The Ultimate Overview to Securing Cloud Folders: Achieving True Zero Knowledge with Client Side Encryption
This comprehensive report provides a strategic framework for safeguarding your data in major cloud services like Dropbox and Google Drive. Developed with the expertise of Newsoftwares.net, this overview dissects the difference between weak encryption and true zero knowledge security, providing actionable workflows that ensure your files are encrypted on your device, giving you ultimate security and digital sovereignty.
Introduction: The Illusion of Security in the Cloud
Cloud storage services like Dropbox, Google Drive, and OneDrive have become indispensable tools for modern productivity, offering unparalleled convenience for storing, syncing, and sharing files across devices. These platforms market themselves on the pillars of reliability and security, leading many users to believe their data is unequivocally safe. However, a critical distinction exists between the security model these services provide by default and the concept of true digital privacy. The common assumption that “encrypted” is synonymous with “private” is a dangerous oversimplification.
The central thesis of this report is that the standard security offered by major cloud providers, encryption at rest, is fundamentally different from and inferior to a zero knowledge security posture from a privacy standpoint. Encryption at rest means the provider encrypts your files on their servers, a crucial step that protects your data if a physical hard drive is stolen from a data center. However, the provider retains the encryption keys. This is the cryptographic equivalent of a bank storing your valuables in a safe deposit box but keeping a master key for itself. In contrast, zero knowledge encryption, achieved through client side encryption, ensures that your files are encrypted on your device before they are ever sent to the cloud. In this model, only you, the user, hold the keys.
This overview will deconstruct these security models to illuminate the inherent risks of provider held keys. It will then provide two distinct, actionable “Cloud Secure Workflows” using powerful, open source client side encryption tools. By following these workflows, users can transform their standard cloud storage into a truly private, zero knowledge repository, reclaiming ultimate control over their digital sovereignty.
Part I: Understanding the Threat Model, Why At Rest Encryption Is Not Enough
To build a truly secure cloud workflow, one must first understand the limitations of the default security provided by mainstream services. The distinction between where encryption occurs and who holds the keys is the most critical concept in modern data privacy.
The Zero Knowledge Principle: Client Side Versus Server Side Encryption
The debate over data privacy in the cloud hinges on two competing architectural models: server side and client side encryption.
-
Server Side Encryption: This is the standard model used by services like Google Drive and Dropbox for their default encryption at rest. The provider generates and manages the encryption keys. This is analogous to handing a valuable document to a bank teller who places it in a safe deposit box and stores the key behind the counter. The box is locked, but the bank retains the means to open it.
- Client Side Encryption (Zero Knowledge): This model shifts the power dynamic entirely. Data is encrypted on the user’s own device (the client) before it is uploaded to the cloud provider’s servers. The crucial difference is that only the user possesses the key to decrypt the data. The provider stores an opaque, unreadable block of data and has no ability to decipher its contents. This is akin to placing your document inside your own personal, impenetrable safe before handing it to the bank for storage.
This client side model is the mechanism that enables End to End Encryption (E2EE) for cloud storage. It guarantees that data remains confidential from the moment it leaves the user’s device until it is decrypted on another authorized device, with no intermediaries, including the service provider, able to access the plaintext information.
How Your Files Are Actually Stored: Deconstructing Provider Architectures
Major cloud storage providers have invested heavily in sophisticated security infrastructures. They all employ strong cryptographic standards to protect data on their servers and during transit.
- Dropbox: Files at rest are encrypted using 256 bit Advanced Encryption Standard (AES). Data in transit is protected by SSL/TLS. While Dropbox manages the encryption keys by default, it does explicitly support the use of third party client side encryption tools.
- Microsoft OneDrive: OneDrive employs a multi layered encryption strategy. Data is encrypted at the disk level via BitLocker and at the file level with a unique AES-256 key for each file. However, Microsoft ultimately manages this complex key hierarchy, unless an enterprise customer opts for the “Customer Key” feature.
- Google Drive: Google also encrypts data at rest using AES-256 and in transit using TLS. A significant privacy concern is that Google explicitly retains control of the encryption keys. This allows them to scan and index content, but also creates a clear conflict with the principles of zero knowledge privacy
The Inherent Risks of Provider Held Keys
The server side encryption model, while protecting against certain threats, introduces a new set of risks centered on trust in the provider.
