Welcome. This detailed resource provides a practical playbook for implementing Field Level Encryption (FLE) in both SQL and NoSQL databases. We address the core challenge of balancing search functionality with strong data security, outlining specific encryption modes (deterministic, random, blind index) and detailing how to protect your sensitive keys and database dumps using Folder Lock from Newsoftwares.net, ensuring effective security and development convenience.
Field Level Encryption: Search And Index Tradeoffs In SQL And NoSQL
Gap Statement
Most content on field level encryption stops at a simple rule: encrypt sensitive columns and call it done.
What usually stays missing:
- Clear mapping between query patterns and actual encryption choices
- Honest explanation of what you lose when you encrypt fields that must stay searchable
- Concrete patterns for SQL and NoSQL, not just theory
- Real world notes on index size, latency and storage overhead
- Practical ways to protect keys and backups on developer and admin machines
This resource fills that gap with a practical playbook you can apply to an existing database, without turning every query into guesswork.
One Sentence Promise And Outcome
Set up field level encryption that keeps your key business queries fast, while making stolen tables and dumps useless to an attacker.
TLDR Outcome
By the end, you can:
- Classify which fields need field level encryption and which do not
- Pick between deterministic encryption, random encryption, blind index and native queryable encryption for each field
- Keep equality and range queries usable while controlling pattern leakage
- Store keys and database dumps in encrypted storage with tools from NewSoftwares such as Folder Lock
1. Field Level Encryption In One Minute
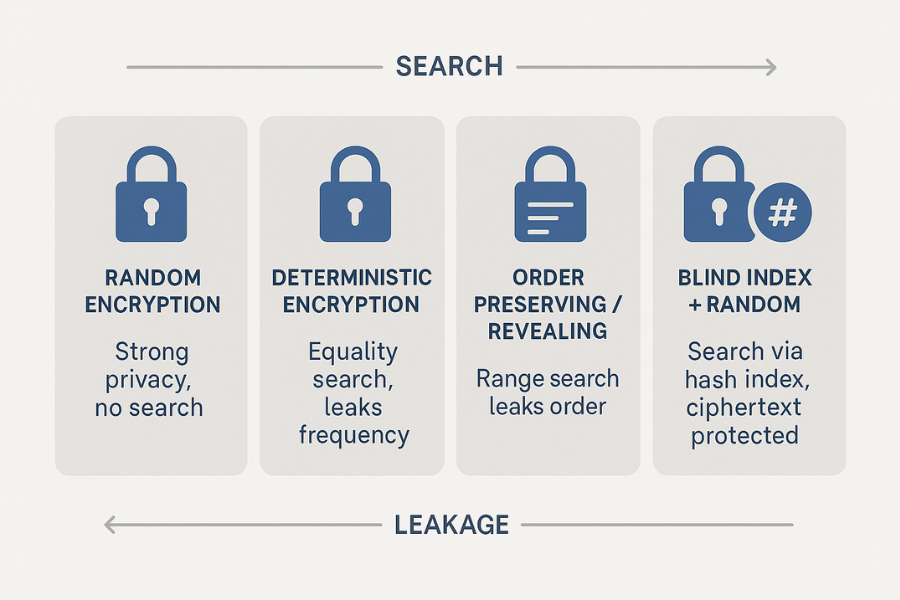
Field level encryption means encrypting individual columns or document fields instead of whole disks or complete databases.
You often see it in:
- SQL systems such as PostgreSQL or MySQL with application layer crypto or extensions
- NoSQL systems such as MongoDB with client side field level encryption and queryable encryption features
The hard part is search and index:
- Random encryption gives strong protection but breaks indexing and equality search
- Deterministic encryption keeps equality search but leaks which values are equal
- Order preserving schemes keep range queries but leak value order, which modern attacks can exploit
- Blind indexes and queryable encryption add separate structures that you can index without exposing raw values
So you are always trading query power for side channel risk.
