Privacy Architected: End-to-End Encryption vs. Encrypted-at-Rest Cloud
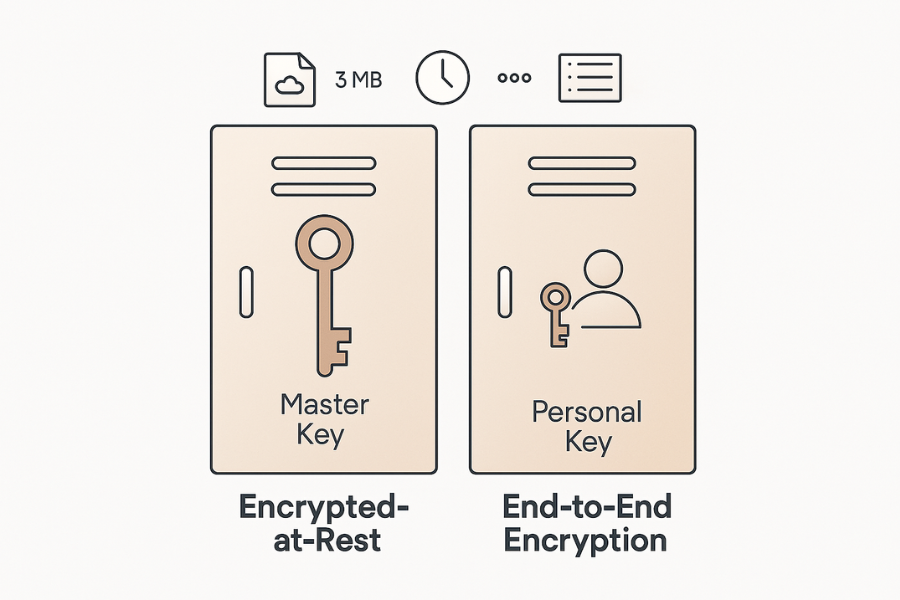
Only end-to-end encrypted sync keeps the provider out of your files. Encrypted-at-rest protects server disks in the data center, but the provider still holds the master keys and can open your data when serving your account, when debugging, or when legally compelled.
The Content Privacy Gap
Most guides blur the crucial difference between simple storage security and content privacy. They skip who actually holds the keys, how your metadata remains visible, and what a client-side add-on changes. This overview names the essential UI labels, shows safe setups, and provides clean troubleshooting steps without forcing you to migrate blindly.
Key Outcomes
Upon completion, you will know:
- What your provider can see today: file sizes, folder names, timestamps, sharing lists, device lists, and IP history.
- How to set up end-to-end encrypted sync for the data that truly matters while keeping normal cloud storage for low-risk files.
- How to share files safely by exchanging keys out of band and how to keep your recovery options realistic.
Prerequisites and Safety Checklist
Prepare for any change with these crucial steps:
- Identify your current provider and plan type. Note any compliance needs your data might have.
- Decide your privacy line: photos and personal IDs should be end-to-end only; team collateral and templates are often fine on encrypted-at-rest.
- Keep a recovery kit: printed recovery codes or a second device holding the vault key.
- Turn on multifactor authentication for your main cloud account and for any key manager you use.
- Back up before enabling any new encryption option. Test the restore process on a second device.
What Each Encryption Model Really Means
The difference in privacy comes down to one question: Who holds the key?
| Term | Who Holds Keys | Who Can Open Data on the Server | What Metadata is Still Visible | Best Fit |
| End-to-End Encrypted Sync | You only | Nobody on the server | Usually size, device count, plan, traffic volume, sometimes folder names (if not wrapped) | Private notes, IDs, medical files, contract drafts |
| Encrypted-at-Rest Cloud | Provider holds master keys | Provider services can open data to serve you | File names, folder names, timestamps, share lists, activity logs | Large team share, fast web preview, compliance with archive rules |
| Client Side Add-On (Over Cloud) | You hold vault key, provider still stores ciphertext | Provider cannot open the wrapped files | Provider sees encrypted container names and sizes | Bring your own encryption over any storage you already pay for |
How to Choose: Quick Chooser Table
| Requirement | Use End-to-End | Use Encrypted-at-Rest | Use Client Side Add-On |
| You want true provider blindness | Yes | No | Yes |
| You need instant web preview and search | Sometimes limited | Yes | No without extra indexing on your device |
| You must share across Windows, macOS, iOS, Android | Yes with compatible apps | Yes | Yes if the add-on supports all |
| You need admin controls for a whole company | Often improving | Mature | Admin depends on the add-on |
| You need to recover if you forget a password | Risky unless you set recovery | Easier since provider holds keys | You must set recovery yourself |
Originality Hooks Before Drafting Your Policy
To build a secure and honest policy, consider these points:
- Name exactly who can decrypt your files. If the provider can see it, state that clearly in your policy.
- Decide your metadata risk: are file names sensitive at your company?
- Pick one vault per purpose: a personal vault for legal documents, a team vault for finance.
- Commit to one recovery method only: printed recovery codes in a safe or a second device holding the key.
