Authenticated Encryption (AEAD), Securing Data Streams Against Undetected Tampering

Developed by Newsoftwares.net, this professional guide cuts through the jargon to explain Authenticated Encryption with Associated Data (AEAD), the mandatory standard for securing data streams. Learn how this crucial mechanism enforces both confidentiality and integrity, instantly detecting any tampering or corruption. By following these clear, step by step instructions, users gain the confidence of defense grade security and privacy in their data handling.
Direct Answer: Authenticated Encryption with Associated Data (AEAD) is the mandatory cryptographic standard for ensuring data security. AEAD stops tampering in data streams by enforcing two crucial properties simultaneously: confidentiality (encryption) and integrity (authentication). Unlike older encryption methods that simply scramble data, AEAD algorithms like AES GCM and ChaCha20 Poly1305 instantly detect even a single bit of alteration or corruption via a cryptographic tag. If the data is tampered with, the system refuses to decrypt, halting processing immediately and preventing silent, malicious data injection.
I. Stopping Tampering, The AEAD Imperative
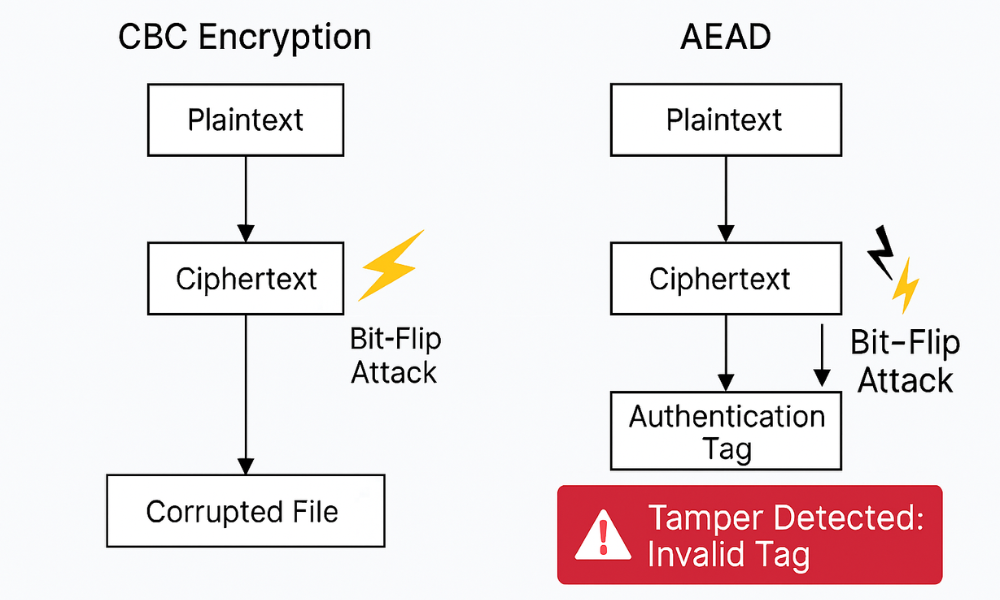
1.1. Why Encryption Alone Fails (The Integrity Gap)
Confidentiality, making data unreadable without the key, is only half of the security equation. Legacy encryption modes, such as the older Advanced Encryption Standard (AES) in Cipher Block Chaining (CBC) mode, were fundamentally flawed because they only guaranteed confidentiality. They provided no intrinsic mechanism to verify if the ciphertext had been modified after encryption. This is known as the integrity gap.
The absence of built in authentication allows for critical manipulation attacks, such as bit flipping. An attacker does not need the secret key to successfully change the output of the decryption process in a predictable way. When a victim decrypts this tampered ciphertext, the file opens without raising an error, but the data payload is corrupted or maliciously altered as directed by the attacker. This is a severe failure mode, particularly visible in proprietary or older tools that employ weak encryption layers, such as certain legacy file formats that utilize the seriously flawed ZIPCrypto.
