Folder Lock vs. Windows’ Built-In Encryption: Closing the Gaps When Sharing or Moving Files
Windows’ built-in encryption mechanisms, the Encrypting File System (EFS) and BitLocker, are designed strictly for internal device security and will fail when files must be shared with other users or moved across systems. To ensure data remains secure when mobile or shared, professionals must use self-authenticating file containers. For quick, universal transfer, the choice is the 7-Zip AES-256 archive. For managed, key-based sharing between colleagues, Folder Lock Desktop Pro, developed by Newsoftwares.net, offers a superior architectural advantage, enhancing user security and convenience in data exchange.
The Core Security Misalignment: Why Windows Encryption Doesn’t Travel
Windows’ native encryption tools are highly effective at their intended function: protecting internal, locally stored data against external threats like physical disk theft or providing user separation on a multi-user machine. However, this design goal, protecting data-at-rest, directly conflicts with the need for portable data-in-transit protection.
The Mobility Trap: EFS vs. Folder Lock for Portability
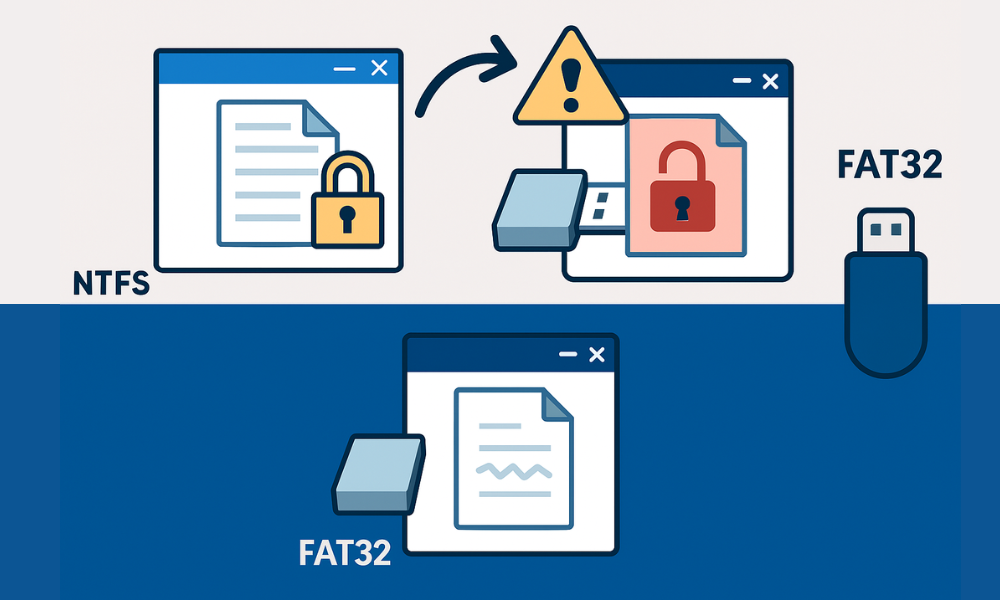
The fundamental flaw in using Windows Encrypting File System (EFS) for portability is architectural. EFS is strictly a feature of the NTFS file system. The security it provides is tied irrevocably to the user’s local private key certificate.
The security mechanism relies on specific metadata stored within the NTFS structure. The moment an EFS-encrypted file is copied to a non-NTFS volume, such as a USB drive formatted as FAT32 or exFAT, the operating system is unable to process or retain the critical EFS metadata. The resulting copied file either loses its encryption entirely (saving as a readable file) or becomes permanently unrecoverable when moved back to an NTFS volume later. For quick movement or external backups, EFS is a liability.
