Encryption and Digital Trust: Verifiable Practices that Build Confidence
This essential overview, created by the security specialists at Newsoftwares.net, details the core principles of verifiable digital trust. Moving beyond simple marketing claims, it focuses on transparent security practices, open infrastructure, and rigorous cryptographic foundations necessary to protect user data and ensure privacy. By adopting independently audited tools and modern key management techniques, users can build genuine, structural confidence in their digital security and convenience.
Digital trust is not a soft concept based on marketing, it is the verifiable outcome of transparent security practices. The belief that online services, platforms, and devices will protect personal data and operate ethically is earned by companies that commit to standards, based infrastructure and clear disclosure of their security boundaries.
The only way to build digital confidence is through verifiable transparency. This requires companies and individuals to employ solutions built on open, independently audited code, publish explicit disclosures regarding legal compliance, and use robust cryptographic foundations like Public Key Infrastructure (PKI) and End, to, End Encryption (E2EE).
TL;DR Outcome: Three Verifiable Trust Pillars
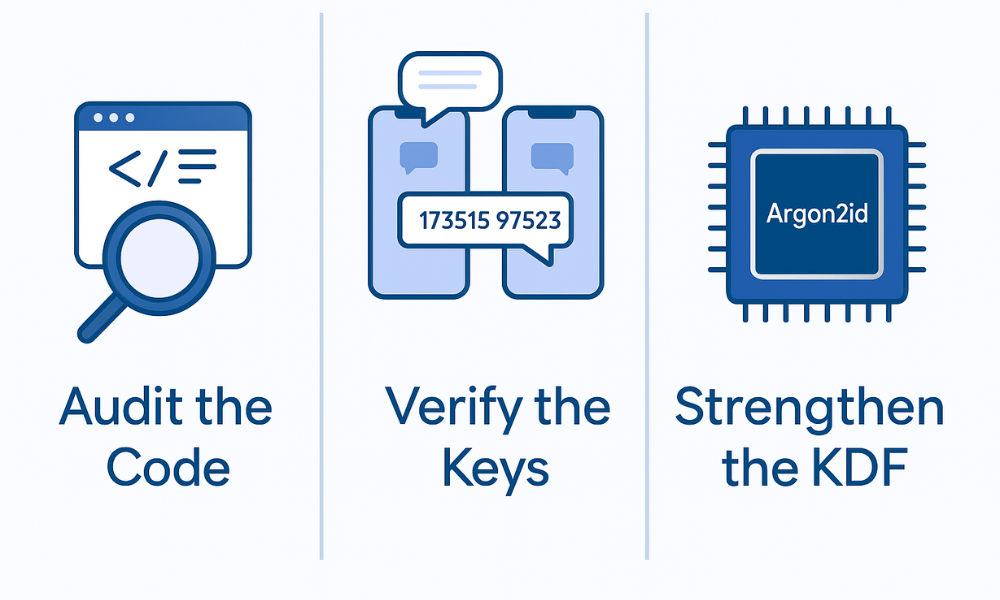
- Audit the Code: Never use encryption tools that have not undergone independent cryptographic security reviews or penetration tests to expose underlying design flaws.
- Verify the Keys: When utilizing End, to, End Encryption, always complete the manual key verification step (e.g., comparing safety numbers) to confirm the integrity of the key exchange.
- Strengthen the KDF: For securing master passwords, prioritize modern, memory, hard Key Derivation Functions (KDFs), specifically Argon2id, over older functions like PBKDF2 for superior resistance against brute, force attacks.
