Encryption Through the Ages: From DES and 3DES to AES-256 and Beyond

Encryption standards do not just evolve; they are forced to retire when mathematical breakthroughs or computing power expose their foundational weaknesses. The transition from the Data Encryption Standard (DES) to the Advanced Encryption Standard (AES) was driven by the catastrophic failure of key length and the rise of dedicated hardware cracking.
The security of modern data relies on recognizing three historical shifts:
- DES to 3DES: A desperate attempt to survive the immediate brute, force threat by tripling the key length.
- 3DES to AES: A complete architectural replacement demanded by the computational overhead and the primary flaw of 3DES (the Meet, in, the, Middle attack).
- AES to AEAD (Authenticated Encryption): A shift from merely guaranteeing confidentiality to guaranteeing both confidentiality and integrity to prevent malicious data tampering.
For any data requiring protection over the next decade, the minimum standard is AES, 256 implemented using an Authenticated Encryption with Associated Data (AEAD) mode like GCM. This is the only commercially available standard currently considered resistant to theoretical quantum computing attacks.
I. The Failed Legacy: Key Length Catastrophe (DES and 3DES)
The first federal standard, DES, provided a critical foundation for cryptography, but its short lifespan serves as a harsh lesson in computational security. Its successor, 3DES, offered a temporary fix that ultimately proved too slow and flawed for the digital age.
1.1. Data Encryption Standard (DES): A 56, Bit Failure
The DES algorithm, developed in the 1970s, established the block cipher structure used today. Its fatal flaw was a key length of only 56 bits. In the late 1990s, dedicated hardware became cheap enough to crack this key size quickly.
In 1998, the EFF’s “Deep Crack” machine demonstrated the end of DES by breaking a key in just 56 hours. By January 1999, distributed efforts further reduced the cracking time to 22 hours and 15 minutes. This proved 56, bit encryption was no longer safe for any long, term sensitive data.
1.2. Triple DES (3DES): The Temporary Patch
To temporarily patch the DES failure without rebuilding existing banking and infrastructure systems, the industry adopted Triple DES (3DES or TDEA). This method runs the DES algorithm three times, effectively increasing the key length to 168 bits.
3DES offered enough protection to be reaffirmed as a FIPS standard in 1999. However, it suffered from two major operational problems that forced its retirement:
- Performance Overhead: Running the cipher three times made 3DES three times slower than its single DES counterpart. This was a significant performance drain on high, throughput systems.
- Meet, in, the, Middle Attack (MITM): Despite the 168, bit key, 3DES is vulnerable to the MITM attack. This attack reduces the brute, force complexity from $2^{168}$ to approximately $2^{112}$ operations, which is still massive but demonstrates the inherent insecurity of chaining weaker ciphers.
This combination of slow performance and a known mathematical vulnerability led the Payment Card Industry (PCI DSS) to mandate its replacement. The final retirement of the supporting standard, PCI DSS v3.2.1, occurred in March 2024. The US government also encouraged the use of AES over 3DES starting in 1999.
II. The Modern Benchmark: AES-256 and Quantum Resistance
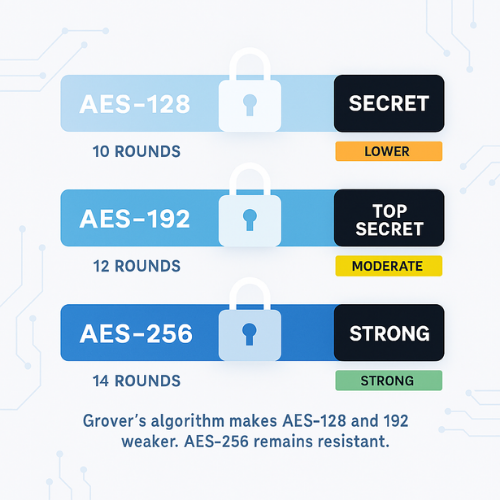
The Advanced Encryption Standard (AES) was selected by the U.S. National Institute of Standards and Technology (NIST) in 2001 to replace DES. Based on the Rijndael block cipher, AES fixed the block size at 128 bits and offered three distinct key lengths: 128, 192, and 256 bits.
2.1. Key Length and Security Margin
AES security is scaled by increasing the key size, which also increases the number of encryption rounds performed, adding to the cryptographic defense.
| AES Key Size | Encryption Rounds | Security Margin |
| 128, bit | 10 rounds | Sufficient for general use |
| 192, bit | 12 rounds | Enhanced resistance, required for classified data |
| 256, bit | 14 rounds | Maximum security, recommended for long, term data |
The U.S. Government announced in 2003 that AES, 128 was sufficient for classified information up to the SECRET level, but TOP SECRET data requires either the 192, bit or 256, bit key length. This establishes AES, 256 as the highest civilian and government standard for maximum confidentiality.