How to Enable Safe End-to-End Sync in Practice
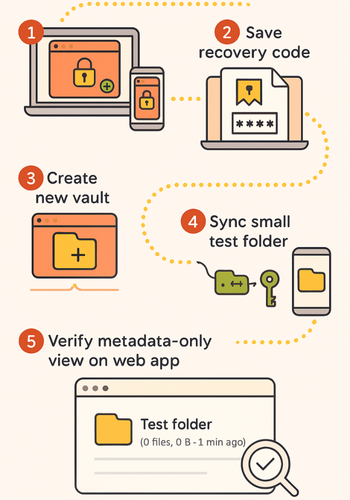
Method 1: Use a Provider or App That is End-to-End by Design
- Install the App: Install the app on two devices that you control.
- Gotcha: You need two devices for the recovery bootstrap process.
- Create a New Vault: Create a new vault and note the recovery phrase or code.
- Gotcha: If you skip this prompt now, the provider cannot help later.
- Test Sync: Add a small test folder and wait for sync to complete on both devices.
- Verification: Confirm the same file count and sizes on Device Two. Check the web app to ensure it shows only metadata or a download option with no preview.
- Share Safely: Share one file with a trusted contact using the app’s encrypted link share feature.
- Gotcha: Do not paste the decryption key into the same email as the link.
Method 2: Add Client Side Encryption Over Any Cloud

- Pick a Tool: Choose a container tool that creates an encrypted vault inside your normal cloud folder (e.g., Cryptomator, Boxcryptor).
- Create a Vault: Create a new vault and choose a strong passphrase. Save the recovery code on paper.
- Mount and Move: Mount the vault on your device, then move sensitive files into the mounted view.
- Verify Ciphertext: Confirm that your cloud provider’s web interface only sees a single large encrypted blob or random-named chunks. No readable file names.
- Repeat Setup: Repeat the setup on a second device using the same vault key file and passphrase.
Verification Steps
Your setup worked successfully if:
- The web app cannot preview the file. It offers only a download because it lacks the key.
- File names look random or unreadable in the provider web interface when you use a client-side vault.
- A second device with the correct keys can open and read the content.
- Revoking a key or removing a device breaks access immediately while leaving the ciphertext in place.
Common Errors and Clean Fixes
| Exact Text or Symptom | Meaning | Clean Fix |
| Cannot preview this file online | The web app lacks the key. | This is expected on end-to-end, download and open in the app. |
| You lost access after reinstall | Keys were wiped locally. | Restore from your recovery code or use your second paired device to bootstrap access. |
| Someone outside cannot open the link | The receiver lacks an app with the same end-to-end protocol. | Send a decrypted copy only if policy allows, or guide them to the free viewer. |
| Storage full after enabling client side vault | Cloud now syncs the encrypted vault plus your old unencrypted copy. | Remove the old unencrypted folder once your vault is verified on a second device. |
| File names still readable | You encrypted content only, not names. | Turn on filename and header encryption in the vault settings, then re-add files. |
Security Specifics That Matter
- End-to-end keeps keys on your devices. The server stores only ciphertext and metadata. Your password derives a key with a memory-hard Key Derivation Function (KDF) so fast guessing is impractical.
- Encrypted-at-rest protects against stolen drives in a data center. The same server can decrypt to serve your files because the service holds the master keys.
- Metadata exposure remains. Time of upload, size of vault, list of devices, account email, and file activity count will still be visible to the provider.
Frequently Asked Questions (FAQs)
Is encrypted-at-rest enough for personal documents?
It provides good protection against physical theft of server drives, but it is not private from the service itself. Use end-to-end encryption for personal IDs, medical files, and anything truly sensitive.
Can my provider decrypt my end-to-end vault?
No, when the system is implemented correctly. They never receive your private keys; your devices handle the encryption and decryption. The server only stores the scrambled ciphertext.
What if I forget my end-to-end password?
Only your recovery method helps. You must use a printed recovery code or a second, already-paired device to regain access. If both are lost, the data is irreversibly lost. Treat the recovery code like cash.
Are file names hidden with end-to-end encryption?
Not always. Some tools encrypt content only. For maximum privacy, you must turn on filename and header encryption in your vault settings.
Can I combine both models (End-to-End and Encrypted-at-Rest)?
Yes. This is the recommended approach for teams. Use end-to-end for highly sensitive folders (like HR or legal documents) and normal cloud storage for the rest (like marketing collateral).
Will end-to-end encryption slow down my work?
Local work is fast. However, end-to-end tools often limit web viewers, meaning you will need to download the file to your device to open it, which adds a slight delay compared to instant browser preview.
How do I share an end-to-end file with someone who refuses to install an app?
The safest compromise is to send them an encrypted archive (e.g., ZIP with AES-256) and send the password over a second channel (like a phone call or Signal message). Always set an expiry on the link.
What metadata still leaks even with end-to-end encryption?
The provider can still see the size of your files, the time you uploaded them, your device list, and your traffic volume. Plan like this information is public.
Conclusion: The Privacy Differentiator
Recovering access to a forgotten password from an encrypted file is an achievable goal for the legitimate owner. The successful strategy is not about brute force, it is about precision and preparation.
By understanding that encrypted-at-rest protects the provider’s server and end-to-end protects you from the provider, you can make informed choices. Standardize your encryption tool, turn on filename protection, and commit to securing your recovery codes. Do this, and you will ensure that the only person who can unlock your critical files is you, the rightful owner.