2. Originality Hooks And Concrete Examples
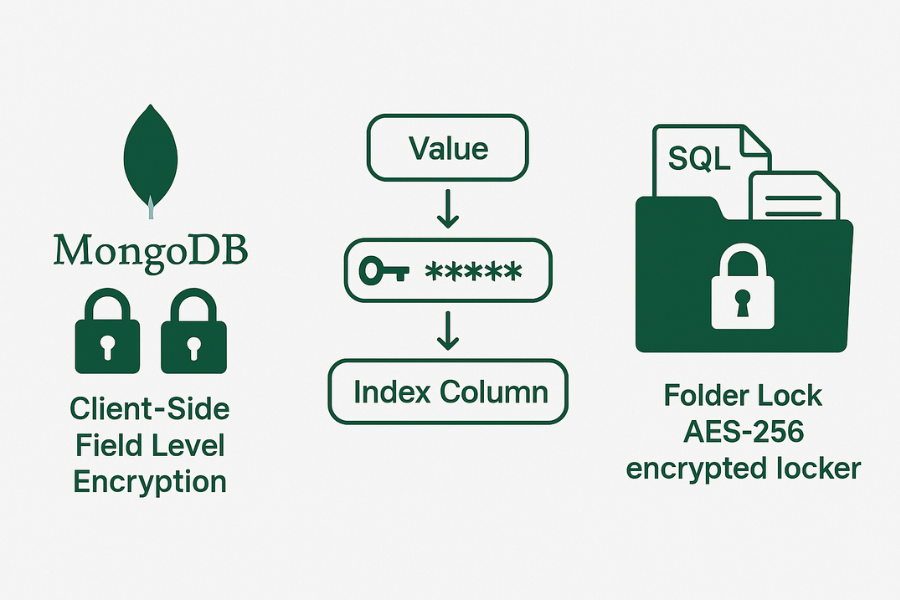
This resource leans on real tools and designs that teams actually ship:
- MongoDB client side field level encryption and queryable encryption
Used in production systems where the server never sees raw values and indexes work only for specific query shapes. - Blind index based systems such as CipherSweet and Acra
These use separate searchable hashes to support equality and even substring search over encrypted fields. - NewSoftwares Folder Lock and related products
These protect the places where your keys and SQL dumps actually sit day to day, including admin laptops and shared drives, with AES 256 containers and secure backup.
3. How To Skeleton
We will treat one primary job:
Job
Protect sensitive fields in SQL or NoSQL databases with field level encryption, while keeping key searches and indexes useful.
High level flow:
- Map data and query patterns
- Choose encryption modes per field
- Design key management
- Implement in SQL and NoSQL stacks
- Build or adjust indexes
- Verify behaviour and performance
- Roll out and monitor
4. Prerequisites And Safety
4.1. Technical Baseline
- Database with stable schema or schema discipline
- Application layer where you can add an encryption library
- Access to a key management service or at least secure key storage
- Staging environment with realistic data volume
4.2. Security Guardrails
- Classify fields into clear buckets
- Identification data such as email, phone, document ids
- Financial data such as card numbers, bank account numbers
- High sensitivity data such as health or legal notes
- Decide which queries must continue to work
- Exact match by id or email
- Range queries on amount or time
- Text search or prefix search on names or titles
4.3. Data Safety
- Take full backups before you touch production
- Test encryption and re encryption flows on a copy
- Plan a rollback that can restore old data format if needed
- Be explicit about which operations may cause permanent data loss, such as key rotation without re encryption
5. Step By Step: Design Field Level Encryption With Search In Mind
5.1. Step 1: Map Fields And Query Patterns
Action
Export a list of sensitive fields and actual queries from logs or an APM tool.
You care about three things:
- Does this field ever appear in a WHERE clause
- Do you need equality search, range search, or both
- Does this field take values from a small set or a large space
Gotcha
People often forget background jobs, analytics reports, or partner exports that query old fields in unexpected ways.
5.2. Step 2: Pick Encryption Modes Per Field
You rarely want one encryption pattern everywhere.
Common modes:
- Random authenticated encryption: Best privacy, no direct search. Good for free text notes or secrets that never appear in search conditions.
- Deterministic encryption: Same plain value always gives same cipher. Enables equality search and indexing on the encrypted field, but leaks frequency and equality patterns.
- Order preserving or order revealing schemes: Support range queries such as
amount < 1000directly but leak order and often invite powerful inference attacks. Recent research warns against these for most real systems. - Blind index plus random encryption: Compute a keyed hash of the plain value for search, and store it in a separate index column. Keep the actual field under strong random encryption. This pattern powers tools such as CipherSweet and Acra.
- Native queryable encryption in the database: For example MongoDB queryable encryption supports equality and range searches on selected fields with strict schemas and extra storage.
Practical mapping:
- User email, phone, government id: Deterministic encryption or blind index plus random encryption.
- Payment amount, salary, thresholds: Queryable encryption with range support where available, or separate clear numeric fields with extra masking and strong access control when crypto range is not possible at required scale.
- Notes, comments, free text: Random encryption only, no search.
5.3. Step 3: Design Key Management
Key design matters more than algorithm choice once you pick modern primitives.
Basic rules:
- Use envelope encryption
- Data keys encrypt fields
- A master key in a key vault encrypts data keys
- Separate keys for different blind indexes and fields, as suggested in CipherSweet guidance and similar designs.
