The Browser Lock Icon Explained
![]()
Answer first: the lock means your connection to that site is encrypted and the certificate matches the domain. It does not prove the site is honest, safe, or who you think it is. You still need to check the certificate, the address bar, and the content.
Gap Statement
Most posts stop at “lock means encryption.” They skip real checks for domain names, issuer trust, expiry, and mixed content. Many still hype EV badges that modern browsers no longer elevate. This overview fixes that with step by step checks in Chrome, Edge, Safari, and Firefox, real error strings to recognize, and a plain playbook you can run in under two minutes.
TLDR Outcomes
- You will know exactly what the lock confirms and what it does not.
- You will run a quick three point certificate check on any site.
- You will fix the most common TLS errors without losing data.
Core Ideas Without Jargon
| Concept | What it means | What you do with it |
|---|---|---|
| TLS or SSL | The protocol that encrypts the connection between your browser and the site | Expect privacy from local snoops and most network observers |
| Certificate | A digitally signed ID card for the site | Confirm the domain, issuer, and validity dates |
| CA (certificate authority) | A company that signs certificates that browsers trust | If the issuer is unknown, your browser shows a warning for a reason |
| DV, OV, EV | Levels of identity vetting behind a certificate | Your browser treats them the same in the lock icon; focus on domain and content |
| HSTS | A rule telling browsers to always use HTTPS for a domain | Stops downgrade tricks and reduces warning fatigue |
| Mixed content | A secure page that loads insecure parts | Can break the lock and leak data requests |
| Phishing on HTTPS | A fake site with a valid certificate | The lock still appears; the address bar is your first defense |
Quick Chooser: What to Check by Situation
| Situation | Do this first | Why |
|---|---|---|
| New store checkout | Click the lock, confirm the domain and validity dates | Stops lookalike domains and expired certificates |
| Login page from a link | Type the site address yourself or use a saved bookmark | Bypasses phishing pages with valid TLS |
| Hotel or public Wi Fi | Check the lock and the issuer name on first load | Catches captive portals and fake login pages |
| Corporate portal | Confirm the issuer matches your company or a known CA | Stops rogue proxies and bad roots |
| Browser shows a red full page warning | Stop and read the exact error string | Many are unrecoverable without risk |
What the Lock Guarantees and What It Does Not
| The lock does mean | The lock does not mean |
|---|---|
| Data in transit is encrypted | The site is trustworthy or well reviewed |
| The certificate matches the domain you see | The content is safe to download |
| The issuer is in the browser’s trust store | That third party scripts are private or honest |
| The connection negotiated modern ciphers | Your device or network is free of malware |
How to Check a Site in Three Moves (Any Browser)
- Read the address bar letter by letter. Example: pay.example.com is not payexamp1e.com.
- Click the lock and open the certificate panel. Note the domain, issuer, and validity dates.
- Load a second page on the same site and repeat. Consistent results confirm you are not bouncing through a captive portal or a redirect trap.
Time needed: about 30 seconds.
Hands On: View and Verify Certificates Per Browser
Google Chrome (Desktop)
- Click the lock icon in the address bar. Choose “Connection is secure” then “Certificate is valid.”
- In “Details,” confirm the “Subject” shows the exact domain or a wildcard that fits.
- Check “Valid from” and “Valid to” dates.
- In “Certification path,” the top should be a known root (for example ISRG Root X1 for Let’s Encrypt).
Gotcha
If you see “Not secure,” you are on HTTP or the certificate is broken. Do not enter passwords.
Microsoft Edge (Desktop)
- Click the lock. Select “Connection is secure” then “Certificate (valid).”
- Confirm Subject, Issuer, and dates.
- Open the “Certification path” tab to view the chain.
Gotcha
Edge sometimes caches HSTS. If a site just renewed a certificate and you still see an error, close all tabs for that site and try again.
Mozilla Firefox (Desktop)
- Click the lock. Select the arrow for “Connection secure.”
- Click “More information,” then “View Certificate.”
- Confirm “Common Name” or “Subject Alternative Names,” issuer, and dates.
Gotcha
Firefox uses its own root store by default. A private CA that works in Chrome or Edge may fail here until you import the certificate to Firefox.
Safari (macOS and iOS)
- Click or tap the lock. Choose “Show Certificate.”
- Confirm the domain under “Issued to,” check the issuer, and the dates.
- On iOS, you may need to tap the lock twice for details.
Gotcha
On iOS, enterprise or school profiles can add certificates. If something looks off, check Settings then General then VPN and Device Management for installed profiles.