1.2. AEAD 101, Defining Confidentiality, Integrity, and AAD
Authenticated Encryption with Associated Data (AEAD) closes the integrity gap by combining encryption with a robust Message Authentication Code (MAC) into a single, seamless function.
The three essential functions AEAD provides are:
- Confidentiality: The process encrypts the message (plaintext) into an unreadable ciphertext, ensuring only holders of the correct key can read the content.
- Integrity: During encryption, a unique cryptographic tag (or MAC) is calculated using the key, the nonce, and the resulting ciphertext. Upon decryption, the recipient recalculates this tag. If the calculated tag does not perfectly match the received tag, the decryption process stops instantly and fails validation. This ensures detection of any intentional or unintentional corruption.
- Associated Data (AAD): AEAD schemes allow a block of non secret data (AAD) to be authenticated alongside the ciphertext. This AAD could include crucial metadata, file headers, or protocol identifiers. While the AAD itself is not encrypted (it remains readable), its integrity is guaranteed. An attacker cannot tamper with the ciphertext or the AAD without invalidating the final authentication tag.
II. Deep Dive, AEAD Algorithms and Selection
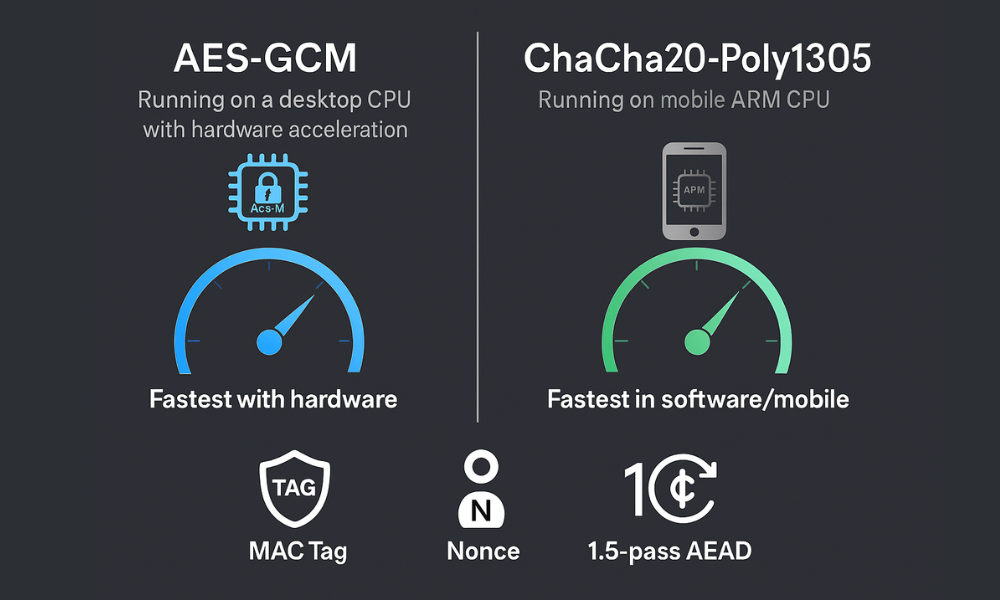
Choosing the correct AEAD algorithm depends heavily on the platform where the encryption operation takes place. The two major modern standards are AES GCM and ChaCha20 Poly1305.
2.1. AES GCM, The Hardware Acceleration Champion
AES in Galois/Counter Mode (AES GCM) is frequently the default choice in enterprise and desktop environments. It combines high speed AES encryption with the GHASH integrity function. AES GCM is designed to perform exceptionally well on systems that support the AES NI instruction set extension, which is built into most modern Intel and AMD CPUs. On systems utilizing AES NI, GCM achieves industry leading throughput, often operating at less than 1 cycle per byte (cpb) for large data records.
However, this reliance on hardware acceleration introduces a vulnerability on systems lacking the instruction set. Without AES NI, performance degrades significantly. Furthermore, security experts recommend exercising caution when implementing software only versions of GHASH, as they may present security risks compared to relying on dedicated hardware support.