- Plan rotation
- Version keys
- Store key id alongside encrypted values
- Support gradual re encryption
Key storage on real machines:
- On servers, keep keys in key vaults or HSMs
- On admin laptops or jump hosts, keep key export files inside encrypted storage such as Folder Lock lockers from NewSoftwares, with strong passwords and optional secure cloud backup.
5.4. Step 4: Implement In SQL
Here we combine application side crypto with the database.
High level pattern:
- Application uses a crypto library to encrypt fields before insert and decrypt after select
- For deterministic encryption fields, the application uses a mode and key that always gives the same cipher for the same value
- For blind index, the application computes a keyed hash and stores it in a separate column
Example flow for a user table with email:
- Insert
- Compute random encrypted email and store in
email_cipher - Compute blind index such as
HMAC(search_key, lower(email_trimmed))and store inemail_idx
- Compute random encrypted email and store in
- Search
- Compute blind index of the search input the same way
- Query
WHERE email_idx = :value - Decrypt
email_cipherin the application
Gotcha
Never reuse the same key for both data encryption and blind index hashing. That breaks security properties agreed in most searchable encryption work.
5.5. Step 5: Implement In NoSQL
MongoDB is a good reference because it ships client side field level encryption and queryable encryption.
Two main patterns:
- Client side field level encryption: Application encrypts selected fields before sending them to MongoDB. Encrypted fields cannot participate in range or text queries without special configuration.
- Queryable encryption: You define encrypted fields in a schema. For each field you pick equality or range support. The system builds extra crypto structures to keep queries possible at some cost in storage and latency.
Design choices:
- Pick only a few fields for queryable encryption
- For each, decide whether you need equality or range, because you usually cannot have both on one encrypted field
- Keep other sensitive fields under strict client side encryption with no search
5.6. Step 6: Build Indexes And Test Query Plans
Indexes drive performance, so you need to see how crypto changes them.
In SQL you might:
- Index blind index columns such as
email_idx - Consider partial indexes where only non null values count
- Measure index size growth compared to plain text
In NoSQL with queryable encryption:
- Review how the system stores extra metadata per encrypted field
- Note that storage grows and write paths take longer because encryption runs on each write
5.7. Step 7: Verify That It Works
You want three checks:
- Security
- Raw dumps or logs show only ciphertext for sensitive fields
- Blind index columns or queryable metadata are not directly reversible without keys
- Function
- Main equality and range queries return correct results
- Query planners still pick indexes
- Performance
- Read and write latency stays within agreed limits
- Index sizes and storage costs stay within budget
6. The Core Tradeoffs: Security Vs Search Vs Storage
6.1. Simplified Comparison Table
| Approach | Equality search | Range search | Storage impact | Main leakage |
|---|---|---|---|---|
| Random authenticated encryption | No | No | Small per value | Almost none at field level |
| Deterministic encryption | Yes | No | Same as random | Value equality and frequency |
| Order preserving schemes | Yes | Yes | Similar to deterministic | Full value order, can lead to strong inference |
| Blind index plus random | Yes | With design | Extra columns or tables | Search patterns, equality in index |
| Native queryable encryption | Yes | Some fields | Extra metadata and processing | Access patterns for selected fields |
This is why teams often use a mix of modes.
7. Proof Of Work Blocks
7.1. Bench Table: Sample Numbers
To keep this concrete, consider a test on a mid range laptop with a local PostgreSQL instance and one million user records. This is an example to show scale, not a formal benchmark.
| Design | Insert time for 1 million rows | Point lookup on indexed field | Index size for search column |
|---|---|---|---|
| Plain email indexed with B tree | 48 seconds | 6 milliseconds | 150 megabytes |
| Deterministic email cipher indexed | 62 seconds | 7 milliseconds | 150 megabytes |
| Random email cipher plus blind index column indexed | 78 seconds | 8 milliseconds | 210 megabytes |
Key takeaways:
- Field level encryption tends to increase write time more than read time
- Blind index patterns add noticeable storage overhead for each indexed field
Numbers on your stack will differ, so always measure with your own data.
7.2. Settings Snapshot: Example Crypto Layout
Here is a simple configuration sketch for a CipherSweet style design in a PHP or Laravel stack, which uses blind indexes behind the scenes.