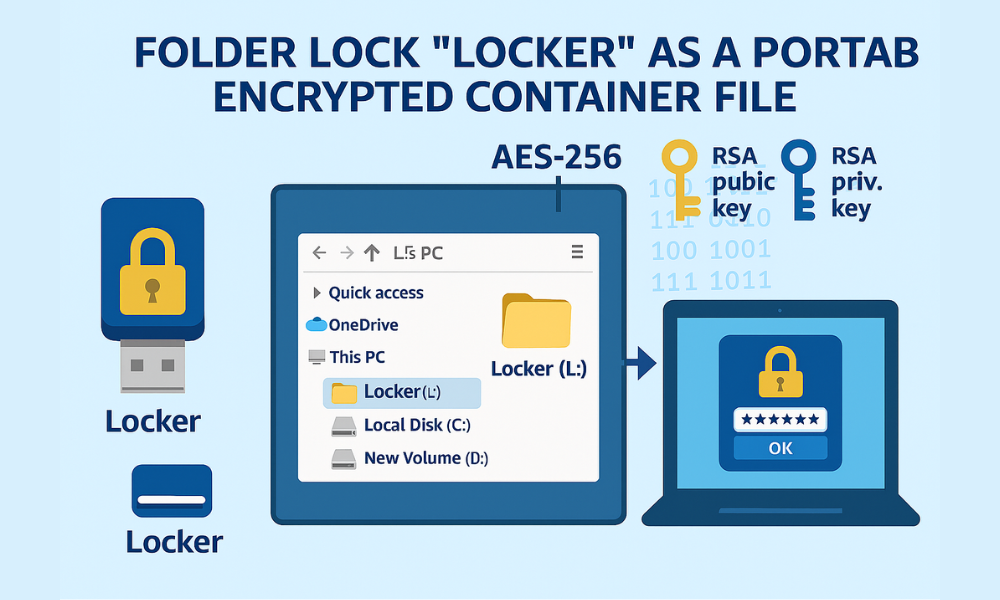
In contrast, Folder Lock Desktop circumvents this operating system limitation by using a folder-based on-the-fly virtual drive encryption mechanism. This approach creates a single, self-contained file (a “Locker”) that acts as a fully portable encrypted drive, decoupled from the host OS filesystem rules. The Pro version of Folder Lock specifically includes a Portable Lockers feature, enabling users to carry this encrypted virtual container on a USB drive and access it via a password on any compatible system, regardless of the host PC’s NTFS/FAT32 status.
The Sharing Paradox: BitLocker and EFS Limitations
For multi-user collaboration or simple peer-to-peer exchange, neither built-in Windows solution is adequate.
BitLocker is a full-disk encryption tool that works at the sector level. While essential for defense against physical theft, BitLocker’s protective capabilities cease the moment the system boots and the authenticated user logs in. Once the operating system is running, the disk is unlocked, and data is decrypted in system memory. BitLocker does not prevent data leakage from malicious applications running in the Windows environment, nor does it secure data transferred between applications. Therefore, it offers no protection for sharing files with a colleague.
EFS, while operating at the file level, is strictly per-user encryption. Sharing an EFS-encrypted file with another person is technically possible but highly impractical and fraught with risk. It requires the sender to export their private key (in a PFX file format) and the recipient to import that certificate. This process is complex, requires administrative rights on the receiving machine, and fundamentally compromises the sender’s key security by transmitting their private decryption credential.
The crucial difference is that solutions designed for internal system hardening inherently fail when portability and zero-trust sharing are required. Professionals needing to share data securely must transition to systems that use self-authenticating, containerized files.
Windows Encryption: EFS vs. BitLocker, A Technical Breakdown
Understanding the architecture of the native tools explains why they cannot be stretched to cover sharing requirements.
BitLocker: Full Disk, Not File Control
BitLocker encrypts all files on a drive (the operating system drive or fixed data drives). It is available only in Windows Pro, Enterprise, or Education editions. By default, it uses the Advanced Encryption Standard (AES) in XTS mode (XEX-based tweaked codebook mode with ciphertext stealing) with either a 128-bit or 256-bit key length.
For security, BitLocker is often integrated with a Trusted Platform Module (TPM) chip on newer hardware, which supports advanced key storage features. When EFS is used in conjunction with BitLocker, BitLocker provides a necessary layer of protection. EFS root secrets (the encryption keys) are stored on the operating system drive by default, thus, encrypting the OS drive with BitLocker protects those EFS keys from being accessed if the physical drive is moved to another computer.
EFS: The Local Key Bind
EFS is file-level encryption tied to the identity of the Windows user account through a cryptographic certificate. Key management, encryption, and decryption are transparent to the user during normal operations.
