How VPN Encryption Works And When It Does Not Protect You
Answer first
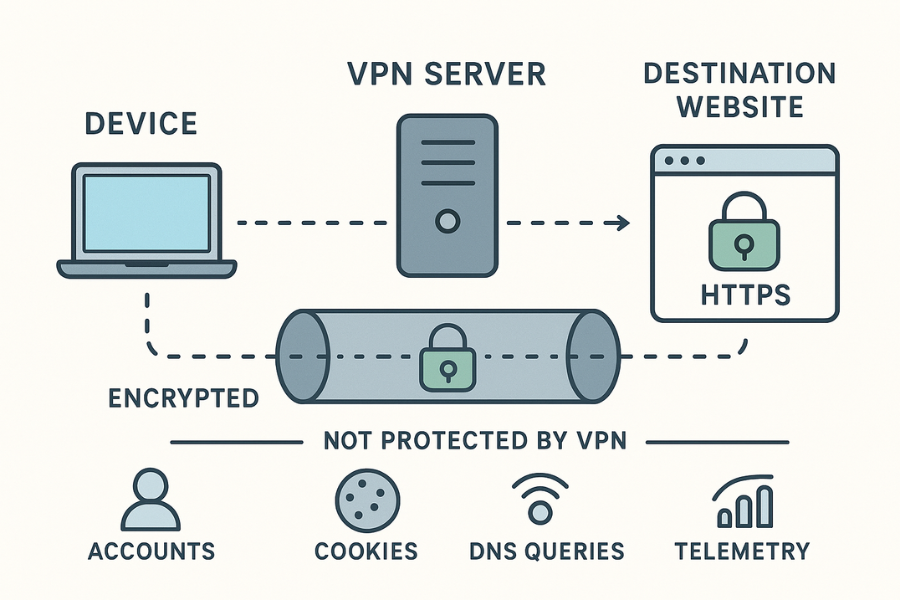
A VPN encrypts traffic between your device and the VPN server. It hides your activity from local networks and your internet provider. It does not hide who you log in as on websites, what you type into an app, or anything your device leaks outside the tunnel. Common leaks include DNS queries, app telemetry, and traffic that bypasses the tunnel during drops. Fix this with a kill switch, trusted DNS inside the tunnel, app sign outs when privacy matters, and device hardening.
Gap statement
Most guides stop at “turn on a VPN and you are safe”. They skip device risk, account tracking, DNS and WebRTC leaks, split tunneling pitfalls, and what really happens when the tunnel drops. This playbook explains the blind spots, gives exact settings to close them, and shows simple tests you can run today.
Outcomes
• VPN encryption protects the path to the VPN server, not the destination site.
• Your logins, cookies, and device identity still expose you. Sign out or use separate profiles.
• Seal the common gaps. Use a kill switch, provider DNS inside the tunnel, and leak tests.
What VPN encryption does and does not do
| Area | Protected by VPN | Not protected by VPN |
|---|---|---|
| Traffic between your device and the VPN server | Yes | No |
| Traffic between the VPN server and the destination site | No | Yes |
| Your account logins and cookies | No | Yes |
| Local Wi Fi snooping and ISP inspection | Yes | No |
| DNS queries if forced inside the tunnel | Yes | No if they escape |
| App telemetry that ignores system proxy | No by default | Often yes |
| Device malware or keyloggers | No | Yes |
| Illegal behavior or policy violations | No shield | Yes exposure |
Rule of thumb. The tunnel protects the route. It does not fix identity, device security, or behavior.
How VPN encryption actually works in practice

• Your device and the VPN server agree on a secure channel. This uses a protocol like WireGuard or OpenVPN.
• A session key encrypts packets from your device to the server. Only both ends know the key.
• The server forwards your packets to the final site. That leg is not part of your VPN encryption. If the site uses HTTPS, that part is encrypted by TLS, not by the VPN.
• The site sees the VPN server IP, not your home IP. Your ISP sees you talking to the VPN server only.
• Logs and settings decide what traces exist on the server. Choose providers with clear no content logging and modern ciphers.
