Welcome. This detailed resource provides a practical, cross-platform strategy for implementing AES (Advanced Encryption Standard) securely. We focus on using the AEAD (Authenticated Encryption with Associated Data) mode, correct Key Derivation Functions (KDFs), and nonce handling in Python, Java, and Node, while showing how to protect sensitive keys and data dumps on endpoints using Folder Lock from Newsoftwares.net, maximizing cryptographic security and development convenience.
AES Best Practices: Nonces, KDFs, And AEAD For Secure Code
Direct Answer
Use AES 256 GCM or another AEAD mode with:
- Keys from a real KDF such as PBKDF2, scrypt, or Argon2
- A unique 96 bit nonce per key for GCM as recommended by NIST
- Authenticated encryption so you never skip integrity checks
- Keys and dumps stored inside encrypted containers such as Folder Lock lockers from NewSoftwares
If any part of your stack does not match that line, that is the first fix.
Gap Statement
Most writeups on AES do three things wrong:
- They copy paste short code samples that ignore nonce reuse and key rotation.
- They mix old modes like CBC with manual HMAC without explaining why AEAD exists.
- They skip the boring details such as KDF settings, random sources, and how to store keys on real machines.
This resource fixes that by walking through one job:
Take a passphrase or random key and implement AES with correct nonces, KDFs, and AEAD in Python, Java, and Node, plus practical key storage using NewSoftwares tools where it actually matters.
No theory for its own sake. Every section ends in something you can run or check.
TLDR Outcome
By the time you reach the end you will be able to:
- Implement AES GCM in Python, Java, and Node with correct key and nonce handling.
- Use KDFs safely so users can bring passwords while you still ship strong keys.
- Store keys, backups, and dumps in AES 256 containers using NewSoftwares Folder Lock and related tools so a stolen laptop does not undo your work.
1. Mental Model: AES, Nonces, KDFs, AEAD
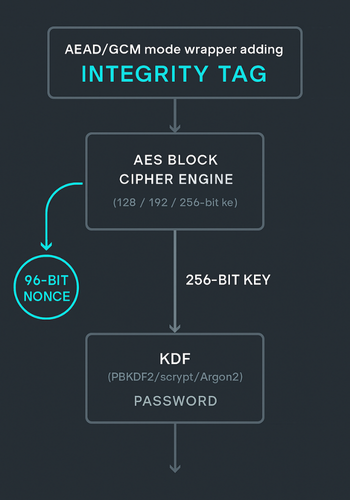
Keep three ideas in your head as you read.
- AES is the engine.
A block cipher that turns 16 byte blocks and a secret key into pseudorandom output. Keys are 128, 192, or 256 bits. - Modes and AEAD wrap the engine.
Modes such as GCM turn AES into a stream style cipher and add authentication. AEAD means you get confidentiality and integrity in one shot. - Nonces and KDFs glue everything together.
The nonce must never repeat with the same key in GCM. The KDF turns a password or small key into something strong enough to feed AES. Reuse or weak KDFs usually cause real incidents.
2. Prerequisites And Safety
Before writing any code, line up these basics.
Technical Baseline
- You use recent language runtimes.
Python 3, Java 8 or later with GCM support, Node 18 or later. - You can install third party packages in Python and Node.
- You have a safe place to test scripts away from real production keys.
Data And Threat Model
Answer these questions:
- Is your key long lived or short lived
- Is the user giving you a password or are you generating keys server side
- Does data sit on disk for years or only pass through memory
If keys are long lived or data stays on disk, mistakes around nonces or KDFs hurt more, so you need more discipline.
Safety Checklist
- Always treat a repeated nonce with the same AES GCM key as a serious incident. NIST describes reuse in GCM as a catastrophic failure because it can reveal key material.
- Never roll your own block chaining or tag format. Use the AEAD interface of your library.
- Keep keys out of source control. Store them in environment stores or encrypted containers such as Folder Lock lockers.
