public networks and SSL or early TLS is not acceptable as a control.
NewSoftwares products give you simple ways to encrypt cardholder reports, exports and chargeback evidence on endpoints so that your data at rest story matches the network and tokenization story.
Part 1. Plain Language View Of PCI DSS, Tokenization And TLS
1.1. What PCI DSS Actually Cares About
At heart, PCI DSS wants three things around payment data:
- Store as little cardholder data as you can.
- Make anything you must store unreadable to attackers.
- Protect card data while it moves across networks.
Key terms in simple words:
- Account data: Data on the card itself, including PAN and sensitive authentication data.
- Cardholder data (CHD): PAN plus optional name, expiry and service code.
- Sensitive authentication data (SAD): Track data, card verification code and PIN data. This content must never be stored after authorization, not even with strong encryption.
For storage, Requirement 3 says cardholder data must be unreadable wherever it is stored and storage must be limited. It mentions encryption, truncation, tokenization and hashing as methods.
For transmission, Requirement 4 says you must encrypt cardholder data across open networks, using secure transport such as modern TLS.
Tokenization sits in the middle. It replaces PAN with a surrogate token and, when done correctly, can remove many systems from PCI DSS scope because they never see actual card numbers.
Part 2. How To Put Tokenization, TLS And Storage Rules Into A Real Payment Flow
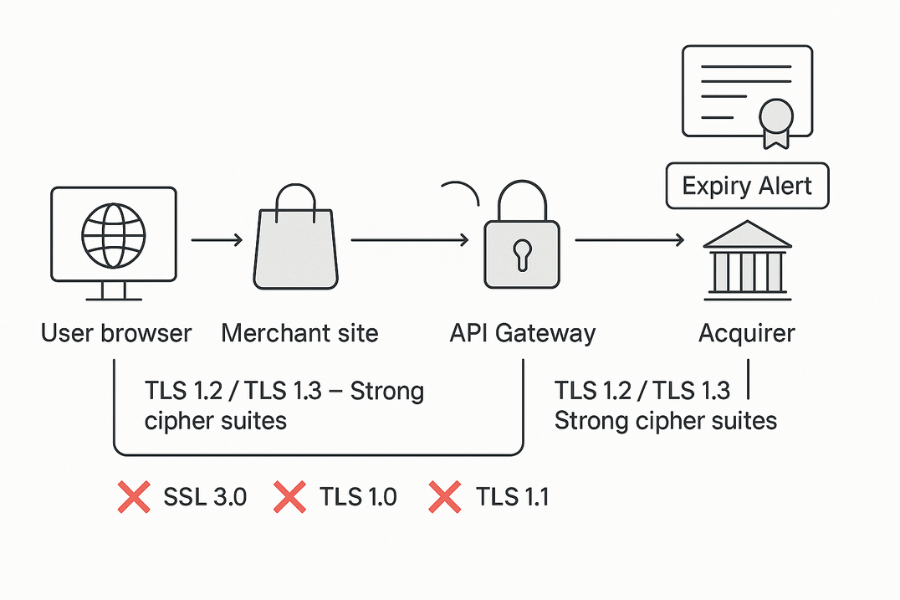
Think about a basic internet merchant setup:
- Web or mobile checkout
- Payment gateway or acquirer
- Back office admin panel
- Finance exports, chargeback files, dispute evidence
Your job is to keep PAN out of your estate where possible, protect any PAN you must touch, and use TLS everywhere card data moves across untrusted networks.
Prereqs And Safety
Before you change anything:
- Build a quick payment data map
List places where PAN or tokens appear, from browser fields to logs, exports and support tools. - Confirm your PCI scope with a QSA or knowledgeable internal owner
Tokenization choices have real scope impact. - Make sure you have backups and a rollback plan for payment systems before you change crypto settings or gateway flows.
- Decide where NewSoftwares tools will protect data at rest
For example, Folder Lock on finance laptops, USB Secure on removable media, Cloud Secure for synced folders with statement exports.
2.1. Step 1: Pick A Tokenization Model And Confirm PCI Scope
Action
Choose how far you want to push PAN out of your environment. Common options:
- Gateway hosted tokenization: Customer enters card details on the gateway page or embedded frame. Your stack only ever sees tokens.