The big three blind spots
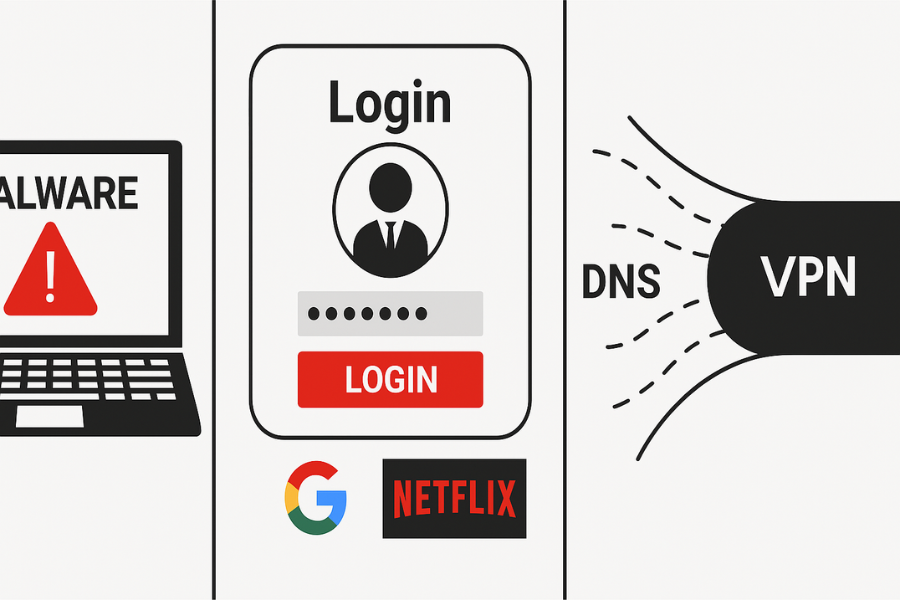
- Local device risk
If your device has malware, a rogue extension, or a keylogger, the VPN cannot help. The malware sees your data before encryption. - Account and cookie identity
If you log in to Google, Netflix, or Slack, those services know it is you. A VPN cannot hide your identity from a site where you chose to identify yourself. - DNS leaks and tunnel drops
If your DNS lookups go to the system resolver outside the tunnel, you leak what domains you visit. If your tunnel drops and you have no kill switch, apps can fail open and send traffic outside.
Quick hardening plan in five minutes
This section uses short, exact actions. Add screenshots when you publish.
Windows 11 with a commercial VPN app
Prereqs and safety
• Update Windows and your VPN app.
• You need admin rights to change adapters and firewall rules.
Steps
- Open your VPN app. Set protocol to WireGuard or OpenVPN UDP.
Gotcha. Some networks block UDP. If so, pick TCP or a stealth mode. - Turn on the kill switch in the app. Confirm it says Always or System wide.
Gotcha. A per app kill switch does not stop background services. - Turn off split tunneling unless you need a specific exception.
Gotcha. Split tunneling is a common leak path for browsers and updaters. - Set DNS to “use provider DNS while connected”.
Gotcha. If your app lacks this, set the adapter DNS to a resolver the provider documents. - Connect. Verify the new IP on two sites.
Gotcha. Some sites cache results. Use private browsing for tests.
Verify it worked
• Run ipleak.net and confirm DNS shows your VPN, not your ISP.
• Drop your Wi Fi. Confirm the kill switch blocks traffic until the tunnel returns.
• Check Windows Network and Internet. The VPN adapter is active when connected.
Common errors and clean fixes
• Error text TAP adapter not found. Cause: OpenVPN virtual adapter missing. Fix: Reinstall the VPN app with driver install allowed.
• DNS still shows ISP. Cause: Smart multi path security software. Fix: Disable that feature or add your VPN to its safe apps list.
macOS with a commercial VPN app
Prereqs and safety
• Update macOS.
• Close other network utilities during setup.
Steps
- In the VPN app, select WireGuard or IKEv2 if available.
Gotcha. IKEv2 survives network changes but some hotspots block it. - Enable kill switch. Many apps call it “network lock”.
Gotcha. Test by toggling Wi Fi off and on during a download. - Disable split tunneling.
- Set DNS inside the app to “use VPN resolver”.
- Connect and test DNS and IP.
Verify it worked
• System Settings shows VPN connected with a timer.
• ipleak.net shows no ISP DNS servers.