2.2. Beyond Brute Force: The Quantum Challenge
For data intended to remain secret for decades, AES, 256 is the only viable choice among these established standards.
Future quantum computers using Shor’s algorithm could theoretically crack RSA and ECC public key cryptography. Grover’s algorithm, a quantum search algorithm, could reduce the effective security strength of symmetric ciphers.
Under a quantum attack:
- AES, 128’s security strength drops to 64 bits, rendering it insecure.
- AES, 192’s security strength drops to 96 bits, rendering it insecure.
- AES, 256 retains 128 bits of effective security, making it the only option considered quantum, resistant among the AES family.
Organizations must mandate the use of AES, 256 today to safeguard data against the eventual deployment of cryptographically powerful quantum computers.
III. The Modern Flaw: Integrity and the AEAD Mandate
Even with AES, 256, older encryption modes contain critical flaws that compromise data integrity, allowing silent, malicious tampering.
3.1. The Dangers of Legacy Block Modes
Block ciphers like AES must use a mode of operation (like ECB, CBC, or GCM) to handle long streams of data. Older, simple modes present severe, exploitable vulnerabilities:
- Electronic Codebook (ECB): ECB encrypts identical blocks of plaintext into identical blocks of ciphertext. This mode is visually vulnerable. For example, encrypting an image with ECB clearly retains the original image’s outline and patterns, revealing information without breaking the key. It must never be used.
- Cipher Block Chaining (CBC): CBC provides superior confidentiality to ECB but lacks any integrated integrity check. An attacker can modify blocks of ciphertext in a predictable manner, known as a bit, flipping attack, which corrupts the plaintext upon decryption without raising any error flag. This integrity gap is a massive security failure.
3.2. Authenticated Encryption with Associated Data (AEAD)
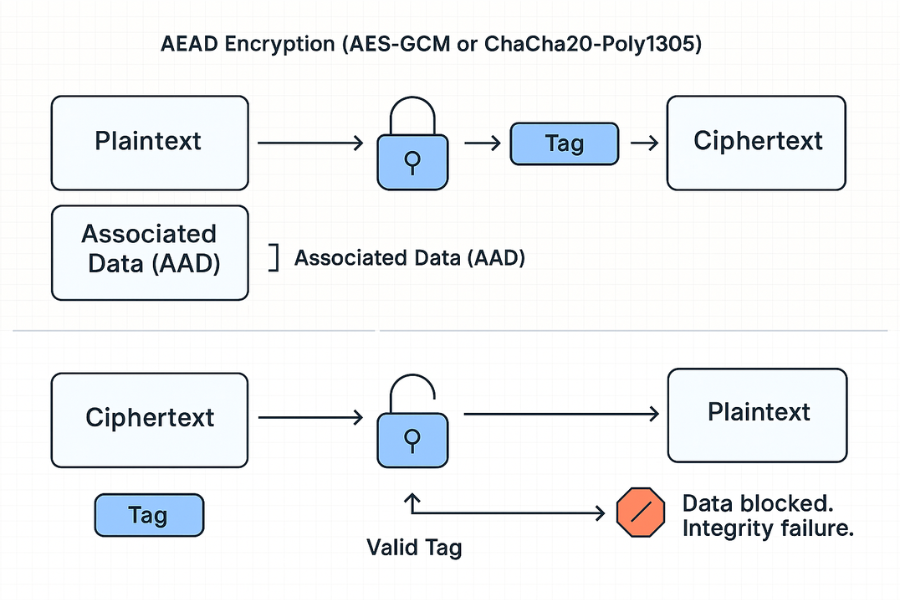
Authenticated Encryption with Associated Data (AEAD) is the mandatory modern solution. It solves the integrity gap by combining encryption (for confidentiality) and a Message Authentication Code (MAC) (for integrity) into one function.
How AEAD Works:
- Encryption: The plaintext is scrambled into ciphertext.
- Tag Generation: A unique cryptographic tag is generated from the key, a Nonce (a number used once), and the ciphertext.
- Integrity Check: Upon decryption, the recipient recalculates the tag. If the calculated tag does not perfectly match the received tag, the system halts instantly. It refuses to output any plaintext, preventing both corruption and malicious tampering.
The “Associated Data” (AAD) feature allows the system to authenticate unencrypted metadata, such as file headers or protocol versions, ensuring the integrity of the entire data package.