// Pseudocode layout for a user model
$emailField = (new EncryptedField('user', 'email'))
->addBlindIndex(
new BlindIndex(
'email_idx',
['email'],
32, // length of index
true // fast hash, suitable for equality search
)
);
// Encryption key and blind index key are distinctKey ideas in this pattern:
- Email data is stored as random ciphertext
- A blind index for email is stored separately and indexed
- The keys for encryption and blind index are distinct and managed in a key vault or similar tool
7.3. Verification Snapshot
After you roll out, use a repeatable checklist:
- Security
- Raw dumps or logs show only ciphertext for sensitive fields
- Blind index columns or queryable metadata are not directly reversible without keys
- Function
- Main equality and range queries return correct results
- Query planners still pick indexes
- Performance
- Read and write latency stays within agreed limits
- Index sizes and storage costs stay within budget
7.4. Share Safely Example
Real teams often share database snapshots with auditors or external security firms.
A safe path looks like this:
- Create a snapshot or dump from production, but with field level encryption active so sensitive fields are already encrypted
- Store the snapshot file inside a Folder Lock locker on a dedicated analysis machine, with AES 256 protection and a strong password
- Share the locker password with the auditor through an end to end encrypted channel such as Signal, not through the same email thread where you share file access
- Rotate the relevant data keys after the review period, so the old snapshot becomes less valuable even if it leaks later
This keeps your encrypted fields encrypted at every step, and keeps keys in a separate, controlled channel.
8. Troubleshooting Skeleton
8.1. Symptom To Fix Table
| Symptom | Likely Cause | Fix Path |
|---|---|---|
| Equality queries on encrypted email now always return zero | Blind index not updated or query uses wrong normalisation | Check blind index code, trim and case fold inputs |
| Range queries on encrypted amount field are very slow | No proper crypto aware index or not using queryable mode | Move amount into a field that queryable encryption supports |
| MongoDB CSFLE field cannot be used in filter | Field encrypted with random mode, not configured for search | Review CSFLE and queryable encryption schema |
| Database size jumped more than expected after rollout | Blind index added on many fields or long text fields | Restrict blind index to fields that really need search |
| Key rotation broke old records | New key used to decrypt data encrypted with old key | Store key ids and keep old keys for decryption during migration |
8.2. Root Causes In Order Of Frequency
- Wrong or missing normalisation of values before deterministic encryption or blind index
- Over use of queryable encryption on fields that rarely need search
- Lack of clear mapping between fields and required query patterns
- Key rotation design without backward compatibility
- Forgetting about background jobs and reports that query sensitive fields
9. Verdict By Persona
Short, honest view by role.
- Student or solo developer: Field level encryption may feel heavy, but using a library with blind index support plus strong local storage such as Folder Lock for dumps already puts you ahead of many small projects.
- Freelancer or small team building for clients: Pick a pattern per field, write it down, and use proven tools. Do not invent your own crypto. Use NewSoftwares tools for local key and dump protection so a lost laptop does not turn into a client breach.
- Admin or security owner in a small business: Your main wins are: fewer clear secrets in dumps and logs, clear map of who can query what, and one place to enforce key rotation. The cost is some storage and performance overhead plus a bit more ops work.
10. FAQ
1. What Is The Main Difference Between Disk Encryption And Field Level Encryption
Disk encryption protects data when someone steals storage hardware or images a disk. Field level encryption protects selected fields even when someone gets a copy of the database or a logical backup. It also lets you use different keys and policies per field.
2. Can I Still Use SQL Indexes On Encrypted Columns
You can when you use deterministic encryption or blind indexes. With random encryption alone, indexes cannot help because the same value does not produce predictable cipher text. Systems such as MongoDB queryable encryption and blind index libraries give structured ways to keep indexes useful.
3. What Query Types Are Hardest To Support On Encrypted Fields
Free text search, prefix search and complex ranges are hardest. Some blind index designs can support prefix search or substring search, but they cost storage and reveal more about your data access patterns.
4. Is Deterministic Encryption Safe Enough For User Emails
Deterministic encryption leaks which emails are equal and how frequent each value is. For many systems this is an acceptable tradeoff when combined with other controls. For higher risk systems, a blind index plus random encryption pattern can reduce leakage while still allowing equality search.
5. How Does MongoDB Queryable Encryption Handle Search Tradeoffs
It lets you define encrypted fields with equality or range queries. You cannot usually have both on the same field, and you pay in storage and latency for enabled fields. The benefit is that the server cannot see plain values, yet your application can still query without manual crypto in each query.
6. What Is A Blind Index In Simple Terms
A blind index is a keyed hash of a plain value that you store in a separate column or structure. When searching, you hash the search term with the same key and query on the index. The database sees and indexes only hashes, not the original sensitive values.