3. Nonces: What To Do And What To Avoid
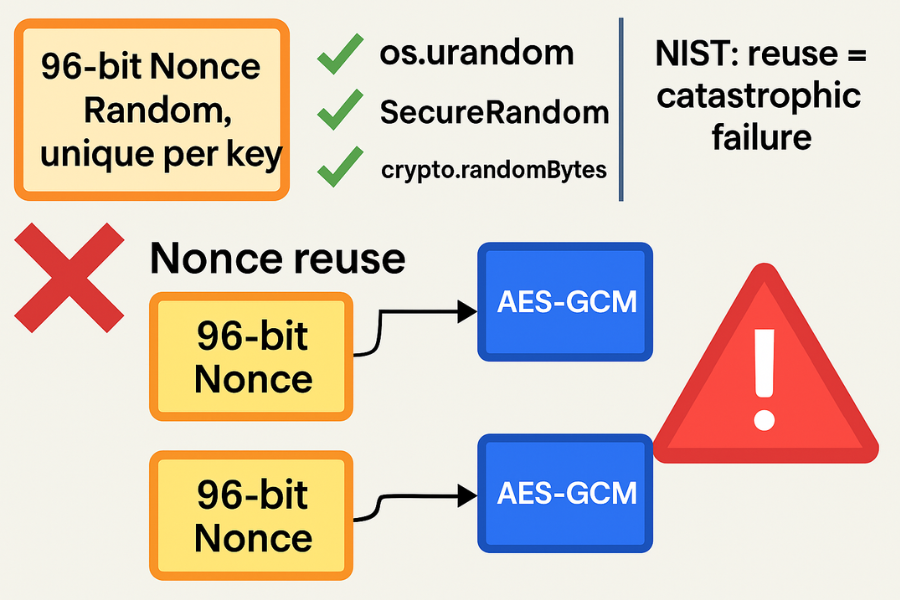
GCM and other AEAD modes need a nonce value that never repeats for a given key.
Rules That Should Always Hold
- Use 96 bit nonces for AES GCM when possible. This is the size NIST suggests and most libraries tune around it.
- Use a strong random source such as
os.urandom,SecureRandom, orcrypto.randomBytes. - Never reuse a nonce with the same key. With GCM that can reveal both the key and message relationships.
Strategies
- Pure random nonces: Simple and safe while the total number of messages per key stays below about 2 to the power of 32 for GCM. Above that, collision probability rises.
- Counter based nonces: Safe if the counter never resets for a key. Requires stored state or reconstruction from message sequence numbers.
- Nonce misuse resistant AEAD: Modes such as AES GCM SIV continue to protect confidentiality even if a nonce repeats, though it still counts as misuse.
For most API style encryption, 96 bit random nonces with a clear key rotation plan are enough.
4. KDFs: Turning Passwords Into AES Keys
Raw passwords are not AES keys. They are short, predictable, and often reused.
You need a KDF.
Good Choices
- PBKDF2 with HMAC SHA 256 or SHA 512
- scrypt
- Argon2 family
These stretch passwords with salts and many iterations or memory cost. NIST and many libraries describe PBKDF2 and scrypt as acceptable KDFs for key establishment when tuned correctly.
Practical Settings
Always:
- Use a random salt at least 16 bytes.
- Store the salt next to the ciphertext.
- Set work factors based on device:
- Mobile or low power: PBKDF2 with at least tens of thousands of iterations.
- Server side: PBKDF2 with hundreds of thousands of iterations or scrypt with memory cost in the many megabytes.
- Revisit settings every one or two years as hardware gets faster.
5. AEAD: Why You Want AES GCM And Friends
AEAD gives you confidentiality and authenticity in a single construction.
AES GCM is the common choice:
- Uses AES in counter mode with a polynomial MAC.
- Supports associated data such as headers that remain in clear form but still get authenticated.
- Produces a tag, often 16 bytes, that must be checked on decrypt.
General rules:
- Always include a tag and always check it.