Common TLS Warnings You Will See (and Clean Fixes)
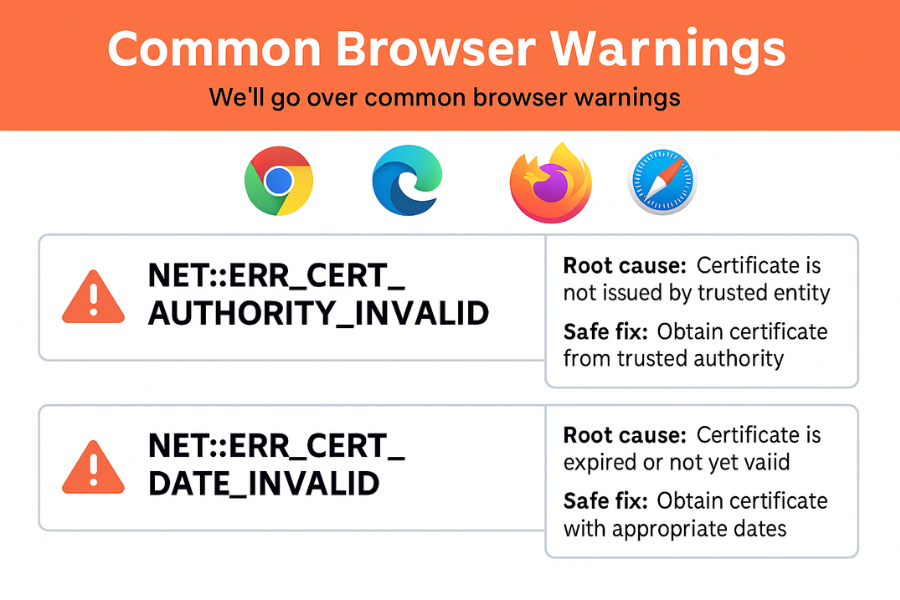
| Warning text | What it usually means | Non destructive test | Safe fix |
|---|---|---|---|
| NET::ERR_CERT_AUTHORITY_INVALID | Unknown or untrusted issuer | Try the same site from a mobile network | If it works on mobile, your desktop trust store is missing a root or a proxy is intercepting TLS |
| NET::ERR_CERT_DATE_INVALID | Clock skew or expired certificate | Check device time and date | Fix system time; if time is correct, the site needs renewal |
| NET::ERR_CERT_COMMON_NAME_INVALID | Certificate name does not match the domain | Click the lock and read Subject or SAN | Use the correct address or avoid the site |
| ERR_SSL_VERSION_OR_CIPHER_MISMATCH | The site uses outdated TLS or a bad cipher | Try a different browser and a modern device | If still broken, wait for the site to fix their server |
| SSL_ERROR_BAD_CERT_DOMAIN (Firefox) | Same as common name invalid | Test the www and bare domain variants | Use the version that matches the certificate |
| SEC_ERROR_UNKNOWN_ISSUER (Firefox) | Untrusted issuer or intercepting proxy | Try on mobile data | Do not proceed unless your company IT confirms the proxy |
| Safari “Cannot verify server identity” | Certificate path or name problem | Force close the tab and try again | If it repeats, avoid entering any data |
Do not click “proceed” on a red full page warning unless you expressly trust the network and are using a pinned private CA on purpose.
Mixed Content and Why the Lock Sometimes Flickers
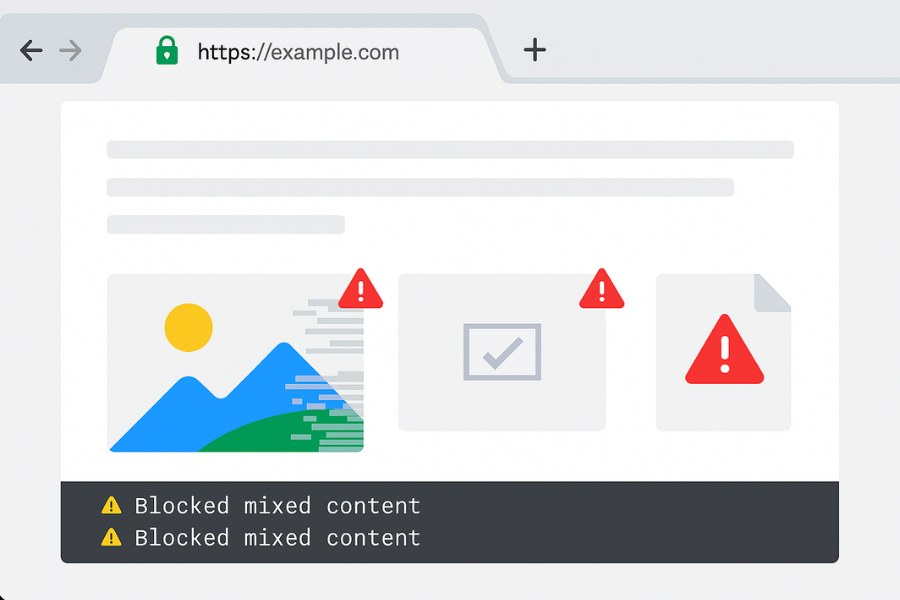
A page can be served over HTTPS yet pull images or scripts over HTTP. That is mixed content. Modern browsers block the risky parts but the page can break in odd ways.