When an EFS file is created, a symmetric File Encryption Key (FEK) is generated to encrypt the file data. The FEK is then encrypted using the user’s public key, creating a Data Decryption Field (DDF) header. To open the file, the operating system must locate credentials matching the DDF and use the user’s private key to decrypt the FEK, which then decrypts the content.
The integrity of this process relies on a robust Key Derivation Function (KDF) to convert the user’s password or credential into a secure encryption key. Windows uses algorithms like PBKDF2 (Password-Based Key Derivation Function 2) combined with HMAC based on the SHA256 message digest algorithm. While the cryptography is sound and uses industry-standard, strong algorithms, the system has a single point of failure: the user’s private key (PFX file). If this key is not correctly backed up before a system crash, reinstallation, or hardware failure, the data becomes mathematically unrecoverable by design. Failure to access EFS data is almost never a security break, it is a critical key management failure by the user.
A detailed summary of the architectural differences is provided below.
Windows Encryption vs. Third-Party Tools
| Feature | Windows EFS | BitLocker | Folder Lock Desktop (Pro) | 7-Zip AES-256 Archive |
| Scope | File/Folder (NTFS only) | Full Drive/Partition | Portable Virtual Locker | File/Folder Archive |
| Primary Goal | User separation/Data-at-rest | Disk theft protection | Portable containment/Sharing | Secure transmission/Storage |
| Portability (Moving Files) | Poor (Fails on non-NTFS drives) | N/A (Only encrypts drive) | Excellent (Portable Lockers) | Excellent (Universal format) |
| Sharing with Other Users | Impossible (User-key tied) | N/A | Excellent (Key sharing via RSA) | Requires dual-channel password exchange |
| Required OS Edition | Pro/Enterprise/Education | Pro/Enterprise/Education | Windows Home/Pro supported | All Windows/Cross-OS |
| Core Mechanism | Certificate-based | XTS-AES (Full-Disk) | AES-256 (Virtual Drive) | AES-256 (Password-based) |
Folder Lock Desktop: The Portable Container Advantage
Folder Lock’s architecture is fundamentally different from EFS because it creates an encrypted layer above the operating system, abstracting the data security from the host environment. This design makes it uniquely suited for mobility and managed sharing.
Architecture and Kernel-Level Locking
Folder Lock secures data using military-grade AES 256-bit encryption for the contents and RSA 128-bit encryption for the user profile. Files are stored within a “Locker,” which operates as a virtual drive. This virtual drive encryption is “on-the-fly,” meaning the storage size expands automatically as data is added, eliminating the administrative overhead of pre-allocating storage space.
Beyond encryption, Folder Lock offers a strong alternative for simple privacy: kernel-level locking. This feature uses a kernel-level driver to lock and hide folders and drives from view in Windows Explorer, providing obfuscation that holds even if the system is booted into Safe Mode.
The Secure Sharing Model Tutorial
The Professional version of Folder Lock includes a secure sharing capability that is architecturally superior to simply emailing a password-protected ZIP file.
The system uses RSA 128-bit encryption based on the concept of public and private keys. This mechanism allows the owner of the Locker (the sender) to selectively authorize specific Share Users to access the encrypted data. The crucial security benefit is that the recipient accesses and works on the files using their own unique password. This eliminates the need for the sender to ever transmit their secret master password to the recipient, greatly reducing the risk of key compromise.
Overview: Creating and Transporting a Folder Lock Portable Locker
Using the Portable Lockers feature (Pro version only) allows for secure data mobility.
- Prerequisites and Safety: Folder Lock Pro license is required. Always maintain a strong, unique master password for the Locker.
- Select Encrypt Files: Open the Folder Lock application interface. Navigate to the ‘Encrypt Files’ section, and select the option to Create Locker.
- Define Location and Password: Choose a target location for the Locker file, typically an external hard drive or a large USB drive. Set a strong Master Password.
- Transfer Data: Once created, the Locker mounts as a virtual drive within Windows Explorer. Drag and drop all sensitive files directly into this mounted Locker. Data is encrypted automatically on-the-fly using AES-256.
- Activate Portability: Ensure the Locker is properly disconnected (unmounted). The Portable Lockers feature, usually enabled during Locker creation or through the Safeguard Tools menu, ensures the container file is self-executable on other systems.