2.2. ChaCha20 Poly1305, The Mobile and Software Advantage
ChaCha20 Poly1305 provides an elegant and fast solution for environments that lack specialized cryptographic hardware. It consists of the ChaCha20 stream cipher combined with the high speed Poly1305 MAC function.
This construction is optimized for fast and secure software implementations, particularly on platforms like mobile devices using ARM based CPUs. In these mobile and embedded systems, ChaCha20 Poly1305 typically offers superior performance compared to AES GCM, which has more software overhead. For mobile applications, ChaCha20 Poly1305 often results in lower power consumption while maintaining comparable security levels to GCM.
2.3. The Crucial Nonce (IV) Management Rule
Both AES GCM and ChaCha20 Poly1305 are counter modes of encryption, meaning they require a unique, one time value, typically referred to as a Nonce (number used once) or Initialization Vector (IV), for every single message encrypted under the same key. For ChaCha20 Poly1305, this is a 12 byte value.
The critical mandate is simple and absolute: NEVER reuse a nonce with the same key. Reusing this pair constitutes a catastrophic cryptographic failure. If the nonce and key pair are reused, the security of all messages encrypted with that pair is immediately compromised, potentially leading to the leakage of plaintext information and enabling direct, known plaintext attacks. Proper implementation demands that the nonce be unique, whether generated randomly or derived from a message sequence number.
AEAD Algorithm Selection Matrix
| Feature | AES 256 GCM | ChaCha20 Poly1305 | Legacy (e.g., AES CBC HMAC) |
| Underlying Primitive | AES Block Cipher | ChaCha Stream Cipher | AES Block Cipher + HMAC Hash |
| Integrity Mechanism | GHASH (Built in MAC) | Poly1305 (Built in MAC) | HMAC (Separate Pass) |
| Performance (w/ AES NI) | Fastest (Sub 1 cpb) | Fast (Software Optimized) | Variable (Two passes) |
| Performance (No AES NI) | Slower, Higher Overhead | Excellent, Low Power Draw | Poor |
| Complexity/Passes | 1.5 pass (Highly efficient) | 1.5 pass (Highly efficient) | 2 pass (Less efficient) |
| Recommended Use | Enterprise servers, modern desktop hardware (with AES NI). | Mobile devices (ARM), embedded systems, high speed software. | Should be avoided for new implementations. |
III. Secure Implementation Tutorial, Key Derivation and Verification
The security of any AEAD scheme starts not with the cipher, but with the quality of the secret key. When the key is derived from a user provided password, a robust Key Derivation Function (KDF) is essential.
3.1. Establishing Trust, Key Derivation Function (KDF) Setup
A KDF takes a low entropy password (which humans can remember) and stretches it into a high entropy, cryptographically strong key suitable for an AES 256 cipher. This process relies on two fundamental principles: salting and key stretching.
- Salting: A unique, random value (the salt) must be stored alongside the hashed key for every user. This ensures that even if two users choose the exact same weak password (e.g., “password123”), the resulting derived keys will be different. Salting effectively defeats precomputed attack tables, such as rainbow tables.
- Key Stretching: The KDF executes the hashing function iteratively thousands of times (e.g., 200,000 iterations). This process is deliberately time consuming. While it slows down the legitimate user slightly, it exponentially increases the time required for an attacker to perform a brute force attack, providing a vital layer of defense against modern computing power. Algorithms like Argon2 offer stronger resistance to modern parallel processing than older standards, though PBKDF2 remains widely used and secure when properly configured.
3.2. Step by Step KDF Principle (PBKDF2 HMAC SHA256)
A recognized standard KDF implementation is PBKDF2 (Password Based Key Derivation Function 2) using HMAC SHA256.
- Input Preparation: Collect the user’s password, a unique salt value (typically 16 bytes), and the predetermined iteration count.