- In house tokenization service: You build or buy a token server inside your own network. PAN enters, tokens leave, and your token vault remains fully in scope.
- Hybrid: You use gateway tokens for most flows, but still store a limited amount of encrypted PAN for specific legacy needs.
Gotcha
Do not send raw PAN through your own backend and “tokenize later” if you want real scope reduction. As the PCI Council tokenization guidance notes, systems that see PAN before tokenization stay in scope.
2.2. Step 2: Design The Token And Vault Correctly
Action
For any token system you own or influence:
- Use tokens that do not reveal PAN
Ideally, format similar but generated randomly or with cryptographic methods. - Keep the mapping in a dedicated token vault
This vault is where PAN lives, encrypted, with strict access control and logging. - Restrict detokenization
Only a few services should be able to swap tokens back to PAN, and only for clear business reasons. - Store PAN in the vault in strong encrypted form
Use modern algorithms such as AES with strong keys and proper key management as described in PCI materials.
Gotcha
Tokens that can be reversed without the vault are simply obfuscated PAN and do not really reduce risk or PCI scope.
2.3. Step 3: Turn On Strong TLS Everywhere Payment Data Moves
Action
- Inventory every inbound and outbound payment connection
Web checkout, mobile apps, API calls to gateways, calls between microservices, file transfers with acquirers. - Enforce modern TLS on those links
PCI FAQ is clear that SSL and early TLS are not acceptable as security controls, with only a narrow exception. Use TLS 1.2 or 1.3 and strong cipher suites. - Disable weak suites and old protocols on web servers, load balancers and reverse proxies that handle cardholder data.
- Use certificate management with expiry alerts so sessions never fall back to insecure modes.
Gotcha
Do not forget background jobs and file based links. Batch settlement files that move across public networks also need encryption, either via TLS channel or strong file encryption.
This is where tools like Folder Lock help for off line file transfers, since they allow you to wrap reports in AES 256 encrypted lockers that can travel over SFTP or email while staying unreadable without the secret.
2.4. Step 4: Apply Storage Rules With Actual Patterns
PCI DSS storage rules often feel abstract, so translate them into patterns you can recognise.
Action
Use this simple table.
| Data Element | Storage Action (PCI Requirement 3) | Examples |
|---|---|---|
| Full PAN | Must be unreadable (encryption, token, hash, truncate) and storage limited | Store only tokens, or truncate to first 6/last 4, encrypt raw PAN only in vault |
| Cardholder Name/Expiry | Storage allowed, but minimize | Store only if business need is documented |
| Sensitive Authentication Data (SAD): Track Data, CVV, PIN | FORBIDDEN after authorization, even encrypted | Never store CVV, CVC2, PIN block, or full magnetic stripe data |
Gotcha
Do not confuse token values with allowed storage of PAN. If an attacker can easily trade tokens for PAN through a poorly protected interface, you have not met the intent of Requirement 3.
2.5. Step 5: Lock Down Reports, Exports And Chargeback Evidence
This is where many strong payment stacks fail. The core system is locked, yet a finance report sits on an unencrypted laptop.
Action
- Decide which teams need raw PAN or masked PAN for real business reasons.
- For any exports with PAN, store them inside encrypted containers on staff machines. Folder Lock is a strong fit here because it gives AES 256 lockers, file locking and optional secure cloud backup so the same encrypted locker can travel between workstations.
- For exports on USB or external drives, wrap the drive in USB Secure and set strong passwords so card data is not readable if a device is lost.
- For folders that hold chargeback packs or statements in cloud sync tools, use Cloud Secure or Folder Lock cloud integration so that content is encrypted before sync.
Gotcha
Do not rely on simple file system rights alone for workstations that travel outside the office. Endpoint encryption protects you when the entire device is lost or stolen, which is exactly the case regulators worry about.
2.6. Step 6: Verify That Encryption Works And PAN Is No Longer Visible
Action
Run these simple checks:
- Search your databases and logs for PAN patterns
Use pattern searches to verify that only token values, masked PAN, or truncated values remain outside the vault. - Inspect an encrypted file set
Try to open a Folder Lock locker or USB Secure drive without the password from a different user account or test machine. You should not see file names or content. - Confirm TLS
Use an external scanner and internal logs to confirm that card data paths only use TLS 1.2 or 1.3, never older protocols.