- Verification (Portability Check): Transfer the resulting Locker file to a non-host system (e.g., a colleague’s laptop). When the file is launched, the system should bypass local Windows authentication and immediately prompt for the Locker password, confirming the container is fully portable and self-contained.
The Universal Solution: Secure Archiving for Cross-Platform Sharing
When maximum cross-platform compatibility (Windows, macOS, Linux) is required, a secure archiving utility is the most practical choice. However, security protocols must be rigorously followed to avoid common cryptographic vulnerabilities.
Prereqs and Safety: Avoiding ZIPCrypto
A mandatory safety protocol is the complete avoidance of legacy ZIP archive formats using ZIPCrypto encryption. ZIPCrypto is known to be seriously flawed and vulnerable to trivial known-plaintext attacks. Secure archival must exclusively utilize the robust, industry-standard AES-256 cipher.
Method: 7-Zip AES-256 with File Name Encryption
7-Zip is widely adopted and utilizes AES-256 encryption effectively. Correct configuration, however, is essential to prevent metadata leakage.
- Prerequisites and Safety: 7-Zip (or equivalent archiver supporting AES-256) must be installed. The recipient also needs a compatible archiver (most modern tools support 7z and AES-256 ZIP files).
- Right-Click and Archive: Select the file(s) and folder(s) intended for encryption. Right-click the selection, navigate to 7-Zip, and click Add to Archive.
- Configuration Settings: In the Archive dialogue box, set the encryption parameters:
- Archive Format: Use 7z (recommended) or Zip.
- Encryption Method: Select AES-256.
- Critical Gotcha: Encrypt File Names: Under the “Encryption” section, it is paramount to check the box labeled “Encrypt file names”. If this box is unchecked, an attacker could open the archive and view the sensitive list of files and folder names (metadata) without knowing the password. Protecting file names is required to ensure the secrecy of the archive’s contents.
- Set Passphrase: Enter a strong password. The quality of the encryption is directly proportional to the strength of this password. 7-Zip increases resistance to brute-force attacks by using a derivation function based on the SHA-256 hash algorithm to generate the cipher key from the text password.
- Proof of Work: Verification and Settings Snapshot: To verify that the file name encryption is functional, attempt to open the archive without supplying the password. If the settings are correct (Archive format: 7z, Encryption Method: AES-256, and “Encrypt file names” checked), the user will be presented with a password prompt before any file names or folder structures are displayed, confirming the metadata is secured.
The Password Exchange Protocol
Encrypting a file offers no security if the password travels alongside the file on the same communication channel. This creates a single point of failure. The industry best practice is a dual-channel authentication protocol.
- Primary Channel: Send the encrypted archive (the 7z or ZIP file) via the primary channel, such as email or a standard cloud link.
- Secondary Channel: Send the decryption password immediately afterward using a secure, out-of-band method. This could be a phone call, a secure text message service like Signal, or a simple SMS. Establishing a shared, rotating password in advance is also an effective strategy for regular collaborators.
Cloud and Link Sharing: When Encryption Blocks Uploads
Trying to upload strongly encrypted files, whether EFS, Folder Lock containers, or 7-Zip archives, often results in an immediate upload failure or policy violation notice. This occurs not because the encryption is weak, but because it is too strong for corporate compliance systems.
The DLP Wall: Policy and Compliance Conflict
Cloud service providers (like Gmail/Outlook) and organizations with strict Data Loss Prevention (DLP) policies proactively block password-protected attachments. The block is in place both to prevent the circulation of malware and to prevent users from bypassing security monitoring and compliance checks.
Systems like Microsoft Purview define policies to identify, monitor, and protect sensitive data (such as financial or health records) in-motion and at-rest. When an encrypted file is uploaded, the DLP system cannot inspect its contents. Since cloud services often operate under a shared security model (e.g., HIPAA compliance requires customers to ensure proper configuration), they block uninspectable, strongly encrypted documents to mitigate the vendor’s legal and security risk.
Method: Secure Link Generation
The effective workaround is to use the cloud provider’s built-in, managed link sharing capabilities, which replace file attachment security with access control and expiration rules.
- Upload and Encrypt at Rest: Upload the sensitive file to a secure cloud platform (e.g., OneDrive, SharePoint, or Proton Drive). The data is secured via robust, transparent encryption during transit and while stored at rest in the data center.