- Algorithm Execution: The PBKDF2 algorithm repeatedly applies the HMAC SHA256 function, utilizing the password and salt across the specified number of iterations (e.g., 200,000 iterations).
- Key Output: The KDF produces a 32 byte (256 bit) secret key. This key is the high entropy input used directly by the AEAD cipher (e.g., AES 256 GCM). The integrity protection is thus derived from the user’s secret password.
3.3. Applying AEAD to Local Files, Secure Archiving with 7 Zip
For securing and porting files between systems, archive utilities that implement modern AEAD are preferable. The open source tool 7 Zip, which implements AES 256, uses a robust KDF derived from the SHA 256 hash algorithm and incorporates a large number of iterations to stretch the key, ensuring effective security.
How To: Encrypting a File with Integrity Using 7 Zip
TL;DR Outcome: Generate a portable .7z container using AES 256 encryption and confirm the critical option to encrypt filenames is enabled.
Prerequisites & Safety: Ensure the password meets high security requirements (minimum 8 characters, mixed case, and numerals).
Steps: Encrypting the Archive
- Initiate Archiving: Locate the target file or folder in File Explorer. Right click the selection, choose 7 Zip, and click Add to Archive… .
- Algorithm Selection: In the resulting dialog box, verify that the Encryption Method under the Encryption section is set to AES 256.
- Set Password: Input a strong password and confirm it.
- Crucial Privacy Step: The most vital step for true privacy is checking the box labeled Encrypt file names. If this option is not checked, an attacker can still view the entire directory structure, file names, and sensitive metadata within the archive, even though the file contents are encrypted. Unencrypted filenames are a serious privacy breach.
- Finalize: Click OK to generate the encrypted .7z archive.
Proof of Work: 7 Zip Configuration Snapshot
| Setting | Required Value | Security Rationale |
| Archive Format | 7z | Supports robust AEAD standards (AES 256). |
| Encryption Method | AES 256 | Industry standard for confidentiality and integrity. |
| Password | (Strong, High Entropy) | The KDF process relies entirely on this source strength. |
| Encrypt file names | ON | Hides sensitive metadata (file structure) from unauthorized viewers. |
IV. Cross Platform Security Comparison, Vaults Versus OS Native Encryption
When assessing data protection tools, a clear distinction must be made between OS native, defense grade solutions and proprietary, third party applications.
4.1. The Windows EFS Layering Concept
Windows offers the Encrypting File System (EFS), which provides filesystem level encryption integrated directly into the NTFS file system. EFS operates on a per user, per file basis, ensuring that files are only decryptable by the specific user account that encrypted them. EFS is available in Professional and Enterprise versions of Windows but is typically excluded from Home editions.
EFS keys are stored by default on the operating system drive. If a system lacks full disk encryption, an attacker who gains physical access can remove the drive and analyze the contents offline. Therefore, EFS should never be used as a standalone defense against physical theft. The robust security strategy requires pairing EFS with BitLocker Drive Encryption. BitLocker encrypts the entire system drive, effectively safeguarding the underlying EFS root secrets and preventing offline access to the keys. This combination creates a powerful defense: BitLocker protects the entire container, and EFS provides individual user separation within it.
4.2. The Catastrophic Flaws of Proprietary Vault Apps
Many third party mobile applications marketed as “vaults” or “lockers,” often disguised as functional calculator apps , pose significant security risks due to weak or proprietary cryptographic implementations.
Vulnerability Case Study: Hardcoded Keys
Forensic analysis has revealed that certain popular calculator vault apps exhibit critical cryptographic deficiencies. For instance, some versions of the “Locked Secret Calculator Vault” were found to use a single, hardcoded encryption key, such as Rny48Ni8aPjYCnUI, for all cryptographic operations. This practice nullifies any security derived from the user’s password. The discovery of that single key compromises every single user of that application instantly and universally.