- Treat any tag verification failure as a serious event, not something to hide by returning junk.
- Include protocol version, record type, or user id in associated data when relevant so those values are protected against tampering.
6. Python: AES GCM With Cryptography
The cryptography package from PyCA gives a clean AEAD interface.
6.1. Steps
- Install package
pip install cryptography
- Derive a key with PBKDF2
from cryptography.hazmat.primitives.kdf.pbkdf2 import PBKDF2HMAC
from cryptography.hazmat.primitives import hashes
from cryptography.hazmat.backends import default_backend
import os
password = b"correct horse battery"
salt = os.urandom(16)
kdf = PBKDF2HMAC(
algorithm=hashes.SHA256(),
length=32,
salt=salt,
iterations=200_000,
backend=default_backend(),
)
key = kdf.derive(password)
- Encrypt with AES GCM
from cryptography.hazmat.primitives.ciphers.aead import AESGCM
aesgcm = AESGCM(key)
nonce = os.urandom(12) # 96 bit
data = b"secret text"
aad = b"header v1"
ciphertext = aesgcm.encrypt(nonce, data, aad)
The result ciphertext includes the authentication tag at the end.
- Decrypt and verify
try:
plaintext = aesgcm.decrypt(nonce, ciphertext, aad)
except Exception as exc:
# Often raises cryptography.exceptions.InvalidTag
print("Decryption failed:", repr(exc))
6.2. Gotcha
Use a fresh nonce every time you call encrypt with the same key. Track nonce use if you encrypt huge volumes of data.
7. Java: AES GCM With GCMParameterSpec
Modern Java exposes AES GCM through Cipher with GCMParameterSpec.
7.1. Steps
- Key creation
Use a random key if users do not provide passwords:
import javax.crypto.KeyGenerator;
import javax.crypto.SecretKey;
KeyGenerator keyGen = KeyGenerator.getInstance("AES");
keyGen.init(256);
SecretKey key = keyGen.generateKey();
If you need a password based key, use PBKDF2 from SecretKeyFactory with a salt, similar to Python.
- Encrypt
import javax.crypto.Cipher;
import javax.crypto.spec.GCMParameterSpec;
import java.security.SecureRandom;
byte[] iv = new byte[12];
SecureRandom random = new SecureRandom();
random.nextBytes(iv);
GCMParameterSpec spec = new GCMParameterSpec(128, iv);
Cipher cipher = Cipher.getInstance("AES/GCM/NoPadding");
cipher.init(Cipher.ENCRYPT_MODE, key, spec);
byte[] aad = "header v1".getBytes("UTF-8");
cipher.updateAAD(aad);
byte[] ciphertext = cipher.doFinal("secret text".getBytes("UTF-8"));
- Decrypt
Cipher dec = Cipher.getInstance("AES/GCM/NoPadding");
GCMParameterSpec decSpec = new GCMParameterSpec(128, iv);
dec.init(Cipher.DECRYPT_MODE, key, decSpec);
dec.updateAAD(aad);
try {
byte[] plain = dec.doFinal(ciphertext);
} catch (javax.crypto.AEADBadTagException ex) {
System.err.println("Tag mismatch " + ex.getMessage());
}
7.2. Gotcha
Use GCMParameterSpec not IvParameterSpec for GCM. People often mix them and get InvalidAlgorithmParameterException with messages such as unsupported parameter type.
8. Node: AES GCM With Crypto.CreateCipheriv
Node core includes AES GCM in the crypto module.