Quick check
Open dev tools then the Console. You will see “blocked mixed content” messages. Share those with the site owner.
Your move as a user
Reload with cache bypass. If it still breaks, avoid login or checkout on that site until they fix it.
Identity Levels: DV, OV, EV and What Actually Shows
| Type | What it verifies | How browsers display it today |
|---|---|---|
| Domain Validation (DV) | Control of the domain only | Standard lock and HTTPS in the address bar |
| Organization Validation (OV) | Domain control plus basic company records | Same lock; organization name is behind one or two clicks |
| Extended Validation (EV) | More paperwork and checks | Same lock; some browsers show the company name in the certificate viewer only |
Takeaway
Treat all three the same in your flow. Always read the address bar and the certificate details. Do not trust a site only because EV appears in the paperwork.
Admin Corner: Real World Policy Tips
- Turn on HSTS with include subdomains and preload for your domains once you are sure every subdomain is ready.
- Use ACME automation for renewals so certificates never expire on a weekend.
- Monitor for new certificates that mention your domains using Certificate Transparency logs.
- If you must use a TLS inspection proxy, install the private root only on managed devices and present clear user notices.
- Avoid client side public key pinning in production. Use report only mechanisms and focus on CT monitoring.
Two Minute Safety Routine for Any Checkout or Login
- Address bar check for typos or lookalikes.
- Lock details check for domain, issuer, and expiry.
- Look for a padlock consistently across the entire flow: product page, cart, login, and payment pages.
- If the flow jumps to a different domain for payment, repeat the check there.
- Save the bookmark and use it for future visits.
Troubleshooting Playbook Without Data Loss
| Symptom | Root cause (ranked) | First tests | Last resort |
|---|---|---|---|
| You cannot reach a site but others can | Local DNS cache, stale HSTS, security software | Try private window, try mobile data | Clear HSTS set for that domain, reset security tool rules |
| Red warning on only one device | System clock skew, local proxy, antivirus interception | Compare time with your phone, try a second browser | Reinstall problematic root store or remove the proxy |
| The lock appears then disappears on scroll | Dynamic content loading insecure items | Open dev tools, watch Console for mixed content | Do not log in; report URL and errors to the site |
| Random “server identity” popups on iOS | Captive portal, school profile, Wi Fi proxy | Toggle airplane mode, forget and rejoin Wi Fi | Remove unknown profiles with admin help |
How to clear HSTS for a single host
Chrome and Edge: visit chrome://net internals, choose HSTS, query the domain, and delete domain security policies.
Firefox: in the address bar enter about:config and search for the domain in HSTS settings, or clear site data from Preferences then Privacy and Security.
Comparison: Browser Certificate Viewers and Shortcuts
| Browser | Quick path to certificate | Chain viewer | Root store used |
|---|---|---|---|
| Chrome | Lock then “Connection is secure” then “Certificate is valid” | Yes | OS trust store |
| Edge | Lock then “Connection is secure” then “Certificate (valid)” | Yes | OS trust store |
| Firefox | Lock then arrow then “More information” then “View Certificate” | Yes | Built in Mozilla store by default |
| Safari macOS | Lock then “Show Certificate” | Yes | OS trust store |
| Safari iOS | Lock then “Show Certificate” | Partial | OS trust store with mobile profile overrides |
Safety Notes for Special Cases
Public Wi Fi
If a login page pops up with no lock and a different domain, it is a captive portal. Complete it, then browse to your site again and recheck the lock before entering any credentials.
Enterprise guest networks
Expect TLS interception on managed machines. On personal devices, do not install unknown roots for convenience.
Home routers
If your router admin page claims to be your bank with a lock, you are on the wrong address. Always reach your bank by typing the known domain or using a saved bookmark.
Field Examples You Can Practice
Exercise 1: a real store
Open a well known store. Check the lock and view the certificate. Note the issuing CA and the validity period. Add the data to a short note so you can spot changes later.
Exercise 2: a phishing test page from your security team
Observe that it can still show a lock. Identify the domain mismatch that gives it away. Capture a screenshot for training.
Exercise 3: an expired cert playground
Search for “expired bad ssl” test pages. Load one and read the full warning. Capture the exact error text your browser uses. This builds muscle memory for the day it matters.
Conclusion
The browser lock icon is a fundamental pillar of internet privacy, guaranteeing that your connection is encrypted and that the site’s certificate identity matches the domain. However, the lock is a sign of privacy, not trust. True online safety requires the user to execute a quick, three, step verification: check the address bar for typos, verify the certificate domain/issuer, and watch for full, page red warnings. Never click through a security warning, always be skeptical of lookalike domains, and treat all identity validation levels (DV, OV, EV) with the same vigilance. Your active verification, not the presence of a passive icon, is your best defense against phishing and network interception.