The Danger of Opacity: When “Encryption” Is Not E2EE
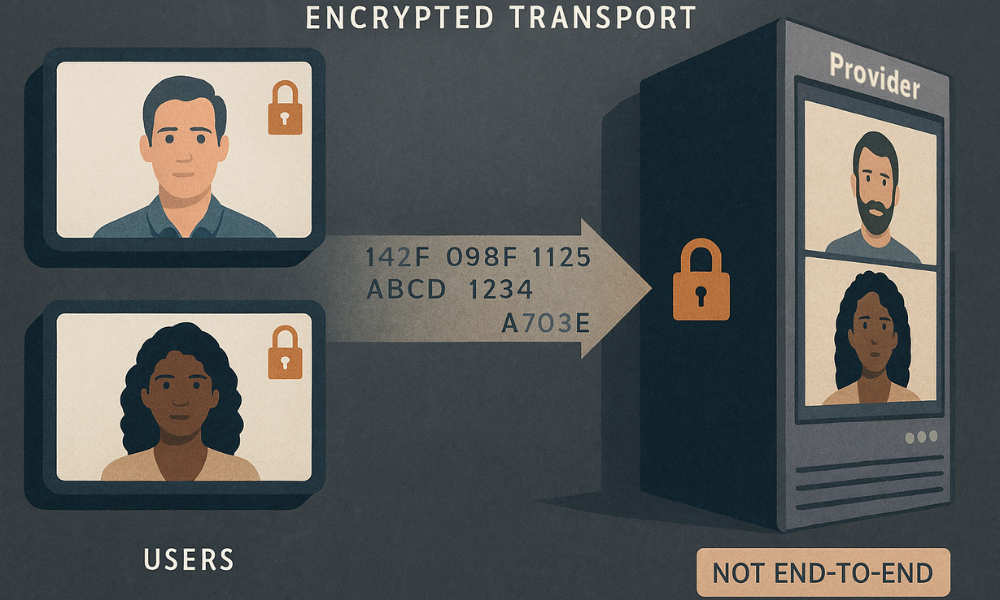
Technical complexity does not automatically equate to user trust. If a security boundary is described misleadingly, even if unintentional, it violates the user’s expectation of integrity. This relationship between semantics and security was severely tested during the Zoom controversy in 2020.
The company faced a major erosion of public confidence after admitting “a discrepancy” in its usage of the term “E2EE”. Although Zoom employed encryption during data transmission, the content remained accessible to Zoom itself. This access meant the service lacked true end, to, end encryption, the industry, accepted standard where only the communicating endpoints hold the keys. The incident proved that reliance on broad or imprecise terms for security features is inherently damaging to the relationship with the user base. For digital services, technical rigor must be paired with precise, clear language regarding security boundaries, confirming that semantic transparency is a fundamental prerequisite for building security systems that people can truly rely on.
Transparency Layer 1: Organizational Proof of Work
Organizational transparency involves providing objective evidence of security controls that external parties can validate. This validation is critical for separating genuine security commitments from internal security promises.
Open Source: Code as the Ultimate Transparency Report
Making software code freely accessible is the highest form of transparency because it invites constant scrutiny from a global community of developers and experts. This collaborative, open review process significantly enhances security, often identifying flaws faster than proprietary, closed, source development. For example, organizations actively contribute to the open, source community by maintaining critical cryptographic libraries for languages like JavaScript and Go.
Beyond the code, the structural commitment of the organization matters. The Signal Foundation, which develops the Signal E2EE messaging platform, operates as a non, profit. This structural choice functions as a structural safeguard, insulating the mission from investor pressure that often compels commercial tech companies to “sacrifice a little privacy” in pursuit of higher growth or profit margins. This organizational transparency builds a deep, structural confidence in the commitment to privacy.
Independent Cryptographic Audits: How Experts Find Flaws
Trust in a security tool can never rest solely on the developer’s assurance. Independent security audits, such as penetration tests conducted by Red Team labs, provide an objective and unbiased perspective on the implemented security controls and compliance posture. These external assessments, often resulting in SOC reports, are vital for demonstrating adherence to industry standards and legal requirements.