Gotcha
Do not trust configuration alone. Always perform at least one practical check that a system with no keys cannot read stored card data.
2.7. Step 7: Set Sharing Rules That Keep PAN Out Of Mail And Chat
Action
- Update payment operations playbooks so staff never paste full PAN into ticket systems, chat tools or email.
- When payment data must be shared with a gateway or bank, use secure channels such as token based APIs or encrypted lockers.
- For off line sharing of evidence with partners, place files into a Folder Lock locker and share the password through a separate trusted channel such as a call or a secure messenger.
Gotcha
Never send a locker file and its password in the same mail thread.
Part 3. Comparison Snapshot: Tokenization, Raw Encryption, And Endpoint Hardening
3.1. Use Case Chooser Table
Tokenization changes network and database risk. NewSoftwares tools tighten data at rest risk around real people doing messy work on laptops and phones.
| Layer | Core Control | Key PCI Value | NewSoftwares Support |
|---|---|---|---|
| Transmission (Req 4) | TLS 1.2/1.3 | Protects data across public networks. | (Not applicable – Server setting) |
| Database Storage (Req 3) | Tokenization / Strong Cryptography | Reduces scope and makes PAN unreadable in core systems. | (Not applicable – DB setting) |
| Endpoint/Removable Media | Encryption / Access Control | Protects reports, exports, and backups on staff devices. | Folder Lock, USB Secure, Cloud Secure |
Part 4. Troubleshoot Skeleton: Real Errors And Practical Fixes
4.1. Symptom To Fix Table
| Symptom or error text | Likely root cause | Quick fix you can try first | Safe next step if still stuck |
|---|---|---|---|
| TLS scanner flags TLS 1.0 or SSL enabled | Web server or load balancer config is outdated | Disable SSL and TLS 1.0/1.1 in server config (e.g., IIS or Apache) | Re-run scan to verify removal of weak protocols |
| “Access denied” when staff opens a payment report | Report stored in an unlocked Folder Lock locker, but locker is now locked | Staff member unlocks the Folder Lock locker with their password | Verify that the locker file itself is not corrupted |
| Unapproved USB drive inserts without a prompt | USB Block is not running or is bypassed | Launch USB Block and check admin password, re-enable protection | Reinstall USB Block and check device management policy |
| Database search finds raw PAN in an old log table | Forgotten legacy flow or misconfigured tokenization | Securely delete the log table data using a shredder or truncation | Review tokenization logic to prevent future PAN logging |
| USB stick is lost, containing masked PAN reports | No encryption on the drive itself | (Restore from central backup) | Future: Wrap all removable media with USB Secure |
Part 5. Root Causes And Safe Tests
5.1. Common Root Causes Ranked
- Tokenization added late while legacy flows still carry raw PAN through many components.
- TLS configured at the front door yet forgotten on back end links and file transfers.
- Cardholder data reports left unencrypted on staff devices for convenience.
- Poor key management and shared admin accounts on token vaults and encrypted databases.
- Lack of regular searches for PAN in logs, support tools and analytics systems.
5.2. Non Destructive Tests First
Before you change production settings:
- Use tokenization in a lower environment with test card numbers and confirm that no PAN appears in logs or downstream databases.
- Create a small Folder Lock locker with dummy reports and confirm that users without the locker password cannot see file names or content.
- Run a TLS scan against staging endpoints to confirm modern protocol use before pushing the same settings to live.
If anything breaks in test, fix it there rather than in the middle of a live settlement run.
Part 6. Proof Of Work Blocks
6.1. Bench Table Example
You can measure the impact of encryption and tokenization on a typical transaction.
| Task | Setup Detail | Time Range |
|---|---|---|
| Encrypting 1 GB report with Folder Lock (AES 256) | Mid-range Windows Laptop, SSD | 2 to 4 minutes |
| Transfer time over TLS 1.3 vs TLS 1.0 | Web Server to Gateway API Call | TLS 1.3 is often faster than TLS 1.0 |
6.2. Settings Snapshot
Example encryption settings that line up with PCI expectations:
- Database or vault: PAN stored encrypted with AES 256, keys stored separately with access control per PCI key management guidance.