3.3. AEAD Algorithm Choice: GCM Versus ChaCha20, Poly1305
The choice between the two leading AEAD standards often comes down to the host CPU architecture.
| Algorithm | Key Advantage | Best Use Case |
| AES, GCM | Hardware, accelerated performance via AES, NI CPU instructions. | High, throughput servers, modern desktop PCs, and enterprise environments with hardware support. |
| ChaCha20, Poly1305 | Excellent, consistent software performance; low CPU overhead. | Mobile devices (ARM CPUs), embedded systems, and systems lacking AES, NI acceleration. |
ChaCha20, Poly1305 is often preferred for mobile use due to its fast software performance and lower power consumption compared to software, only AES, GCM implementations.
IV. Practical AEAD Implementation: Securing Portable Files
For reliable cross, platform security that requires both confidentiality and integrity, professional, grade archival tools are the definitive solution. They prevent data leakage and ensure the integrity tag is properly calculated.
4.1. Prerequisites: Defending the Key
The cryptographic key must be derived from a strong, unique password. Standard encryption utilities, such as 7, Zip, implement Key Derivation Functions (KDFs) based on the SHA, 256 hash algorithm.
This KDF process is deliberately slow, performing a large number of iterations to stretch the simple text password into a high, entropy key. This “key stretching” protects against dictionary attacks and brute, force attempts, making the resulting AES, 256 encryption resilient.
4.2. How, To: Creating a Secure AEAD Archive (7, Zip)
Using a standard tool with the correct settings is the most common way to apply AEAD protection to portable files.
- Select and Archive: Locate the file(s) or folder. Right, click the selection, choose 7, Zip, and click Add to Archive….
- Select AES, 256: In the Archive dialogue box, set the
Encryption Methodto AES, 256. Enter and confirm a strong password (minimum 8 characters, mixed case, and numerals). - Critical Privacy Step: Encrypt File Names: Under the Encryption section, check the box labeled Encrypt file names.
Gotcha: If you skip checking “Encrypt file names,” an attacker can open the archive and read the internal file names and folder structure (metadata) without the password. This compromises privacy and often flags the file for blocking by enterprise DLP security systems.
Verification (Proof of Work): Attempt to open the resulting .7z file without entering the password. The utility must immediately block access and show no internal file names, confirming the metadata is secured.
4.3. Safe Key Exchange Protocol
AEAD security is nullified if the key is sent via the same channel as the encrypted file. Always use dual, channel transmission:
- Primary Channel (File): Send the encrypted 7, Zip file via email or cloud link.
- Secondary Channel (Key): Send the decryption password via a separate, secure, out, of, band method, such as Signal, SMS, or a secure voice call.
V. Troubleshooting: Decryption Errors and AES Failures
Decryption failure signals a problem: either the key is wrong, or the data integrity check has failed.
5.1. EFS Key Failure (Windows)
Windows Encrypting File System (EFS) is tied to the user’s private key certificate. If this key is unavailable, decryption fails with specific error codes.
| Symptom / Error Code | Root Cause | Non, Destructive Fix |
The specified file could not be decrypted. (0x80071771 or 6001) |
EFS Private Key/Certificate is missing or inaccessible on the new system. | 1. Open Windows Certificate Manager (certmgr.msc). 2. Import the backup .pfx file into the Personal Certificates store. 3. Verify the certificate’s General tab shows: “You have a private key that corresponds to this certificate”. |
| File opens unencrypted when copied to USB drive. | EFS is NTFS, only. The file was copied to a non, compatible partition (FAT32/exFAT). | Only copy EFS files to another NTFS drive, or use a portable AEAD container (like 7, Zip) for cross, platform transfers. |
5.2. AEAD Tampering Detection
If you receive an error like GCM authentication tag verification failed or a GCMInvalidTagException, the AEAD scheme has successfully detected an integrity failure.
Action: Stop processing the data immediately. The error signals the ciphertext was tampered with, either due to malicious attack, bit corruption during transit, or a Nonce reuse failure. Do not attempt to retrieve partial or corrupt plaintext, as this leaks information to an adversary. The data must be resent from a trusted source.
VI. Encryption Standards Evolution Table
The following table summarizes the key evolution points and the eventual fate of each major symmetric cipher standard.
| Cipher Standard | Key Size (Effective) | Rounds | Primary Vulnerability | Status |
| DES | 56, bit | 16 | Brute, force (Broken by Deep Crack) | Obsolete (Withdrawn by NIST) |
| 3DES | 168, bit ($2^{112}$ effective) | 48 (3x DES) | Meet, in, the, Middle Attack | Legacy (Retired for new systems; PCI DSS retired 2024) |
| AES, 128 | 128, bit | 10 | Quantum attack ($2^{64}$ effective) | Legacy (Not recommended for long, term security) |
| AES, 256 | 256, bit | 14 | None known (128 bits quantum resistant) | Industry Standard (Required for TOP SECRET data) |
| AES, GCM / ChaCha20, Poly1305 | 256, bit | Variable | Nonce Reuse (Catastrophic failure) | AEAD Standard (Mandatory Integrity Check) |
VII. Frequently Asked Questions (FAQ)
1. Why is AES-128 no longer considered secure for future use?
AES, 128’s security margin drops to 64 bits under theoretical quantum attacks (Grover’s algorithm). This reduction means the cipher is no longer robust enough for protecting data against emerging high, power adversaries.