Weak Modes and KDFs
Furthermore, these applications often use weak or dangerous encryption practices, such as AES CBC mode where the Initialization Vector (IV) and the key are derived from the same low entropy value, sometimes even using the same value for both. This avoids the fundamental requirements of modern AEAD standards and introduces high risk.
4.3. OS Native Vaults, Defense Grade Integrity
Modern OS native file lockers, often leveraged by device manufacturers, provide substantially higher levels of security by integrating with hardware trust mechanisms.
Samsung Secure Folder
This feature is protected by the defense grade Samsung Knox security platform. Knox provides hardware backed encryption and protects the folder against malicious attacks and unauthorized access. It operates within a secure execution environment, encrypting all stored data.
Feature Superiority
OS native vaults, like Samsung’s Secure Folder or Google Files’ Locked Folder, offer granular control, separate password requirements from the device lock screen, and prevent data leakage via the clipboard or notifications. They avoid creating a risky chain of trust with third party developers, whose proprietary key management often leads to the vulnerabilities detailed above.
V. Safe Sharing and Transfer Integrity
Data must retain its confidentiality and integrity when moving from one secure location to another. AEAD guarantees integrity at the file level, but the mechanism of exchange must be handled securely.
5.1. The Core Rule, Out of Band Key Exchange
The most common failure in securely sharing encrypted data is transmitting the key alongside the data. If the communication channel (e.g., email) is compromised, the attacker gains both the ciphertext and the key instantly.
The core security principle dictates that one should never transmit the encrypted data and the decryption password/key in the same communication. After encrypting a document (using 7 Zip AES 256, for example), the encrypted file should be sent via one method (e.g., email or cloud link), and the password should be sent via a separate, trusted, out of band channel, such as Signal, SMS, or a secure voice call.
5.2. Secure Cloud Sharing as an Attachment Alternative
Many organizational email systems and security gateways (DLP policies) proactively block attachment types deemed high risk, such as executable files (.exe) or compressed archives that cannot be scanned (like password protected ZIPs or PDFs).
Instead of struggling to bypass these necessary security layers, the best practice is to leverage secure cloud storage.
Method: Sharing Encrypted Files Via Link (Proton Drive Example)
- Upload: Upload the file (already protected by AEAD encryption, e.g., a .7z container) to a secure cloud platform such as OneDrive or Proton Drive.
- Generate Link: Select the file and choose to generate a secure, sharable link by enabling Create public link.
- Policy Control: To enforce access control, navigate to the link settings (often a gear icon). The integrity of the link sharing mechanism is dramatically improved by enforcing:
- Set link password: A separate password to access the link.
- Set expiration date: The link automatically revokes access after a defined time (e.g., 24 hours).
- Distribution: Send the link via the less secure channel (email), and transmit the link password and the file decryption key via a separate, secure channel.
5.3. Hashing for Post Decryption Integrity Checks
While AEAD’s tag verification ensures that the file was not altered in transit, it can be useful to verify the content’s integrity after decryption using a cryptographic hash function (checksum).
The standard process involves calculating the file’s SHA 256 hash before encryption and transmission. This unique hash value is shared with the recipient. The recipient calculates the hash after successfully decrypting the file. If the two hash values match, the content is definitively unaltered. It is important to remember that hashing only verifies integrity; it provides no confidentiality. Encoding schemes, such as Base64, are not cryptographic protections; they are reversible data transformations that add no security value.
VI. Advanced Troubleshooting, AEAD Failure Modes and Recovery
When encryption fails, understanding the exact error message is crucial for determining if the issue is tampering, key loss, or misconfiguration.
6.1. When AEAD Tags Fail, Recognizing Tampering
The most definitive sign of data tampering or corruption is an AEAD tag validation failure.
Symptom: Decryption attempts halt immediately, often generating a specific error message such as GCM authentication tag verification failed. In Java environments, this may present as a nested GCMInvalidTagException.