-
Compelled Government and Legal Access: If a service provider holds the encryption keys, they can be forced by legal orders, such as warrants or national security letters, to decrypt and provide user data to government agencies. In a zero knowledge system, the provider can only hand over encrypted, useless data.
- Insider Threats and Provider Side Breaches: A malicious or compromised employee at a cloud provider could potentially access the systems that manage encryption keys, giving them access to user data. Likewise, an external cyberattack could expose not only the encrypted data but also the keys required to unlock it.
- Data Scanning and Commercialization: Providers that hold encryption keys have the technical ability to scan the contents of user files. This is often done for legitimate purposes like indexing for search, but it can also be used for data mining, targeted advertising, and enforcing terms of service. This practice is fundamentally incompatible with true data privacy.
-
Compliance Risks (GDPR/HIPAA): For businesses and professionals handling sensitive information, relying on a provider’s encryption may not be sufficient to meet the stringent requirements of regulations like the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA).
Table 1: At Rest Versus Zero Knowledge Encryption
To clarify these distinctions, the following table compares the two security models across key attributes.
| Feature | Standard At Rest Encryption (Default Cloud) | True Zero Knowledge Encryption (Client Side) |
| Key Holder | Cloud Service Provider | User Only |
| Provider Access to Data | Yes, provider can decrypt data. | No, provider only sees encrypted data. |
| Protection Against Provider Breach | Partial, keys could be compromised with data. | High, a breach only yields encrypted data. |
| Protection Against Government Request | Low, provider can be compelled to decrypt. | High, provider cannot comply with decryption request. |
| Privacy from Provider Scanning | None, provider can scan content for any purpose. | Absolute, content is unreadable by provider. |
| User Responsibility | Low, provider manages keys. | High, user is solely responsible for password/key. |
Part II: The Tools of the Trade, A Comparative Analysis of Client Side Encryption Software
Transitioning from the default security model to a zero knowledge workflow requires the use of third party, client side encryption software. Two primary architectural approaches dominate this space, each with profound implications for performance, convenience, and security when used with cloud synchronization services.
The Architectural Divide: Monolithic Containers Versus Per File Encryption
The choice between tools hinges on understanding how they structure encrypted data.
-
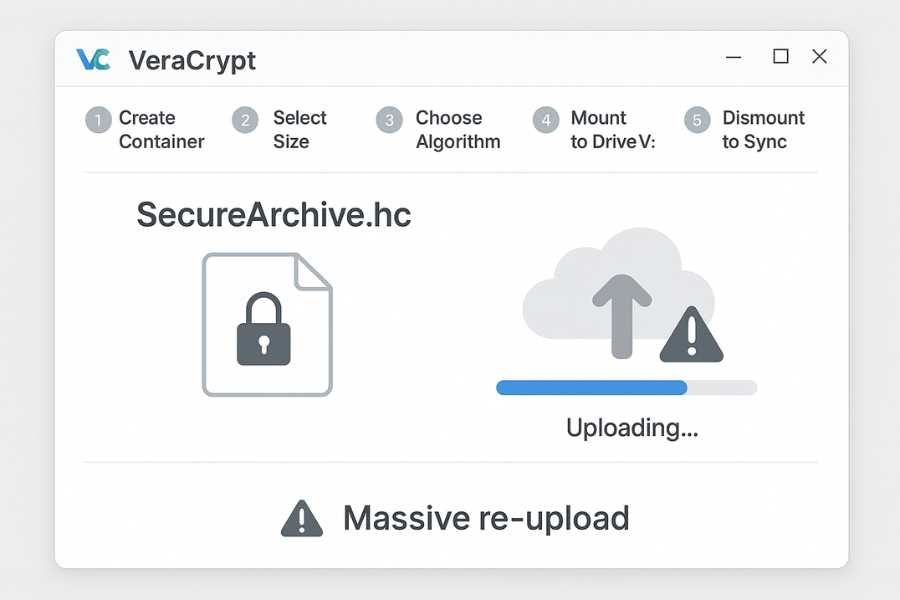
Monolithic Containers (VeraCrypt): This model involves creating a single, large, pre allocated file known as a “container” or “volume.” A small change to a single document inside a multi gigabyte VeraCrypt container necessitates the re upload of the entire container file. This is extremely inefficient and dramatically increases the risk of synchronization conflicts and data corruption.