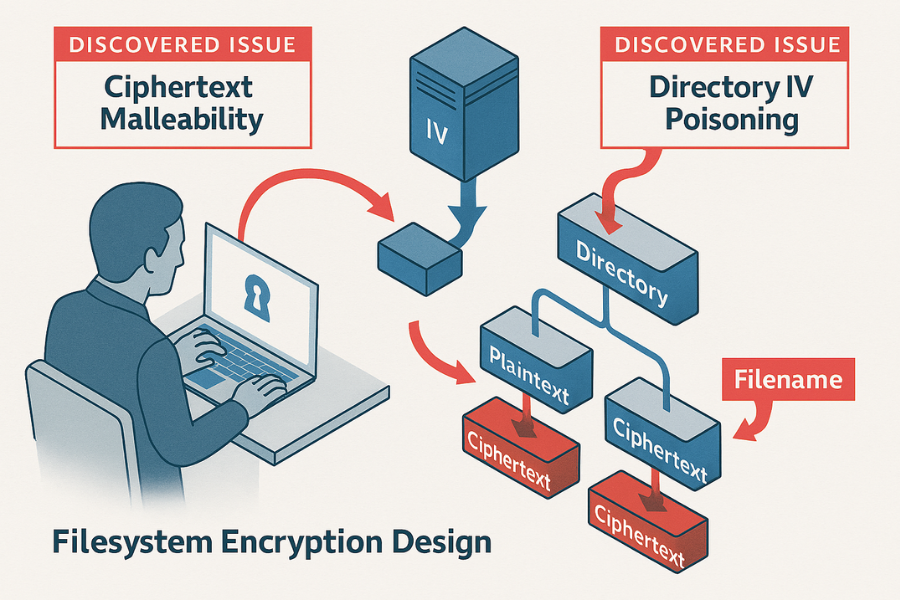
A detailed examination of past audit findings illustrates why external review is essential. The security audit of the gocryptfs filesystem (version 1.2), which uses high, quality ciphers like AES-GCM and AES-EME, revealed that implementation errors, rather than weak ciphers, can destroy the system’s integrity.
- Ciphertext Malleability: The audit discovered a complete break of file confidentiality because the integrity check was bound only to an internal “file ID” and not to the file path or name. This design flaw meant an attacker could simply copy the encrypted data (ciphertext) into a directory they controlled on the mounted filesystem and instantly decrypt the original plaintext content, proving that encryption is only as secure as its implementation logic.
- File ID and Directory IV Poisoning: The audit also found that an adversary could force two different files to share the same file ID, allowing for data chunks to be swapped between files undetected. Similarly, the Directory Initialization Vector (IV), used to encrypt filenames, was stored unauthenticated, allowing an attacker to swap IVs and potentially discover secret plaintext filenames.
These findings demonstrate that trust is established when developers permit external review, expose flaws, and fix them, proving that standard cryptographic algorithms can be rendered useless by non, cryptographic implementation errors regarding metadata handling or key usage.
Signaling Resistance: The Function and Necessity of Warrant Canaries
The warrant canary is an active signaling mechanism used by organizations to communicate their legal status transparently. It is a public statement asserting that the organization has not received certain government demands, specifically those carrying gag orders that prevent disclosure.
This practice signals confidence and resistance to the ongoing legal tensions between privacy advocates and authorities seeking access to encrypted data. Cloudflare, for example, maintains explicit warrant canaries stating they have never turned over encryption keys, installed law enforcement software on their network, or modified customer content at the request of a third party. If this public statement disappears or is modified, it serves as a transparent warning to users that the company has potentially received a secret, compelled request, thus adhering to privacy principles in a legally non, verbal manner.
Transparency Layer 2: Secure Data, at, Rest Mechanics
Genuine trust relies on the robust handling of the secret keys used for encryption, particularly the efficiency of the Key Derivation Function (KDF) and the comprehensive management of the key lifecycle.
Key Derivation Functions (KDFs): The Password Firewall
The KDF transforms a user’s weak, human, memorable password into a cryptographically strong key used to decrypt the secured data header. KDFs actively slow down brute, force attacks by introducing significant computational difficulty through the use of a large random salt and a tunable work factor, usually defined by computational iterations or required memory.
BitLocker currently uses the older PBKDF2 algorithm combined with HMAC-SHA-256. While PBKDF2 uses iterations to slow attacks, it is primarily constrained by CPU cycles. This limitation is increasingly problematic because modern attackers can deploy specialized hardware, such as ASICs or powerful GPUs, to brute, force PBKDF2 efficiently and cheaply.