Root Cause Analysis
AEAD is designed to fail loudly upon compromise. The tag mismatch indicates that the ciphertext received does not correspond to the original tag calculated during encryption. This means:
- The data was altered in storage or transit, confirming the threat model AEAD is designed to prevent.
- The Nonce (IV) used for decryption was incorrect or, critically, was reused with the same key, a catastrophic cryptographic failure.
- The data stream was truncated, which can be exploited by truncation attacks.
Mandatory Response: The decryption system must never ignore the invalid tag warning. Upon tag failure, the system cannot output any plaintext, even a slightly corrupt version, as this could leak information to an attacker.
6.2. EFS Decryption Failure Troubleshooting (Windows)
EFS failures usually indicate a failure in key management, as EFS decryption is inextricably linked to the user’s private key certificate.
Prerequisites: EFS relies on a user certificate and a private key stored in the Certificate Manager (certmgr.msc). If Windows is reinstalled, or the user profile is moved, these keys must be backed up as a .pfx file and imported to the new system.
EFS Decryption Error Symptoms and Fixes
| Symptom / Error String | Root Cause (Ranked) | Non Destructive Fix | Data Loss Warning |
| Error 0x80071771: The specified file could not be decrypted or The specified file could not be decrypted | Missing or corrupt EFS Private Key/Certificate (most common); user account lacks decryption authority. | 1. Open certmgr.msc and navigate to Personal > Certificates. 2. Use the Certificate Import Wizard to import the backed up .pfx file, ensuring the private key is selected for import. 3. Verify the certificate’s intended purposes include EFS. | If the original private key is permanently unrecoverable, the encrypted data is lost. Modern encryption is uncrackable without the key. |
| File Access Denied. You need permission to perform this action. | Non owner attempting access; encryption driver may be unavailable. | 1. Log in using the original user profile that performed the encryption. 2. Verify that the correct keystore is loaded using the efskey command if a secondary password was used for the keystore. | EFS keys are tied to the user credentials. Changing file ownership in the Security tab is usually insufficient for decryption. |
| The specified file is encrypted and the user does not have the ability to decrypt it. | The key is present but not loaded into the kernel associated with the user’s current process credentials. | Restart the computer to allow the encryption driver to reload and associate credentials. | N/A. |
6.3. Third Party Vault Data Recovery (High Risk)
Proprietary vault applications carry a high intrinsic risk of data loss because they rely on the user to manage their own cloud backups, which are often not automatic.
- Accidental App Uninstall Risk: If a user accidentally uninstalls a third party calculator vault application, all files stored and encrypted by that application are often deleted immediately, unless the user had proactively configured and synced an in app cloud backup feature.
- Corrupted Retrieval: In cases where users retrieve raw encrypted files from storage after an app failure, files frequently appear corrupted or “unsupported” because the necessary encryption metadata or key structure was lost during the retrieval process.
- Password Reset Risk: For security hardened native vaults (like Samsung Secure Folder), if the option to reset the PIN/password via a linked Samsung account was not enabled initially, the only recourse upon forgetting the password is the destructive option: deleting the Secure Folder and all its contents to reset the configuration.
VII. Key Takeaways and Recommendation Verdict
The fundamental lesson in data protection is that confidentiality without integrity is insufficient and dangerous. All modern applications handling sensitive data must adhere to AEAD standards.
Recommendation Verdict by Persona
| Persona | Primary Security Need | Recommended Solution | Justification |
| Student/Freelancer | Simple, portable file transfer and storage. | 7 Zip (AES 256 + Encrypt Filenames ON) | Provides cross platform portability using verified AES 256 AEAD standards and eliminates metadata exposure via filename encryption. |
| SMB Administrator | Centralized user file security on Windows endpoints. | Windows EFS paired with BitLocker | EFS handles per user separation; BitLocker provides essential full disk encryption to protect the underlying EFS root secrets from physical theft. |
| Mobile User (High Privacy) | Stealth and protection against proprietary cryptographic flaws. | OS Native Vaults (Samsung Knox/Google Files Locked Folder) | Leverages defense grade hardware security, offers key separation, and avoids the severe risk of hardcoded keys found in many third party apps. |
VIII. Frequently Asked Questions (FAQ)
Q: Will using a password protected ZIP file prevent cloud upload blocks?