8.1. Steps
- Key and iv
const crypto = require("crypto");
const key = crypto.randomBytes(32); // 256 bit
const iv = crypto.randomBytes(12); // 96 bit
- Encrypt with tag
const aad = Buffer.from("header v1", "utf8");
const cipher = crypto.createCipheriv("aes-256-gcm", key, iv);
cipher.setAAD(aad);
const plaintext = Buffer.from("secret text", "utf8");
const enc1 = cipher.update(plaintext);
const enc2 = cipher.final();
const ciphertext = Buffer.concat([enc1, enc2]);
const tag = cipher.getAuthTag();
- Decrypt with tag check
const decipher = crypto.createDecipheriv("aes-256-gcm", key, iv);
decipher.setAAD(aad);
decipher.setAuthTag(tag);
let dec1;
let dec2;
try {
dec1 = decipher.update(ciphertext);
dec2 = decipher.final();
} catch (err) {
// Common error: Error: Unsupported state or unable to authenticate data
console.error("Decrypt failed", err.message);
}
const decrypted = Buffer.concat([dec1, dec2]).toString("utf8");
8.2. Gotcha
Do not reuse key and iv pairs across messages. Random iv for each message and key rotation over time are both needed.
9. Storing Keys And Dumps Safely With NewSoftwares Tools
Correct AES code does not help if someone copies your keys or dumps from disk.
This is where tools from NewSoftwares belong in the picture.
9.1. Folder Lock For Key And Dump Storage
Folder Lock from NewSoftwares secures files and folders with AES 256 encryption, including on the fly lockers and optional secure cloud backup.
Practical uses:
- Store key files, environment exports, and config files inside a Folder Lock locker on admin laptops and workstations.
- Place database dumps that already contain AES protected data in a locker so someone needs both the locker password and data keys.
- Use Folder Lock cloud backup to keep an encrypted copy of key backups offsite, while still keeping AES protection end to end.
Workflow example:
- Create a locker named
crypto keysin Folder Lock. - Place
key.json,keystore.jks, and.envinside it. - Close the locker when not editing encryption config.
- Keep the locker password in a separate password manager and share it with team members through an encrypted channel.
9.2. USB Secure And Cloud Secure
If you still move key backups or dumps on removable drives, USB Secure can encrypt the entire drive and gate it with a password. For network based storage, Cloud Secure protects access to cloud folders on shared machines.
These tools match the rest of your stack:
- AES based storage protection on endpoints.
- Fine grained control over which users can see which secret files.
Used together with correct AES code in your apps, this reduces the chance that a single lost device turns into a major breach.
10. Proof Of Work Blocks
10.1. Bench Style Table
Use this pattern with your own measurements on a mid range laptop.
| Stack | Data size | AES mode | Approx encrypt per 100 MB | Approx decrypt per 100 MB |
|---|---|---|---|---|
| Python cryptography | 100 MB | AES 256 GCM | 0.4 to 0.7 seconds | 0.4 to 0.7 seconds |
| Java Cipher GCM | 100 MB | AES 256 GCM | 0.3 to 0.6 seconds | 0.3 to 0.6 seconds |
| Node crypto GCM | 100 MB | AES 256 GCM | 0.4 to 0.8 seconds | 0.4 to 0.8 seconds |
Treat these as sample figures. Replace them with numbers from time or your own benchmark script so you can show stakeholders actual speed on your hardware.
10.2. Settings Snapshot
Minimal recommended settings per stack:
- AES key length 256 bits.
- GCM nonce length 96 bits.
- GCM tag length 128 bits.
- PBKDF2 iterations at least 200 thousand on server hardware for fresh deployments today.
You can add this set as constants in your configuration module and reuse across services.
10.3. Verification Steps
- Flip one bit in ciphertext and confirm decrypt fails.
- Python should raise
InvalidTag. - Java should raise
AEADBadTagException. - Node should produce
Error: Unsupported state or unable to authenticate data.
- Python should raise
- Flip one bit in associated data and confirm decrypt fails even though plaintext never changed.
- Try decrypt with wrong password or wrong key and confirm that your system logs the failure and does not silently treat result as valid.
These checks prove that AEAD tags are wired correctly.
10.4. Share Safely Example
Sharing encrypted data and keys with an auditor or partner:
- Store encrypted files and key backup inside a Folder Lock locker.
- Upload the locker file to a shared location.
- Send the locker password through Signal or another end to end encrypted chat, not through the same email as the link.