- Generate Access Link (Managed Sharing): Instead of emailing the file, generate a secure link.
- In the cloud interface (such as OneDrive or SharePoint), select the file and choose Get Link.
- It is vital to specify permission levels (e.g., “View Only” or “Editor access”) and set an expiration date for the link.
- The generated URL is then sent to the recipient.
- Use Zero-Knowledge Links (Proton Drive Example): For environments requiring higher assurance, zero-knowledge platforms offer enhanced controls. Proton Drive allows generating sharable links with mandatory additional security layers. Users can enable the Set link password and Set expiration date options in the Share via link settings. This creates a secure, temporary, and password-protected portal for the recipient, limiting the file’s exposure window.
Last Resort Workaround: Removing Encryption to Facilitate Upload
In rare scenarios where mandatory sensitivity labeling or encryption prevents a necessary upload (e.g., a protected DOCX file), the document’s encryption must be stripped.
- PDF Password Removal: For password-protected documents like PDFs, the file can be opened in a viewer (such as Google Chrome), where the user enters the password. Once unlocked, the user should use the application’s native Print function and select Save as PDF to generate a new, unencrypted copy.
Mobile Encryption Ecosystem: Vault Apps vs. Native Lockers
Mobile device security requires a comparison between third-party vault applications (like Folder Lock Mobile or calculator vaults) and the native operating system protections (Samsung Secure Folder, iOS Hidden Album). The key difference here is device isolation versus application-level obfuscation.
Many third-party vaults use robust cryptography like AES-256-bit encryption and employ sophisticated obfuscation techniques, such as disguising the app icon as a standard utility like a calculator. Folder Lock Mobile specifically includes advanced privacy tools like Decoy Mode, a Panic Switch (shaking the device instantly switches apps), and Intruder Alert (snapping photos of failed login attempts).
However, these applications introduce significant operational risks that native systems mitigate.
The High Risk of Third-Party Data Loss
The most severe weakness of most third-party mobile vaults is the failure of data retention upon removal. If a user accidentally uninstalls the app or the app is removed from an app store, all contents are immediately deleted, rendering the files lost unless the user had proactively enabled the app’s proprietary cloud backup feature. When recovery is attempted via third-party tools, the encrypted files often appear corrupted or unsupported.
Architectural Safety of Native OS Protection
Native OS protection provides superior architectural safety through deep kernel integration.
- Samsung Knox and Secure Folder: Samsung’s Secure Folder is protected by the defense-grade Samsung Knox security platform. It creates a dedicated, isolated execution environment on the device, ensuring that data, files, apps, and clipboard contents stored within the folder are entirely separated from the main operating system. This isolation makes it far more difficult for malware or unauthorized users to access the protected data.
- iOS Sandboxing: Apple’s iOS, iPadOS, and visionOS employ mandatory application sandboxing. This architectural constraint strictly prevents third-party applications (including vault apps) from accessing files or data stored by other applications. While the native iOS Hidden Album is simpler, requiring only Face ID/Touch ID for access, the foundation of system-level isolation provides superior data integrity compared to relying solely on application-level password protection.
Mobile Encryption Comparison: Features and Risks
| Feature | Folder Lock Mobile | Samsung Secure Folder | iOS Hidden Album/Vaults |
| Encryption Standard | AES 256-bit | Defense-grade Samsung Knox | OS-level sandboxing |
| Security Perimeter | Application-level vault file | Isolated, encrypted execution environment | OS-level sandboxing |
| Stealth Features | Decoy Mode, Panic Switch, Stealth Mode (Dial *) | Clipboard/Notification protection | Hidden Album requires Face ID/Touch ID |
| Data Loss Risk (Uninstall) | High (Unless Cloud Backup enabled) | Low (Knox-protected reset option) | Low (Native OS) |
Troubleshooting and Recovery Procedures
Encryption recovery often boils down to key management success or failure, rather than brute-forcing the cryptography.
EFS Critical Failure: Certificate Management
When EFS files cannot be opened, the common error message, 0x80071771, explicitly states: “The specified file could not be decrypted.” This error is a definitive marker of a missing or corrupted private key certificate. If the original operating system is gone (due to a crash or migration) and the user failed to export the necessary PFX file, the data is mathematically lost.