A: Organizations use Data Loss Prevention (DLP) policies that often specifically block password protected archives (like ZIPs or PDFs) because their contents cannot be scanned for sensitive data. File extension changing is a weak bypass. The best method is to use secure link sharing with expiry dates.
Q: How does tokenization differ from authenticated encryption?
A: Tokenization is a substitution technique that replaces sensitive data (e.g., credit card numbers) with a non sensitive, random placeholder (a token). The token itself has no exploitable value. AEAD, conversely, cryptographically secures the original, full data payload, ensuring both its confidentiality and integrity.
Q: Is AES GCM or ChaCha20 Poly1305 better for mobile devices?
A: ChaCha20 Poly1305 is generally preferred for mobile devices using ARM based CPUs without dedicated AES NI hardware acceleration. It is optimized for safe software execution, offering comparable security and often lower power consumption than software implementations of AES GCM.
Q: What is the risk of moving an EFS encrypted file to a non NTFS drive?
A: EFS is intrinsically tied to the NTFS file system. When an EFS encrypted file is copied to a partition that does not support EFS (such as FAT32 or network shares without EFS), the file is frequently decrypted transparently during the transfer process, exposing the plaintext data immediately.
Q: Can a calculator vault app developer view my encrypted files?
A: If the application uses robust client side AES 256 with unique user derived keys, the developer cannot access your data. However, if the app uses known poor security practices, such as hardcoded keys, or if the “Private Cloud” feature centralizes key management, the potential for unauthorized access exists.
Q: Is encoding data (like Base64) a substitute for encryption?
A: No, encoding is not encryption. Base64 is merely a simple, two way reversible process used to represent binary data in text format. It provides no security or confidentiality and can be instantly decoded by anyone who intercepts it.
Q: Why is key stretching mandatory when encrypting files with passwords?
A: Key stretching (using KDFs like PBKDF2) is vital because it makes the key derivation process deliberately computationally slow. By forcing a large number of iterations (high work factor), key stretching dramatically increases the time required for an attacker to successfully brute force common or dictionary passwords.
Q: If I lose my EFS private key, are my files recoverable?
A: Without the associated private key or a valid Recovery Agent key, the files encrypted by EFS are permanently cryptographically locked. The system is designed to prevent recovery without the key, meaning the data is considered unrecoverable. Recovery requires importing a previously backed up PFX file.
Q: Why would AES GCM fail with an “Invalid Tag” error after moving a file?
A: The “Invalid Tag” error means the AEAD integrity verification check failed, signaling that the data has been altered since encryption. This is the cryptographic scheme successfully halting execution to prevent tampering. Possible causes include unintentional bit corruption during disk transfer or intentional modification.
Q: How can I bypass a cloud policy that blocks password protected PDFs?
A: If a cloud policy blocks password protected PDFs because it cannot scan the contents, one non destructive workaround is to open the protected PDF, enter the password, and use the “Print” function to “Save as PDF.” This creates an unprotected PDF copy that lacks the mandatory encryption and will typically bypass the upload block.
Conclusion
This article demonstrates that Authenticated Encryption with Associated Data (AEAD) is not optional, but the essential foundation for data security, guaranteeing both confidentiality and integrity. You have learned the imperative of avoiding the integrity gap, the correct use of modern AEAD algorithms like AES GCM and ChaCha20 Poly1305, and the absolute necessity of key stretching and out of band key exchange. By standardizing on tools like 7 Zip with Encrypt file names enabled, or leveraging OS native vaults paired with full disk encryption, you can move beyond simple secrecy to verifiable security.
Would you like me to generate the full HTML code for this article, ready for publication on a WordPress blog?