2. What is the fundamental difference between AES-CBC and AES-GCM?
AES, CBC only guarantees confidentiality (hiding the content). AES, GCM is an AEAD mode that guarantees both confidentiality and integrity (preventing undetected modification) via a cryptographic tag.
3. What happens if I reuse the Nonce (IV) with the same key in AES-GCM?
This results in a catastrophic cryptographic failure. Reusing the Nonce with the same key compromises the confidentiality and integrity of all messages encrypted with that key pair.
4. Why was 3DES retired if it had a 168-bit key?
Despite the long key, 3DES was mathematically vulnerable to the Meet, in, the, Middle attack, reducing its effective security to $2^{112}$. It was also prohibitively slow and resource, intensive compared to AES.
5. Which AES key length is required to protect classified U.S. TOP SECRET data?
The U.S. Government requires the use of either the 192, bit or 256, bit key length for protecting TOP SECRET classified information.
6. Is AES-256-GCM always faster than ChaCha20-Poly1305?
No. AES, GCM is fastest only on systems that support the dedicated AES, NI hardware instruction set. ChaCha20, Poly1305 is usually faster and more efficient on mobile devices (ARM) and older CPUs lacking that hardware support.
7. Why is the “Encrypt file names” option critical when using 7-Zip?
Checking this box encrypts the file’s metadata, hiding the folder structure and file names from anyone who accesses the archive without the password. Without it, an attacker can still determine what data you are hiding.
8. If my EFS file gives a 0x80071771 error, is the data lost?
The 0x80071771 error typically means the EFS private key is missing or inaccessible. If you have not backed up your PFX certificate file containing the key, the data is permanently lost.
9. Why do organizations block encrypted email attachments?
Cloud DLP (Data Loss Prevention) policies block encrypted files because the systems cannot scan the content for malware or compliance violations (like health records or credit card numbers), prioritizing compliance and integrity over user confidentiality.
10. What is a “Known-Plaintext Attack,” and which standard was highly vulnerable to it?
A Known, Plaintext Attack occurs when an attacker possesses both the ciphertext and the corresponding original plaintext, allowing them to rapidly deduce the key. The legacy ZIPCrypto standard is seriously flawed and highly vulnerable to this attack.
11. Is it safe to send the AES password in the body of the same email as the file?
No. This practice creates a single point of failure. If the email is intercepted, the attacker gains both the encrypted file and the decryption key simultaneously.
12. What specific hardware feature makes AES-GCM fast on desktop computers?
The AES, NI (Advanced Encryption Standard New Instructions) instruction set is built into modern Intel and AMD CPUs. This set accelerates AES operations, allowing AES, GCM to achieve extremely high throughput.
13. What is the AEAD security requirement known as “AAD”?
AAD stands for Associated Data. It is non, secret information (like a file header or protocol identifier) that is authenticated but not encrypted alongside the ciphertext, ensuring its integrity against tampering.
14. Why should I combine EFS with BitLocker on my laptop?
EFS keys are stored on the operating system drive. BitLocker encrypts the entire system drive, safeguarding those EFS keys against being accessed or copied by an attacker who steals the physical hard drive.
15. What is the fundamental difference between AES and Hashing?
AES is reversible (two, way) and provides confidentiality. Hashing is irreversible (one, way) and provides only integrity (verifying that the data has not been altered).
Conclusion
The history of encryption, from the failure of 56, bit DES to the retirement of 3DES, is a history of security margins being breached by advancing computational power. This evolution has led to a single modern mandate: AES, 256 implemented in an Authenticated Encryption (AEAD) mode.
AES, 256 is essential because it is the only established standard that provides an effective 128 bits of security under a future quantum computing threat, making it mandatory for all long, term and classified data. The AEAD mode (GCM or ChaCha20, Poly1305) is equally critical, as it eliminates the integrity gap of legacy ciphers, guaranteeing that any malicious tampering with the data during transit is instantly and unequivocally detected. Practical security relies on combining this mathematically sound choice with robust key management and correct configuration, such as checking “Encrypt file names” in portable archives, to create an end, to, end secure system.