This attack economy necessitates a shift toward memory, hard KDFs. VeraCrypt, for instance, recommends Argon2id for new volumes. Argon2id is specifically designed to require a substantial allocation of system memory (RAM) to execute rapidly. By introducing memory, hardness, the function makes large, scale, parallel brute, force attacks disproportionately costly by requiring significant dedicated memory resources, thereby defending against specialized hardware deployment and increasing the economic cost required for key compromise.
Encryption Key Management (EKM)
Key management encompasses the processes and mechanisms for the entire lifecycle of cryptographic keys, from generation and storage to exchange and replacement. A robust EKM strategy emphasizes the separation of the cryptographic keys from the data they protect.
Transparent Key Management (TKM) supports compliance with security standards, reinforcing trust with stakeholders by objectively demonstrating adherence to best practices.
It is essential to understand the limitations of high, level encryption deployments. Full, Disk Encryption (FDE), though simple to deploy and transparent to applications, only addresses a limited range of threats: physical loss or theft of the storage media. FDE is insufficient against internal risks, such as malicious insiders or advanced persistent threats (APTs), because once the volume is unlocked and mounted, the keys are accessible to the operating environment. For comprehensive protection against sophisticated internal threats, organizations must move up the software stack to deploy file, level, database, or application, layer encryption.
Practical How To: Full Volume Encryption (BitLocker)
BitLocker is the default Full, Volume Encryption (FVE) integrated into professional versions of Windows. The deployment relies heavily on correctly configured prerequisites, especially the Trusted Platform Module (TPM).
Prerequisites and Safety Checks
BitLocker enrollment requires specific checks to avoid failure:
- OS Requirement: Windows Pro, Enterprise, or Education edition must be used.
- TPM Requirement: The TPM chip must be present, enabled, and unlocked. The enrollment process will halt if the TPM state is incorrect.
- Recovery Environment: Windows Recovery Environment (Windows RE) must be active. This is checked using the
reagentc.execommand. - Partition Format: The system, reserved partition must be formatted as FAT32 on modern UEFI systems or NTFS on older, legacy computers.
Procedure: Enabling BitLocker on Windows 10/11
System protection begins with verifying hardware readiness.
Step 1: Verify TPM State (Prerequisite Check)
- Open an elevated PowerShell window (Run as Administrator).
- Run the command:
Get-Tpm - Gotcha: Ensure
TpmPresentandTpmReadyboth return True. If not ready, the user must access the system’s UEFI/BIOS settings to ensure the TPM is provisioned.
Step 2: Check Windows RE Status
- Open Command Prompt as Administrator.
- Run the command:
reagentc.exe /info - Ensure the status shows the environment is
Enabled.
Step 3: Initiate Encryption
- Navigate to the Control Panel > System and Security > BitLocker Drive Encryption.
- Select “Turn on BitLocker” for the system drive (C:).
- Choose the required key protection method (typically TPM only, or TPM + PIN).
Step 4: Saving the Recovery Key Safely
- The system requires saving the unique, 48, digit recovery password. This key is essential for recovery in case of system failure or TPM change.
- The key must be saved to a location separate from the drive being encrypted (e.g., printed, saved to an external USB, or uploaded to a cloud management platform).
Verification (Proof of Work Block)
Trust requires explicit verification of the encryption status using non, GUI diagnostic tools.
BitLocker Verification Checks
| Verification Check | Command Line | Expected Output Snippet |
|---|---|---|
| Confirm Protection Status | manage-bde -status C: |
“Protection Status: Protection On” |
| Confirm Cipher Details | manage-bde -status C: |
“Encryption Method: XTS-AES 256” (or XTS-AES 128) |
| Confirm Key Protector | manage-bde -protectors -get C: |
Displays the 48, digit Numerical Recovery Password. |
Practical How To: Cross, Platform Container Encryption (VeraCrypt)
VeraCrypt is an open, source, independently verified disk encryption tool offering high customization and crucial cross, platform support. It is ideal for creating encrypted file containers or securing non, system partitions.
Prerequisites and KDF Selection
VeraCrypt allows for powerful customization of key derivation. It is crucial to select Argon2id as the Key Derivation Function for new volumes. Argon2id is the memory, hard standard that provides the best modern protection against specialized brute, force hardware.