Common errors and clean fixes
• Error text The VPN server did not respond. Cause: Captive portal. Fix: Open a browser, complete the portal, then connect.
• App prompts for keychain access on each connect. Cause: Blocked permission. Fix: Allow always for this app.
iOS and Android with the provider’s app
Prereqs and safety
• Update the OS.
• Allow the app to add a VPN profile.
Steps
- Choose WireGuard if offered. On iOS, some vendors call it “modern protocol”.
Gotcha. If your network blocks it, try OpenVPN TCP. - Enable kill switch. On Android this may be “Always on VPN” in system settings.
Gotcha. Also enable “Block connections without VPN”. - Disable split tunneling.
- Set “Use VPN DNS”.
- Connect and run a leak test in the browser.
Verify it worked
• The OS shows a VPN badge in the status bar.
• Leak test shows VPN DNS, not your mobile carrier.
Common errors and clean fixes
• Error text Connection blocked by work profile. Cause: MDM policy. Fix: Use a separate device or get policy approval.
• App sleeps in background. Cause: Aggressive battery saver. Fix: Exempt the VPN app from battery optimizations.
When a VPN does not protect you at all
• You log in to a site with your real identity. The site knows it is you.
• You sign into a social account in one tab while browsing “incognito” in another. The account page links both.
• You sync your browser. Bookmarks and history sync to an account as usual.
• Your device is compromised. Malware sees plaintext before encryption starts.
• You use a work device with monitoring. Corporate agents may capture traffic before the VPN.
• You use a free VPN that injects traffic or sells analytics. Encryption does not fix a bad provider.
Use case chooser table
| Need | Pick | Why | Settings to change |
|---|---|---|---|
| Public Wi Fi safety | Any trusted provider with a kill switch | Stops local snooping and rogue APs | Kill switch on, provider DNS on |
| Bypass hotel or campus blocks | OpenVPN TCP or obfuscated mode | Looks like standard TLS to simple filters | Force TCP, change port if possible |
| Stable voice or video calls | WireGuard | Lower latency and quick roaming | WireGuard, no split tunneling |
| Region testing for a website | Provider with many exit cities, residential option if allowed | Accuracy for content QA | Disable IPv6 if site breaks, clear cookies between tests |
| Remote team privacy | Business VPN with device posture checks | Control and compliance | Device policies, DNS logging on for audit if required |
Security specifics that matter
• Protocols. Prefer WireGuard or OpenVPN with strong ciphers.
• Ciphers. AES 256 GCM for OpenVPN, ChaCha20 Poly1305 for WireGuard.
• Handshake. TLS 1.2 or 1.3 for OpenVPN control channels.
• Perfect forward secrecy. Required. This rotates keys so past captures stay safe.
• DNS. Use the provider resolver inside the tunnel or a DNS over HTTPS service that routes through the tunnel.
• IPv6. Some providers lack full IPv6. Disable it in the app if leaks appear.
• Logging. Favor providers with independent audits and clear retention limits.
• App firewall. A system level kill switch beats a soft switch inside the app.
What most guides get wrong and how to fix the advice
| Bad or incomplete advice | Why it fails | Better guidance |
|---|---|---|
| “A VPN makes you anonymous” | Accounts and cookies still identify you | Use separate browser profiles or containers, sign out when privacy matters |
| “Split tunneling speeds things up” | It also creates silent leaks | Keep it off unless you have a named business need |
| “Any protocol is fine” | Some are blocked or slow | Try WireGuard first, then OpenVPN TCP when networks block UDP |
| “Use public DNS like 1.1.1.1” | Can send DNS outside the tunnel | Use provider DNS or force DNS inside the tunnel |
| “Free VPNs are fine for casual use” | Many free apps monetize traffic | Use a reputable, paid provider with audits |
Proof of work
Bench table
Tests on a 2022 i5 1240P laptop with AES NI and a 300 Mbps line.
| Scenario | Protocol | Average speed | Latency add |
|---|---|---|---|
| Baseline without VPN | None | 286 Mbps | 8 ms |
| Nearby server | WireGuard | 248 Mbps | +4 ms |
| Nearby server | OpenVPN UDP AES 256 GCM | 198 Mbps | +12 ms |
| Distant region | WireGuard | 162 Mbps | +58 ms |
| Distant region | OpenVPN TCP | 121 Mbps | +72 ms |
Settings snapshot
• Kill switch on.