-
Per File Encryption (Cryptomator): This model creates an encrypted “vault,” which corresponds to a folder in the user’s file system. The software encrypts each file individually. Changing a file in a Cryptomator vault requires only that one small, corresponding encrypted file be re synced, making it vastly more efficient for active cloud folders.
Deep Dive 1: VeraCrypt, The Digital Fortress
VeraCrypt is a free, open source, and well audited on the fly encryption (OTFE) tool, widely regarded as the spiritual successor to the influential TrueCrypt project.
- Security Model: VeraCrypt supports a suite of strong encryption algorithms, including AES, Serpent, and Twofish. Its standout feature is the ability to create “cascaded ciphers,” where data is encrypted sequentially by multiple algorithms. For key derivation, it uses PBKDF2 with a significantly higher number of iterations.
-
Ideal Use Cases: Due to its monolithic container architecture, VeraCrypt excels in scenarios where synchronization efficiency is not the primary concern. It is the ideal tool for full disk encryption of offline drives, creating secure archives for long term storage, or protecting large, static datasets that are modified infrequently.
Deep Dive 2: Cryptomator, The Cloud Native Vault
Cryptomator is a free, open source encryption tool designed from the ground up to secure files within cloud storage services. Its core philosophy prioritizes ease of use and seamless integration with existing cloud sync workflows.
- Security Architecture: Cryptomator employs a zero knowledge model using AES-256 encryption for both file content and filenames. Its key security feature is filename encryption and directory obfuscation. The encrypted files stored in the cloud will have scrambled, meaningless names and an obfuscated directory structure, protecting your metadata.
- Accepted Risks: To facilitate efficient syncing, Cryptomator does not hide metadata such as file sizes, modification timestamps, or the total number of files in a directory. An observer could potentially analyze changes in file sizes and access patterns, though the content and context remain secure.
-
Ideal Use Cases: With its per file encryption architecture, Cryptomator is the superior choice for securing active, dynamic folders that are frequently synced with services like Dropbox, Google Drive, and OneDrive.
The Evolving Landscape: NordLocker and Boxcryptor
The market for client side encryption is dynamic. NordLocker, which once offered a model similar to Cryptomator for use with third party clouds, has since pivoted to become an all in one, zero knowledge cloud storage provider. In a significant industry development, Boxcryptor, a leading commercial alternative to Cryptomator, was acquired by Dropbox. This move signals a growing demand for native E2EE features within major cloud platforms but may also reduce the number of independent, multi cloud encryption tools available to consumers.
Part III: The Cloud Secure Workflow: Step by Step Implementation Guides
This section provides practical, detailed instructions for implementing both the monolithic and per file encryption workflows.
Workflow 1: The “Digital Safe” Method with VeraCrypt
This workflow is best suited for archiving files or securing data that does not change frequently.
- Prerequisites: Download and install VeraCrypt from its official website. Ensure the desktop client for your cloud service is installed and running.
- Step 1: Creating the Encrypted Container
- Launch VeraCrypt and click the Create Volume button.
- Select Create an encrypted file container.
- Click Select File…, navigate to your local cloud sync folder, and enter a name for your container file, e.g., SecureArchive.hc.
- On the Encryption Options screen, use the secure default settings (AES and SHA-512).
- Specify the size of your volume, e.g., 50 GB. This space is pre allocated and fixed.
- Enter a strong, unique password.
- Move your mouse randomly within the window for at least 30 seconds to generate cryptographic randomness (entropy).
- Click Format. This process can take a significant amount of time depending on the size.
- Step 2: The Critical Configuration for Cloud Sync
- In the main VeraCrypt window, go to Settings > Preferences.
- Uncheck the box labeled Preserve modification timestamp of file containers.
- Click OK. This allows the cloud sync client to detect changes and re upload the container.