Procedure: Creating a VeraCrypt Encrypted Container (Windows)
Step 1: Start Volume Creation
- Launch VeraCrypt and click “Create Volume”.
- Select “Create an encrypted file container” (default option).
- Choose “Standard VeraCrypt volume”.
Step 2: Select Volume Location and Filename
- Click “Select File” and choose the storage location (e.g., an external drive).
- Specify a filename (e.g.,
SecureArchive.hc). The container file functions like any regular file and can be moved or copied.
Step 3: Choose Encryption Options and KDF
- In the Volume Creation Wizard, define the parameters.
- Encryption Algorithm: Use AES-256.
- Key Derivation Function (KDF): Select Argon2id. This modern algorithm uses BLAKE2b internally and is designed to resist ASIC attacks better than PBKDF2.
Step 4: Define Size and Password
- Enter the container size (e.g., 2 GB).
- Create a strong, unique password, optionally incorporating a keyfile for multi, factor security.
Step 5: Formatting and Finalizing
- Move the mouse randomly within the wizard window for at least 30 seconds to gather cryptographic entropy (randomness).
- Click “Format” to encrypt the volume header and initialize the container.
Procedure: Mounting and Accessing the Container
- Select Drive Letter: On the main VeraCrypt window, choose an unused drive letter (e.g.,
A:). - Select File: Click “Select File” and choose your container file.
- Mount: Click “Mount,” enter the password, and click “OK”.
- Verification Check: A new virtual drive letter should appear in the system’s file explorer, confirming successful mounting and decryption of the header key.
Proof of Work Bench: Cipher Performance and Hardware Impact
Usability is a security factor, as performance degradation leads users to bypass encryption. VeraCrypt leverages hardware, accelerated AES (AES-NI) on supporting Intel and AMD processors, achieving high speeds (e.g., 3.9 GB/s) that ensure negligible CPU impact.
However, the architecture dictates performance. On hardware lacking AES-NI (e.g., older or specialized chips like the Broadcom in the Raspberry Pi 4), software performance for AES-256 drops to 113 MB/s. In such cases, alternative ciphers like Twofish (194 MB/s) may offer superior throughput, demonstrating that cipher selection must be tailored to the specific hardware environment to maintain trust and prevent abandonment.
VeraCrypt Benchmark Comparison (Approximate Speeds)
| Cipher | i5 Processor (with AES-NI) | Raspberry Pi 4 (No AES-NI) |
|---|---|---|
| AES | 3.9 GB/s | 113 MB/s |
| Twofish | 887 MB/s | 194 MB/s |
| Camelia | 1.5 GB/s | 102 MB/s |
Practical How To: Verifying End, to, End Messaging Trust (Signal)
Signal is built on a powerful, layered cryptographic foundation, including X3DH for key establishment, the Double Ratchet algorithm for session security, and recent adoption of PQXDH for quantum resistance. However, the cryptographic strength of E2EE only holds if the user actively verifies the authenticity of the shared public keys.
Procedure: Verifying a Safety Number
The Safety Number is a 60, digit representation of the unique public keys shared between two contacts. Verification confirms that no unauthorized party has swapped the keys (a key compromise attempt).
Step 1: Access the Safety Number
- Open the chat with the contact.
- Tap the contact’s name at the top of the screen.
- Select “View Safety Number”.
Step 2: In, Person Verification (Preferred Method)
- If possible, meet the contact in person.
- Use the QR code scanner feature on your Safety Number screen to scan the QR code displayed on your contact’s device.
- Verification Check: The application confirms if the safety numbers match.
Step 3: Remote Verification
- If remote, the 60, digit sequence must be manually compared over an entirely separate, secure communication channel (e.g., a phone call or a verified email).
Step 4: Mark as Verified
- Once successfully compared, tap “Mark as verified” on your device.