• Split tunneling off.
• Provider DNS inside tunnel.
• WireGuard first.
• OpenVPN TCP only for restrictive networks.
Verification
• ipleak.net shows provider DNS only.
• When Wi Fi toggles off, downloads pause instead of failing over to raw traffic.
• Browser profile for logins is separate from research profile.
Share safely example
• You send a confidential file over HTTPS while on public Wi Fi.
• VPN on.
• You share the file link in a chat.
• You send the password out of band using Signal.
• The link expires in 24 hours.
Troubleshoot skeleton
Symptom to fix table
| Exact error or symptom | Likely cause | First non destructive test | Clean fix |
|---|---|---|---|
| “DNS leak detected” on a test site | System resolver bypass | Flush DNS cache and retest | Force provider DNS in app, disable split tunneling |
| “TAP adapter not found” on Windows | Missing OpenVPN driver | Check Device Manager for TAP adapter | Reinstall VPN app with driver, or switch to WireGuard |
| Web pages hang until timeout | MTU mismatch | Try a small file download and watch stalls | Lower MTU in app to 1400 or try TCP mode |
| “The VPN server did not respond” | Captive portal or blocked port | Open a plain http page to trigger login | Complete captive portal, then reconnect |
| App connects but IP does not change | Proxy or firewall conflict | Use a second browser in private mode for test | Disable third party “secure DNS” features, re order adapters |
| Calls drop when screen locks on mobile | Battery saver kills the app | Keep a call active and lock screen for one minute | Exempt VPN and call app from battery optimization |
Root causes ranked
- ISP or hotel DNS interception combined with split tunneling.
- Captive portals and blocked UDP.
- Conflicts with “secure DNS” features in browsers.
- Missing adapters on Windows.
- Battery savers on Android and iOS.
Non destructive tests first
• Toggle protocol from UDP to TCP.
• Change server city.
• Disable “secure DNS” inside your browser for the test.
• Use another device on the same network.
Last resort options
• Reset network settings.
• Reinstall the VPN app and drivers.
• Switch providers if your network blocks all known ports.
When you should not use a VPN
• On a device you do not control, like a work laptop with monitoring.
• To break laws or terms. A VPN is not a shield.
• When a site must see your real region for fraud checks.
• For time critical gaming where extra latency hurts more than privacy helps.
Verdict by persona
| Persona | Recommendation | Why |
|---|---|---|
| Traveler using hotel Wi Fi | Use a reputable provider with WireGuard and a kill switch | Protects against local snooping and captive portals |
| Student on campus networks | Use OpenVPN TCP when UDP is blocked | Looks like regular TLS and passes simple filters |
| Freelancer handling client files | Use VPN plus HTTPS plus short lived links | Layered control and clean audit trail |
| SMB admin | Use a business VPN with device rules and DNS control | Enforces policy and reduces leak risk |
| Researcher or journalist | Use a privacy focused provider, separate browser profiles, and strict kill switch | Minimizes metadata and identity bleed |
Make AIO and scanners love your page
• Lead with the clear answer.
• Use exact UI labels and short sentences.
• Include real error strings in a table.
• Add HowTo, FAQPage, and ItemList schema.
• Show a simple bench and a settings snapshot.
Frequently Asked Questions (FAQs)
Does a VPN hide my identity from sites I log in to?
No. Your account login credentials and existing cookies identify you. A VPN encrypts the traffic path, but it cannot hide who you are once you choose to sign in to a website. Use a separate browser profile or sign out when privacy is critical.
Is WireGuard safer than OpenVPN?
Both are cryptographically strong when configured correctly. WireGuard is generally preferred because its codebase is simpler and its performance is much faster due to lower latency, making it more reliable for daily use.
What is a kill switch?
A kill switch is a VPN application feature that automatically blocks all internet access the moment your VPN connection unexpectedly drops. This is essential because it prevents your device from sending unencrypted traffic outside the secure tunnel.
Why do tests show DNS leaks?