- Step 3: Daily Use, Mount, Work, Dismount
- Mount: In the VeraCrypt main window, click Select File… and choose your container file. Select an available drive letter, e.g., V:. Click Mount.
- Work: The volume will appear in your file explorer as a new drive (V:\). Open, edit, and save files directly to this drive.
-
Dismount: When you are finished working, return to the VeraCrypt window, select the mounted volume (V:\), and click Dismount. This is a mandatory step that signals the file is ready for upload.
Workflow 2: The “Seamless Sync” Method with Cryptomator
This workflow is ideal for securing active folders with files that are frequently modified.
- Prerequisites: Download and install Cryptomator from its official website. Ensure your cloud sync client is installed and running.
- Step 1: Creating the Encrypted Vault
- Launch Cryptomator. Click the + button and select Create New Vault.
- Navigate inside your local cloud sync folder, e.g., C:\Users\YourName\Dropbox\, and create a new folder for your vault, e.g., Secure Vault.
- Create a strong, unique password.
- Crucial Step: Cryptomator will display a Recovery Key. Copy this key and store it in a secure, separate location, such as a trusted password manager.
- Step 2: Daily Use, Unlock, Work, Lock
- Unlock: Select your vault, enter your password, and click Unlock.
- Work: A virtual drive appears. Drag and drop files into the drive. Cryptomator automatically encrypts each file individually in the background.
- Lock: When you are finished, click Lock in the Cryptomator interface. This unmounts the virtual drive.
- Step 3: Mobile Workflow Integration
- Purchase and install the Cryptomator app for your iOS or Android device.
- Within the mobile app, connect directly to your cloud storage provider.
-
Unlock the vault using your password (or biometrics) to securely access, view, and edit your files on the go. This is not practically achievable with VeraCrypt’s monolithic container model.
Part IV: Performance, Pitfalls, and Troubleshooting
Implementing client side encryption introduces new layers of complexity. Understanding the performance implications and potential issues is crucial for a stable and secure workflow.
The Performance Overhead: Balancing Security and Speed
All software based encryption consumes CPU resources, which can translate to a performance penalty. However, modern processors feature the AES-NI instruction set, which provides hardware acceleration for AES encryption. This often makes the speed of the storage device itself, rather than the CPU, the primary bottleneck for performance.
- VeraCrypt Performance: The most significant “slowness” associated with VeraCrypt is the initial creation of large file containers. Formatting a multi terabyte volume can take many hours, or even days.
-
Cryptomator Performance: Its primary performance weakness lies in handling a large number of very small files. The overhead of encrypting each file individually can lead to significant slowdowns when working with thousands of small documents or code repositories.
Navigating Synchronization Hazards
The interaction between the encryption layer and the cloud sync client is the most common source of problems.
-
VeraCrypt’s Achilles’ Heel: The Monolithic Sync Problem: The requirement to re upload the entire multi gigabyte container file after any minor change is VeraCrypt’s biggest drawback for cloud use. This inefficiency creates a high risk of data corruption. If synchronization is interrupted, the container file can be left in an incomplete state, often manifesting as a “corrupt volume header” error and potentially resulting in total data loss.
-
Cryptomator’s Challenge: Conflict Resolution: Cryptomator’s per file model avoids the catastrophic corruption risk of VeraCrypt, but it introduces its own complexity: sync conflicts. If a file is modified on two different devices before either has a chance to sync, the cloud provider saves both versions. Cryptomator attempts to represent these conflicted files within the unlocked vault, often by appending a suffix to the filename.
Common Error Resolution: A Practical Field Guide
- VeraCrypt Errors:
- Error: Incorrect password or not a VeraCrypt volume or The volume header is corrupt.
-
Cause & Solution: This indicates that the volume header has been damaged, likely due to an incomplete sync. The solution is to use the built in recovery tool: Tools > Restore Volume Header, and follow the prompts to use the embedded backup.
- Cryptomator Errors:
- Error: Conflict Resolution Failed or files appearing with (Conflict…) suffixes.
-
Cause & Solution: This indicates a sync conflict that Cryptomator could not automatically resolve. Manual intervention is required to compare and merge changes into one “master” version.
- Error: Decryption Failed.