If the safety number changes, the verified status is instantly cleared. This typically happens when a contact changes devices, but the user is mandated to re, verify the key over a reliable secondary channel before sensitive communication resumes, acknowledging that endpoint integrity requires user confirmation. The manual verification step is the only truly verifiable component of the E2EE trust chain, shifting responsibility from the company’s algorithm to the user’s conscious action.
Troubleshooting and Maintaining Encrypted Systems
Encryption systems often fail due to underlying system dependencies, not cryptographic errors. Efficient troubleshooting involves checking environmental prerequisites first.
BitLocker Troubleshooting: Common Errors and Immediate Fixes
BitLocker issues primarily relate to the state of the TPM, pre, boot environment, or partition configuration.
BitLocker Troubleshooting: Symptom > Fix
| Symptom / Error Message | Root Cause(s) and Check | Non, Destructive Fix |
|---|---|---|
| BitLocker fails to start/encrypt drive. | TPM is locked, disabled, or uninitialized. | Run Get-Tpm in PowerShell, if not ready, check UEFI/BIOS settings and clear the TPM ownership if necessary. |
| Device enters recovery loop on restart. (e.g., after firmware update). | UEFI/Secure Boot setting changes or TPM 1.2 issues with Virtualization, based Security. | Suspend BitLocker (Suspend-BitLocker -RebootCount 0), reboot, correct the UEFI settings (e.g., Secure Boot to ‘Microsoft Only’), then resume BitLocker. |
| Cannot encrypt, system partition is missing or wrong format. | System, reserved partition must be FAT32 on UEFI or NTFS on Legacy systems. | Use Disk Management to verify and correct partition formats (requires advanced skill). |
General Cryptographic Error Diagnostics
Failures in secure communication protocols, such as SSL/TLS handshakes, often stem from configuration errors like incompatible cipher suites, mismatched protocol versions, or expired digital certificates. Diagnosis relies on analyzing the explicit error strings produced by the cryptographic libraries. Error messages, such as those generated by OpenSSL, frequently point directly to the issue, for example, “Certificate verification failures” or “Incompatible SSL/TLS versions”. A frequent root cause is the incomplete configuration of the certificate chain, where necessary intermediate certificates are missing.
Encryption Comparisons and the Legal Context
Cipher Choice Deep Dive: AES-256 vs. XChaCha20
While AES-256 is the long, established block cipher standard, XChaCha20, a modern stream cipher introduced in 2014, offers implementation advantages. XChaCha20 encrypts data bit, by, bit and requires less reliance on hardware acceleration (AES-NI) than AES.
The simplicity of XChaCha20’s design results in a faster, easier software implementation, reducing the chance of human implementation error. This makes XChaCha20 a superior choice for environments lacking modern CPU acceleration, such as embedded or entry, level mobile devices, ensuring high performance and security across a wider range of hardware and improving the overall reliability of its deployment.
Legal Tension: The Right to Encrypt vs. Law Enforcement Access
The encryption debate centers on the tension between civil liberties and public safety. Governments often push for legislative mandates or court orders compelling tech providers to build “backdoors” into encryption to facilitate investigations, such as the widely documented FBI vs. Apple case. Companies largely resist this, citing the inherent risk of introducing systemic vulnerabilities that compromise mass user security.
Legal access varies significantly by jurisdiction. Some nations allow authorities, with judicial authorization, to compel third parties to provide decryption keys or passwords. For the user, this means that even cryptographically strong encryption is ultimately contingent upon the key holder’s ability to resist compelled disclosure in their legal jurisdiction. Organizational transparency tools, like warrant canaries, become essential for communicating the service provider’s legal resistance posture.
Verdict by Persona
- SMB Admin: Mandate BitLocker for corporate endpoints due to centralized key management capability (via Active Directory/Entra ID) and compliance requirements. XTS-AES 256, bit must be the standard cipher selection.
- Freelancer/Activist: Requires open, source tools with independently audited code (VeraCrypt, Cryptomator) utilizing memory, hard KDFs (Argon2id) for protection against targeted attacks. All communications must use a verified E2EE platform like Signal.
- Security Architect: Full, Disk Encryption is insufficient. Must mandate organization, wide use of memory, hard KDFs (Argon2id/Scrypt) and prioritize application, layer or file, level encryption to mitigate insider threats and APTs where FDE fails.