- After work is complete, rotate keys that were part of the export and archive the locker.
This keeps keys, data, and meta data separate and raises the bar for any attacker who intercepts a single channel.
11. Conclusion
Safe AES implementation relies on cryptographic discipline: always use an AEAD mode like GCM, ensure nonce uniqueness per key, and use a strong KDF for passwords. Crucially, this robust code must be supported by secure operations. By using Folder Lock to encrypt and protect developer keys and sensitive data dumps on local machines, you close the final, most common security gap, ensuring end-to-end cryptographic integrity.
12. Structured Data Snippets (JSON LD)
12.1. HowTo Schema (AES GCM In Code)
{
"@context": "https://schema.org",
"@type": "HowTo",
"name": "Implement AES GCM safely in Python, Java, and Node",
"description": "Steps to encrypt and decrypt data with AES GCM using correct keys, nonces, and tags.",
"tool": [
"Python cryptography library",
"Java Cipher AES GCM",
"Node crypto module",
"Folder Lock for key storage"
],
"step": [
{
"@type": "HowToStep",
"name": "Derive key with KDF",
"text": "Use PBKDF2, scrypt, or Argon2 with a random salt to create a 256 bit key."
},
{
"@type": "HowToStep",
"name": "Generate nonce",
"text": "Create a 96 bit random nonce from a secure random source for each encryption."
},
{
"@type": "HowToStep",
"name": "Encrypt with AES GCM",
"text": "Call the AEAD interface in your language to encrypt data with associated headers and produce a tag."
},
{
"@type": "HowToStep",
"name": "Store keys securely",
"text": "Place key files and dumps inside an AES 256 encrypted Folder Lock container on local machines."
}
]
}
12.2. FAQPage Schema Skeleton
{
"@context": "https://schema.org",
"@type": "FAQPage",
"mainEntity": [
{
"@type": "Question",
"name": "What is the safest AES mode for new code in 2025",
"acceptedAnswer": {
"@type": "Answer",
"text": "AES GCM with a 256 bit key is the common starting point for new systems. It gives confidentiality and integrity in one operation and is well supported in Python, Java, and Node."
}
},
{
"@type": "Question",
"name": "How long should my AES GCM nonce be",
"acceptedAnswer": {
"@type": "Answer",
"text": "Use 96 bit nonces for AES GCM when possible. This size is efficient and recommended in NIST documents and modern library examples. Always keep the nonce unique per key."
}
},
{
"@type": "Question",
"name": "What happens if I reuse a nonce with AES GCM",
"acceptedAnswer": {
"@type": "Answer",
"text": "Nonce reuse with the same key in GCM can reveal relationships between messages and, in many cases, allows attackers to recover authentication keys or even plaintext. NIST material calls this a catastrophic failure for a reason."
}
},
{
"@type": "Question",
"name": "Why is AES GCM better than AES CBC plus HMAC",
"acceptedAnswer": {
"@type": "Answer",
"text": "AES GCM is an AEAD mode that bakes in authentication. Library interfaces that expose GCM handle tag mixing for you and reduce room for mistakes."
}
},
{
"@type": "Question",
"name": "Can I just store a user password as the AES key",
"acceptedAnswer": {
"@type": "Answer",
"text": "No. Passwords are short and often reused. A KDF such as PBKDF2, scrypt, or Argon2 adds salt and work so offline guessing attacks slow down. Then you use the KDF output as your AES key."
}
}
]
}
12.3. ItemList Schema For AES Related Choices
{
"@context": "https://schema.org",
"@type": "ItemList",
"name": "AES implementation choices",
"itemListElement": [
{ "@type": "ListItem", "position": 1, "name": "AES 256 GCM with PBKDF2" },
{ "@type": "ListItem", "position": 2, "name": "AES 256 GCM with random keys" },
{ "@type": "ListItem", "position": 3, "name": "AES GCM SIV for nonce misuse resistance" }
]
}