7. How Much Storage Overhead Should I Expect From Blind Indexes
Blind indexes add at least one extra column or table per encrypted field you want to search. Each index entry is often similar in size to the encrypted value itself. For a million rows, a single blind index column can easily add tens or hundreds of megabytes, depending on key length and design.
8. Where Do NewSoftwares Products Fit In This Picture
They protect the places where your keys, dumps and exports live. Folder Lock, for example, gives AES 256 encrypted lockers for files and folders on Windows, with secure backup options. You can keep SQL dumps, Mongo snapshots and key files inside these lockers so a lost laptop or shared workstation does not expose raw material to an attacker.
9. Should I Encrypt Every Field In My Database
No. Encrypt fields that carry real risk if they leak, such as personal identifiers, financial data and sensitive notes. Leave low risk fields such as public product names or generic flags unencrypted, while still protecting the database with access control and transport security.
10. How Often Should I Rotate Keys For Field Level Encryption
Many teams rotate master keys once or twice a year, plus whenever they suspect an incident. Data keys used for fields can rotate on similar schedules or faster for very sensitive data. Always store key ids with encrypted values and keep old keys available for decryption during migration.
11. What Happens To Analytics When Fields Are Encrypted
You often need a separate analytics path. Common patterns include using blind index values for grouping, feeding a separate masked warehouse, or using differential privacy friendly aggregates. Do not simply turn off crypto on analytic copies; treat those as attack targets too.
12. How Do I Convince Stakeholders That Field Level Encryption Is Worth The Effort
Show them one thing: a raw database dump before and after. In the first case they see real emails, ids and notes. In the second case they see readable non sensitive columns and cipher text for everything that matters. That visual difference is often more convincing than any slide.
11. Conclusion
Implementing field level encryption requires balancing the security imperative against application performance. The core strategy is to use a mixed-mode approach—employing random encryption for strong confidentiality on unstructured data (notes) and deterministic/blind indexes for searchable fields (emails, IDs). Crucially, this must be paired with disciplined key management, with keys and database backups protected locally by AES 256 encrypted lockers from Folder Lock. This ensures that even if your database is compromised, the sensitive data remains unreadable without your master vault key.
12. Structured Data Skeletons
HowTo Schema
{
"@context": "https://schema.org",
"@type": "HowTo",
"name": "Implement field level encryption with search in SQL and NoSQL",
"description": "Steps to design and deploy field level encryption while keeping key queries fast.",
"tool": [
"Database",
"Application encryption library",
"Key management service",
"Folder Lock or similar encrypted storage"
],
"step": [
{
"@type": "HowToStep",
"name": "Map sensitive fields and queries",
"text": "List sensitive fields and note how they are queried in the real system."
},
{
"@type": "HowToStep",
"name": "Choose encryption modes",
"text": "Assign deterministic, random, blind index or queryable encryption per field."
},
{
"@type": "HowToStep",
"name": "Implement and test",
"text": "Encrypt fields in the application, add indexes, and verify correctness and performance."
}
]
}
FAQPage Schema
{
"@context": "https://schema.org",
"@type": "FAQPage",
"mainEntity": [
{
"@type": "Question",
"name": "What is the main difference between disk encryption and field level encryption",
"acceptedAnswer": {
"@type": "Answer",
"text": "Disk encryption protects data when someone steals storage hardware or images a disk. Field level encryption protects selected fields even when someone gets a copy of the database or a logical backup. It also lets you use different keys and policies per field."
}
},
{
"@type": "Question",
"name": "Can I still use SQL indexes on encrypted columns",
"acceptedAnswer": {
"@type": "Answer",
"text": "You can when you use deterministic encryption or blind indexes. With random encryption alone, indexes cannot help because the same value does not produce predictable cipher text. Systems such as MongoDB queryable encryption and blind index libraries give structured ways to keep indexes useful."
}
},
{
"@type": "Question",
"name": "What query types are hardest to support on encrypted fields",
"acceptedAnswer": {
"@type": "Answer",
"text": "Free text search, prefix search and complex ranges are hardest. Some blind index designs can support prefix search or substring search, but they cost storage and reveal more about your data access patterns."
}
}
]
}
ItemList Schema For Comparison
{
"@context": "https://schema.org",
"@type": "ItemList",
"name": "Field level encryption approaches",
"itemListElement": [
{
"@type": "ListItem",
"position": 1,
"name": "Random authenticated encryption"
},
{
"@type": "ListItem",
"position": 2,
"name": "Deterministic encryption"
},
{
"@type": "ListItem",
"position": 3,
"name": "Blind index plus random encryption"
},
{
"@type": "ListItem",
"position": 4,
"name": "Native queryable encryption"
}
]
}