Essential Questions (FAQs)
1. What is a “memory, hard” KDF and why is it better than PBKDF2
A memory, hard Key Derivation Function (KDF), such as Argon2id, requires significant RAM allocation to generate the encryption key from a password. This necessity makes highly parallel brute, force attacks using specialized hardware (ASICs) economically unattractive and inefficient compared to attacks targeting older, CPU, intensive KDFs like PBKDF2.
2. Does using strong encryption slow down my computer significantly
In most cases, no. Modern processors (Intel/AMD) include AES-NI instructions, which hardware, accelerate AES encryption. When this acceleration is available, tools like BitLocker and VeraCrypt operate at speeds approaching native disk transfer rates, making the performance impact negligible.
3. What happens if my Signal safety number changes unexpectedly
A safety number change typically occurs when your contact reinstalls the application, changes their phone number, or links a new device. However, this event must be treated as a critical warning. You must immediately cease sensitive communication and re, verify the 60, digit number or QR code with your contact over a secondary, reliable channel.
4. Why are independent security audits more important than a company’s internal security team report
External audits provide objective, unbiased verification of a system’s cryptographic design and implementation. As demonstrated by audits like the one on gocryptfs, external experts often identify critical design flaws (e.g., ciphertext malleability) that internal developers might overlook, proving that independent scrutiny is vital for genuine trust.
5. If I use Full, Disk Encryption (FDE), is my data fully protected
FDE is excellent for preventing data theft if the device is lost or stolen. However, it provides minimal protection against insider threats or malware. Once the FDE volume is unlocked, the operating system can access the data, making it vulnerable to any malicious processes running on the host machine. For highly sensitive data, use application, layer encryption layered on top of FDE.
6. What is the biggest advantage of stream ciphers like XChaCha20 over block ciphers like AES-256
XChaCha20 is simpler to implement in software and is less dependent on hardware acceleration. This simplicity reduces the probability of human implementation error and ensures high speed and security across a wider range of hardware, including older or entry, level devices that lack AES-NI support.
7. Why must I verify the recovery key when enabling BitLocker
The 48, digit recovery key is the sole mechanism for accessing data if the TPM fails, the system configuration changes unexpectedly (e.g., BIOS update), or if the password is forgotten. Failure to save this key in a secure, separate location results in permanent data loss if the primary protection method fails.
8. What is a warrant canary and how does it help build trust
A warrant canary is a periodic public statement asserting that a company has not received certain government demands, particularly those that carry non, disclosure orders. If the canary disappears or changes, it implicitly warns the user that a secret legal demand may have been received, providing a transparent, non, verbal clue about the company’s legal status.
9. Why do companies rely on non, profit structures to signal trust
A non, profit structure, such as that used by the Signal Foundation, provides a structural safeguard against commercial pressure. By eliminating investor mandates for monetary targets and growth, the organization can maintain a singular focus on privacy and user security without the structural incentive to compromise those values.
10. What is the specific encryption method used by BitLocker
BitLocker defaults to the Advanced Encryption Standard (AES) in XTS (XEX, based Tweakable Block Cipher with Ciphertext Stealing) mode, typically utilizing a 128, bit or 256, bit key. XTS mode is applied sector, by, sector to the volume.
Conclusion
Digital trust is not a subjective metric, it is the measurable outcome of verifiable transparency. Confidence is earned through two simultaneous commitments: organizational structure and technical rigor. Structural commitments, such as open, source codebases and non, profit models, invite external scrutiny and safeguard missions against commercial compromise. Technical commitments involve migrating from legacy security primitives (like PBKDF2) to modern, memory, hard standards (Argon2id) to actively defeat specialized hardware attacks.
The analysis confirms that even high, quality encryption algorithms can be rendered useless by flawed implementation logic or metadata mismanagement, underscoring the necessity of independent cryptographic audits. Ultimately, while technology facilitates trust, the final and most powerful component in the cryptographic trust chain is the user’s conscious action, completing manual verification steps and understanding that security is a mandate requiring constant diligence in both policy and practice.