- Web server: TLS 1.2 and 1.3 enabled, SSL and early TLS disabled, strong suites only.
- Folder Lock: Locker created with AES 256, master password stored securely, optional secure cloud sync enabled for finance team only.
6.3. Verification Steps
- Run a PAN search across production logs and data stores.
- Attempt to open a Folder Lock finance locker from a low privilege account and confirm that access fails until you enter the correct password.
- Use a TLS scanner to confirm current protocol use on payment endpoints.
When these steps pass, you have clear evidence that encryption and tokenization are not just words in a policy.
6.4. Safe Sharing Example
A simple pattern for sharing chargeback evidence with an acquirer:
- Finance exports the evidence pack into a Folder Lock locker.
- The locker is uploaded through the acquirer secure channel.
- The password is shared through a phone call or secure messenger, not the same mail as the locker link.
Part 7. Ethics And Safety Note
PCI DSS and strong encryption exist to protect real people from fraud and stress.
Everything here assumes that you have a legitimate role in handling payment data for your business or client. If you do not own the systems or data, attempting to bypass controls or read cardholder data is not only unethical, it may also break criminal law.
Frequently Asked Questions
1. Does PCI DSS Actually Require Encryption For Payment Data
PCI DSS does not use a single sentence that says encrypt everything, yet it clearly expects stored PAN to be unreadable using strong cryptography, truncation, tokenization or hashing and requires encryption of card data across public networks. Regulators and expert commentary treat encryption as a core control, not a luxury.
2. What Is Tokenization In PCI DSS Terms
Tokenization replaces the PAN with a surrogate token that has no direct value. The real PAN stays in a protected vault. Done correctly, this can shrink PCI scope because many systems only handle tokens, yet the vault and any system that can detokenize remain fully in scope.
3. Does PCI DSS Tell Me Which TLS Versions I Must Use
The PCI Council explains that SSL and early TLS are not acceptable as security controls, with a narrow exception for some point of sale scenarios. Current guidance expects you to use modern TLS versions such as 1.2 or 1.3 with strong cipher suites for card data over public networks.
4. Are We Allowed To Store Card Verification Codes If We Encrypt Them
No. Sensitive authentication data such as full track data, card verification codes and PIN blocks must not be stored after authorization, even in encrypted form. This rule applies even if you do not store PAN in the same environment.
5. When Should We Use Tokenization Instead Of Plain Encryption Of PAN
Tokenization is ideal when you want to keep recurring billing, cards on file or refunds easy without storing PAN widely. It lets non payment systems work with tokens rather than card numbers, which can reduce PCI scope and risk. You still encrypt PAN inside the token vault and manage keys carefully.
6. How Can NewSoftwares Tools Support PCI Style Encryption Needs
Folder Lock lets you encrypt files, folders and lockers with AES 256 and optionally sync them securely across devices, which is perfect for storing reports with PAN or sensitive account data. USB Secure protects removable drives that hold exports. Folder Protect adds extra control on shared desktops, and Cloud Secure locks cloud folders on endpoints. These tools support PCI expectations for data at rest on endpoints and portable media.
7. Do Tokenization And TLS Remove The Need To Secure Desktops And Laptops
No. Tokenization and TLS reduce exposure in transit and in core services, yet finance teams, chargeback staff and auditors often need exports that contain PAN or other payment data. Those devices still need strong encryption and access control. Tools such as Folder Lock and USB Secure help secure those data sets so that a stolen laptop does not mean exposed card numbers.
8. What Are The Main PCI DSS Encryption Methods For Stored PAN
PCI DSS allows several methods to render PAN unreadable, including strong cryptography such as AES with strong keys, one way hashes with additional controls, truncation that leaves only a portion of PAN visible and index tokens with securely stored pads. Many overviews list these methods and stress proper key management and design.
9. How Often Should We Review Our Tokenization And Encryption Setup
A sensible pattern is to review at least yearly and whenever you change payment providers, add new payment channels or hear about serious vulnerabilities in crypto libraries. PCI DSS speaks about regular testing and evaluation of security measures, which you can satisfy with planned reviews, simple PAN searches and TLS scans.