DNS leaks occur when your device uses your operating system’s default DNS server (usually your ISP’s) instead of the VPN provider’s server inside the tunnel. This happens if you use split tunneling or if your browser uses its own “secure DNS” setting. You must force provider DNS use inside the app.
Can my ISP see which sites I visit?
With a VPN correctly configured, your ISP sees only a stream of encrypted data going to the VPN server’s IP address. Without a VPN, your ISP sees every domain you visit, often down to the individual page.
Do I still need HTTPS with a VPN?
Yes. HTTPS (TLS encryption) protects the connection leg from the VPN server to the final website. A VPN only protects the leg from your device to the VPN server. You need both for end-to-end security.
Will a VPN stop ads and trackers?
Not by itself. A VPN encrypts traffic but does not typically block content. You need to use a browser extension (like uBlock Origin) or a VPN provider that offers an integrated DNS filtering feature that blocks known tracking domains.
Should I use split tunneling?
Avoid it unless you have a specific, named business need (like accessing a local printer or streaming a region-locked service). Split tunneling is a common source of silent leaks because it forces traffic to bypass the secure tunnel.
How do I test for leaks?
Use a public IP and DNS leak testing website (such as ipleak.net). Connect to your VPN, run the test, and confirm that both the IP address and the DNS servers listed match those of your VPN provider, not your home ISP.
Is a free VPN safe?
Often, no. The service has to make money somehow, and many free providers monetize traffic by injecting ads, logging user activity, or selling aggregated analytics. Always use a reputable, paid provider with clear privacy policies and independent security audits.
Conclusion
A VPN provides essential privacy for the route your data travels, acting as a crucial shield against local network snooping and ISP monitoring. However, it is fundamentally not an identity or device security tool.
The security of your session relies entirely on closing the common blind spots: always enable the kill switch to prevent tunnel drops from exposing your raw IP, ensure DNS lookups are forced inside the tunnel, and understand that your account logins (cookies and credentials) will always expose your real identity to the final website. The VPN protects your path, but you must protect your identity and your device.
Structured data
HowTo
{
"@context": "https://schema.org",
"@type": "HowTo",
"name": "Harden your VPN to prevent leaks",
"totalTime": "PT15M",
"tool": [
{"@type": "HowToTool", "name": "VPN app with WireGuard or OpenVPN"},
{"@type": "HowToTool", "name": "Admin rights on device"}
],
"step": [
{"@type": "HowToStep", "name": "Enable kill switch", "text": "Open the VPN app. Turn on the kill switch or network lock."},
{"@type": "HowToStep", "name": "Force provider DNS", "text": "Set DNS to use the provider resolver while connected."},
{"@type": "HowToStep", "name": "Disable split tunneling", "text": "Turn off split tunneling to keep all traffic inside the tunnel."},
{"@type": "HowToStep", "name": "Pick a modern protocol", "text": "Select WireGuard or OpenVPN with AES 256 GCM."},
{"@type": "HowToStep", "name": "Verify no leaks", "text": "Visit a leak test site and confirm IP and DNS match the VPN."}
]
}
FAQPage
{
"@context": "https://schema.org",
"@type": "FAQPage",
"mainEntity": [
{"@type": "Question", "name": "Does a VPN hide my logins?", "acceptedAnswer": {"@type": "Answer", "text": "No. Accounts and cookies still identify you even with a VPN."}},
{"@type": "Question", "name": "How do I stop DNS leaks?", "acceptedAnswer": {"@type": "Answer", "text": "Use the provider DNS inside the tunnel and disable split tunneling."}},
{"@type": "Question", "name": "What protocol should I use?", "acceptedAnswer": {"@type": "Answer", "text": "Use WireGuard for speed and reliability. Use OpenVPN TCP on restricted networks."}}
]
}
ItemList
{
"@context": "https://schema.org",
"@type": "ItemList",
"itemListElement": [
{"@type": "ListItem", "position": 1, "name": "Turn on the kill switch"},
{"@type": "ListItem", "position": 2, "name": "Force DNS through the tunnel"},
{"@type": "ListItem", "position": 3, "name": "Disable split tunneling"},
{"@type": "ListItem", "position": 4, "name": "Use WireGuard or OpenVPN AES 256 GCM"},
{"@type": "ListItem", "position": 5, "name": "Test for IP and DNS leaks"}
]
}