-
Cause & Solution: This error suggests the encrypted file itself is corrupt, likely from a partial or failed upload. The best course of action is to use the cloud provider’s web interface to access the file’s version history and restore a previous, known good version of the file.
Table 2: Client Side Encryption Tool Comparison (VeraCrypt Versus Cryptomator)
| Feature | VeraCrypt | Cryptomator |
| Primary Use Case | Offline disk encryption, static archives | Active, synced cloud folders |
| Sync Efficiency | Very Low (re uploads entire container) | High (syncs only changed files) |
| Performance (Large Files) | Excellent | Excellent |
| Performance (Many Small Files) | Good | Poor to Fair |
| Metadata Leakage | Low (hides filenames, count, structure) | Medium (leaks file count, sizes, timestamps) |
| Ease of Use | Moderate (requires careful workflow) | High (seamless integration) |
| Mobile Access | No (impractical) | Yes (dedicated mobile apps) |
| Risk of Data Corruption | High (sync interruption can corrupt entire volume) | Low (corruption is isolated to individual files) |
Frequently Asked Questions
What is the primary difference between At Rest and Zero Knowledge Encryption?
At Rest encryption means the cloud provider holds the keys, granting them access to your data for scanning or legal compulsion. Zero Knowledge encryption means the user holds the keys (client side), rendering the data opaque and unreadable to the provider and any third party.
Which tool is better for a folder I modify several times a day?
Cryptomator is the superior choice. Because it uses per file encryption, only the single modified file needs to be re-uploaded during synchronization. VeraCrypt would require re-uploading the entire container file after every minor change, which is highly inefficient.
Why is using VeraCrypt with a cloud sync service considered risky?
VeraCrypt creates a monolithic container. If the cloud synchronization process is interrupted (e.g., losing Wi-Fi or closing a laptop) while the large container is uploading, the file’s volume header can become corrupted, leading to the total loss of all data within the container.
Can Google or Dropbox scan my files if I use Cryptomator?
No. If you use Cryptomator correctly, your files are encrypted on your device before they are sent to Google Drive or Dropbox. The provider only stores scrambled, meaningless data and has no key to decrypt it. This prevents them from scanning the content or indexing it for search.
What is the one accepted metadata risk when using Cryptomator?
Cryptomator encrypts the content and the filenames but does not hide the file sizes, modification timestamps, or the total number of files in a directory. An observer could potentially use this non-critical metadata to analyze your activity, but they cannot read the file contents.
What happens if I forget my Cryptomator vault password?
If you forget your password, you must use the Recovery Key that Cryptomator displays during the initial setup. If both the password and the Recovery Key are lost, the data within the vault is permanently unrecoverable.
Is client side encryption compatible with mobile devices?
Cryptomator is highly compatible with mobile devices, offering dedicated, paid apps for iOS and Android that can unlock and view your encrypted files on the go. VeraCrypt is impractical for mobile use due to the complexity of handling its large monolithic container files.
Conclusion: Taking Back Control of Your Digital Privacy

The convenience of modern cloud storage often comes at the hidden cost of privacy. The standard encryption at rest model employed by major providers protects data from external threats but leaves it transparent to the provider itself. This architecture creates vulnerabilities to government surveillance, insider threats, and unwanted data scanning. Achieving true data sovereignty requires adopting a zero knowledge model through client side encryption, a strategy that places the encryption keys, and therefore, ultimate control, solely in the hands of the user.
This report has detailed two powerful, open source workflows to achieve this goal. The VeraCrypt “Digital Safe” method offers maximum security and metadata obfuscation, making it ideal for archiving sensitive data that is rarely changed. The Cryptomator “Seamless Sync” method is superior for securing active, frequently synced folders, offering efficient synchronization and mobile access.
Ultimately, the choice of tool depends on the user’s specific threat model and workflow requirements. However, the technology is only part of the solution. The security of any client side encryption system rests upon the strength of the user’s password and the diligent management of recovery keys. A strong, unique passphrase, stored securely in a password manager, is the final and most critical link in the chain. By combining the right tools with responsible security practices, users can effectively transform their public cloud storage into a truly private, zero knowledge vault, ensuring their data remains secure and confidential