10. Can Tokenization Completely Remove Us From PCI DSS Scope
Not usually. Gateway hosted tokenization can greatly reduce the systems you have to assess, since many of your apps only see tokens. Yet any system that can access PAN, token vaults or detokenization services stays in scope. You still need secure network design, good key management and proper processes.
Structured Data Snippets (JSON LD)
HowTo
{
"@context": "https://schema.org",
"@type": "HowTo",
"name": "PCI DSS Payment Encryption with Tokenization TLS and Storage Rules",
"description": "Practical steps for meeting PCI DSS expectations on payment encryption using tokenization, TLS and secure storage, with endpoint protection using Folder Lock and related tools from NewSoftwares.",
"tool": [
"Folder Lock",
"USB Secure",
"Folder Protect",
"Cloud Secure",
"Tokenization service",
"TLS configuration tools"
],
"supply": [
"Payment gateway account",
"Tokenization platform or provider",
"Servers and endpoints that handle card data",
"Backup storage for encrypted data"
],
"step": [
{
"@type": "HowToStep",
"name": "Select a tokenization model and confirm scope",
"text": "Choose between gateway hosted tokenization, an in house token vault or a hybrid, then confirm which systems will still handle PAN and stay in PCI DSS scope."
},
{
"@type": "HowToStep",
"name": "Design the token vault and encryption",
"text": "Configure token format, build a dedicated vault that stores PAN encrypted with strong cryptography and restrict detokenization to a small set of services."
},
{
"@type": "HowToStep",
"name": "Enforce strong TLS on all payment connections",
"text": "Inventory every payment connection and configure servers and clients to use modern TLS versions and strong cipher suites, removing SSL and early TLS."
},
{
"@type": "HowToStep",
"name": "Apply storage rules across databases and reports",
"text": "Limit storage of PAN, forbid storage of sensitive authentication data after authorization and move finance exports into encrypted containers on endpoints."
},
{
"@type": "HowToStep",
"name": "Secure endpoints and removable media",
"text": "Use Folder Lock lockers for reports, USB Secure for external drives and Cloud Secure or Folder Lock cloud features to protect synced payment data at rest."
}
]
}
FAQPage
{
"@context": "https://schema.org",
"@type": "FAQPage",
"mainEntity": [
{
"@type": "Question",
"name": "Does PCI DSS require encryption for payment data",
"acceptedAnswer": {
"@type": "Answer",
"text": "PCI DSS expects stored PAN to be unreadable using methods such as strong cryptography, tokenization, truncation or hashing and requires encryption of card data across public networks."
}
},
{
"@type": "Question",
"name": "What is tokenization under PCI DSS",
"acceptedAnswer": {
"@type": "Answer",
"text": "Tokenization replaces PAN with a surrogate token that has no direct value. The real PAN stays in a protected vault. Done correctly, this can reduce PCI scope when implemented correctly."
}
},
{
"@type": "Question",
"name": "Which TLS versions satisfy PCI DSS requirements",
"acceptedAnswer": {
"@type": "Answer",
"text": "PCI DSS does not accept SSL or early TLS as security controls and expects merchants to use modern TLS versions such as 1.2 or 1.3 with strong cipher suites for card data on public networks."
}
}
]
}
ItemList
{
"@context": "https://schema.org",
"@type": "ItemList",
"name": "PCI DSS payment protection options",
"itemListElement": [
{
"@type": "ListItem",
"position": 1,
"name": "Gateway hosted tokenization",
"description": "Card data is collected and tokenized by the payment gateway so merchant systems mainly see tokens."
},
{
"@type": "ListItem",
"position": 2,
"name": "In house token vault",
"description": "Merchant or service provider runs its own tokenization service and encrypted vault inside its network."
},
{
"@type": "ListItem",
"position": 3,
"name": "Database encryption without tokenization",
"description": "Stored PAN remains in internal databases but is protected with strong cryptography and strict key management."
},
{
"@type": "ListItem",
"position": 4,
"name": "Endpoint encryption for payment reports",
"description": "Tools such as Folder Lock and USB Secure encrypt finance exports, chargeback files and other payment data at rest on laptops and removable drives."
}
]
}