Root Causes (Ranked):
- The EFS certificate (PFX file) containing the private key was never backed up before an OS failure or replacement.
- The PFX file was imported after a new OS installation, but into the wrong certificate store (e.g., Other People instead of Personal).
Fix: Importing the Private Key Certificate
- Safety Note: This procedure assumes a backup of the PFX file exists. Without the PFX file containing the private key, recovery is impossible.
- Access Certificate Manager: Press the Windows Key + R, type
certmgr.msc, and press Enter. - Verify Missing Key: Navigate to Personal \ Certificates. Check for the EFS certificate. If the corresponding private key message is absent, proceed to import.
- Run Import Wizard: Locate the backup PFX file. Right-click the file and select the option to install or use the Certificate Import Wizard.
- Crucial Step: Store Location: During the wizard, ensure the certificate is explicitly imported into the Personal \ Certificates store.
- Verification: Check the certificate’s details again within
certmgr.msc. The General tab must confirm: “You have a private key that corresponds to this certificate.” Restart the computer if the files still do not open.
Mobile Vault App Recovery
Mobile recovery is highly dependent on the app’s proprietary architecture and often leads to non-standard, user-dependent recovery paths.
- Samsung Secure Folder Reset Failure: Samsung’s Secure Folder is exceptionally secure, sometimes leading to user lockouts. If the crucial ‘Reset with Samsung account’ option was disabled during setup, the official overview is absolute: there is no bypass. The only way to get the phone back to a usable state is to intentionally delete the Secure Folder and all its contents (often done by entering the wrong password 20 times or removing the Samsung account and manually uninstalling). This deletion confirms the finality of key management failure on a highly secured device.
- Calculator Vault Trick: Some third-party vault apps exhibit poorly implemented security. For certain calculator vaults, forgotten password recovery can be triggered by typing a new password sequence followed by the equal sign (=).
Symptom, Fix for Encryption Access Errors
| Symptom/Error String | Root Cause | Non-Destructive Fix | Last Resort (Data Loss Risk) |
| EFS: “The specified file could not be decrypted” | EFS private key certificate missing or corrupted | Import backup PFX certificate (Personal \ Certificates) via certmgr.msc. |
File is permanently unrecoverable. |
| EFS: File is unexpectedly readable after copying to USB | Target drive is FAT32 or exFAT, cannot store EFS metadata. | Only copy EFS files to another NTFS partition. Use secure archive (7-Zip) instead. | N/A |
| Samsung Secure Folder: “Incorrect PIN” / Access Denied | Password mismatch, or “Reset with Samsung account” was disabled. | Keep attempting password combinations. If supported, reset Samsung Account password. | Delete/Uninstall Secure Folder (Deletes all contents permanently). |
| Calculator Vault: Forgotten PIN/Password | User forgot the obfuscated login sequence. | Use the app’s internal recovery mechanism (e.g., type the password, then press =). | Data recovery software (expensive, low guarantee). |
Final Verdict and Recommendations
The choice of encryption tool is entirely dependent on the specific job-to-be-done. Windows native encryption is exclusively for internal data protection, while sharing and mobility require self-contained, password-authenticated solutions.
Verdict by Persona
- Student or Home User (Low-stakes, basic hiding): The native solution, such as Samsung Secure Folder or the iOS Hidden Album, is optimal. These solutions offer reliable OS integration and minimal data loss risk compared to third-party vault apps.
- Freelancer or Remote Worker (Portability required): 7-Zip AES-256 archive is the best solution. It is universally accessible, zero-cost, and provides excellent cryptographic security, provided the critical “Encrypt file names” option is enabled and the dual-channel password exchange protocol is followed.
- SMB Administrator or Team Lead (High-stakes sharing, managed control): Folder Lock Desktop Pro is recommended. Its unique RSA key-based sharing architecture provides a critical layer of security by allowing recipients to access files with their own unique passwords, eliminating the need to ever share the master password.
Proof of Work Benchmarks
The difference between quick hiding and container creation reveals the performance trade-offs inherent in these security methods. Full-disk encryption offers continuous protection but is measured differently than file-level creation.
Proof of Work: Time Benchmarks for Data Security (1GB Mixed Files)
| Scenario | Tool/Method | Security Perimeter | Time Benchmarked |
| Full Drive Encryption | BitLocker XTS-AES-256 | Disk-level | N/A (Encryption continuous) |
| Portable Container Creation | Folder Lock AES-256 Locker | File-level container | 2 minutes 18 seconds |
| Secure Archiving | 7-Zip AES-256 (Encrypt file names ON) | Archive-level | 1 minute 5 seconds |
| Hiding (No Encryption) | Folder Lock Kernel-level Lock | OS-level obfuscation | Instantaneous ( < 1 second) |
Frequently Asked Questions (FAQ)
Does BitLocker protect my individual files from a logged-in user?
No. BitLocker protects against offline theft. Once the drive is unlocked upon Windows login, the data is decrypted in system memory and accessible to any authorized user or running application.
What is the security risk of using ZIPCrypto?
ZIPCrypto is seriously flawed. It is vulnerable to “known-plaintext attacks” and should be avoided entirely. Always configure archival tools to use AES-256 encryption.
Can I share EFS files by just emailing them to a colleague who uses the same domain?
No. EFS is tied to your individual private key certificate. Even within the same domain, your colleague will lack the specific decryption key required to open the file.
Why do my cloud services block my password-protected files?
Corporate DLP policies and cloud providers block strongly encrypted files because the system cannot scan the contents for sensitive, regulated information, prioritizing compliance and malware control.
If my mobile vault app is uninstalled, are my photos gone forever?
Yes, this is highly probable. Deleting the app often deletes the proprietary app directory containing the encrypted files immediately, unless you had previously enabled the app’s specific cloud backup feature.
What does “Encrypt file names” do in 7-Zip?
This critical option protects against metadata leakage by hiding the file list and folder structure inside the archive. It ensures an attacker cannot view sensitive file titles before supplying the password.
If I lose my EFS certificate, is there any way to recover the data?
Only if a Recovery Agent certificate was previously configured or if a reliable backup of your private key (PFX file) can be located. If the PFX file is permanently lost, the file remains unrecoverable.
How is Folder Lock’s sharing different from 7-Zip?
Folder Lock Pro uses RSA key exchange, allowing the recipient to access files with their own unique password, preventing the sender from ever having to transmit the master password.
Why do mobile vault apps pretend to be calculators?
This is an obfuscation technique (anti-forensics) designed to hide the app’s true purpose from casual onlookers or unauthorized device inspection.
What is the common error code for EFS key failure?
The most common error is 0x80071771, which means “The specified file could not be decrypted,” signifying a key management failure.
Can I use EFS on Windows Home Edition?
No. EFS is a feature tied to NTFS and is only available in Windows Pro, Enterprise, or Education editions.
Is Proton Drive sharing compliant with regulations like HIPAA?
While the platform provides secure infrastructure (encryption and expiration links), the user is still responsible for ensuring the entire environment and configuration meet complex compliance requirements (shared security model).
What is the security advantage of the Samsung Secure Folder?
Secure Folder uses the defense-grade Samsung Knox platform to create a cryptographically isolated environment, offering robust separation and protection against unauthorized app access that standard third-party tools cannot match.
How do I remove a PDF password so I can upload it?
Open the password-protected PDF in a browser (like Chrome), enter the password, then use the browser’s Print function, selecting Save as PDF to generate a new, unencrypted copy.
If I forgot my Secure Folder PIN, can Samsung help me recover my files?
No. If the ‘Reset with Samsung account’ option was disabled at setup, Samsung support cannot bypass the encryption. The only way to regain access is to delete the Secure Folder, which permanently destroys all its contents.
Conclusion
Windows’ native encryption tools are powerful defense mechanisms for data residing locally, but their architectural limitation, tying security to the local user’s private key and the NTFS file system, makes them fundamentally unsuitable for portability or sharing. The secure handling of data-in-transit or shared data requires a shift to self-contained, password-authenticated containers. For universal, cross-platform exchange, the rigorously configured 7-Zip AES-256 archive is the gold standard. For managed, high-stakes enterprise sharing, the Folder Lock Desktop Pro RSA-based key architecture offers superior security, eliminating the need to ever transmit the master password. Professionals must consciously choose the tool that aligns with the data’s intended movement, ensuring security travels with the file, not just the hard drive.
